This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our next Threat Horizons Report, #11 (full version) that we just released (the official blog for #1 report, my unofficial blogs for #2, #3, #4, #5, #6, #7, #8, #9 and #10).
My favorite quotes from the report follow below:
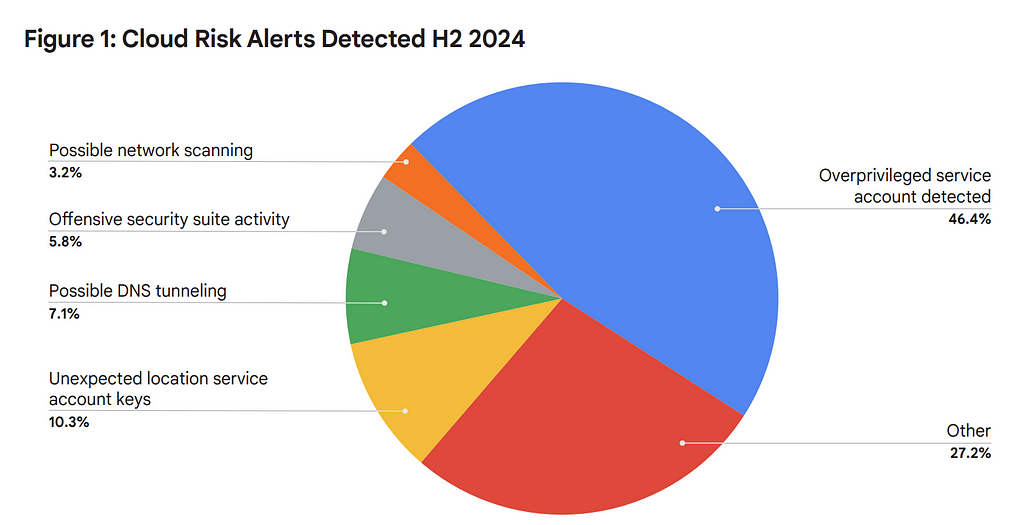
- “Nearly half (46.4%) of the observed security alerts were due to overprivileged service accounts. ” [A.C. — using new data on cloud detections, we confirmed an old hypothesis: if you overprovision, you suffer. Very cause->effect: overprovision -> suffer!]
- “During H2 2024, credential-related vulnerabilities like weak or no passwords continued to be the most common entry point for attackers as shown [below], though the frequency decreased slightly through 2024. Misconfiguration of cloud environments (services or software) remained a significant security gap.” [A.C. As I said in other THR blogs, the main news here is that there is no news; a lot of cloud security problems in 2025 are 2020 problems, at best. Initial access vectors didn’t change all that much. “Secure by default” seems to apply to new cloud deployments perhaps and having no effect on what is running today …]
- “We also observed a new trend in the second half of 2024: a sharp rise in compromised APIs and UIs due to threat actor targeting. These attacks accounted for 17.1% of observed incidents, a substantial increase from the approximately 13% observed in the first half of 2024. “ [A.C. — aha, something DOES change! Perhaps all that endless whining of those ‘“API security vendors” had an effect and attackers are finally interested :-)]
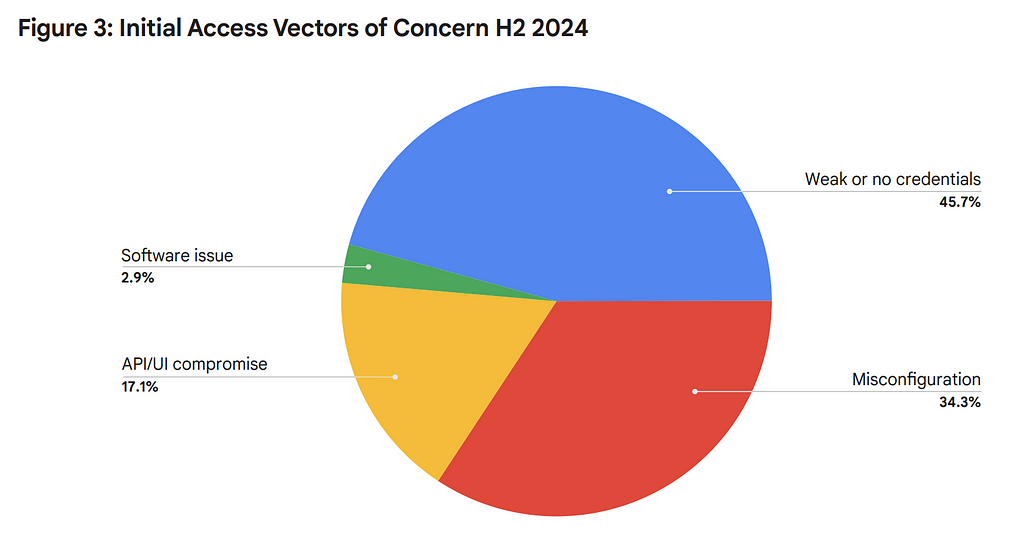
- “We also saw a significant trend in threat actors searching for insecure private keys (13.7%), reinforcing the need for organizations to prioritize the security and proper management of private keys.” [A.C. — next time, somebody asks you in the dark cloud alley “do you even lateral, dude?”, you go “PRIVATE KEY SEARCH!!!”]
- “More than half (62.2%) of threat actor movements once they gained access involved attempting lateral movement within an environment and downloading tools designed for this purpose.” [A.C. — not sure what happened to cryptomining, I think we fixed it…]
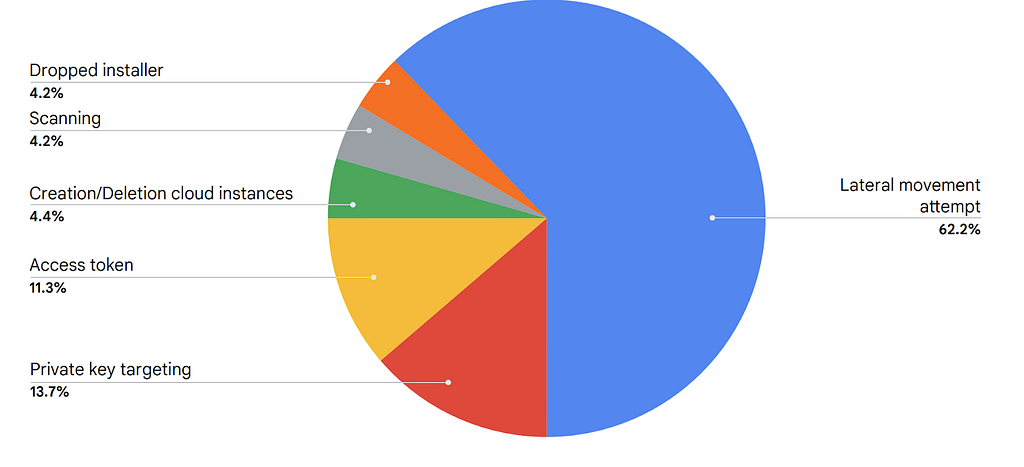
- “Identity compromise is no longer limited to password theft based upon misconfigurations or weak passwords. Threat actors are now gaining access by intercepting or stealing post-authenticated tokens or cookies, effectively bypassing traditional authentication criteria. ” [A.C. — while I am still not a fan of ITDR as a separate tool, it is very clear that we are still under-equipped to fight this one…]
- “The most common methods of identity compromise include brute-forcing using common/guessable passwords, replaying stolen credentials from a previous breach, credential stuffing, phishing, and social engineering.” [A.C. — in other words, a range of 1970s-2020s tactics and methods 😉 And, yes, well-crafted MFA helps against many of these, but not all]
- “Threat actors are increasingly targeting identities and databases, exploiting misconfigurations and vulnerabilities to gain access to sensitive information and resources. Insecure databases containing critical business data and personally identifiable information (PII) are particularly attractive targets.” [A.C. — I am going to channel Captain Obvious here, but can you imagine? Corporate databases contain valuable data! No way, right? And somebody will steal it if you don’t secure it….]
- “To take over cloud service accounts, TRIPLESTRENGTH leverages stolen credentials and cookies, at least a portion of which have come from Racoon infostealer logs, to gain access to victim cloud environments.” [A.C. — a fun example re: cookies!]
- “Mandiant has observed threat actors increasingly extorting victim organizations by exposing their stolen data on Data Leak Sites (DLS). […] The expanded use of these extortion tactics combined with the prevalence of DLS poses a growing threat for all organizations, regardless of where their data is stored.” [A.C. — kinda makes sense, I suspect [gut, not data!] that “encrypt only” was easier on-prem, whole “encrypt+steal and post” works in the cloud]
Now, go and read the THR 11 report!
P.S. Coming soon! Trend analysis of THR1–11!
Related posts:
- EP112 Threat Horizons — How Google Does Threat Intelligence podcast
- Google Cloud Security Threat Horizons Report #10 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #9 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #8 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #7 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #6 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #5 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #4 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #3 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #2 Is Out!
- Illicit coin mining, ransomware, APTs target cloud users in first Google
- Cybersecurity Action Team Threat Horizons report
Google Cloud Security Threat Horizons Report #11 Is Out! was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/google-cloud-security-threat-horizons-report-11-is-out-253b9eae8451?source=rss-11065c9e943e------2


