November 27, 2024 5 Minute Read 2024-11-27 22:0:0 Author: www.trustwave.com(查看原文) 阅读量:10 收藏
5 Minute Read
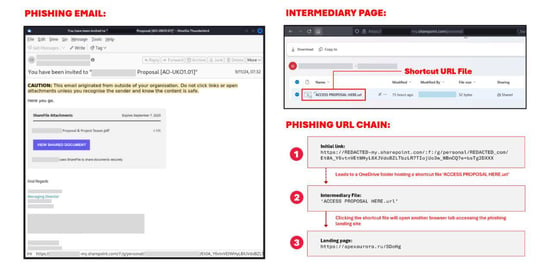
Welcome to the second part of our investigation into the Rockstar kit, please check out part one here. This blog tackles real-world Rockstar 2FA email examples incorporating noteworthy techniques. The Rockstar platform highly promotes its capability to generate fully undetectable (FUD) links in phishing campaigns. These FUD links are specifically crafted to evade URL-based detection systems, which usually only examine the initial link to determine malicious intent. Common examples include the use of link redirectors (such as shortened URLs, open redirects, URL protection services, or URL rewriting services), the abuse of email marketing services, and other legitimate and trusted sites to host phishing content or perform redirection. I. Microsoft: OneDrive Trustwave SpiderLabs detected a new method of URL redirection involving OneDrive to host URL shortcut files. In Figure 1, the campaign abuses URL shortcut (.url) files linked to Rockstar 2FA. The message arrived as a ShareFile notification for a project proposal document. The initial link uses OneDrive, which this format can recognize: Accessing it will lead to the OneDrive folder hosting a shortcut file named ‘ACCESS PROPOSAL HERE.url’. A shortcut file, when clicked, redirects the victim to a specific webpage. In this case, unsuspecting users who click on the .url file are automatically redirected to the phishing landing page via a new browser tab. This technique offers seamless redirection and hides the actual destination URL from the user. II. Microsoft: OneNote Here is another Microsoft platform abused in Rockstar 2FA campaigns to host phishing links. The message example shown in Figure 2 used a document-themed lure with the subject line "Complete review of contract." The text seen in the email body is actually contained in an image. The image is anchored with a link to a OneNote document hosted on the 1drv[.]ms domain. This image-based approach helps attackers evade text-based detection mechanisms. This is a common technique that is still seen in phishing samples today. Users will be redirected to a OneNote page entitled “Complete Document for Review”. This webpage displays an Adobe PDF logo and a text hyperlink that leads to the phishing landing page. Microsoft’s Dynamics 365 Customer Voice is a feedback management platform that is used to track customer metrics. Unfortunately, it has been actively abused in phishing attempts as a malicious link stager. Another popular platform that we spotted being abused as a phishing link stager is Atlassian Confluence. Confluence is a collaboration platform commonly known for its web-based corporate wiki functionality. In Figure 4, an email was crafted to look like a shared Microsoft Excel document notification. It urges users to click on a link labeled “STIAHNUT’ DOKUMENT” which translates from Slovak as ‘download the document’. However, clicking this link directs users to a Confluence wiki page, which is not associated with Microsoft. Once accessed, the Confluence page displays another link that leads to the malicious landing page impersonating the Office 365 login page. Figure 5 shows another variant of a document sharing theme. A Google Docs Viewer link in the email is used to render a malicious PDF file hosted on an external site. This Google service acts as a loader for malicious PDFs. Phishers have started abusing this feature that allows users to embed PDF and PowerPoint files in a webpage. The URL format is: Figure 6 shows a phishing email sent from a compromised sender account. In this case, threat actors hijacked a teacher’s account and used it to deliver payment-related phishing emails. The attacks were sent to contacts of the compromised account, making it more convincing since it comes from a known and trusted source. The message contains a link that takes users to a legitimate external website, ladesk.com, a platform for customer helpdesk services. Like previously mentioned platforms, LiveAgent has been exploited to host Rockstar 2FA phishing links. QR phishing, also known as Quishing, remains a popular technique attackers use in phishing campaigns. It is particularly effective because instead of embedding a visible link, the URL is encoded within a QR code, which can be placed in the email body or in attachments. This method often bypasses traditional detection systems that focus on visible links. Figure 7 shows a sample email impersonating DocuSign and using a QR code to redirect users to a landing site linked to Rockstar. The message only contains a PDF attachment mimicking a DocuSign interface with a QR code. It includes instructions urging users to scan the code using a smartphone camera to electronically sign the document, a social engineering attempt to trick users into scanning the code. Phishers sometimes incorporate previously stolen email thread discussions to inflate the size of their emails. In this approach, the phishing email is not sent from the account from which the stolen threads are sent. Also, the topic of the added email thread may not coincide with the matter raised by the email's sender. The email sample shown in Figure 8, which imitates an IT password expiration email, is in English. In contrast, the discussion in the latter part of the email is in French and for a completely different subject matter. The source code of the HTML attachment or HTML message body is employed with syntax-based obfuscations. This approach aims to evade detection methods that rely on keyword matching. The HTML code is split into tokens, and words like the phishing URL are split into arrays. Comments and hidden HTML elements are inserted in between code elements to further obscure the source code. Email campaigns from the Rockstar PaaS kit highlight the need to be cautious of emails sent through legitimate platforms and clicking associated links. Threat actors are increasingly using them as FUD links, taking advantage of the trust that comes with legitimate platforms. SpiderLabs noted the attacks utilizing Rockstar leverage multi-stage phishing chains where the phishing attack is carried out in multiple phases. This layered approach exploits various legitimate services to host malicious links or act as redirectors designed to evade detection further and conceal phishing pages from email gateways. Part of the offerings of this kit is the inclusion of randomized attachments in phishing emails. In our traps, PDF, HTML, and MS Office documents are the files most abused by this kit. Fake documents are often well crafted and are aligned with the email theme. PDF and Office documents act as redirectors, containing links or QR codes that lead to the next-stage phishing link. Meanwhile, HTML attachments also act as redirectors or standalone landing pages. IOCs: Initial and/or Intermediary Links: Landing Pages: AiTM Server Domains:Legitimate Services Abused in FUD Link Feature
https://[TenantName]-my.sharepoint.com/personal/[UserPrincipalName]
Figure 1. URL shortcut files linked to Rockstar 2FA.
Figure 2. Document-themed phishing email where the entire email body content is contained in an image to evade text-based detection mechanisms.
III. Microsoft: Dynamics 365 Customer Voice
Figure 3. Malicious actors abuse Dynamics 365 Customer Voice in phishing attacks.
IV. Atlassian: Confluence
Figure 4. The phishing email leads to a malicious Confluence wiki page that redirects to the phishing landing page.
V. Google: Docs Viewerhttps://docs.google.com/viewerng/viewer?url=[insert URL].
Figure 5. Malicious actors abuse Google Docs Viewer to embed a malicious PDF that contains a link to the phishing landing page.
VI. LiveAgent: ladesk.com
Figure 6. A hijacked sender account was used to send out phishing emails using LiveAgent’s ladesk.com.Prevalent Use of QR Codes as Phishing Link Containers

Figure 7. A phishing email that has a malicious QR code in the PDF attachment. When scanned, the QR code will lead to a phishing landing page.Insertion of Stolen Email Threads in the Message Body

Figure 8. Malicious actors inflate the size of their phishing emails with previously stolen email threads.Obfuscations in HTML

Figure 9. Malicious actors evade detection with syntax-based obfuscation techniques.Conclusion
hxxps[://]redacted-my[.]sharepoint[.]com/:f:/g/personal/redacted_co_uk/Et0A_Y6vtnVEtWHyL8XJVdoBZLTbzLR7TIojUo3w_WBnCQ?e=bsTg2Dhxxps[://]1drv[.]ms/o/s!Ar8dxVBUvGlGiIgzb0_10Zq_e9ysmQhxxps[://]emea[.]dcv[.]ms/5IgHbcWimlhxxps[://]customervoice[.]microsoft[.]com/Pages/ResponsePage[.]aspx?id=y8WYKByhAE-PQmCpBHM28YWYrIrntjdJiNDbsLTiwthUNEIySFJCSVBaRkxaVzYzSk0xUEJZN1RPWi4uhxxps[://][redacted][.]atlassian[.]net/wiki/external/ZWQxMzM2MDdmMTEwNDk5NDgwZGNlZDJkZmNkOTE4ZmYhxxps[://]docs[.]google[.]com/viewerng/viewer?url=hxxps[://]quedi[.]adv[.]br/N2[.]pdfhxxps[://][redacted][.]ladesk[.]com/XXXXXXX-SECURE-BUSINESS-DOCUMENTShxxps[://]weathered-waterfall-4976[.]tekot88473[.]workers[.]dev/?e=<email>hxxps[://]luthschoenmode[.]nl/winkel/generated/arull[.]php?7104797967704b536932307466507a53784b7a4d37494c79704b7a4d73723053744f3145764f7a39565044764a784b64494841413d3d1hxxps[://]www[.]arceva[.]site/uploads/images/24_01/pbcmc[.]php?0096797967704b53693230746376793079703145334f7953394e7964524c7a732f564b386a524e7a514f4474414841413d3d<email>
hxxps[://]apexaurora[.]ru/SDoHg/hxxps[://]swiftsparkmon[.]ru/F4CQo/hxxps[://]54774675[.]rainblessings[.]pages[.]devhxxps[://]saluminyum[.]com/secure/index[.]htmlhxxps[://]vilug-onteroi[.]com[.]pl/RkHd/hxxps[://]urbanlifeinnolo[.]ru/KGgthxxps[://]vendantacoursessonu[.]ru/7VINmhxxps[://]vidy-cloudy[.]com[.]pl/13SP
cotsworld[.]com[.]rutxjudge-mentsol[.]com[.]pllifestreamtechho[.]ru
如有侵权请联系:admin#unsafe.sh