2024-11-6 20:46:35 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
Imagine this: you’re all set to launch a new software update, and then—bam!—you find out there’s a security flaw that could put your entire customer base at risk. It’s a nightmare, right? Unfortunately, this kind of thing happens more often than you might think.
With cyber threats evolving faster than ever, it’s crucial to integrate penetration testing into your CI/CD pipeline. This isn’t just a nice-to-have; it’s essential for keeping your software secure and your customers safe. Let’s talk about why that matters!
Organizations are constantly seeking ways to enhance their security measures while maintaining agility and efficiency. The integration of Penetration Testing as a Service (PTaaS) with Continuous Integration/Continuous Deployment (CI/CD) pipelines represents a significant advancement in achieving this balance. This article explores how PTaaS can be effectively integrated into CI/CD workflows, enhancing security, streamlining processes, and fostering a culture of continuous improvement.
As organizations adopt DevOps practices, the need for robust security measures becomes paramount. CI/CD pipelines facilitate rapid development and deployment cycles, but they also introduce new vulnerabilities if security is not prioritized. Traditional penetration testing methods, which often involve lengthy engagements and delayed reporting, are ill-suited for this dynamic environment. PTaaS offers a solution by providing continuous security assessments that integrate seamlessly into CI/CD workflows. This article will delve into the mechanics of this integration, its benefits, challenges, and best practices.
Understanding CI/CD Pipelines
CI/CD pipelines are automated processes that manage code changes throughout the software development lifecycle. They encompass two primary components:
- Continuous Integration (CI): This involves automatically merging code changes from multiple contributors into a shared repository. Automated builds and tests are triggered to ensure that new code does not introduce errors or vulnerabilities.
- Continuous Deployment (CD): This extends CI by automatically deploying code changes to production environments once they pass testing phases. This ensures that new features and fixes reach users quickly and efficiently.
Key Components of CI/CD Pipelines
A typical CI/CD pipeline includes several critical components:
- Source Code Management: Tools like Git manage version control and collaboration among developers.
- Build Automation: Tools such as Jenkins or CircleCI automate the building and testing of applications.
- Artifact Management: Repositories store build artifacts like Docker images or binaries.
- Deployment Automation: Platforms like Kubernetes or AWS facilitate automated deployment and scaling of applications.
Security Testing has evolved over the years
Traditional penetration testing faces several limitations in modern development:
- Time Constraints:
- Traditional penetration tests can take weeks to complete.
- Reports often arrive too late in the development cycle.
- Findings may become outdated by the time they are addressed.
- Resource Limitations:
- Testing can only be conducted infrequently.
- High costs associated with each engagement.
- Challenges in scaling testing efforts to keep pace with rapid development.
- Integration Challenges:
- Manual testing processes do not align well with automated workflows.
- Lack of real-time feedback impedes timely responses.
- Limited visibility into testing progress hampers overall effectiveness.
What is PTaaS?
PTaaS is an innovative approach to penetration testing that leverages automation and continuous assessment methodologies. Key benefits include:
- Continuous Testing: Organizations can perform penetration tests on-demand or at regular intervals, ensuring ongoing security assessments.
- Real-Time Reporting: Vulnerabilities are reported as soon as they are identified, allowing for immediate remediation.
- Scalability: PTaaS can scale with the organization’s needs without the constraints of traditional testing models.
The PTaaS Integration Model
1. Smart Security Gates
2. Intelligent Triggering System
Instead of performing full penetration tests for every change, PTaaS (Penetration Testing as a Service) platforms employ intelligent triggers based on:
- Change Analysis:
- Major version releases
- Modifications to authentication systems
- Introduction of new API endpoints
- Changes to infrastructure
- Updates to security-critical components
- Compliance Requirements:
- Regulatory deadlines
- Certification needs
- Industry standards
- Client-specific requirements
- Risk Assessment:
- Impact analysis
- Results from threat modeling
- Historical vulnerability patterns
- Criticality of assets
3. Parallel Processing Model
The key to maintaining development velocity while ensuring robust security lies in the implementation of a parallel processing model. This revision enhances clarity and professionalism while retaining the original intent.
Practical Implementation Strategies
1. Setting Up the Integration
1. Platform Selection:
- Choose PTaaS Platforms with Robust API Support: Select platforms that offer strong application programming interfaces (APIs) to facilitate seamless integration with your existing systems.
- Ensure Compatibility with Existing CI/CD Tools: Verify that the chosen PTaaS platform can work effectively with your current Continuous Integration/Continuous Deployment (CI/CD) tools to streamline workflows.
- Look for Real-Time Collaboration Features: Opt for platforms that provide features enabling real-time collaboration among team members, enhancing communication and efficiency during testing.
- Verify Reporting and Integration Capabilities: Assess the platform’s reporting features to ensure they meet your needs for tracking progress and integrating findings into your development cycle.
2. Process Definition:
- Define Clear Trigger Criteria: Establish specific criteria that will trigger security assessments, ensuring that all relevant changes are monitored effectively.
- Establish Security Gates: Create checkpoints within your development process where security assessments must be completed before moving forward, ensuring a proactive approach to security.
- Create Escalation Paths: Develop clear escalation procedures for addressing security issues that arise, allowing for timely responses to vulnerabilities.
- Set Up Communication Channels: Implement effective communication channels among team members to facilitate quick information sharing regarding security findings and remediation efforts.
3. Team Organization:
- Assign Security Champions: Designate team members as security champions who will advocate for security best practices within their respective teams and coordinate security efforts.
- Define Roles and Responsibilities: Clearly outline the roles and responsibilities of each team member involved in the integration process to ensure accountability and streamline efforts.
- Establish Communication Protocols: Create protocols for how team members will communicate about security issues, ensuring everyone is informed and aligned.
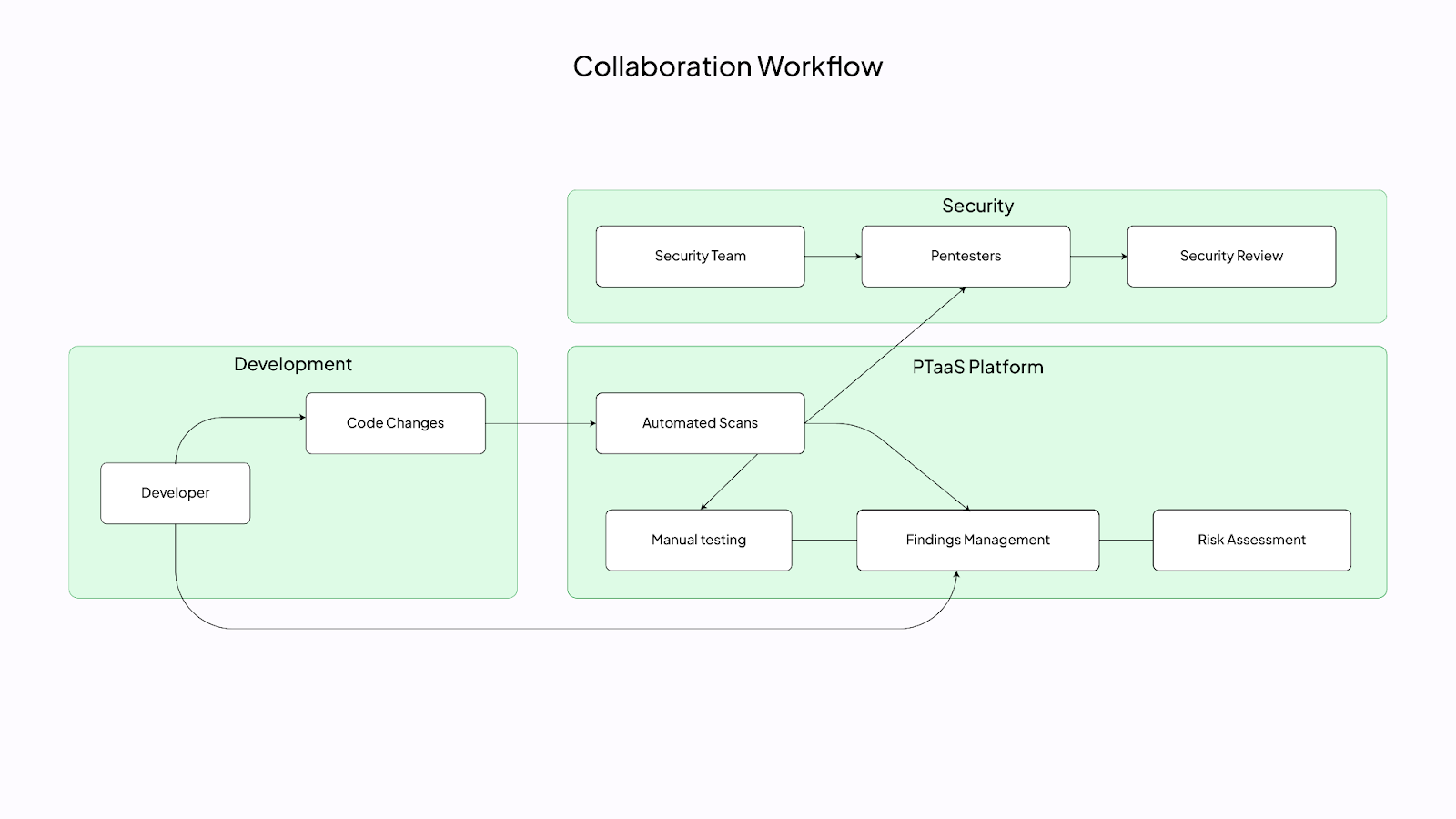
- Set Up Collaboration Workflows: Develop workflows that promote collaboration between development and security teams, facilitating a culture of shared responsibility for security.
2. Real-World Testing Workflows
1. Continuous Security Assessment:
- Automated Vulnerability Scanning: Implement automated tools to continuously scan for vulnerabilities in your codebase, ensuring ongoing protection against threats.
- Dependency Checking: Regularly check dependencies for known vulnerabilities, ensuring that all third-party libraries are secure and up-to-date.
- Configuration Validation: Validate configurations across environments to ensure they adhere to security best practices and do not introduce risks.
- Code Security Analysis: Conduct regular code reviews focused on security aspects, identifying potential vulnerabilities early in the development process.
2. Triggered Manual Testing:
- Full Penetration Testing: Schedule comprehensive penetration tests at key points in the development lifecycle to identify vulnerabilities that automated tools may miss.
- Focused Security Reviews: Conduct targeted reviews of specific components or features that have undergone significant changes or pose higher risks.
- Architectural Assessments: Evaluate the overall architecture of your application to identify potential security weaknesses at a systemic level.
- Compliance Validations: Ensure that your application meets relevant regulatory and compliance requirements through dedicated assessments.
3. Hybrid Approaches:
- Automated Preliminary Assessment: Use automated tools for initial assessments to quickly identify obvious vulnerabilities before manual testing begins.
- Manual Validation of Findings: Follow up on automated findings with manual testing to ensure accuracy and address any complex issues that require human expertise.
- Targeted Penetration Testing: Focus penetration testing efforts on high-risk areas identified during previous assessments, maximizing resource efficiency.
- Continuous Security Monitoring: Implement ongoing monitoring solutions to detect threats in real time, allowing for immediate response to potential incidents.
By following these detailed practical implementation strategies, organizations can effectively integrate PTaaS into their development processes while ensuring robust security measures are in place.
Advanced Integration Features
1. Collaboration and Communication
Modern PTaaS (Penetration Testing as a Service) platforms facilitate enhanced collaboration and communication through the following features:
1. Real-Time Interaction:
- Direct Communication Between Developers and Pentesters: PTaaS platforms enable immediate dialogue between development teams and penetration testers, fostering a collaborative environment.
- Immediate Clarification of Findings: Any vulnerabilities identified can be discussed in real time, allowing for quick clarification and understanding of the issues at hand.
- Quick Validation of Fixes: Once developers implement fixes, pentesters can promptly validate these changes, ensuring that vulnerabilities are effectively addressed.
- Continuous Feedback Loops: The ongoing interaction creates a feedback loop that helps teams iterate on security improvements swiftly.
2. Visibility and Tracking:
- Live Dashboards: PTaaS platforms often feature live dashboards that provide real-time visibility into testing progress and findings.
- Progress Monitoring: Teams can track the status of ongoing tests, allowing for better project management and resource allocation.
- Status Updates: Regular updates keep all stakeholders informed about the current state of security assessments.
- Metrics Tracking: Detailed metrics help assess the effectiveness of security measures and identify areas for improvement.
2. Risk-Based Assessment
PTaaS platforms utilize intelligent risk evaluation methods that consider both technical factors and business context:
1. Technical Factors:
- Vulnerability Severity: Assessing how critical each vulnerability is based on its potential impact on the system.
- Exploitability: Evaluating how easily a vulnerability can be exploited by an attacker.
- Technical Impact: Understanding the consequences of a successful exploit on the system’s functionality and data integrity.
- Attack Complexity: Analyzing the level of skill or resources an attacker would need to successfully exploit a vulnerability.
2. Business Context:
- Asset Criticality: Identifying which assets are most vital to business operations and prioritizing their protection.
- Data Sensitivity: Considering the sensitivity of the data involved, which may affect regulatory compliance and reputational risk.
- Business Impact: Evaluating how vulnerabilities could affect business operations, customer trust, and financial performance.
- Regulatory Requirements: Ensuring that assessments align with industry regulations and compliance standards to mitigate legal risks.
Benefits of Integrating PTaaS with CI/CD Pipelines
Enhanced Security Posture
Integrating PTaaS into CI/CD pipelines significantly enhances an organization’s overall security posture by ensuring continuous monitoring and assessment of applications throughout their lifecycle.
Faster Remediation Times
With real-time reporting and immediate feedback loops, organizations can remediate vulnerabilities quickly before they reach production environments.
Cost Efficiency
The shift from traditional pentesting to PTaaS reduces costs associated with lengthy engagements while providing more frequent assessments without additional overheads.
Improved Collaboration
The integration fosters collaboration between development and security teams, promoting shared responsibility for application security.
Challenges in Integration
Despite its advantages, integrating PTaaS with CI/CD pipelines presents several challenges:
Cultural Resistance
Transitioning to a DevSecOps model may face resistance from teams accustomed to traditional workflows where security is an afterthought rather than an integral part of development.
Tool Compatibility
Ensuring compatibility between existing tools and new PTaaS solutions can pose technical challenges that require careful planning and execution.
Resource Allocation
Organizations must allocate sufficient resources—both human and technological—to effectively manage ongoing penetration testing efforts alongside regular development activities.
Best Practices for Successful Integration
To maximize the benefits of integrating PTaaS with CI/CD pipelines, organizations should follow these best practices:
- Start Small: Begin by integrating PTaaS into specific stages of the pipeline before expanding its use across all workflows.
- Foster Collaboration: Encourage open communication between development, operations, and security teams to facilitate knowledge sharing and alignment on security goals.
- Provide Training: Equip developers with training on secure coding practices and how to address vulnerabilities identified during testing.
- Leverage Dashboards: Utilize dashboards provided by PTaaS platforms for visibility into vulnerability statuses and remediation efforts across teams.
Future Trends in PTaaS and CI/CD Integration
As organizations continue to evolve their software development practices, several trends are likely to shape the future of PTaaS integration with CI/CD pipelines:
Increased Automation
The role of automation in both penetration testing and CI/CD will continue to grow, enabling faster identification and remediation of vulnerabilities without significant manual intervention.
AI-driven Testing Solutions
Artificial intelligence will play a pivotal role in enhancing vulnerability detection capabilities within PTaaS platforms by analyzing vast amounts of data for patterns indicative of potential threats.
Greater Emphasis on Compliance
As regulatory requirements evolve, organizations will increasingly rely on integrated solutions like PTaaS within their CI/CD processes to demonstrate compliance with industry standards.
Strobes PTaaS: Enhancing Security in CI/CD Pipelines
Strobes PTaaS (Penetration Testing as a Service) is designed to provide organizations with a comprehensive, agile approach to security testing. By leveraging advanced methodologies and integrating seamlessly with existing development workflows, Strobes PTaaS enhances the security posture of applications while fostering collaboration between security and development teams.
Key Features of Strobes PTaaS
- Continuous Monitoring
- Strobes PTaaS offers relentless monitoring capabilities, ensuring that your digital assets are continuously assessed for vulnerabilities. This proactive approach allows organizations to identify emerging threats in real-time, maintaining defenses in a state of constant readiness.
- Comprehensive Coverage
- The platform covers a wide range of environments—including web applications, mobile apps, cloud infrastructures, and APIs—ensuring that no aspect of your digital ecosystem remains untested.
- Customized Testing
- Recognizing that every organization has unique security needs, Strobes PTaaS provides tailored testing methodologies. This customization ensures that assessments align with specific business objectives and security requirements.
- Real-Time Reporting and Feedback
- With Strobes PTaaS, vulnerabilities are reported as soon as they are identified. This immediate feedback loop allows developers to address issues quickly, minimizing exposure and enhancing overall security.
- Integrated Risk Scoring and Prioritization
- The platform employs advanced risk scoring techniques to categorize vulnerabilities based on their severity. This prioritization helps organizations focus remediation efforts on the most critical issues first.
Conclusion
Integration/Continuous Deployment (CI/CD) pipelines represents a transformative approach to application security in today’s fast-paced development environments. By embedding continuous security assessments into existing workflows, organizations can proactively identify vulnerabilities, enhance collaboration across teams, and significantly reduce remediation times.
As cyber threats continue to evolve, adopting such integrated approaches will be crucial for maintaining robust security postures while delivering high-quality software at speed. Organizations should evaluate their current processes against these capabilities and consider implementing strategies that align with their unique needs in order to thrive in an increasingly complex digital landscape.
The post Integrating Penetration Testing as a Service (PTaaS) with CI/CD Pipelines: A Practical Guide appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Akhil Reni. Read the original post at: https://strobes.co/blog/integrating-penetration-testing-as-a-service-ptaas-with-ci-cd-pipelines-a-practical-guide/
如有侵权请联系:admin#unsafe.sh

