2024-11-2 03:7:53 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Table of Contents
You could hear the cybersecurity product marketing departments groan in collective disgust following the unmasking and sanctioning of further members of the ‘Evil Corp’ ransomware group. The Law Enforcement actions unmasked not only the identities of these threat actors, but that they are in fact, pretty normal humans. Who wouldn’t want to hug a baby cheetah? Color us guilty.

(image of ‘Evil Corp’ members Dmitry Smirnov and Aleksandr Ryzhenkov)
These two individuals shattered the stereotypical image most people have of these actors. It turns out they aren’t working out of a cold, dark warehouse in hooded sweatshirts. They are not half-human, half-cyborg, transformer octopus. They are actually normal people who enjoy things that normal people would also enjoy. One of those things is, of course, having money. Participation in the cyber extortion economy is attractive because of three key drivers. These three drivers are also the areas where defenders, LEA, and policy makers can apply pressure and impose costs.
1) The high probability of earning money from cyber extortion. Even with ransom payment rates declining from over 80% in 2019 to 32% in Q3 2024, payment rates remain quite high as compared to monetization rates of legitimate businesses. When combined with extremely low revenue acquisition costs, cyber extortion remains an incredibly compelling career choice for STEM-educated individuals with few other economic opportunities.
It is also worth noting that Coveware’s payment rates are substantially lower than rates reported in other industry surveys. While surveys have their limitations, the primary reason for the lower rates lies in the difference in service. Coveware achieves these lower payment rates through data and technical advantages that drive better outcomes for our clients. As a result, compared to victims without access to expert vendors, our clients are far more likely to recover more quickly and experience less business interruption without needing to pay.

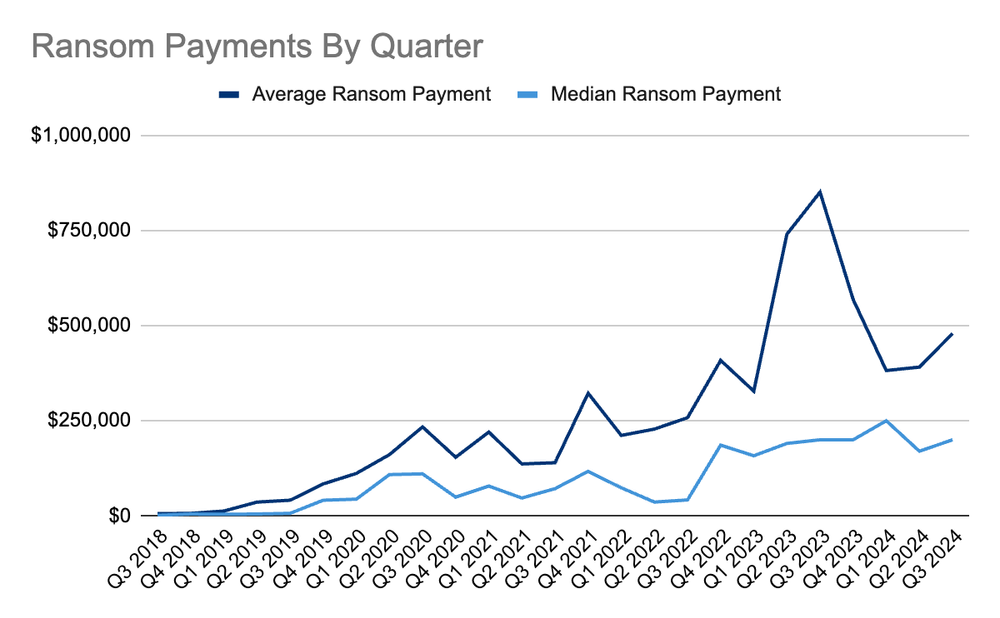
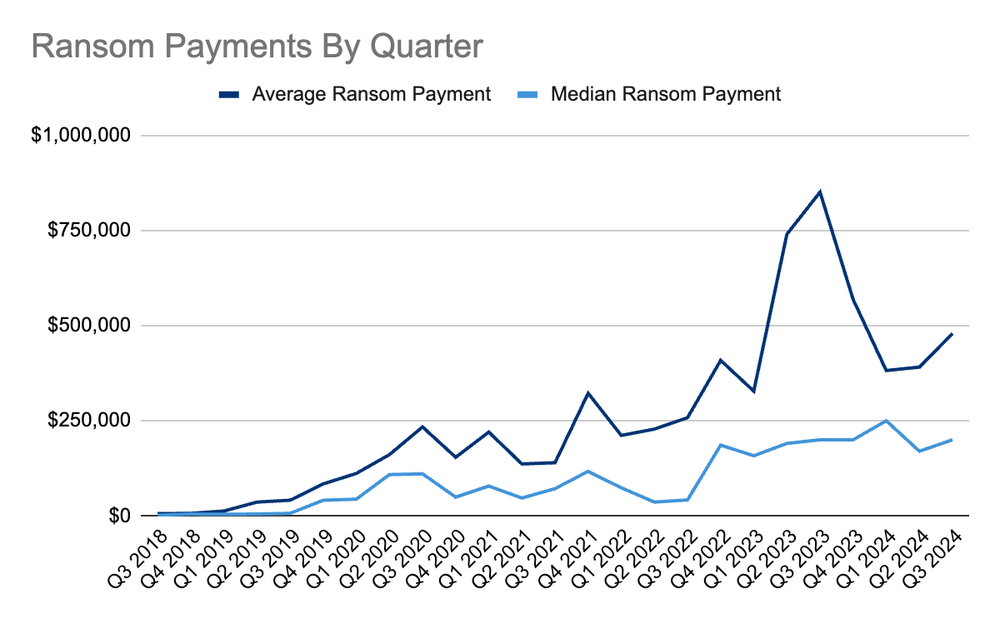
2) The high level of profitability of cyber extortion. When we analyzed the unit economics of cyber extortion, we found that profit margins to the person or group could easily approach or exceed 90%. This is due to the very low cost of conducting an attack compared to the relatively high payout from a ransom payment. Over the years since that analysis, organizations have gotten safer. Every additional hour, tool, or specialist a cyber extortion group must employ to succeed adds to their costs and reduces their profit margins. Even though the average and mean ransom payment rose in Q3 (Average Payment $479,237 (+23% from Q2 2024), Median Payment $200,000 (+18% from Q2 2024)), these figures remain volatile. They are not skyrocketing, despite media reports of extreme outliers.
Ransom Payment Amounts in Q3 2024
Average Ransom Payment
$479,237
+23% from Q2 2024
Median Ransom Payment
$200,000
+18% from Q2 2024
3) Cybercrime involves relatively low levels of violence and risk of incarceration compared to other forms of crime. Arrests are rare in cybercrime despite the outstanding work by LE agencies over the past few years. Disrupting cybercriminal infrastructure and doxing cyber criminals have emerged as new and highly effective strategies. Anonymity is one of the few things cybercriminals fiercely protect. When LE agencies demonstrate that cybercrime infrastructure is vulnerable to compromise, and cybercriminal operational security is not bulletproof, it raises the perceived risk profile of carrying out ransomware attacks. While increasing the risk profile will not end these attacks, it WILL decrease the number of participants in the industry. Scores of cybercriminals on the verge of engaging in the extortion economy are highly sensitive to shifts in economics and risk. A slight decrease in profits pushes them toward other careers, while a slight increase in risk drives them to pursue safer ways of earning a living.
Decreasing the economic attractiveness of ransomware through less payments, and increasing the perceived risk of ransomware is a very effective way to shrink the cybercrime economy.
Most Common Ransomware Variants in Q3 2024
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q2 2024 |
|---|---|---|---|
| 1 | Akira | 13% | – |
| 2 | RansomHub | 12% | New in Top Variants |
| 3 | Fog | 9% | New in Top Variants |
| 4 | Inc Ransom | 5% | +1 |
| 4 | Qilin | 5% | New in Top Variants |
| 4 | Blacksuit | 5% | -1 |
| 4 | Cicada3301 | 5% | New in Top Variants |
Market Share of the Ransomware attacks
For the fifth consecutive quarter, Akira remained the most common variant of ransomware impacting companies large and small in Q3 2024. New to the top three market share boards were RansomHub and Fog ransomware. RansomHub has been gaining share throughout 2024, despite its alleged ties to Evil Corp. Fog ransomware began its activity in Q1 2024, likely acquiring affiliates from both BlackCat and Lockbit, as its operators have shown a level of skill and experience that belies their relative newness in the field. The group is using an encryptor of new technical origin which is somewhat rare these days given the easy availability of leaked builders for early versions of Babuk, Lockbit and Conti.
Most Common Attack Vectors in Q3 2024

Attack vector prevalence continues to be driven by the threat actor groups with the greatest market share, and Q3-2024 is no deviation. Akira remains the most active threat actor in our dataset, and their continued focus on remote access via VPN abuse keeps this trend prominent and one of the largest threats to the SME market. The precise nature of VPN compromise continues to vary case-to-case, wherein some threat actors are exploiting a vulnerability/unpatched CVE, some are brute forcing accounts on appliances without multi-factor authentication enabled, and others are weaponizing legitimate stolen/leaked credentials that are scraped weeks or months in advance by infostealers. The popularity of access via infostealer data underscores the need for additional authentication factors and strong password hygiene.
Phishing compromise suffered a relative downturn earlier in the year, stemming from the temporary dormancy of some groups and complete collapse of others, but it is making an aggressive comeback as of the end of Q3 as groups like Scattered Spider re-emerge in earnest (focus on HelpDesk social engineering) and groups like RansomHub and Black Basta employ mixed vectors involving callback phishing and voice phishing (“vishing”) to coerce victims into calling or answering a support number and either downloading remote assistance software onto their machines, or entering their VPN credentials into websites controlled by the threat actors themselves. Other groups have employed Search Engine Optimization (SEO) poisoning tactics to lure victims into downloading malware disguised as common tools through sponsored links or poisoned AI summaries.
Insider Threats remain rare, but have been observed in the last quarter, often involving disgruntled contractors or third-party vendors who pose as external threats. The proliferation of these threats seems to be bolstered by access to AI and deepfake technology, allowing attackers to become increasingly creative in their tactics. Notably, insider attacks in Q3 appear to follow a pattern observed over the past few years, likely driven by organizational changes, restructuring, and budget cuts that often occur during this time in the corporate fiscal year.
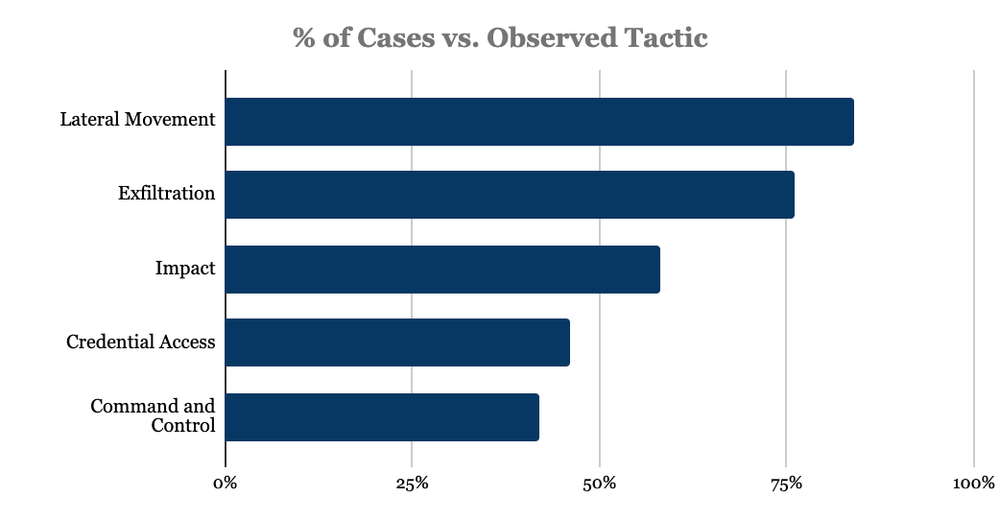
Lateral Movement [TA0008]: Lateral Movement takes the top spot with 84% of our cases, up from 71%. This is primarily driven by the exploitation of remote services like Remote Desktop Protocol (RDP), Lateral Tool Transfer techniques such as PSexec, and Secure Shell (SSH) connections particularly to connect to VMware ESXi environments. To mitigate these risks, organizations should implement robust access controls, limit RDP access to trusted IP addresses, network segmentation for critical systems, and enforce multi-factor authentication (MFA). For SSH access to ESXi servers, it’s crucial to restrict SSH access to only necessary users and utilize strong authentication methods.
Exfiltration [TA0010]: Data exfiltration has fallen from the number one spot after two consecutive quarters at the top, representing 76% of our cases but still consistent with the 75-80% seen over prior quarters. The persistence of data exfiltration remains a critical concern for organizations either as a pre-cursor to an encryption attack and double extortion, or as the sole tactic and objective. In addition to data security and loss prevention controls, organizations should focus on preparation activities such as understanding their data landscape, including identifying and classifying sensitive data and its locations, and incorporating data breach response strategies into ransomware playbooks. This includes evaluating third-party software and services as potential vectors for data breaches.
Impact [TA0040]: Forensically, the Impact category has remained in the #3 position for the second consecutive quarter, increasing to 58% from 48%. However, this figure can be misleading, as the actual number of cases involving data encryption reached 92% in Q3. A significant portion of the discrepancy between case statistics and forensic findings can be attributed to VMware ESXi. Forensic inspections of impacted ESXi hosts pose challenges in identifying the specific Tactic/Technique used by threat actors. This issue is further complicated when victims find themselves locked out of the ESXi console due to password tampering. In such cases, a complete reinstallation is often necessary to access the datastores for recovery, which unfortunately results in the loss of forensic artifacts.
Credential Access [TA0006]: Credential access has risen to the #4 position, representing 46% of our cases, an increase from 35%. This highlights the continued focus of threat actors on obtaining credentials, as any credential stored on a host system—regardless of its storage location—poses a potential target for compromise. Tools such as Mimikatz, Lazagne, and WebBrowserPassView remain popular and prominent. Organizations must prioritize robust security measures, including regular credential audits, implementation of strong password policies, and the use of multi-factor authentication (MFA) to safeguard against unauthorized access and reduce the risk of credential exploitation.
Command and Control [TA0011]: Command and Control (C2) remains a consistent threat, accounting for 42% of our cases, unchanged from Q2. This stability underscores the continued reliance of threat actors on established Command and Control infrastructures to maintain access and control over compromised systems. Notably, many adversaries are leveraging legitimate Remote Monitoring and Management (RMM) tools such as AnyDesk, ScreenConnect, and TeamViewer to facilitate their operations, which can complicate detection efforts. Organizations must enhance their monitoring capabilities to identify unusual activity associated with these tools and consider both application and network controls to mitigate the risks associated with unauthorized use of legitimate software.
Ransomware Victimology: Victims size Q3 2024

Q3 2024 is one of the first quarters in recent memory where professional services as an industry has dipped below 10% share of ransomware attacks. Historically, small professional service organizations, such as consulting, law, and financial service firms, have been particularly vulnerable to compromises. Many of these firms either chronically underinvest in security or believe they are too small to be targeted. We hope that as more and more services move to a SaaS model, that these types of firms become less and less prone to impactful compromise.
After a 6-month period of purely sporadic and opportunistic impact to Healthcare, our data indicates several groups seem to have turned their focus to this industry vertical intentionally – RansomHub and Inc Ransom. BlackCat/ALPHV previously held market share in healthcare attacks but following their disruption in Q1, no single threat group consolidated this focus until now.

Ransomware continues to be a major risk for small and medium sized organizations. The median size of companies impacted by ransomware attacks was 258 in Q3 2024 (+29% from Q2 2024). As has been the case in prior quarters, the large enterprise market tends to be more impacted by data-theft-only attacks whereas the SME market more often suffers from encryption-only or encryption-plus-data-theft incidents.

*** This is a Security Bloggers Network syndicated blog from Blog | Latest Ransomware News and Trends | Coveware authored by Bill Siegel. Read the original post at: https://www.coveware.com/blog/2024/11/1/law-enforcement-doxxing-raises-risk-profile-for-threat-actors
如有侵权请联系:admin#unsafe.sh

