A sophisticated supply chain attack targeting Chrome browser extensions has compromised at least 35 Chrome extensions, potentially exposing over 2.6 million users to data theft and credential harvesting.
The campaign, which began in mid-December 2024, exploited extension developers through a targeted phishing operation, allowing threat actors to inject malicious code into legitimate extensions.
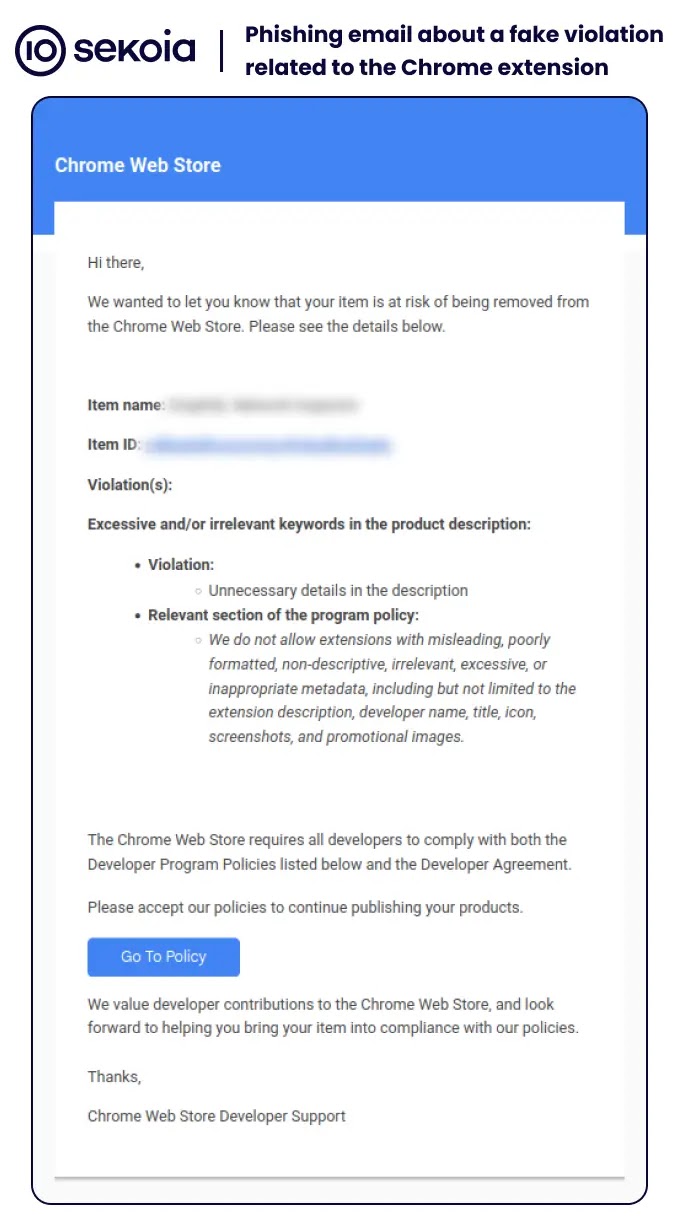
The attack chain started with phishing emails sent to Chrome extension developers, impersonating Google Chrome Web Store support.
.webp)
These emails claimed that the developer’s extension violated store policies and was at risk of removal.
.webp)
Security experts at Sekoia noted that clicking the embedded link led victims to a legitimate Google OAuth authorization page for a malicious application named “Privacy Policy Extension.”
Once authorized, the threat actors gained full access to publish new versions of the targeted extensions.
They then uploaded modified versions containing two malicious JavaScript files: background.js and context_responder.js. These scripts communicate with command and control (C2) servers to download configurations and exfiltrate sensitive user data.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Supply Chain Attack & Adversary’s Infrastructure
The injected code primarily targeted Facebook Business users, harvesting API keys, session cookies, access tokens, account information, and ad account details. Additionally, some variants attempted to steal OpenAI ChatGPT API keys and user authentication data.
.webp)
Cybersecurity firm Cyberhaven was among the first to detect the compromise on December 26, 2024. Their investigation revealed that the attacker’s infrastructure had been active since at least March 2024, suggesting earlier campaigns may have gone unnoticed.
Notable compromised extensions include:-
- GraphQL Network Inspector
- Proxy SwitchyOmega (V3)
- YesCaptcha assistant
- Castorus
- VidHelper – Video Download Helper
- Internxt VPN
- Vidnoz Flex
- Wayin AI
- Reader Mode
- Primus (prev. PADO)
- TinaMind
- VPNCity
- Uvoice
- ParrotTalks
- Bookmark Favicon Changer
- Cyberhaven
The threat actors utilized a network of domains for C2 communication, with many resolving to two IP addresses: 149.28.124[.]84 and 45.76.225[.]148. They also employed 149.248.2[.]160 for data exfiltration.
To identify potential compromise, users can check their Chrome local storage for keys like “graphqlnetwork_ext_manage” or similar extension-specific keys containing downloaded configurations.
.webp)
As a result of this, organizations should carefully review their policies on browser extension usage and implement strict controls to mitigate potential threats.
Recommended actions for users:-
- Remove or update affected extensions to versions released after December 26, 2024.
- Reset important account passwords, especially for Facebook and ChatGPT.
- Clear browser data and reset settings to defaults.
- Monitor account activity for any suspicious behavior.
For extension developers:-
- Implement robust multi-factor authentication for developer accounts.
- Carefully review all OAuth application access requests.
- Regularly audit extension code for unauthorized changes.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
如有侵权请联系:admin#unsafe.sh
