2025-1-22 15:15:17 Author: www.bleepingcomputer.com(查看原文) 阅读量:2 收藏

South Korean VPN provider IPany was breached in a supply chain attack by the "PlushDaemon" China-aligned hacking group, who compromised the company's VPN installer to deploy the custom 'SlowStepper' malware.
The hackers managed to infiltrate IPany's development platform and insert its custom 'SlowStepper' backdoor on its installer ('IPanyVPNsetup.exe'), which infected customer systems when the VPN was installed.
According to ESET researchers who uncovered the supply chain attack, companies impacted by the attack include a South Korean semiconductor firm and a software development company. However, the first signs of infected victims date back to November 2023 in Japan.
SlowStepper activity
IPany customers become infected after downloading the program's ZIP installer ('IPanyVPNsetup.zip') from the company's website.
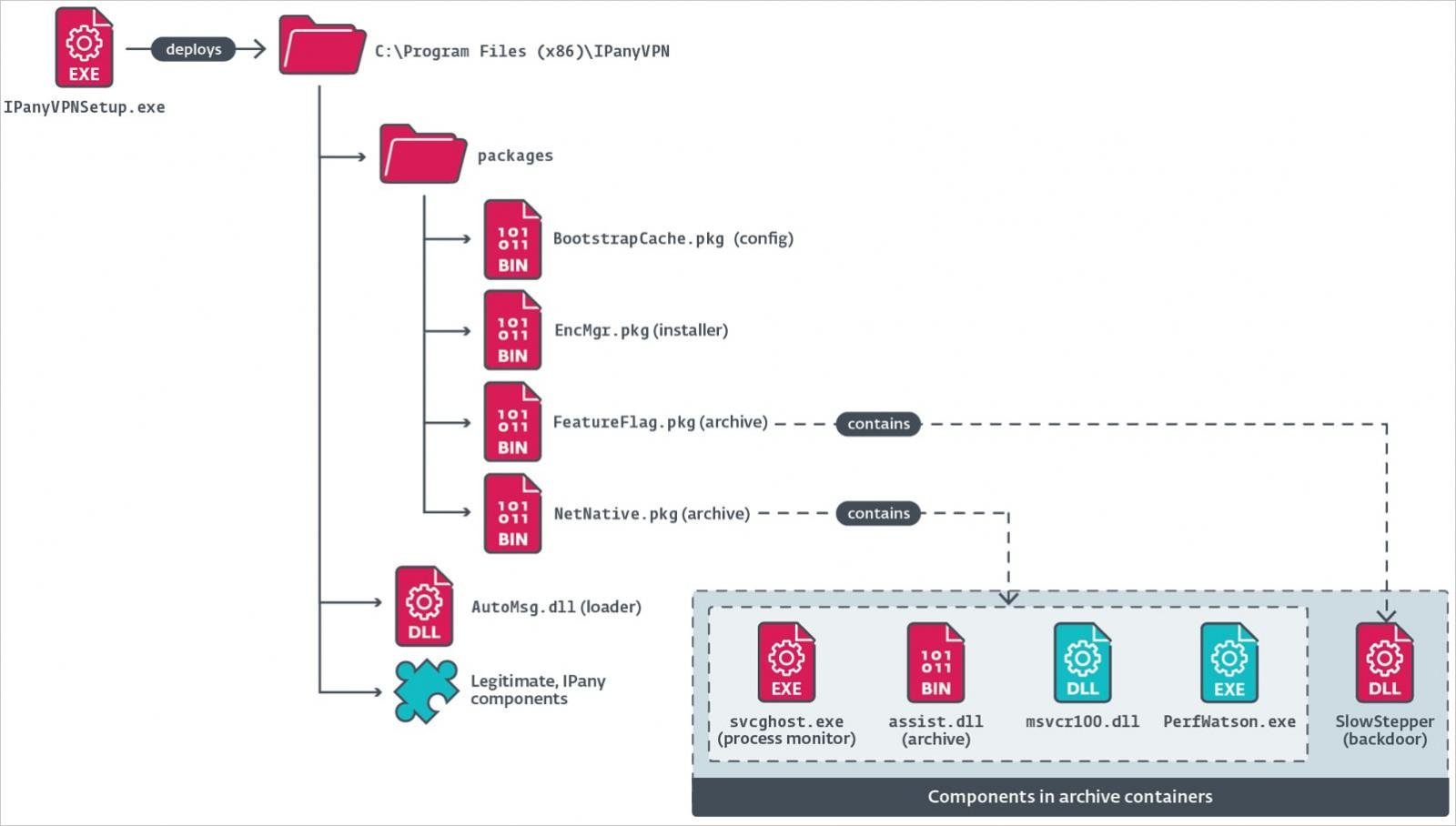
Once the installer is executed, it installs the legitimate VPN product as well as malicious files ('svcghost.exe'), for which a Run key is added in the Registry for persistence.
Source: ESET
The SlowStepper payload is loaded from a image file ('winlogin.gif') via a malicious DLL ('lregdll.dll') that is sideloaded into a 'PerfWatson.exe' process. The svcghost executable monitors the process to ensure it is always running.
ESET says the particular version of SlowStepper used in these attacks is 0.2.10 Lite, which is not as fully-featured as the standard version but could be stealthier due to its smaller footprint and is still a potent tool.
"Both the full and Lite versions make use of an array of tools programmed in Python and Go, which include capabilities for extensive collection of data, and spying through recording of audio and videos," explains ESET.
The most important commands supported by SlowStepper are:
- 0x32 – Gathers a variety of system details, including CPU brand, HDD serial numbers, computer and hostname, public IP address, running processes, installed applications, network interfaces, system memory, webcam, and microphone status, and whether the OS is running in a virtual machine.
- 0x5A – Fetch and run files from the C&C server, enabling the installation of additional payloads.
- 0x3F – Enumerate files and directories on the compromised system.
- 0x38 – Run Python-based spyware tools designed for various espionage functions, such as browser data theft, keylogging, and credential harvesting.
- 0x3A – (Shell mode activation) Enables direct execution of system commands, providing attackers with an interactive environment for controlling the compromised machine.
- 0x39 – Delete specific files or directories, which can be used to erase traces of the malware or disrupt system functionality.
- pycall <module_name> – Loads and runs specific Python spyware modules, such as "Browser" for stealing browser data, "WeChat, Telegram, DingTalk" for extracting chat logs, "ScreenRecord" for capturing screen activity, "Camera" for taking pictures using the webcam, and "CollectInfo" for scanning the disk for sensitive documents.
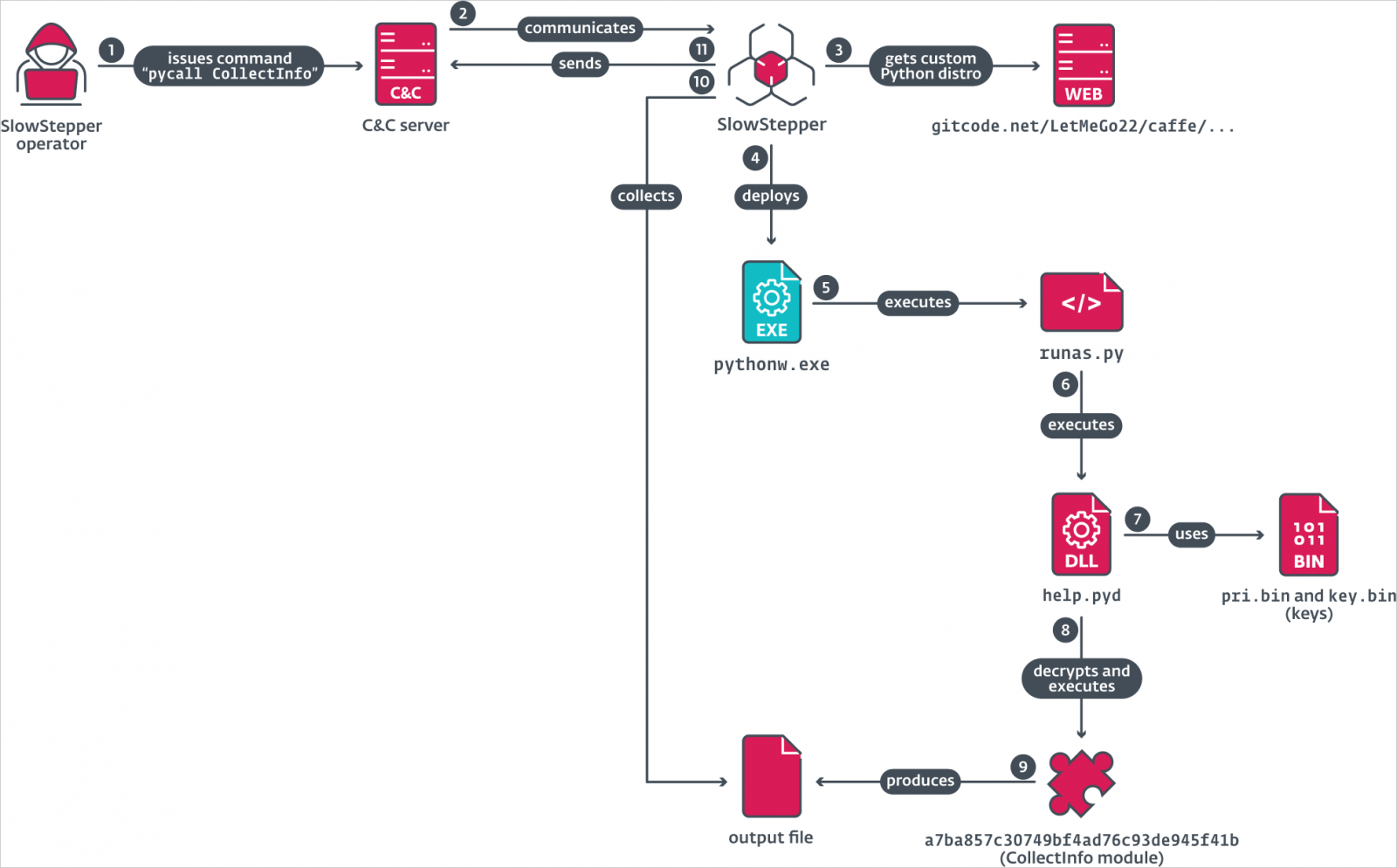
Source: ESET
The researchers contacted the VPN vendor to inform them of the compromise, and the malicious installer was removed from the website. However, those who are already infected need to take action to clean their systems.
ESET underlines that the download page did not feature geo-fencing mechanisms or any other tools to indicate specific targeting, so anyone who downloaded IPanyVPN from November 2023 (and possibly earlier) until May 2024 has been infected by SlowStepper.
The complete list of the indicators of compromise (IoCs) associated with this campaign can be found here.
如有侵权请联系:admin#unsafe.sh