
2025-1-23 09:0:26 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Nisos
Japanese Companies Threatened by DPRK IT Workers
Executive Summary
The Japanese government warned domestic companies in March 2024 about contracting North Korean (DPRK) IT workers posing as Japanese nationals to earn cash, as it is suspected they are using the proceeds to fund Pyongyang’s ballistic missile and nuclear weapons development programs. [1] The United States, Japan, and the Republic of Korea jointly issued an updated warning on 14 January 2025 advising private sector entities, particularly in blockchain and freelance work industries, to thoroughly review risk advisories and announcements to better inform cyber threat mitigation measures and to mitigate the risk of inadvertently hiring DPRK IT workers.[2] Many smaller companies however do not have adequate resources to perform these checks themselves.
In this report, Nisos identified a likely DPRK IT worker, who appears to have been employed in remote Software Engineering and Full Stack Developer positions with Japanese companies since January 2023. The individual appears to be currently employed under the name Weitao Wang at Japanese consulting company, Tenpct Inc., and appears to have been previously employed under the name Osamu Odaka at Japanese software development and consulting firm, LinkX Inc. Nisos researchers identified the individual and his two fake personas based on an email address the United Nations Security Council shared in March 2024, and we were able to identify resumes, GitHub accounts, and work history via open source research techniques. Nisos leverages cross-platform visibility and analytical expertise to provide comprehensive reporting on cyber threats and threat actors that target companies for nefarious reasons.
The United Nations Security Council Report
In March 2024, the United Nations Security Council circulated a panel of experts report which highlighted that DPRK nationals working overseas earn income in violation of sanctions, including in the information technology, restaurant, and construction sectors. [3] In the report, the panel highlighted a list of email addresses that were reportedly associated with DPRK IT workers. One of the email addresses provided was anacondaDev0120@gmail[.]com.
AnacondaDev0120
GitHub Account AnacondaDev0120
Nisos researches identified a Github account associated with the email address anacondadev0120@gmail[.]com, which used the username O_O—likely the initials for the likely DPRK IT worker persona Osamu Odaka—and screenname AnacondaDev0120. Researchers found a commit on the page in March 2024 that was co-authored by github user nickdev0118, which was associated with the email address nickdev0118@gmail[.]com. Research revealed that the email address nickdev0118@gmail[.]com was listed as a contact method for possibly Vietnam-based Huy Diep, who appears to also be employed at Japanese consulting company 10pct. Inc (cf. page 13).
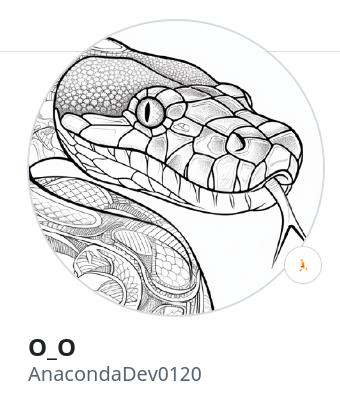
Graphic 1: Profile picture, screenname, and username for the AnacondaDev0120 Github account.[4]
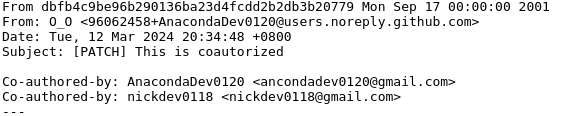
Graphic 2: 12 March 2024 commit on the AnacondaDev0120 Github account.[5]
Freelancer Employment Websites Linked To Anacondadev0120
Nisos researchers identified three freelance employment websites, which listed the Github username anacondadev0120. Two of the websites, LaborX and ProPursuit, had active accounts, while the account on Remote Ok was removed from the website. Each of the freelancer websites’ information was linked to a different name and to different contact information, while claiming the same anacondadev0120 Github account.
LaborX
The resume on freelancer website LaborX listed the name Osamu Odaka while claiming the Github account anacondadev0120. The resume revealed a digitally manipulated photo on the website and an inactive linkedin account.


Graphics 3-4: Profile picture and contact information for the Labor X account. [6]
ProPursuit
The resume on freelancer website ProPursuit listed the name “Link,” while claiming the Github account anacondadev0120. The resume linked to an X account with the username cheng kai ming, which remains active, but has not been updated since 20 October 2012.
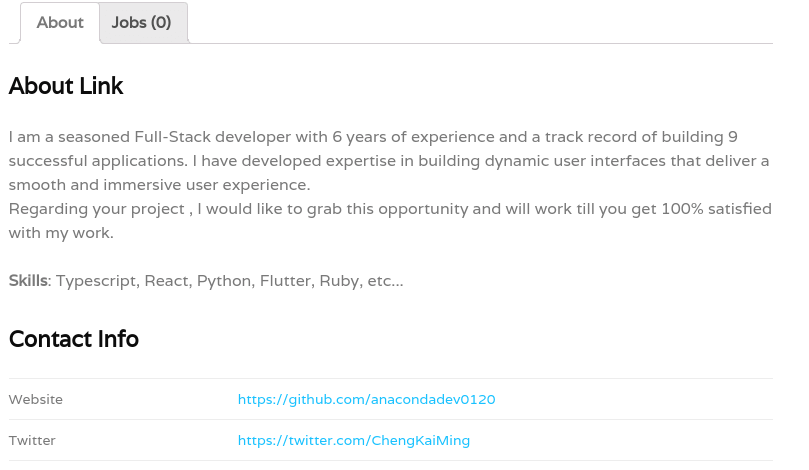
Graphic 5: Account details for the Pro Prusuit account. [7]
Remote Ok
The resume on freelancer website Remote Ok listed the name “shaowtw,” while claiming the Github account anacondadev0120. The resume contained a link to wwt-chi.vercel[.]app, which was no longer active and provided Telegram username skyhero454
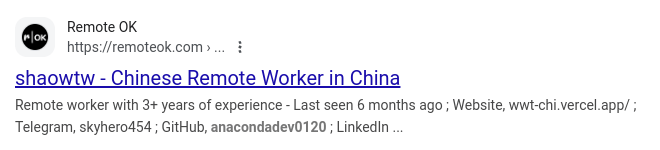
Graphic 6: Google search result for Remote Ok.
To obtain the complete research report, including endnotes, please click the button below.
About Nisos®
Nisos is the Managed Intelligence Company. We are a trusted digital investigations partner, specializing in unmasking threats to protect people, organizations, and their digital ecosystems in the commercial and public sectors. Our open source intelligence services help security, intelligence, legal, and trust and safety teams make critical decisions, impose real world consequences, and increase adversary costs. For more information, visit: https://www.nisos.com.
The post Japanese Companies Threatened by DPRK IT Workers appeared first on Nisos by Nisos
*** This is a Security Bloggers Network syndicated blog from Nisos authored by Nisos. Read the original post at: https://www.nisos.com/research/dprk-it-threat-japan/
如有侵权请联系:admin#unsafe.sh

