2024-10-22 21:13:51 Author: securityaffairs.com(查看原文) 阅读量:3 收藏
Experts warn of a new wave of Bumblebee malware attacks

Experts warn of a new wave of attacks involving the Bumblebee malware, months after Europol’s ‘Operation Endgame‘ that disrupted its operations in May.
The Bumblebee malware loader has resurfaced in new attacks, four months after Europol disrupted it during “Operation Endgame” in May.
Bumblebee has been active since March 2022 when it was spotted by Google’s Threat Analysis Group (TAG), experts noticed that cybercriminal groups that were previously using the BazaLoader and IcedID as part of their malware campaigns switched to the Bumblebee loader.
According to the experts, the malware was developed by the TrickBot group and replaced the BazarLoader backdoor to provide initial access to the victim’s infrastructure in ransomware attacks.
Most Bumblebee infections started by users executing LNK files which use a system binary to load the malware. The malware is distributed through phishing messages using a malicious attachment or a link to the malicious archive containing Bumblebee. After initial execution, Bumblebee was used to perform post-exploitation activities, including privilege escalation, reconnaissance, and credential theft. Threat actors conduct intensive reconnaissance activities and redirect the output of executed commands to files for exfiltration.
Between 27 and 29 May 2024, an international law enforcement operation coordinated by Europol, codenamed Operation Endgame, targeted malware droppers like IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and Trickbot.
The joint actions were carried out by authorities in the Netherlands, Germany, France, Denmark, United States, and the United Kingdom with support from Europol and Eurojust. In addition, with the cooperation of the aforementioned authorities, there have also been police actions in Ukraine, Switzerland, Armenia, Portugal, Romania, Canada, Lithuania and Bulgaria for the arrest or interrogation of suspects, searches or the seizure and downing of servers.
It was the largest operation ever against botnets, crucial in deploying ransomware.
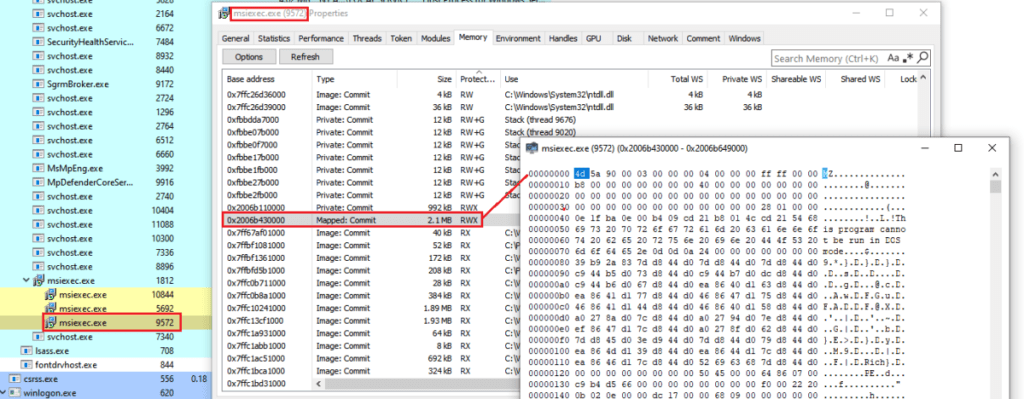
Netskope researchers detected new attacks involving the Bumblebee Loader, it is the first occurrence of a Bumblebee campaign they have seen since Operation Endgame.
The Bumblebee infection detected by Netskope likely begins with a phishing email containing a ZIP file with an LNK file named “Report-41952.lnk” that, once executed, starts the attack chain. Once executed, it downloads the payload directly into memory.
“Once opened, the LNK file executes a Powershell command to download an MSI file from a remote server, renames it as “%AppData%\y.msi”, and then executes/installs it using the Microsoft msiexec.exe tool.” reads the report published by Netskope. “the new Bumblebee payload is delivered via MSI files. The analyzed samples are disguised as Nvidia and Midjourney installers. They are used to load and execute the final payload all in memory, without even having to drop the payload to disk, as observed in previous campaigns using ISO files.”
The latest Bumblebee version avoids creating new processes by using the MSI SelfReg table to execute malicious DLLs directly without spawning tools like rundll32 or powershell, making it stealthier.

The Bumblebee malware uses known traits like an internal DLL name and exported functions. It decrypts its configuration using a hardcoded RC4 key (“NEW_BLACK.”) The decrypted data included port 443 and campaign IDs “msi” and “lnk001.”
Netskope published indicators of compromise (IoCs) for these attacks on a GitHub repository.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
如有侵权请联系:admin#unsafe.sh