2024-11-29 23:36:24 Author: securityaffairs.com(查看原文) 阅读量:14 收藏
Phishing-as-a-Service Rockstar 2FA continues to be prevalent
Pierluigi Paganini
November 29, 2024

Phishing tool Rockstar 2FA targets Microsoft 365 credentials, it uses adversary-in-the-middle (AitM) attacks to bypass multi-factor authentication.
Trustwave researchers are monitoring malicious activity associated with Phishing-as-a-Service (PaaS) platforms, their latest report focuses on a toolkit called Rockstar 2FA.
Rockstar 2FA targets Microsoft 365 accounts and bypasses multi-factor authentication with adversary-in-the-middle (AitM) attacks.
In AiTM phishing, threat actors set up a proxy server between a target user and the website the user wishes to visit, which is the phishing site under the control of the attackers. The proxy server allows attackers to access the traffic and capture the target’s password and the session cookie.
The experts observed a phishing campaign targeting Microsoft 365 users with adversary-in-the-middle attacks that has surged since August 2024. A unique feature of the campaign is the use of car-themed web pages, with over 5,000 related domains identified since May 2024.
The Rockstar 2FA PhaaS is an updated version of the DadSec/Phoenix phishing kit.
“The revamped phishing kit is still operating under the PaaS model, with marketing and communications observed on ICQ, Telegram, and Mail.ru. With these platforms, the kit becomes easily accessible for other cybercriminals seeking to acquire easy-to-set up phishing tools.” reads the report published by Trustwave.
The subscription fee for the PhaaS is $200 for two weeks, $350 for a month, US$180 for a two-week API renewal service.
Authors advertise Rockstar 2FA as a phishing-as-a-service toolkit that bypasses 2FA, harvests cookies, and features FUD links, antibot tools, and custom themes.
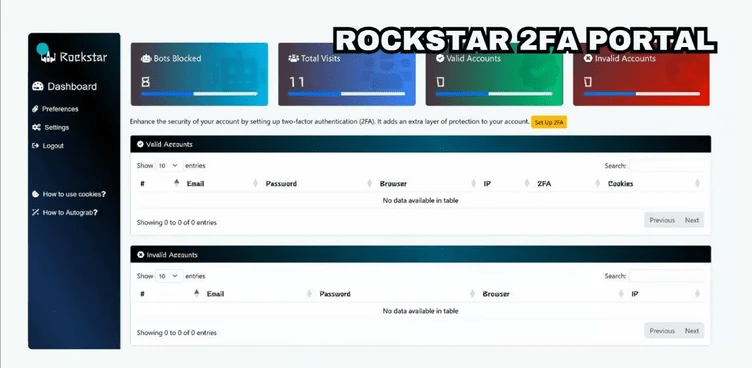
The Rockstar admin panel is user-friendly, it allows customers to track phishing activity, including visit stats and account validity, and offers tools like URL generators and customizable email themes.

Rockstar 2FA phishing campaigns use diverse themes, including file-sharing, HR notices, MFA lures, and account alerts. The toolkit evades detection with FUD links, obfuscation, and QR codes.
The Rockstar 2FA kit bypasses antispam detection with legitimate link redirectors and uses Cloudflare Turnstile antibot checks to prevent automated page analysis.

Trustwave observed threat actors using trusted services like Atlassian Confluence, Google Docs Viewer, and Microsoft OneDrive to host phishing links.
“Commodity phishing attacks, such as campaigns linked to the Rockstar 2FA PaaS platform, continue to be prevalent due to their low cost and ease of deployment. With the integration of AiTM techniques, additional layers of security like MFA can be bypassed. The likelihood of secondary attacks, such as account takeovers, launching phishing campaigns using compromised accounts, or performing business email compromise (BEC) attacks, also increases.” concludes the report.
“Given the continued Rockstar-led phishing activities, it is more likely that the threat actors behind this PaaS will continue updating this kit or develop even more advanced phishing kits.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, phishing)
如有侵权请联系:admin#unsafe.sh