Microsoft is on the front lines helping secure customers worldwide—analyzing and responding to cybe 2024-11-7 01:0:0 Author: www.microsoft.com(查看原文) 阅读量:9 收藏
Microsoft is on the front lines helping secure customers worldwide—analyzing and responding to cybersecurity threats, building security technologies, and partnering with organizations to effectively deploy these technologies for increased security. Many of you have been following as we’ve described our Secure Future Initiative, which is pushing the Zero Trust principles verify explicitly, least privilege and assume breach into the programmatic approach of Secure by Design, Secure by Default, and Secure Operations across Microsoft consistently, durably and at scale. In the Microsoft Security division, we are also focused on helping our customers deploy our suite of security products to protect themselves from cyber threats. We know that most of our customers are embarking on a Zero Trust journey, but many struggle with the enormity of the opportunity: where to start, what to do next, and how to measure progress.
We are announcing a resource to help our customers answer these questions: The Microsoft Zero Trust Workshop, a self-service tool to help you plan and execute your Zero Trust journey guide by yourself or with the guidance of a partner.
The Zero Trust Workshop lets you customize your organization’s end-to-end security deployment to your unique business needs and your environment with a powerful tool that: provides a comprehensive assessment of zero trust capabilities learned from hundreds of deployments; guides you with a visual easy-to-use tool that explains each step of the journey; and delivers a digital artifact that you and your team can use to plan and prioritize your next steps and to compare and measure progress regularly.

Zero Trust Workshop
A comprehensive technical guide to help customers and partners adopt a Zero Trust strategy and deploy security solutions end-to-end to secure their organizations.
How our workshop helps customers and partners solidify their Zero Trust strategy
Over the past year, we have piloted this workshop with more than 30 customers and partners. They have consistently told us that this provides them with the clarity, coverage, and actionable guidance they need to secure their organization within each Zero Trust pillar and across the pillars. When asked how likely they are to recommend the workshop to their partner teams or to other customers, customers give the workshop a net promoter score of 73.
The layout and question structure is fantastic as it provokes a fair amount of thought around adding each of the capabilities to take a multi-faceted approach to authentication and authorization.
—Senior vice president at a major financial institution
Security is a team sport, and we recognize that customers often need security partners to help them plan and execute their security strategy. This is why we partnered with several deployment partners across the pillars of Zero Trust to get their feedback on the workshop and how they would use it to help their customers.
The Zero Trust Workshop is a great starting point for our customers who want to embrace Zero Trust principles, but don’t know how to align the technology they already own. Furthermore, the workshop allows our customers to measure the progress they’ve made and aim for the next incremental hardening of the Zero Trust model, which is part and parcel of the Zero Trust manner of thinking. As a Microsoft partner and as an MVP, I advocate that customers use the materials provided by Microsoft, including these workshops, to measure and further their security posture.
—Nicolas Blank, NBConsult
[The Zero Trust workshop] has enabled Slalom to help clients accelerate their efforts towards a comprehensive cyber resilience strategy. It provides a clear picture of an organization’s current state and provides a template for order of operations and best practices in a very tidy package. It’s an easy-to-use tool with a huge impact, and our clients and workshop participants have been very impressed by how it organizes and prioritizes a complex set of operations in an approachable and manageable way.
—Slalom
How to start using the workshop to plan your Zero Trust journey
The Zero Trust Workshop is comprised of two main components, all in one handy file you can download and use to drive these conversations:
- The Zero Trust Basic Assessment (optional): For customers starting on their Zero Trust journey, the assessment is a foundational tool that customers can run before the workshop to check for common misconfigurations and gaps in settings (for example, having too many global admins) to remediate before starting to enable the security features and capabilities of a Zero Trust journey.
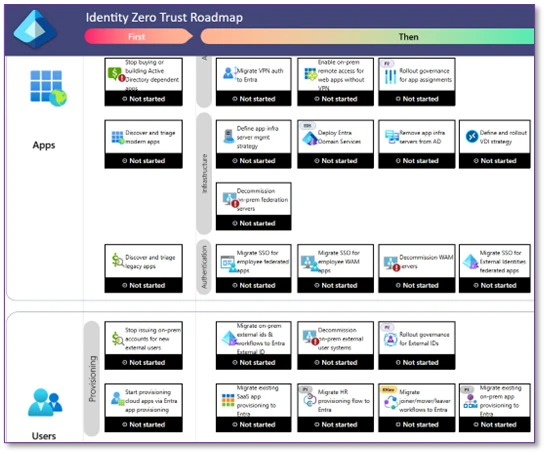
- The Zero Trust Strategy workshop: This is a guided breakdown of the Zero Trust areas according to the standard Zero Trust pillars (Identity, Devices, Data, Network, Infrastructure and Application, and Security Operations). For each pillar, we walk you through the associated areas with a proposed “do this first, consider this then, think about this next” order to how you should tackle them. For each area and capability, you have guidance on why it matters and options to address it and then can discuss it with your stakeholder and decide if this is something you already did, something you are going to do, or something you do not plan to implement at this time. As you progress through the different boxes and areas, you create an artifact for your organization on how well-deployed you are in this Zero Trust pillar and what are the next areas to tackle.
Now, we are launching the Identity, Devices, and Data pillars. We will add the Network, Infrastructure and Application, and Security Operations in the coming few months. The website for the workshop will announce these as they become available.



I invite you to check out the Zero Trust Workshop site where we have detailed training videos and content.
For our valued security deployment partners, the workshop is also included in the recently launched Zero Trust Partner kit where, as a partner, you can take the workshop material and customize it for your customer engagements based on your needs.
Closing thoughts
We all need to work together to help secure the world we live in and keep people safe with the intention of collective defense. As shared in the most recent Microsoft Digital Defense Report, the cyber threat landscape is ever-growing and requires a collaborative approach between product vendors, security experts, and customers to help protect everyone. In the spirit of working with the wider ecosystem to help secure all customers, we recently partnered with NIST’s NCCoE and more than 20 security vendors to publish a guide on how to adopt NIST’s Zero Trust reference architecture using Microsoft’s Security products and this is another example of us working with all of you deploying security out there to help secure the ecosystem.
We would love to hear how you are using it. Use the feedback form on the site to share with us how we can improve it to help your organization implement a Zero Trust journey.
Additional resources to accelerate your Zero Trust journey
This joins a library of other resources to guide your security modernization and Zero Trust journey, including:
- The Microsoft Security Adoption Framework (SAF) which includes the Microsoft Cybersecurity Reference Architecture and the Chief Information Security Officer (CISO) Workshop.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
如有侵权请联系:admin#unsafe.sh