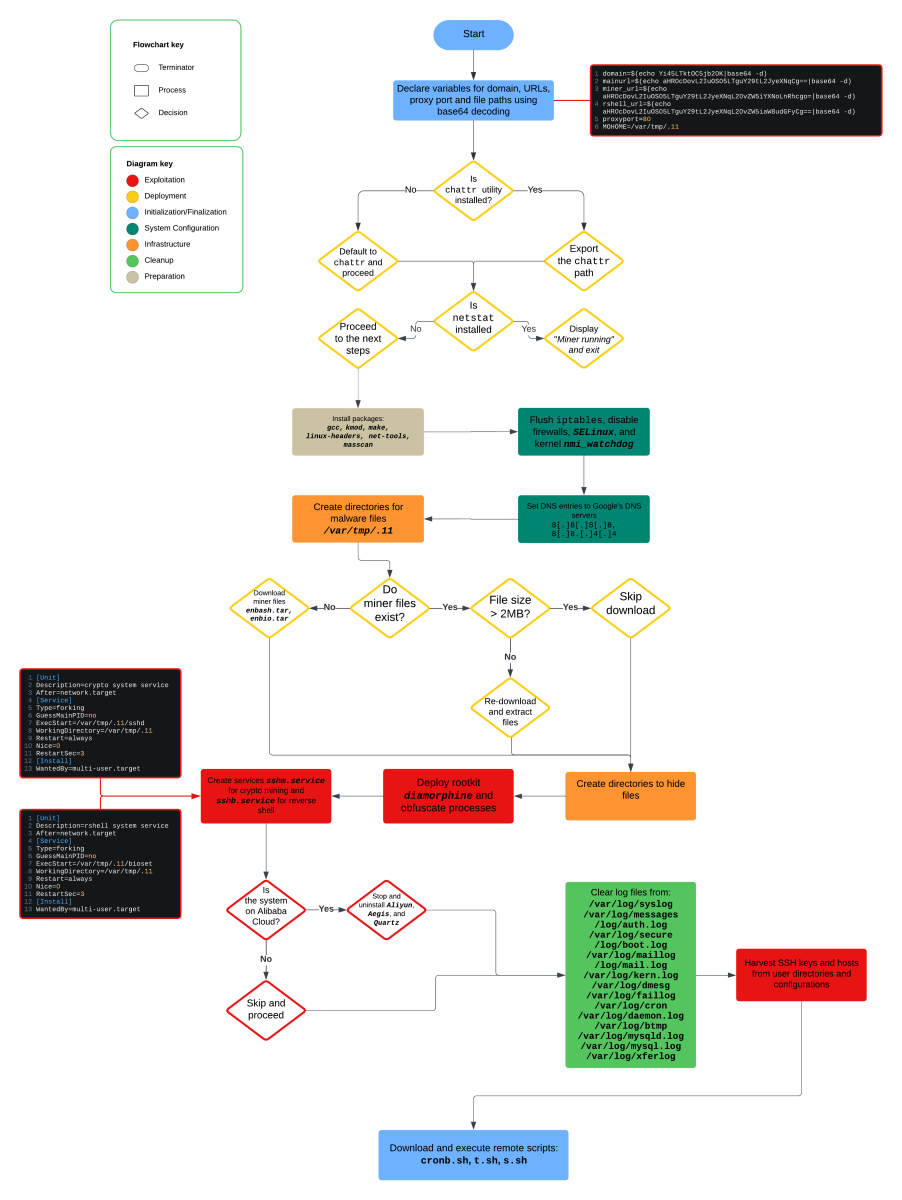
[This is a Guest Diary by James Levija, an ISC intern as part of the SANS.edu Bachelor's Degree in 2024-12-18 00:4:50 Author: isc.sans.edu(查看原文) 阅读量:13 收藏
[This is a Guest Diary by James Levija, an ISC intern as part of the SANS.edu Bachelor's Degree in Applied Cybersecurity (BACS) program [1].]
Executive Summary
TeamTNT is running a crypto mining campaign dubbed Spinning YARN. Spinning YARN focuses on exploiting Docker, Redis, YARN, and Confluence [2]. On November 4th, 2024, my DShield sensor recorded suspicious activity targeting my web server. The attacker attempted to use a technique that tricks the server into running harmful commands. This technique is known as server-side scripting vulnerability. This attack originated from IPv4 address 47.93.56.107 targeting port 8090. The attacker used a technique to disguise their harmful code by encoding it. This technique hides the code’s true purpose and assists with avoiding detection against antivirus software and firewalls.
An analysis of the obfuscated code revealed that the command would send the victim to another website to download a malicious file. The malicious file dropped is named “w.sh” [3]. The purpose of this initial file is to install the requirements to run the intended malware and to download the intended malware from the site hxxp://b[.]9-9-8[.]com/brysj. Once the intended malware is downloaded, it runs and assesses the environment. It targets Linux distributions and cloud environments. The malware identifies possible cloud security and attempts to disable it to allow the rest of the code to run smoothly. The malware then sets up its persistence through creating secure keys to talk back to the attacker’s server and establishes a connection to the attacker’s server. It also uses techniques to hide itself on the victim’s device or cloud environment. Finally, the malware sets up a crypto miner to utilize the victim’s resources for the attacker’s gain.
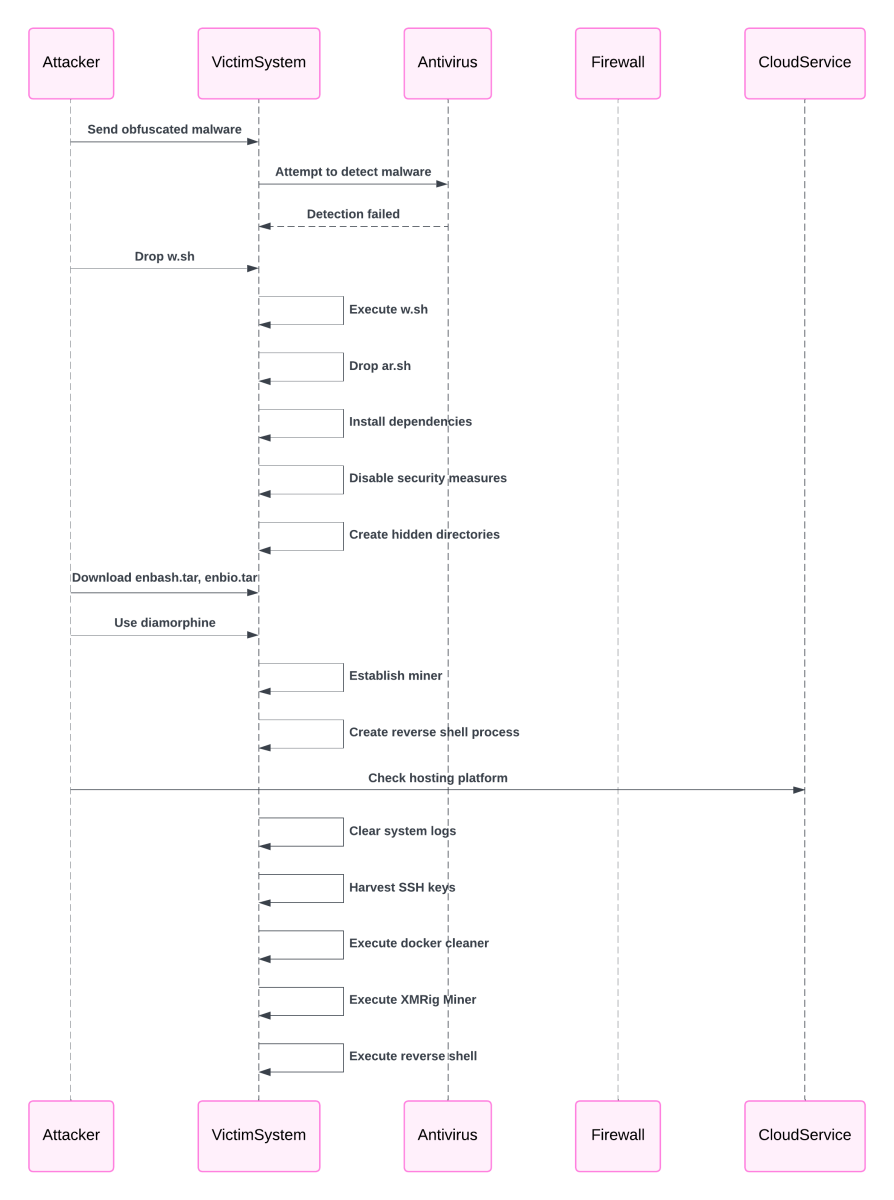
Figure 1: Attack Flow
The impact of this attack extends beyond consuming system resources for cryptocurrency mining. The connection between the victim’s machine or cloud environment and the attacker grants the attacker persistent access. The attacker can abuse this through conducting additional exploits, steal sensitive data, or use the system to launch additional attacks on other systems. TeamTNT is known to have created a work that could steal Amazon Web Service (AWS) credentials. This poses significant risks to operational security and data integrity for any organization.
This attack highlights evolving threats to Linux and cloud environments from sophisticated groups like TeamTNT. Organizations should prioritize securing their infrastructure through regular updates, monitoring suspicious activity, staying up to date on cyber threat intelligence, and implementing robust defenses against malware and their obfuscation techniques. Collaboration withing the cybersecurity community is key to mitigating these ongoing threats.
TeamTNT – Background
TeamTNT is a cyber threat group that has been active since October 2019. The group is well known for their attacks on cloud environments and cryptojacking [4]. The location of the group members is unknown, but they are suspected of being in Germany due to TeamTNT’s X (formerly Twitter) account, with the handle @HildeTnT, sending tweets in English and German [5]. In December 2020, the group was suspected to have 12 members based on a tweet about their group of programmers [6].
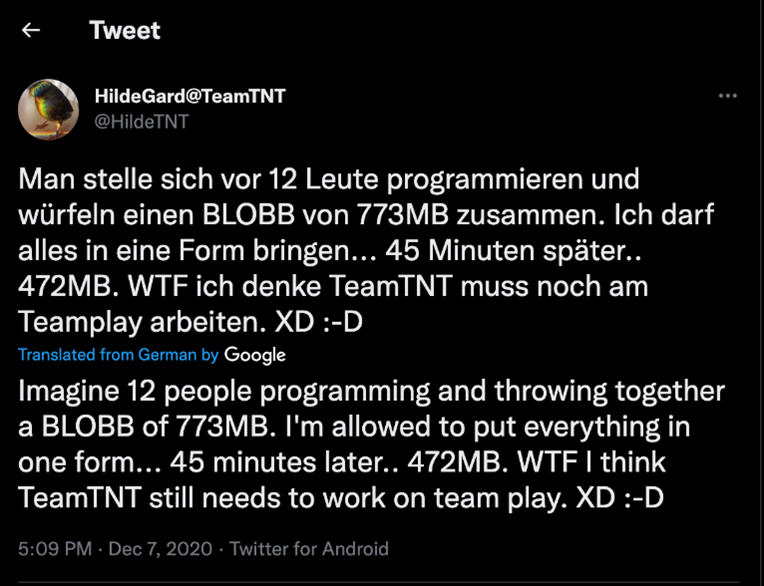
Figure 2: Tweet from TeamTNT referencing the number of programmers [6].
Indicators of Compromise (IoCs)
Identified Malicious Domains and URLs
Below are the malicious URLs observed in the binaries:
- Domain –
hxxps://9-9-8[.]com - Main URL -
hxxps://b[.]9-9-8[.]com/brysj/ - Dropper URL -
hxxps://b[.]9-9-8[.]com/brysj/w[.]sh - Miner URL –
hxxps://b[.]9-9-8[.]com/brysj/d/ar[.]sh - Miner URL -
hxxps://b[.]9-9-8[.]com/brysj/m/enbash[.]tar - Remote Shell -
hxxps://b[.]9-9-8[.]com/brysj/m/enbio[.]tar - Additional URLs –
hxxps://m[.]9-9-8[.]com
IPs Involved
| IP Address | Last Seen |
|---|---|
| 52.223.13.41 | 2024-11-26 |
| 194.36.190.32 | 2024-11-13 |
| 158.160.116.91 | 2024-10-20 |
| 212.233.121.136 | 2024-09-01 |
| 62.113.111.152 | 2024-08-15 |
| 185.208.207.89 | 2024-08-01 |
| 154.38.165.7 | 2024-07-16 |
| 114.114.114.114 | 2024-12-02 |
Figure 3: IP addresses seen.
Associated Files and Hashes
| Filename | Notes | Hash |
|---|---|---|
| w.sh | Dropper | d4508f8e722f2f3ddd49023e7689d8c65389f65c871ef12e3a6635bbaeb7eb6e |
| ar.sh | Dropper | 64d8f887e33781bb814eaefa98dd64368da9a8d38bd9da4a76f04a23b6eb9de5 |
| hf.tar | 651a3034429358a0ccb2d58ecbe2b7f3e4ee1bf4bee3e7a86f7ca873f6049ec2 | |
| diamorphine.c | aec68cfa75b582616c8fbce22eecf463ddb0c09b692a1b82a8de23fb0203fede | |
| diamorphine.h | d27eeb48b1a74efd8710ef4ce62ee8469dd2352b0079c5b1c82e8da43fe932a2 | |
| Makefile | d15af7984ed9b33093d7d5725c84ab24edf7c4ff02af3ac0a6c3aa9d5f7e12f4 | |
| Makefile | 5b9acfd34a30a3f26db492ed4404d518d583c0088a38a7622b683407c34b9108 | |
| processhider.c | 7e84f9aab329754fe4681d4d6e4c64098731fd55b5998d7cfacb08ba4dbdfd5c | |
| enbash.tar | 9eafaf5e0fb9a91f2887f3e81fd7ad6d70973ff7cbb807dab4bf0f319a668b95 | |
| debash.tar | 18137be62c9267cf6b0b40432a91c5818c66bdaa42aad3728c598d3fc65fdcff | |
| bash.sh | b2e26c7ce901296822085164ede73557a10badfdf99d1aa30f338446d0beb2d7 | |
| enbio.tar | bb89a6bbddc5dda36542a5fef230b8fa9d98fbdb0ec4fa1794b8c28a0b5a3af4 | |
| debio.tar | e137bf61096f68478a0daa63fca1b2cc45a99f2dfdcd08d7ff7c449f38cf5ce9 | |
| fkoths | Checks for docker containers | afddbaec28b040bcbaa13decdc03c1b994d57de244befbdf2de9fe975cae50c4 |
| sshd | Xmrig Miner | bbcdffd6fa3b1370dfc091bfd3bfca38be013f72f94af7ef29466d911c9604d8 |
| bioset | Establishes reverse shell | 0c7579294124ddc32775d7cf6b28af21b908123e9ea6ec2d6af01a948caf8b87 |
| cronb.sh | d4508f8e722f2f3ddd49023e7689d8c65389f65c871ef12e3a6635bbaeb7eb6e |
Figure 4: Set of files used for this attack.
Tools and Tactics Used
Malware Insights
Server-Side injection attack
- Attempts to execute an
HTTP GETrequest to download the file w.sh fromhxxp[://]b[.]9-9-8[.]com/brysj/w[.]sh - Attempts to execute the file
w.sh
- Path and domain variables are set
- Domain =
b[.]9-9-8[.]com - Main URL =
hxxp[://]b[.]9-9-8[.]com/brysj
- Domain =
- Bash script checks if the chattr utility is present then renames it to zzhcht and exports the contents.
- This is a tactic used by TeamTNT prior to “quitting” in 2021. [7]
- If chattr is not present, it installs the chatter utility, renames it, and exports the contents.
- It tries both yum install and apt install
- Executes an
HTTP GETrequest to download the file ar.sh fromhxxp[://]b[.]9-9-8[.]com/brysj/ar[.]sh
MITRE ATT&CK Framework Mapping
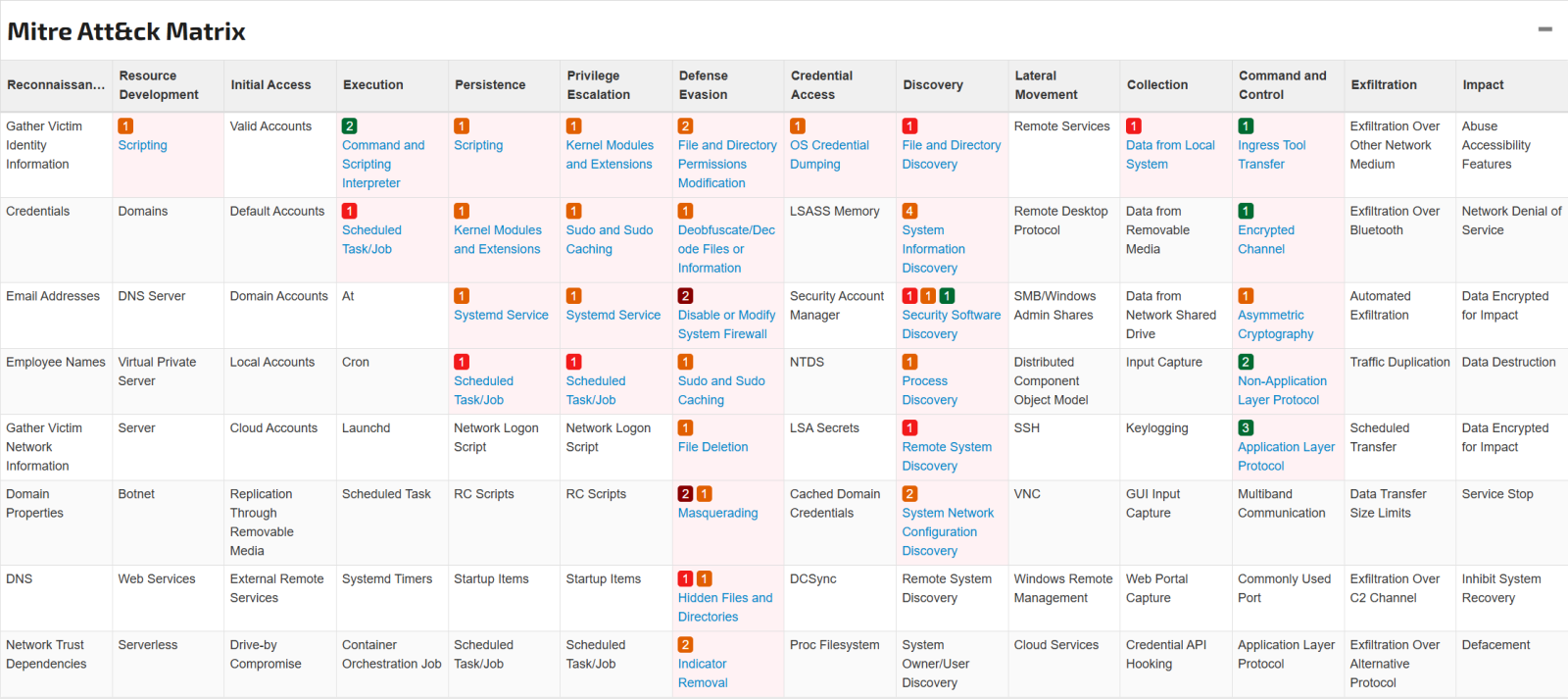
FIgure 5: MITRE ATT&CK mapping for w.sh [3].
ar.sh – Primary file
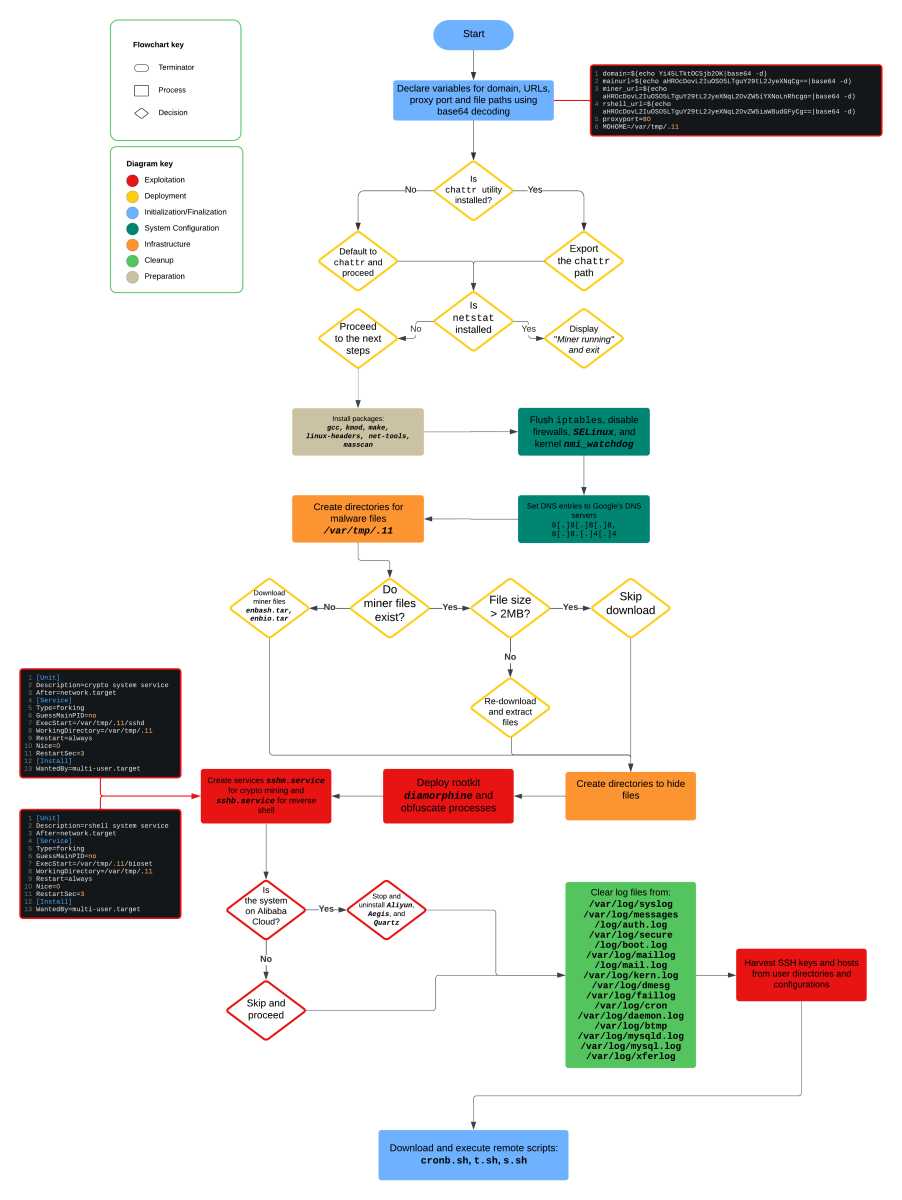
Figure 6: Attack flow of ar.sh
Packages installed by ar.sh:
agcc- “GNU Compiler Collections which is used to compile mainly C and C++ language [8].”
kmod- kmod is a set of tools to handle common tasks with Linux kernel modules like insert, remove, list, check properties, resolve dependencies and aliases [9].”
make- “Assists in the compilation process and is a must-have tool for building large applications [10].”
linux-headers- “A package providing the Linux kernel headers [11].”
net-tools- “This package includes the important tools for controlling the network subsystem of the Linux kernel. This includes arp, ifconfig, netstat, rarp, nameif and route. Additionally, this package contains utilities relating to particular network hardware types (plipconfig, slattach, mii-tool) and advanced aspects of IP configuration (iptunnel, ipmaddr) [12].”
masscan- “MASSCAN is TCP port scanner which transmits SYN packets asynchronously and produces results similar to nmap, the most famous port scanner [13].”
sshd- XMRig 6.20.1-dev payload
pnscan- “Pnscan is a multi threaded port scanner that can scan a large network very quickly. If does not have all the features that nmap have but is much faster [14].”
httpd- “the Apache HyperText Transfer Protocol (HTTP) server program [15].”
bioset- Payload to establish a reverse shell using Platypus
- Platypus is “a modern multiple reverse shell sessions/client manager via terminal written in go” [16].
- Payload to establish a reverse shell using Platypus
MITRE ATT&CK Framework Mapping
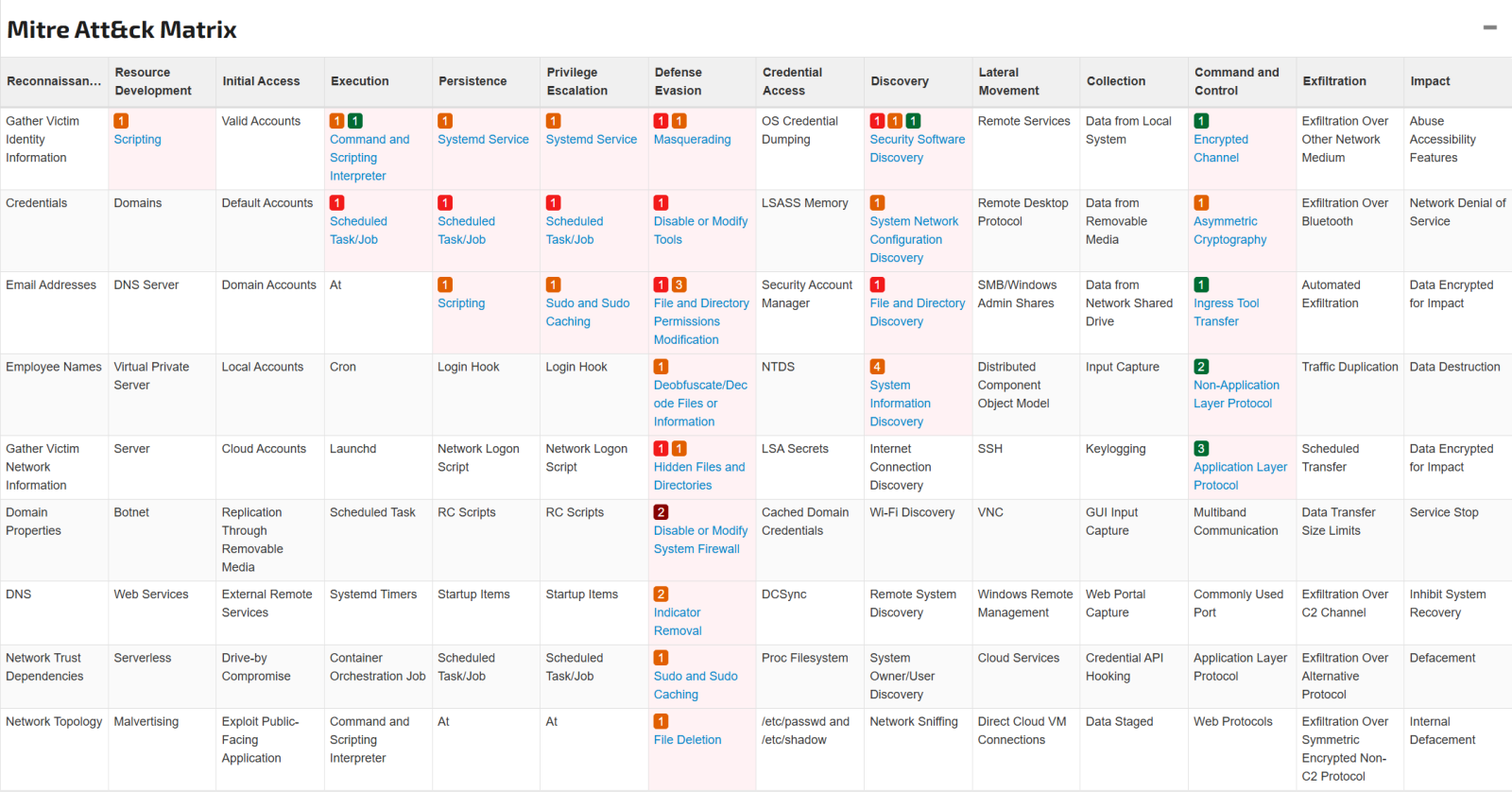
Figure 7: MITRE ATT&CK matrix for ar.sh [17]
fkoths
This binary retrieves and deletes docker images from the host.
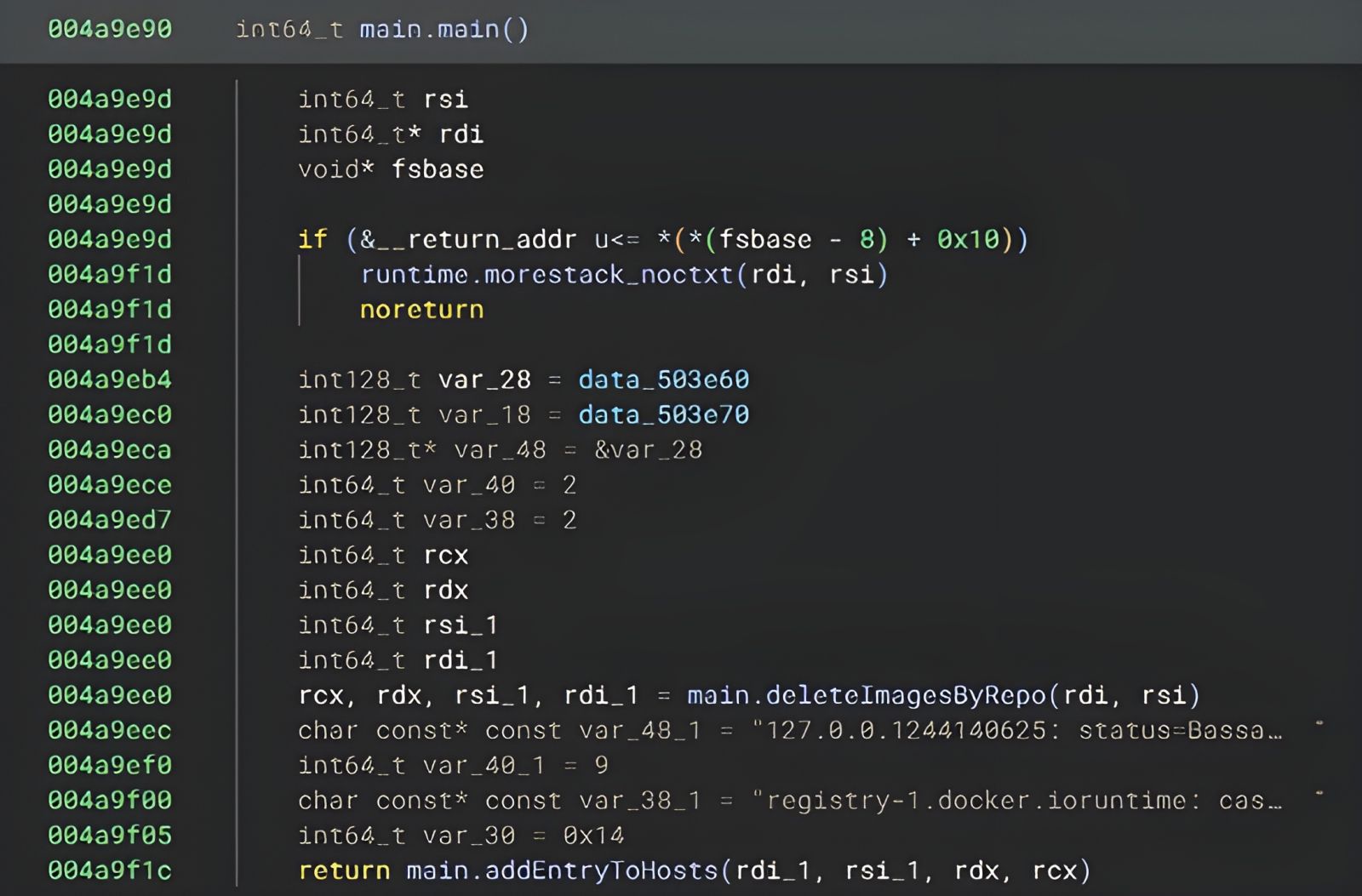
Figure 8: Main.main function of fkoths in BinaryNinja.
MITRE ATT&CK Framework Mapping
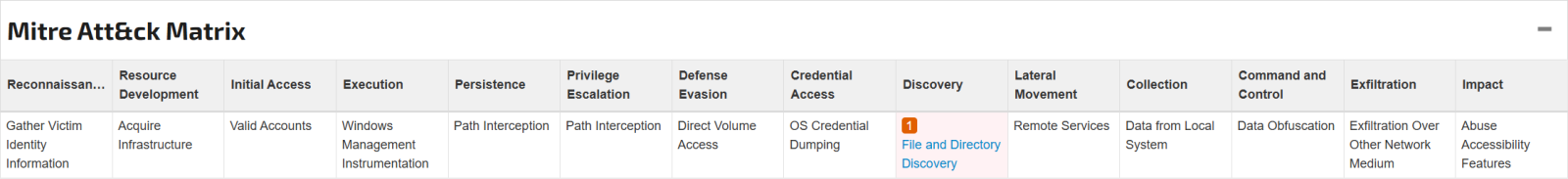
Figure 9: MITRE ATT&CK matrix for fkoths.
sshd
The binary sshd is the payload for the XMRig miner. This one runs on XMRig 6.20.1-dev.
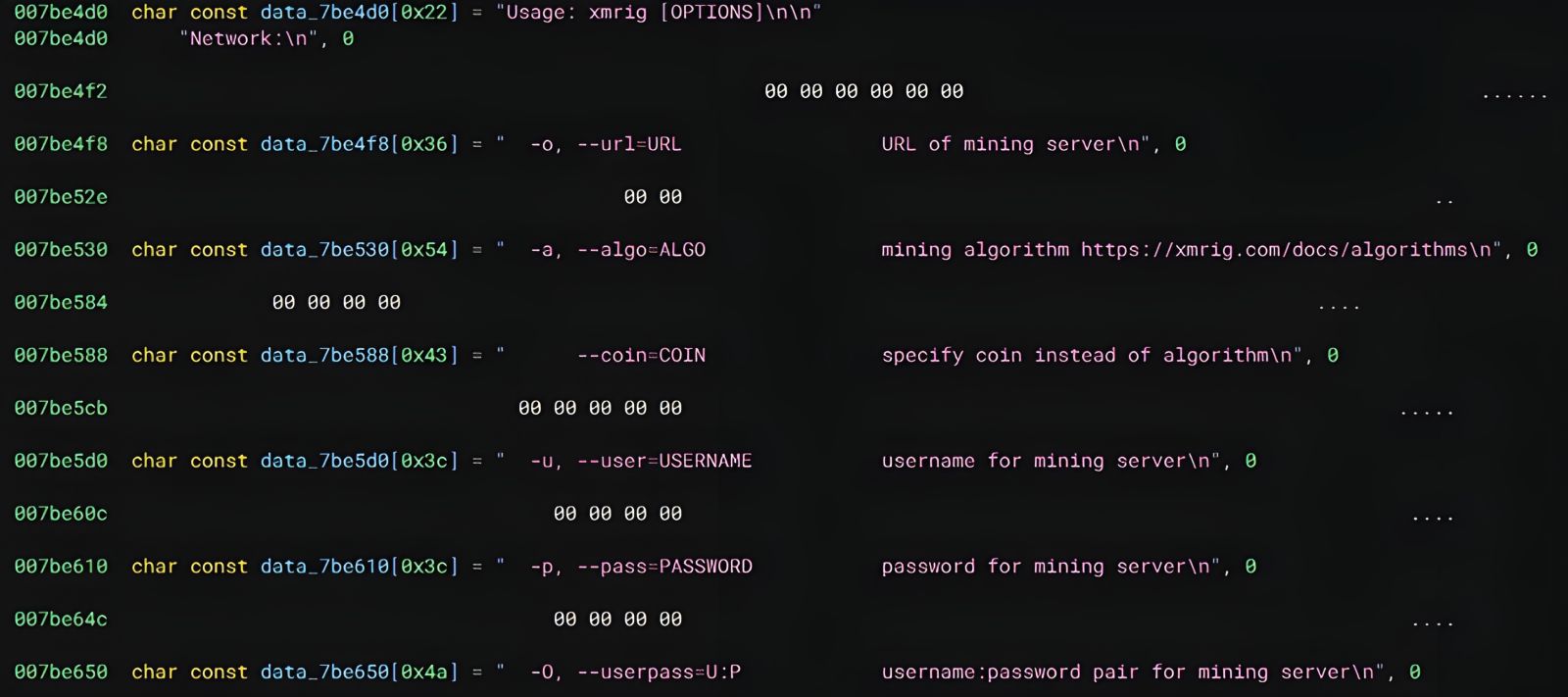
Figure 10: Snippet of the XMRig Miner code from sshd in BinaryNinja.
MITRE ATT&CK Framework Mapping
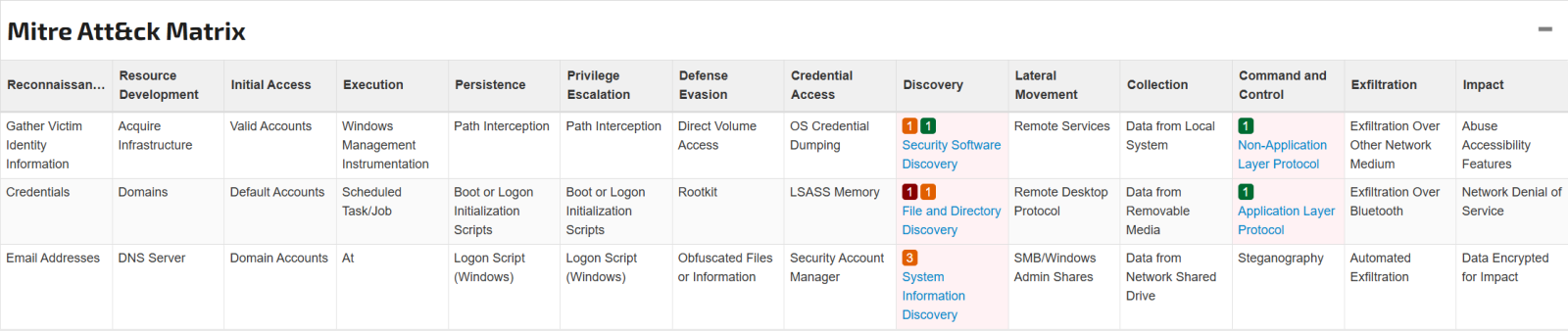
Figure 11: MITRE ATT&CK matrix for sshd [18].
bioset
The bioset binary establishes a reverse shell allowing the attacker to interact with the system remotely. Bioset uses multiple tools from GitHub repositories including:
Go-Daemon- “Library for writing system daemons in Go [19].”
Platypus- “A modern multiple reverse shell sessions/clients manager via terminal written in go [16].”
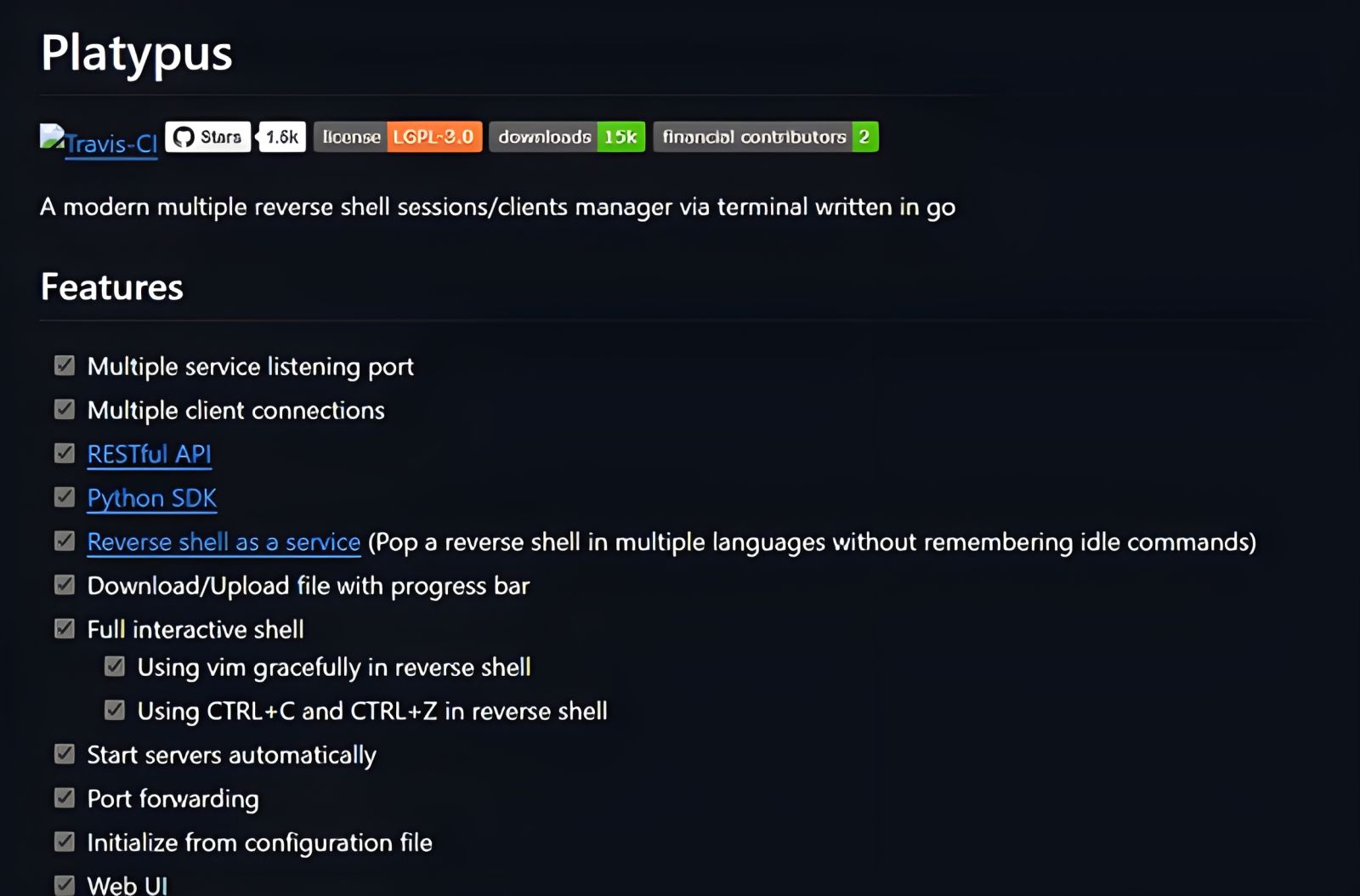
Figure 12: Features of the Platypus reverse shell tool [16].
- “A modern multiple reverse shell sessions/clients manager via terminal written in go [16].”
Xz- “This Go language package supports the reading and writing of xz compressed streams [20].”
Pty- “Pty is a Go package for using unix pseudo-terminals [21].”
Go-socks5- “Provides the socks5 package that implements a SOCKS5 server. SOCKS (Secure Sockets) is used to route traffic between a client and server through an intermediate proxy layer. This can be used to bypass firewalls or NATs [22].”
Freeport- “Get a free open TCP port that is ready to use [23].”
When looking at the code in BinaryNinja, the reverse shell reaches back to m[.]9-9-8[.]com over port 14447.

Figure 13: Snippet of the bioset code showing the reverse shell destination and port
MITRE ATT&CK Framework Mapping
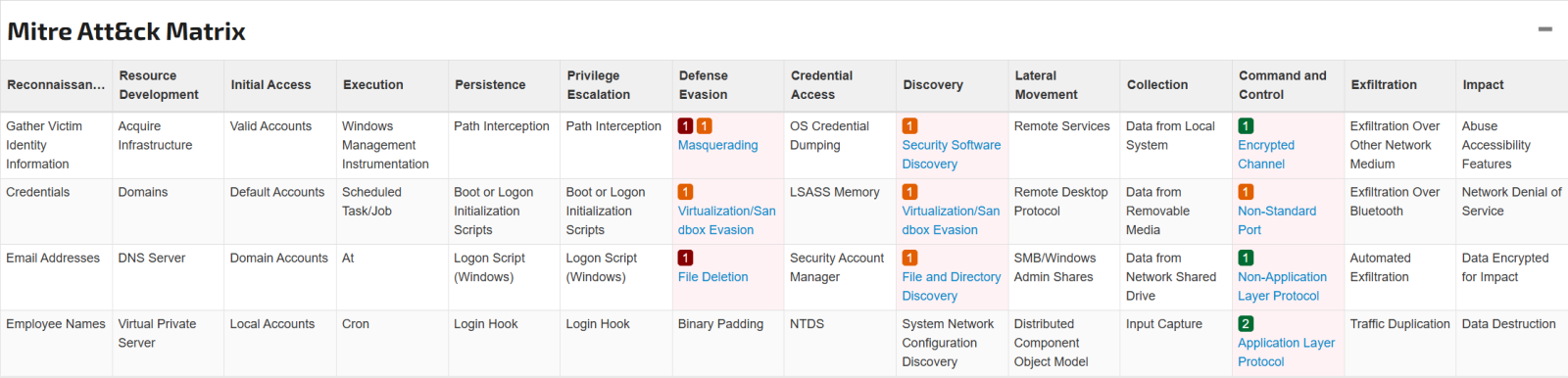
Figure 14: MITRE ATT&CK matrix for bioset [24]
References
[1] https://www.sans.edu/cyber-security-programs/bachelors-degree/
[2] M. Muir, "CADO Security," 6 March 2024. [Online]. Available: https://www.cadosecurity.com/blog/spinning-yarn-a-new-linux-malware-campaign-targets-docker-apache-hadoop-redis-and-confluence. [Accessed 5 December 2024].
[3] Joe Sandbox, "Linux Analysis Report - w.sh," 07 03 2024. [Online]. Available: https://www.joesandbox.com/analysis/1404813/0/html#mitre-pagination. [Accessed 05 12 2024].
[4] C. Will Thomas and C. Darin Smith, "MITRE ATT&CK," [Online]. Available: https://attack.mitre.org/groups/G0139/.
[5] M. Project, "Malpedia," [Online]. Available: https://malpedia.caad.fkie.fraunhofer.de/actor/teamtnt.
[6] Cloudsek, "Cloudsek," [Online]. Available: https://www.cloudsek.com/threatintelligence/timeline-ttps-of-teamtnt-cybercrime-group.
[7] S. Bharti, "TeamTNT Returns - Or Does It?," 19 10 2022. [Online]. Available: https://www.trendmicro.com/en_us/research/22/j/teamtnt-returns-or-does-it.html. [Accessed 5 12 2024].
[8] Geeks for Geeks, "gcc command in linux with examples," 21 11 2021. [Online]. Available: https://www.geeksforgeeks.org/gcc-command-in-linux-with-examples/. [Accessed 09 12 2024].
[9] lucasdemarchi, "kmod-project," 30 06 2022. [Online]. Available: https://github.com/kmod-project/kmod. [Accessed 09 12 2024].
[10] Phoenix NAP Global IT Services, "Linux make Command," 23 10 2024. [Online]. Available: https://phoenixnap.com/kb/linux-make-command. [Accessed 09 12 2024].
[11] Gentoo Linux, "Linux-headers," [Online]. Available: https://wiki.gentoo.org/wiki/Linux-headers. [Accessed 09 12 2024].
[12] Offensive Security, "net-tools," [Online]. Available: https://www.kali.org/tools/net-tools/. [Accessed 09 12 2024].
[13] Offensive Security, "masscan," [Online]. Available: https://www.kali.org/tools/masscan/. [Accessed 09 12 2024].
[14] Offensive Security, "pnscan," [Online]. Available: https://www.kali.org/tools/pnscan/. [Accessed 09 12 2024].
[15] Apache, "httpd - Apache Hypertext Transfer Protocol Server," [Online]. Available: https://httpd.apache.org/docs/2.4/programs/httpd.html. [Accessed 09 12 2024].
[16] W. Yihang, "Platypus," 16 07 2021. [Online]. Available: https://github.com/WangYihang/Platypus. [Accessed 06 12 2024].
[17] Joe Sandbox, "Linux Analysis Report - y0YuUxDd.sh.part," 06 03 2024. [Online]. Available: https://www.joesandbox.com/analysis/1404305/0/html#mitre-pagination. [Accessed 06 12 2024].
[18] Joe Sandbox, "Joe Sandbox - Linux Analysis Report sshd," [Online]. Available: https://www.joesandbox.com/analysis/1568671/0/html#mitre-pagination. [Accessed 06 12 2024]
[19] sevlyar, "go-daemon," 08 07 2022. [Online]. Available: https://github.com/sevlyar/go-daemon. [Accessed 09 12 2024].
[20] ulikunitz, "xz," [Online]. Available: https://github.com/ulikunitz/xz/. [Accessed 09 12 2024].
[21] creack, "pty," [Online]. Available: https://github.com/creack/pty. [Accessed 09 12 2024].
[22] armon, "go-socks5," [Online]. Available: https://github.com/armon/go-socks5. [Accessed 09 12 2024].
[23] phayes, "freeport," [Online]. Available: https://github.com/phayes/freeport. [Accessed 09 12 2024].
[24] Joe Sandbox, "Linux Analysis Report - bioset," [Online]. Available: https://www.joesandbox.com/analysis/1568738/0/html#mitre-pagination. [Accessed 06 12 2024].
[25] m0nad, "m0nad/Diamorphine," 09 2023. [Online]. Available: https://github.com/m0nad/Diamorphine. [Accessed 05 12 2024].
[26] Threat Insights Portal, "Threat Insights Portal -ar.sh," 11 11 2024. [Online]. Available: https://tip.neiki.dev/file/64d8f887e33781bb814eaefa98dd64368da9a8d38bd9da4a76f04a23b6eb9de5/content. [Accessed 06 12 2024].
--
Jesse La Grew
Handler
如有侵权请联系:admin#unsafe.sh