2024-11-6 06:17:5 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Overview
Assura, Inc. has been made aware of this attack pattern, has taken steps to detect it in our managed services, and is following the attack in the blogs of security researchers who found this campaign. A recent phishing attack campaign has attackers installing a virtual machine (VM) on your Windows system, prebuilt with backdoors and tools for credential harvesting and data exfiltration while evading antivirus tools.
First, let’s look at how researchers believe the attack is executed. Phishing emails pretend to be a “OneAmerica survey, ” including a large 285 MB ZIP archive to install a Linux VM with a pre-installed backdoor.
This ZIP file contains a Windows shortcut named “OneAmerica Survey.lnk” and a “data” folder that contains the QEMU virtual machine application. The main executable is disguised as fontdiag.exe.
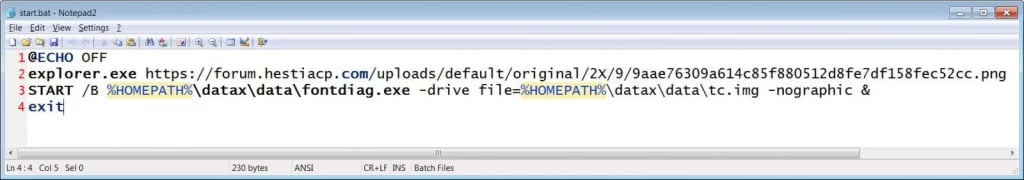
When the shortcut is launched, it executes a PowerShell command to extract the downloaded archive to the “%UserProfile%\datax” folder and then launches the “start.bat” to set up and launch a custom Linux virtual machine on the device.

Start.bat batch file installing the QEMU Linux virtual machine
Source: BleepingComputer
While the virtual machine is being installed, the same batch file will display a PNG file downloaded from a remote site that shows a fake server error as a decoy, implying a broken link to the survey.

Image showing fake error
Source: Securonix
Before we get ahead of ourselves, let’s back it up a little bit. So, what is QEMU and how can it be used maliciously?
In a nutshell, QEMU (Quick Emulator) is a legitimate, open-source virtualization tool that allows for emulating various hardware and processor architectures, enabling them to run different operating systems or applications in a virtualized environment. It can emulate processors like x86, ARM, and PowerPC, making it versatile for testing, development, and research. In the case of the CRON#TRAP campaign, the attackers opted to emulate a Linux installation of Tiny Core Linux. Examination of the preloaded and preconfigured aspects of the Tiny Core Linux environment shows system and user enumeration as well as potential exfiltration or command control channels built in. Another tool found in the installation is called Chisel, designed to connect the client to a command and control (“C2”) server. Chisel is tunneling software, secured via SSH that can pass traffic through firewalls.
Assura Recommends
- As this campaign likely started using phishing emails, avoid downloading files or attachments from external sources, especially if the source was unsolicited. Common file types include .zip, .rar, .iso, and .pdf. Additionally, external links to download these kinds of files should be considered equally dangerous. Zip files, sometimes password-protected, were used during this campaign.
- Block QEMU execution from directories other than %PROGRAMFILES% or %PROGRAMFILES(X86)% unless your users have valid, documented justification for the execution of this tool from another directory.
- We strongly recommend deploying robust endpoint logging capabilities to aid in PowerShell detections. This includes leveraging additional process-level logging such as Sysmon and PowerShell logging for additional log detection coverage.
Assura’s Actions
In addition to detection tools set to notify us of any anomalies related to our recommended steps, we’re using our security stack to detect, notify, and even prevent actions from this attack, including:
- The hashes for OneAmerica Survey.zip, OneAmerica Survey.lnk, and start.bat have been added to our detection rules in SentinelOne for our Managed Detection and Response clients.
- We’ve added QEMU process detection to our Stellar Cyber Open XDR Windows agent for our Managed SIEM/XDR clients.
- We’re keeping a close eye on threat intelligence to see if any of these indicators change over time, as the publicity of the attack may cause the attackers to change tactics.
This attack isn’t unique, as QEMU and other VM creation tools have been used in the past for crypto mining purposes. However, this new aspect of creating backdoors into Windows systems is of concern, as is the fact that these open-source tools are digitally signed and not generally detected by anti-virus or anti-malware tools.
References:
The post Phishing Campaign Installs Backdoor-Loaded VM to Evade Antivirus and Harvest Credentials appeared first on Assura, Inc..
*** This is a Security Bloggers Network syndicated blog from Assura, Inc. authored by Assura Team. Read the original post at: https://www.assurainc.com/blog/phishing-campaign-installs-backdoor-loaded-vm-to-evade-antivirus-and-harvest-credentials/
如有侵权请联系:admin#unsafe.sh

