
2024-11-3 23:54:58 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
In today’s digital landscape, protecting your identity from real-time threats is more critical than ever. As a cybersecurity expert, I’ve seen an evolving spectrum of threats that go far beyond traditional identity theft. From classic dark web doxing to the advent of fullz—full identity kits sold for a few dollars—threat actors are leveraging these methods for a new breed of real-time scams, amplified by cutting-edge technology.
Recently, a project by Anh Phu Nguyen and Caine Ardayfio demonstrated the capability to integrate facial recognition technology with Meta’s smart glasses, allowing instant identification of strangers. This development marks a significant leap from the traditional static forms of identity theft into real-time exploitation, where personal information is weaponized in the moment.
Classic Doxing and Fullz on the Dark Web
For decades, doxing and the sale of fullz (complete identity kits) have been staple methods of cybercriminals on the dark web. Doxing involves collecting and publicizing personal information such as home addresses, phone numbers, and social media profiles, often with the intent to embarrass, harass, or intimidate. OSINT tools (Open-Source Intelligence) allow attackers to scrape social media profiles, public databases, and breached datasets to compile detailed profiles on their victims. Once exposed, this data is used for targeted harassment or extortion.
Meanwhile, fullz provides a more comprehensive set of personal details, typically including social security numbers, financial data, and other sensitive information that can be exploited for identity theft. The sale of fullz on dark web marketplaces has enabled identity theft and financial fraud on a massive scale. For a relatively small fee, threat actors can purchase a victim’s entire identity, making it easy to perform account takeovers, create fake profiles, or apply for credit in the victim’s name.
In the past, these methods were effective but static. Attackers could steal and use personal data long after it was exposed. Today, however, advancements in technology have transformed these identity theft techniques into dynamic, real-time threats.
Real-Time Identity Exploitation: The New Era of Scams
The rise of facial recognition technology combined with wearable devices, like Meta’s smart glasses, introduces a new dimension to identity theft. By pairing this real-time data collection with pre-existing fullz or other doxing techniques, threat actors can instantly exploit an individual’s identity on the fly.
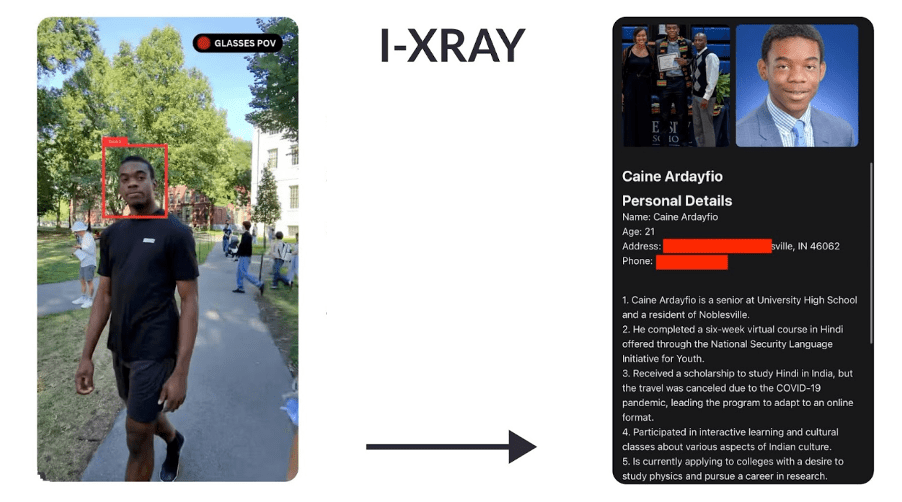
In this I-XRAY demonstration, Meta’s smart glasses were modified to scan faces in public, instantly cross-referencing them with public social media data and possibly with compromised identity information. Imagine walking down the street, unaware that someone can identify you, access your data, and target you with personalized scams—all in real time. This shift turns identity theft into a real-time, hyper-targeted activity.
Here’s how this modern version of doxing and scamming might unfold:
- Real-time recognition: A malicious actor equipped with facial recognition on smart glasses could walk through crowded public spaces and instantly identify individuals based on a match with their leaked photos from social media or other sources. This is no longer hypothetical; the proof-of-concept has already been demonstrated.
- Instant exploitation: Once an individual is identified, scammers could access their leaked fullz from the dark web, providing them with a detailed set of personal information. They could then approach the target in real-time, pretending to know them, creating a social engineering scenario where the victim believes the scammer is a legitimate acquaintance or authority figure.
- On-the-spot phishing: Imagine being approached by someone who knows your full name, email, address, and the last few digits of your social security number. When they ask you to verify some information the victim could easily fall into the trap of handing over even more sensitive information—like bank account details—without realizing they’ve been scammed until it’s too late.
The Role of AI in Amplifying Real-Time Threats
AI plays an integral role in the future of identity scams. It allows for the rapid analysis and deployment of identity data, enabling new, sophisticated scams that were previously unimaginable. Here are several ways AI can enhance these real-time threats:
- AI-Powered Deepfakes: Threat actors can combine AI-generated deepfakes with real-time data to impersonate individuals in both video and audio formats. By using AI to craft believable but fake messages or phone calls, scammers can extort or deceive people more convincingly than ever before.
- Automated Identity Theft at Scale: AI tools can automate the collection and correlation of personal data across multiple sources—social media, leaked data, and public records—faster than any human could. This allows threat actors to assemble profiles on victims quickly, accelerating identity fraud.
- Behavioral Analysis and Predictive Attacks: AI can analyze online behaviors to predict the types of scams most likely to succeed on a given target. For example, someone frequently searching for job opportunities could be targeted with a fake job offer, exploiting the victim’s immediate needs.
Insights from Experts: Combating Modern Threats
As highlighted previously, cybersecurity in the age of AI and real-time technologies requires an updated approach. The reliance on static data protection strategies, such as password managers or even two-factor authentication, is no longer sufficient. We need to implement dynamic identity monitoring, where AI-driven systems track unusual behavior related to your digital presence in real-time.
How Constella is Protecting Your Identity
At Constella, we are dedicated to staying ahead of evolving threats by leveraging cutting-edge AI technologies and continuous monitoring to provide comprehensive identity protection. Our unique approach not only covers traditional dark web monitoring but also focuses on a broader range of sources across the surface web, ensuring a proactive stance against emerging scams and data leaks. Here’s how we’re tackling the future of identity theft:
- Real-Time Identity Alerts: Our system is designed to provide real-time alerts when personal information is exposed across both the surface web, data brokers, and the dark web. Unlike traditional solutions that focus solely on the dark web, Constella offers a multi-source approach. This comprehensive coverage allows us to detect threats before they escalate, offering early warnings on a broader scale than any single-source monitoring service.
- Advanced Dark Web Monitoring: We continuously scan the dark web to detect any exposure of your personal information, whether it has been compromised by infostealers or exposed through data breaches. Our unique approach involves not just scraping the dark web but correlating this data with surface web activities, giving you a more holistic view of your identity exposure. This enables a faster response to potential threats before they result in fraud or exploitation.
- AI-Driven ScamGPT: Leveraging our proprietary AI technology, ScamGPT simulates potential scams that you may be targeted by using your own exposed personal information. This proactive approach allows us to train you before threat actors attempt a real attack, helping you recognize and avoid personalized phishing schemes, social engineering attempts, and other forms of exploitation. By generating potential scam scenarios based on your specific data profile, we ensure you are better prepared for what’s coming long before the attackers strike.
- Surface of Attack Mapping: Constella’s unique AI technology creates a detailed view of your real surface of attack, analyzing how your compromised information could be used against you. Using algorithms developed in collaboration with law enforcement agencies (LEAs), we connect the dots in the same way threat actors do, identifying all possible avenues they could exploit to target you. This approach allows you to see your vulnerabilities from the perspective of an attacker, enabling you to take targeted actions to secure those areas before they become active threats.
By integrating these advanced tools and methodologies, Constella provides a comprehensive identity protection solution designed to stay one step ahead of modern identity theft techniques. Our AI-driven insights ensure that you are equipped to defend against both current and future threats, safeguarding your personal information in an ever-changing cyber landscape.
*** This is a Security Bloggers Network syndicated blog from Constella Intelligence authored by Alberto Casares. Read the original post at: https://constella.ai/identity-protection-real-time-threats/
如有侵权请联系:admin#unsafe.sh

