2024-11-18 16:50:37 Author: hackernoon.com(查看原文) 阅读量:0 收藏
Bitcoin blockchain is the first blockchain for the world's most valuable cryptocurrency, Bitcoin. The network continues to face persistent challenges in scaling and expanding its functionality to handle high transactions.
To tackle these persistent challenges, Bitcoin sidechains have emerged as a groundbreaking solution while maintaining network security and integrity.
In this article, you will understand the following:
- What are Sidechains?
- Understanding Bitcoin Sidechains
- Technical Architecture of Sidechains
- Notable Bitcoin Sidechains
- Use Cases and Applications of Bitcoin Sidechains
- Implementation Challenges
What are Sidechains?
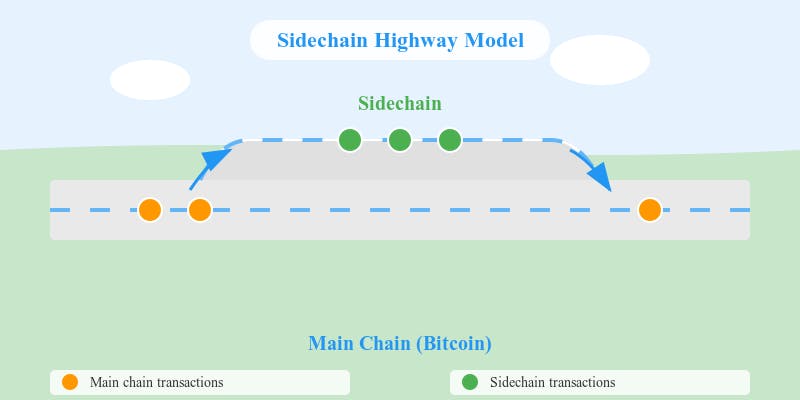
Sidechains are compared to side lanes on a highway that can alleviate congestion on the main highway (main chain), such as Bitcoin, handling transactions separately and then merging back to the main chain.
Adam Back, the CEO of Blockstream, proposed the idea of sidechains in a
white paper in 2014, along with other prominent crypto veterans.
Sidechains help make transactions faster and cheaper without compromising the security of the blockchain. They also let applications, like blockchain-based games, process high-volume transactions more efficiently and allow the transfer of assets (cryptocurrencies) back to the main blockchain.
They improve blockchain performance, though they require careful security measures, as sidechains bear responsibility for their security.
Understanding Bitcoin Sidechains
Bitcoin Sidechains are independent or secondary blockchains that run parallel to the Bitcoin mainchain. They enable assets to move securely between chains through a
The two-way peg system operates through a lock-and-mint mechanism:
-
When moving assets to a sidechain, bitcoins are locked on the main chain
-
An equivalent representation is minted on the sidechain
-
The process can be reversed to return assets to the main chain
These transfers typically require cryptographic proofs (like SPV proofs) to verify the lock/unlock operations between chains. This helps maintain security and prevents double-spending.
Unlike Layer 2 solutions such as the Lightning Network, sidechains are considered scaling solutions and maintain their consensus mechanisms and security models, offering greater flexibility in feature implementation.
Technical Architecture of Sidechains
The technical architecture of sidechains is a complex system that integrates various components to create secure and functional blockchain extensions. At its core, the sidechain protocol design aims to balance innovation with compatibility with Bitcoin's base layer. This is achieved through a modular approach to consensus rules and transaction processing, allowing customization while maintaining essential Bitcoin-like characteristics.
Sidechains implement specialized consensus mechanisms tailored to their specific use cases. For instance, a sidechain focused on high-frequency trading might employ a
These mechanisms are complemented by custom block validation rules that extend beyond Bitcoin's standard rules. These rules support advanced features like additional opcodes for smart contracts, modified block sizes, and specialized validation logic for new transaction types.
Cross-chain communication is a critical component of sidechain architecture, enabling seamless asset transfers while maintaining security. This process involves a sophisticated proof system, typically utilizing Simplified Payment Verification (SPV) proofs.
When assets move between chains, a series of steps occur, including creating transactions, generating cryptographic proofs, and validating against consensus rules. Atomic swaps and transfers are implemented through hash-locked contracts to ensure transaction integrity. At the same time, state synchronization is maintained through regular checkpoints, Merkle root comparisons, and consensus-level validation of cross-chain state updates.
Security models in sidechains vary based on specific requirements and trust assumptions. Merged mining with Bitcoin allows sidechains to leverage Bitcoin's existing mining infrastructure, inheriting a significant portion of its hash power.
The federation-based consensus relies on a predetermined set of trusted validators, often employing multi-signature schemes and regular rotation of federation members. Hybrid security models combine multiple approaches for more robust security guarantees, including elements of proof-of-work, proof-of-stake, and federated validation.
These components work together to create a flexible, secure, and efficient sidechain ecosystem that extends Bitcoin's functionality while maintaining its core principles of security and decentralization.
Notable Bitcoin Sidechain Projects
Rootstock
Rootstock (RSK) stands out as a remarkable achievement in Bitcoin sidechain technology. It offers smart contract functionality while maintaining Bitcoin's security through an innovative merged mining approach. As a sidechain, Rootstock operates parallel to Bitcoin, allowing users to transfer assets between the two networks.
Earlier, the Rootstock network worked on a federated peg mechanism that was centralized, but today, it has advanced to a PowPeg mechanism. PowPeg uses specialized devices called PowHSMs (Proof of Work Hardware Security Modules) to protect private keys.
These devices are designed to be tamper-proof, meaning they are resistant to unauthorized access or attacks. It facilitates the seamless transfer of Bitcoin (BTC) to Rootstock's native token, RBTC (Smart Bitcoin), and vice versa.
This peg ensures that RBTC maintains a 1:1 value with BTC, allowing users to utilize their Bitcoin within the Rootstock ecosystem without creating a competing token. The PowPeg system involves multiple signatories who control access to the locked BTC, enhancing security and decentralization.
Assets are transferred to the sidechain using a peg-in and peg-out process. To understand the peg-in and peg-out process, here is an example below:
Peg-in Process: Transferring BTC to RBTC
-
User Decision: Imagine Sarah wants to use her Bitcoin (BTC) on the Rootstock network to access decentralized applications and smart contracts.
-
Initiating Peg-in: Sarah decides to convert her 1 BTC into RBTC (Rootstock Bitcoin). To do this, she sends her 1 BTC to a designated wallet address. This address is a multi-signature wallet managed by PowPeg functionaries.
-
Informing the Bridge: After sending her Bitcoin, Sarah needs to notify the PowPeg system (often referred to as the Bridge) about her transaction. This notification is crucial because it tells the system that she has initiated a peg-in.
-
Verification by Functionaries: The PowPeg functionaries act as watchtowers, monitoring the Bitcoin network for Sarah's transactions. Once they confirm that her Bitcoin has been successfully sent to the address, they proceed with the next step.
-
Issuing RBTC: After verification, the PowPeg functionaries issue Sarah 1 RBTC on the Rootstock network. This RBTC is now available for her to use in various applications on Rootstock, ensuring a 1:1 relationship with her original Bitcoin.
Peg-out Process: Returning RBTC to BTC
-
User Decision: Later, Sarah decides she wants to convert her RBTC back into Bitcoin so she can withdraw it to her wallet.
-
Initiating Peg-out: Sarah requests a peg-out by notifying the Bridge that she wants to exchange her 1 RBTC for Bitcoin.
-
Verification and Processing: The Bridge verifies that Sarah holds 1 RBTC in her account on Rootstock and prepares a peg-out transaction. This involves checking that all conditions are met for a successful transaction.
-
Building the Bitcoin Transaction: After confirming that Sarah's request is valid, the Bridge constructs a Bitcoin peg-out transaction, commanding the PowHSMs to sign it.
-
Releasing Bitcoin: Once signed by the necessary PowHSMs, the Bridge executes the peg-out transaction, releasing 1 BTC back to Sarah’s original Bitcoin address.
-
Completion: After sufficient confirmations on the Bitcoin network, Sarah can check her wallet and see that her 1 BTC has been successfully returned.
Liquid Network
The Liquid Network is an innovative sidechain solution built on top of the Bitcoin blockchain, designed to enhance Bitcoin's functionality and address some of its limitations.
It was developed by
One of the key features of the Liquid Network is its ability to process transactions more rapidly than the Bitcoin mainchain. While Bitcoin typically requires about ten minutes for block confirmation, Liquid can achieve settlement finality within two minutes. This increased speed is made possible by the network's unique consensus mechanism, which relies on a federation of trusted participants rather than a proof-of-work mechanism.
Liquid introduces its native asset called Liquid Bitcoin (L-BTC), which is pegged 1:1 with Bitcoin. Users can convert their BTC to L-BTC through a process called pegging-in, allowing them to take advantage of Liquid's features while maintaining the value of their Bitcoin holdings.
The network also supports the issuance of other digital assets, including stablecoins, security tokens, and even non-fungible tokens (NFTs), expanding the possibilities for Bitcoin-based decentralized finance (DeFi).
Privacy is another significant aspect of the Liquid Network. It implements confidential transactions, which mask the amounts and types of transferred assets, providing users with enhanced financial privacy compared to the transparent nature of the Bitcoin blockchain. This feature attracts institutional investors and traders who require discretion in their transactions.
While the Liquid Network offers numerous benefits, it's important to note that it sacrifices some degree of decentralization compared to the Bitcoin mainchain. The network's security and operation rely on a federation of members, which includes exchanges and other Bitcoin-focused companies. This trade-off allows for greater speed and functionality but introduces a level of trust not present in Bitcoin's fully decentralized model.
The Liquid Network represents a pragmatic approach to scaling Bitcoin and extending its capabilities, particularly for use cases that require rapid settlement, privacy, and asset issuance.
Use Cases and Applications of Bitcoin Sidechains
Bitcoin sidechains enable a wide range of applications previously unavailable on the main network:
-
Decentralized Finance (DeFi): Protocols like Sovryn, built on Rootstock, allow users to trade, borrow, lend, and stake in directly on Bitcoin, thus integrating Bitcoin into the broader DeFi ecosystem
-
Non-Fungible Tokens (NFTs): Sidechains with smart contract support enable the creation and trading of NFTs representing digital art, collectibles, and other assets.
-
Smart Contracts: Bitcoin sidechains support advanced smart contracts, which are not natively available on the Bitcoin mainchain. RSK allows developers to utilize Ethereum-compatible smart contracts, enabling a wide range of functionalities from complex financial instruments to automated agreements. This capability opens up new avenues for innovation, allowing developers to create sophisticated dApps that leverage Bitcoin's value and Ethereum's programmability.
-
Asset Tokenization: Platforms like the Liquid Network support the tokenization of various assets, including securities and physical goods.
Implementation Challenges
While sidechains offer numerous benefits, they also come with certain challenges:
-
Security Trade-offs: Sidechains typically have their security models, which may not be as robust as the main Bitcoin network.
-
Centralization Risks: Some sidechains, like the Liquid Network, operate on federated, introducing elements of centralization.
-
Adoption Hurdles: The complexity of using sidechains may pose barriers to widespread adoption among less technical users.
Wrap Up
Bitcoin sidechains represent a crucial development in the evolution of blockchain technology, offering a pathway to enhanced functionality while preserving the security and stability of the main Bitcoin network. As the ecosystem advance, we can expect to see:
- Increased adoption of sidechain solutions
- Greater interoperability between different chains
- Enhanced security models
- Expanded use cases and applications
Sidechains will be a crucial component in Bitcoin's journey toward becoming a more versatile and scalable blockchain.
Editor’s note: This article is for informational purposes only and does not constitute investment advice. Cryptocurrencies are speculative, complex, and involve high risks. This can mean high prices volatility and potential loss of your initial investment. You should consider your financial situation, investment purposes, and consult with a financial advisor before making any investment decisions. The HackerNoon editorial team has only verified the story for grammatical accuracy and does not endorse or guarantee the accuracy, reliability, or completeness of the information stated in this article. #DYOR
如有侵权请联系:admin#unsafe.sh

