2024-10-21 21:6:28 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
Is your vulnerability management game on point? If it’s not, you’re handing attackers an open invitation. And if you believe that merely using a vulnerability scanner qualifies as effective management, it’s time to reassess your strategy. Everyone’s doing vulnerability scanning, but that’s just step one. Real vulnerability management is what you do after you find the holes. Don’t confuse the two. Cybercriminals are always on the prowl for weaknesses, and it only takes one missed vulnerability to unleash chaos within your organization.
As per a recent report, organizations experienced an average of 1,636 cyber attacks per week in Q2 2024, a staggering 30% increase compared to the previous year. With threats growing in complexity and frequency, can you genuinely assert that your security measures are sufficient?
To effectively manage vulnerabilities, you must first grasp the true meaning of vulnerability management and the critical role it plays in your organization’s security strategy.
What is Vulnerability Management?
Vulnerability management is a systematic approach to identifying, assessing, prioritizing, and addressing vulnerabilities in your systems and applications. It goes beyond simple detection; it encompasses a continuous cycle of improvement to minimize security risks. This process begins with thorough scanning to uncover potential weak points, but it’s crucial to understand that scanning alone is not management.
Once vulnerabilities are identified, the next steps involve analyzing their severity and impact on your organization. This assessment helps prioritize which issues need immediate attention based on potential risks. From there, appropriate measures are taken to remediate or mitigate these vulnerabilities, ensuring that security is not merely reactive but proactive.
Key components of effective vulnerability management include:
- Continuous Identification: Regularly scanning for new vulnerabilities in your systems.
- Risk Assessment: Evaluating the potential impact and likelihood of exploitation for each vulnerability.
- Prioritization: Determining which vulnerabilities pose the greatest risk and addressing them first.
- Remediation and Mitigation: Implementing fixes or workarounds to address identified vulnerabilities.
- Monitoring and Reporting: Keeping track of vulnerability status and remediation efforts to ensure ongoing security.
Moreover, vulnerability management is an ongoing endeavor. It requires regular monitoring and reassessment as new threats emerge and your environment evolves. It’s about creating a culture of security awareness within your organization, empowering teams to recognize and respond to vulnerabilities effectively.
In essence, vulnerability management is not just a checkbox activity; it’s a critical component of your overall security strategy that enables you to stay ahead of potential attacks while fostering a secure environment for your organization.
Types of Vulnerability
Vulnerabilities are weaknesses in a system, application, or network that can be exploited by attackers to compromise security. Understanding the different types of vulnerabilities is essential for effective vulnerability management. Here are the main categories of vulnerabilities:
1. Software Vulnerabilities
- Buffer Overflow: This occurs when an application writes more data to a buffer than it can hold, potentially allowing an attacker to overwrite adjacent memory, leading to arbitrary code execution.
- SQL Injection: This vulnerability arises when an application includes unfiltered or improperly sanitized input in SQL queries. Attackers can manipulate these queries to access or modify the database.
- Cross-Site Scripting (XSS): XSS vulnerabilities occur when an application allows users to inject malicious scripts into web pages. This can lead to session hijacking, redirection to malicious sites, or defacement of web content.
2. Configuration Vulnerabilities
- Default Credentials: Many systems come with factory default settings and credentials, which, if not changed, can be easily exploited by attackers.
- Misconfigured Security Settings: Incorrectly configured permissions or security settings can expose sensitive information or services to unauthorized users. For example, leaving administrative interfaces accessible over the internet can lead to unauthorized access.
- Open Ports: Leaving unnecessary ports open on firewalls or routers can provide attackers with entry points into a network.
3. Network Vulnerabilities
- Unsecured Wireless Networks: Weak encryption protocols (e.g., WEP) or open networks can allow attackers to intercept data transmitted over the air.
- Denial of Service (DoS): This type of vulnerability allows attackers to overwhelm a network or service, rendering it unavailable to legitimate users. Common methods include flooding the network with excessive requests or exploiting specific weaknesses in protocols.
- Man-in-the-Middle (MitM) Attacks: Vulnerabilities in network communication can allow attackers to intercept and alter communications between two parties without their knowledge.
4. Physical Vulnerabilities
- Unauthorized Access to Facilities: Physical security weaknesses, such as unsecured data centers or lack of surveillance, can enable unauthorized individuals to gain physical access to sensitive systems.
- Insecure Disposal of Equipment: Failing to securely wipe or physically destroy old hardware can result in sensitive data being recovered by malicious actors.
5. Human Factors
- Social Engineering: Vulnerabilities often arise from human behavior, such as falling victim to phishing attacks, where attackers manipulate individuals into divulging sensitive information.
- Insider Threats: Employees or contractors with access to sensitive data may unintentionally or intentionally exploit their privileges, leading to data breaches or leaks.
6. Application Vulnerabilities
- Insecure APIs: Poorly designed application programming interfaces (APIs) can expose back-end systems and sensitive data to unauthorized access or manipulation.
- Race Conditions: These occur when the timing of actions affects the correctness of the application, allowing attackers to exploit the timing of operations to manipulate data or gain unauthorized access.
7. Compliance Vulnerabilities
- Regulatory Non-compliance: Organizations may fail to adhere to industry regulations and standards (e.g., GDPR, PCI DSS), leading to vulnerabilities that can be exploited by attackers and resulting in legal penalties.
8. Emerging Vulnerabilities
- IoT Vulnerabilities: The proliferation of Internet of Things (IoT) devices introduces new vulnerabilities due to inadequate security measures. Many IoT devices have default passwords or lack proper encryption.
- Cloud Security Vulnerabilities: As organizations migrate to the cloud, vulnerabilities related to misconfigured cloud settings, inadequate access controls, and insecure APIs have become prevalent.
How are Vulnerabilities Ranked and Categorized?
Ranking and categorization of vulnerabilities is a crucial part of vulnerability management, which helps organizations focus their resources on the most critical threats. Here’s a breakdown of how vulnerabilities are ranked and categorized:
1. Vulnerability Identification
The first step in vulnerability management is identifying vulnerabilities using a combination of automated tools, manual testing, and threat intelligence sources. Common tools include vulnerability scanners (e.g., Nessus, Qualys, Rapid7) that analyze systems for known vulnerabilities, as well as penetration testing methodologies that simulate real-world attacks.
2. Categorization of Vulnerabilities
Once identified, vulnerabilities are categorized based on several criteria:
- Type of Vulnerability: Vulnerabilities can be categorized by their nature, such as:
- Configuration Issues: Misconfigurations that can be exploited (e.g., open ports, default credentials).
- Code Vulnerabilities: Flaws in application code, such as SQL injection, cross-site scripting (XSS), or buffer overflows.
- Dependency Vulnerabilities: Issues arising from third-party libraries or components that may contain known vulnerabilities.
- Affected Component: Vulnerabilities can also be classified based on the impacted component:
- Operating Systems: Vulnerabilities specific to Windows, Linux, macOS, etc.
- Applications: Vulnerabilities affecting web applications, mobile applications, or enterprise software.
- Network Devices: Vulnerabilities present in routers, switches, or firewalls.
3. Ranking Vulnerabilities
After categorization, vulnerabilities are ranked to prioritize remediation efforts. Various frameworks and scoring systems are utilized to assign a severity level to each vulnerability. The most widely adopted framework is the Common Vulnerability Scoring System (CVSS), which provides a standardized method for evaluating the severity of vulnerabilities based on three metric groups:
- Base Metrics: These metrics represent the intrinsic characteristics of a vulnerability and are constant over time and across environments. They include:
- Attack Vector (AV): Defines how the vulnerability can be exploited (e.g., network, adjacent network, local, physical).
- Attack Complexity (AC): Assesses the conditions beyond the attacker’s control that must exist to exploit the vulnerability (e.g., low, high).
- Privileges Required (PR): Indicates the level of access required to exploit the vulnerability (e.g., none, low, high).
- User Interaction (UI): Specifies whether exploitation requires user interaction.
- Scope (S): Determines whether the vulnerability affects only the vulnerable component or if it impacts other components as well.
- Confidentiality (C), Integrity (I), and Availability (A): Evaluate the impact on these three aspects if the vulnerability is exploited.
- Temporal Metrics: These metrics account for the characteristics of a vulnerability that may change over time, such as:
- Exploit Code Maturity (E): Indicates the current state of exploit techniques (e.g., not defined, proof-of-concept, functional, high).
- Remediation Level (RL): Reflects the availability of fixes or workarounds (e.g., official fix, temporary fix, unavailable).
- Report Confidence (RC): Represents the level of confidence in the existence and impact of the vulnerability.
- Environmental Metrics: These metrics allow organizations to customize the score based on their specific environment, taking into account factors such as:
- Modified Base Metrics: Adjustments to base metrics reflecting the organization’s specific circumstances.
- Security Requirements: The importance of confidentiality, integrity, and availability for the organization, which can further influence the final score.
4. Scoring and Interpretation
The CVSS score, typically ranging from 0 to 10, provides a numerical representation of the severity of the vulnerability, with higher scores indicating more critical vulnerabilities. Organizations can then categorize vulnerabilities into different severity levels based on their CVSS score, often using the following scale:
- Critical (9.0 – 10.0): Immediate action is required.
- High (7.0 – 8.9): Prompt action is necessary.
- Medium (4.0 – 6.9): Mitigation should be scheduled.
- Low (0.1 – 3.9): Monitoring may be sufficient.
5. Prioritization of Remediation
After ranking vulnerabilities, organizations prioritize remediation efforts based on several factors, including:
- Risk Exposure: Assessing the likelihood of exploitation and the potential impact on the organization.
- Business Context: Considering the criticality of affected assets and their role in business operations.
- Compliance Requirements: Addressing vulnerabilities that may impact regulatory compliance or industry standards.
How Vulnerability Management Supports Compliance?
Vulnerability management plays a key role in helping organizations meet the requirements of various cybersecurity regulations like GDPR, HIPAA, and PCI-DSS. These frameworks are designed to protect sensitive information by ensuring that companies maintain a strong security posture. At its core, vulnerability management focuses on identifying, assessing, and remediating weaknesses in systems, which directly supports the security measures these regulations demand. Let’s break down how effective vulnerability management practices can help achieve compliance with these major standards.
The GDPR sets strict rules on how organizations must protect personal data of EU citizens. Non-compliance can lead to severe penalties, including hefty fines. Vulnerability management helps organizations address the following key GDPR requirements:
- Article 32: Security of Processing
GDPR mandates that organizations implement technical and organizational measures to ensure the security of personal data. Vulnerability management supports this by regularly scanning for vulnerabilities and ensuring that any weaknesses that could expose personal data are quickly addressed. - Risk-Based Approach
GDPR emphasizes a risk-based approach to security. By using vulnerability management tools to assess the severity and likelihood of vulnerabilities being exploited, organizations can prioritize remediation efforts, ensuring that critical risks to personal data are mitigated first. - Data Breach Prevention
Regular vulnerability scanning and patch management reduce the likelihood of a data breach, which can occur if attackers exploit unpatched vulnerabilities. Proactively addressing these weaknesses helps companies avoid the reputational damage and financial penalties that result from breaches under GDPR.
2. Health Insurance Portability and Accountability Act (HIPAA)
HIPAA requires healthcare organizations to protect patient data (Protected Health Information or PHI) from unauthorized access. Vulnerability management is essential for maintaining compliance with HIPAA’s security standards:
- HIPAA Security Rule: Technical Safeguards
The HIPAA Security Rule specifies technical safeguards to ensure the confidentiality, integrity, and availability of PHI. Vulnerability management ensures that systems handling PHI are secure by regularly identifying potential vulnerabilities in applications, databases, and networks. - Risk Analysis and Management
HIPAA requires healthcare organizations to conduct a risk analysis to identify potential risks to the confidentiality of PHI. Vulnerability management tools continuously assess systems for risks, allowing organizations to understand and prioritize which vulnerabilities pose the highest threat to PHI. - Access Control and Audit Controls
Regular vulnerability assessments can identify gaps in access control mechanisms or audit systems, ensuring that unauthorized users cannot gain access to sensitive patient information. If vulnerabilities are found in access control configurations, vulnerability management ensures they are fixed promptly.
3. Payment Card Industry Data Security Standard (PCI-DSS)
Organizations that handle credit card transactions must comply with PCI-DSS, which provides detailed requirements for securing payment card data. Vulnerability management directly supports several of these requirements:
- Requirement 6: Develop and Maintain Secure Systems and Applications
PCI-DSS emphasizes the need to fix vulnerabilities in systems and applications. Vulnerability management tools are crucial here, as they scan for potential security flaws in the applications and systems involved in processing credit card information. Remediation steps, such as timely patching, help meet this requirement. - Requirement 11: Regularly Test Security Systems and Processes
PCI-DSS requires regular vulnerability scanning and penetration testing to ensure the security of cardholder data. By conducting vulnerability assessments and resolving identified issues, organizations can demonstrate compliance with the requirement for ongoing security testing. - Compliance Documentation
Vulnerability management tools can generate reports that demonstrate compliance with PCI-DSS requirements, making audits smoother and more straightforward. These reports show that vulnerabilities are being identified, addressed, and resolved in a timely manner, reducing the likelihood of audit failures.
How Effective Vulnerability Management Practices Aid Compliance?
1. Risk Prioritization for Regulatory Focus
Vulnerability management enables organizations to prioritize vulnerabilities based on their potential impact, ensuring that high-risk issues that could lead to non-compliance are handled first. This approach is especially crucial for regulatory frameworks that mandate risk-based security measures, such as GDPR and HIPAA.
2. Automation of Regular Scans and Reporting
Regular scanning is a core requirement of most compliance regulations. Effective vulnerability management platforms automate this process, conducting scans at predefined intervals and generating reports that track remediation progress. These reports can be used as proof during compliance audits, showing that the organization is continually monitoring and improving its security posture.
3. Alignment with Security Best Practices
Many compliance standards are based on widely accepted security best practices, like those outlined by NIST or ISO 27001. A strong vulnerability management process helps companies align with these best practices, improving both security and compliance. Automated remediation, patching, and configuration management ensure organizations consistently meet the required standards.
4. Reduction of Data Breach Risk
The regulations like GDPR, HIPAA, and PCI-DSS all prioritize the protection of sensitive data. Vulnerability management minimizes the risk of a data breach by addressing security gaps before they can be exploited. Preventing breaches reduces the risk of fines and penalties associated with non-compliance, as well as the reputational damage that often follows an attack.
5. Facilitating a Proactive Security Posture
Effective vulnerability management allows organizations to be proactive in managing security risks, rather than simply reacting to incidents. This proactive stance is often required by regulatory bodies, which expect companies to demonstrate continuous improvement in their security measures.
The Role of Vulnerability Management in Risk Management Frameworks
Risk management frameworks are structured approaches that help organizations identify, assess, and mitigate risks to their information systems and data. These frameworks provide a systematic way to manage cybersecurity risks, including vulnerabilities, and ensure compliance with industry standards and regulations. Two of the most widely adopted frameworks that incorporate vulnerability management are NIST and ISO 27001.
1. NIST Cybersecurity Framework (CSF)
The National Institute of Standards and Technology (NIST) provides a risk management framework that is widely recognized and used across industries, particularly in the U.S. NIST’s framework emphasizes five core functions that help organizations build and maintain a robust cybersecurity posture, with vulnerability management playing a crucial role in several areas.
Key Functions in NIST CSF:
- Identify: Organizations must identify their assets, including software, hardware, and data, along with potential vulnerabilities in these assets. This involves understanding your environment and the risks that could affect it.
- Protect: After identifying assets and vulnerabilities, organizations must establish safeguards to ensure these vulnerabilities are addressed. This includes managing access controls, securing data, and implementing patch management.
- Detect: Continuous monitoring of systems to detect potential vulnerabilities or unusual activity that could indicate exploitation is critical. Vulnerability scanning and threat intelligence tools help in the detection process.
- Respond: Once a vulnerability is detected or exploited, organizations must respond quickly by isolating the threat, analyzing the impact, and fixing the vulnerabilities through remediation.
- Recover: NIST emphasizes the need for a recovery plan post-incident to ensure that systems can return to normal operations, while vulnerabilities are permanently addressed.
Vulnerability Management in NIST:
Vulnerability management is explicitly incorporated in the Protect and Detect functions of NIST. It calls for regular vulnerability assessments, patch management, and configuration changes to minimize risk. The NIST framework recommends using vulnerability scanning tools to proactively identify weaknesses and encourages regular updates to vulnerability management practices as new threats emerge.
2. ISO/IEC 27001
ISO/IEC 27001 is an international standard for managing information security, and it outlines the requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). Vulnerability management is a key component of risk assessment and mitigation within ISO 27001.
Key Elements in ISO 27001:
- Risk Assessment: ISO 27001 requires organizations to assess their information security risks. This includes identifying vulnerabilities in systems and networks that could be exploited. The risk assessment helps prioritize vulnerabilities based on their potential impact on the organization.
- Risk Treatment: After assessing risks, organizations must decide how to treat vulnerabilities, either by mitigating, transferring, or accepting the risks. This involves developing a risk treatment plan that includes vulnerability management processes such as patch management and system hardening.
- Annex A Controls: ISO 27001 includes a detailed set of controls (Annex A) that address various aspects of information security. Vulnerability management is tied to these controls, particularly in the areas of asset management, access control, and system acquisition, development, and maintenance. Organizations are required to ensure their systems are regularly checked for vulnerabilities, and appropriate actions are taken to mitigate them.
Vulnerability Management in ISO 27001:
ISO 27001 emphasizes the importance of continuous monitoring and improvement of security controls. Vulnerability management falls under this continuous process of identifying potential weaknesses and applying the necessary security measures to prevent breaches. Regular vulnerability assessments, patch management, and incident response planning are all key parts of complying with ISO 27001.
Comparison of NIST and ISO 27001 in Vulnerability Management
While both NIST and ISO 27001 incorporate vulnerability management, they approach it with slight differences:
- NIST focuses on a risk-based approach tailored specifically to organizations in the U.S. It’s highly flexible and allows organizations to scale their security efforts based on risk tolerance.
- ISO 27001 provides a globally recognized standard that focuses on formalizing the security process through an ISMS. It mandates specific controls for vulnerability management but also requires regular audits and certifications to ensure compliance.
Why These Frameworks Matter for Vulnerability Management?
Risk management frameworks like NIST and ISO 27001 offer structured approaches that not only identify vulnerabilities but also manage them within a broader context of cybersecurity risks. For organizations, adhering to these frameworks helps:
- Ensure Compliance: Both frameworks help organizations meet regulatory requirements (e.g., GDPR, HIPAA) by systematically managing risks, including vulnerabilities.
- Improve Security Posture: Implementing these frameworks ensures that vulnerability management is not a one-time effort but part of an ongoing process.
- Minimize Risk: By identifying and managing vulnerabilities through a structured approach, organizations can significantly reduce the risk of breaches and attacks.
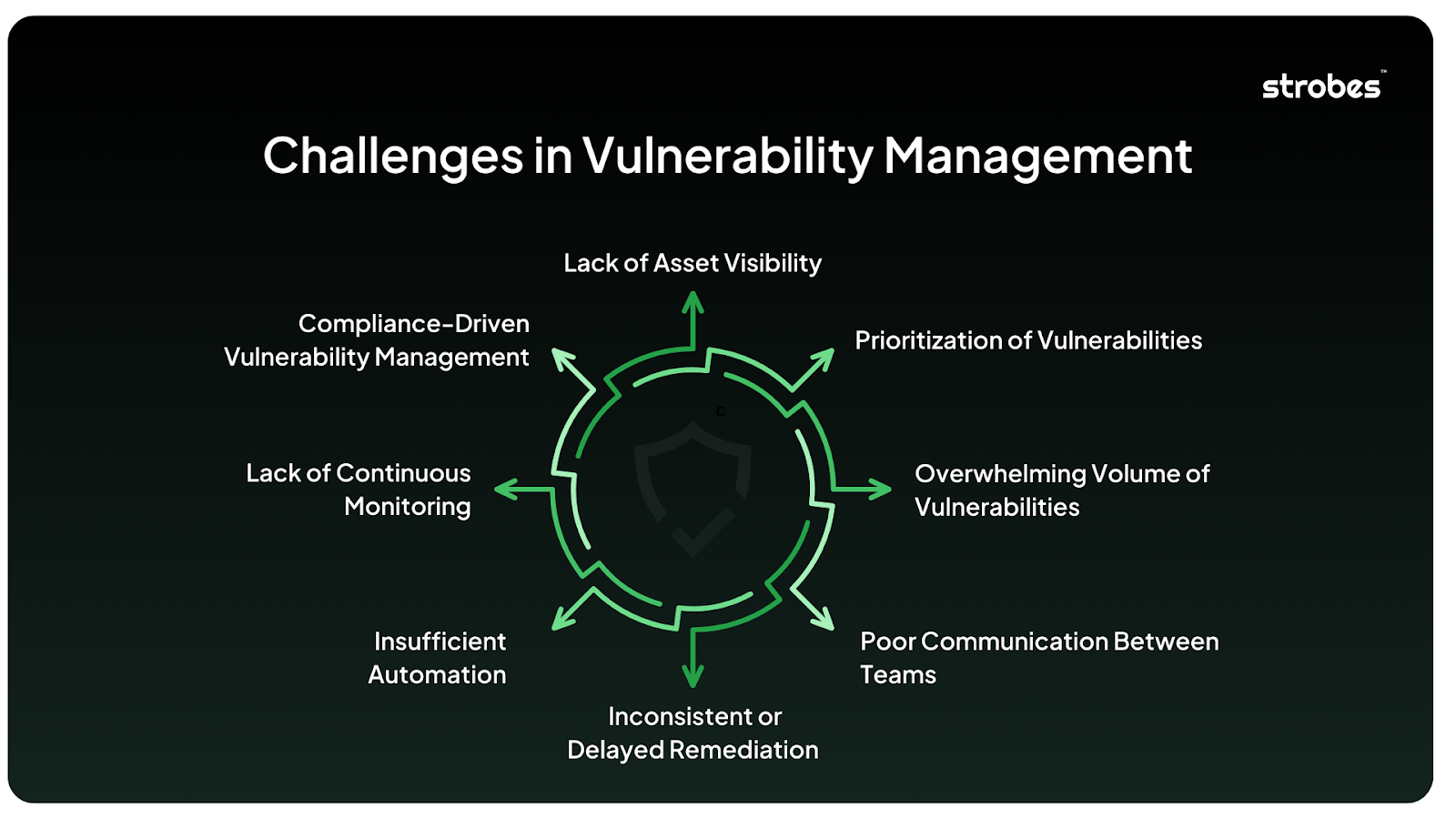
Challenges in Vulnerability Management
Vulnerability management may sound straightforward. All you need is to identify security weaknesses, fix them, and move on. But in reality, it’s far more complex and filled with challenges that can trip up even the most well-equipped organizations. Let’s take a closer look at some of the most frequent and significant pitfalls organizations face when managing vulnerabilities.
1. Lack of Asset Visibility
- The Challenge: You can’t protect what you don’t know exists. Many organizations struggle to maintain an up-to-date inventory of all assets within their networks, including servers, devices, applications, and cloud environments.
- Why It’s a Problem: Without a complete view of your assets, vulnerabilities could be lurking in unmonitored systems, making them easy targets for attackers.
- How It Happens: This challenge becomes worse with remote work, cloud adoption, and rapid scaling, where new assets are introduced frequently but not always tracked properly.
2. Prioritization of Vulnerabilities
- The Challenge: Not all vulnerabilities are created equal. A common mistake organizations make is treating every vulnerability with the same level of urgency.
- Why It’s a Problem: Focusing on low-risk vulnerabilities can waste time and resources while leaving high-risk issues unaddressed. Attackers are more likely to exploit vulnerabilities that offer the easiest and biggest reward, making risk-based prioritization crucial.
- How It Happens: Without clear risk assessments or an understanding of the business impact, teams can struggle to differentiate between what needs immediate attention and what can be addressed later.
3. Overwhelming Volume of Vulnerabilities
- The Challenge: Large organizations often face hundreds, if not thousands, of vulnerabilities to manage at any given time. Security teams can quickly become overwhelmed by the sheer volume.
- Why It’s a Problem: When faced with too many vulnerabilities, teams may experience alert fatigue or feel paralyzed by the amount of work, leading to delays in remediation.
- How It Happens: This is often exacerbated by outdated systems and patch management processes, where known vulnerabilities pile up faster than they can be fixed.
4. Poor Communication Between Teams
- The Challenge: Vulnerability management often requires collaboration between multiple departments—security, IT, development, and even leadership.
- Why It’s a Problem: Poor communication or lack of alignment between these groups can lead to vulnerabilities slipping through the cracks. For example, IT teams may prioritize system uptime, while security teams focus on patching vulnerabilities, causing a conflict in priorities.
- How It Happens: Siloed operations, unclear responsibilities, and lack of centralized reporting are common causes of this communication breakdown.
5. Inconsistent or Delayed Remediation
- The Challenge: Even when vulnerabilities are identified and prioritized correctly, the actual remediation process can be slow or inconsistent.
- Why It’s a Problem: Delays in fixing vulnerabilities increase the window of exposure, giving attackers more time to exploit weaknesses.
- How It Happens: Limited resources, conflicting IT priorities, or reliance on manual patching processes can lead to delayed remediation. Additionally, legacy systems may not support timely updates, requiring extensive testing before applying fixes.
6. Insufficient Automation
- The Challenge: Many organizations still rely on manual vulnerability management processes, which are time-consuming and prone to human error.
- Why It’s a Problem: Without automation, scanning for vulnerabilities and managing their remediation becomes inefficient. Manual processes can’t keep up with the pace at which new vulnerabilities emerge.
- How It Happens: Organizations often hesitate to adopt automation due to perceived high costs, a steep learning curve, or fears of disrupting existing workflows.
7. Lack of Continuous Monitoring
- The Challenge: Many organizations conduct vulnerability assessments periodically, rather than continuously. They may scan quarterly or even annually, leaving large gaps in their security posture.
- Why It’s a Problem: Vulnerabilities don’t wait for your quarterly scan. New weaknesses can be introduced at any moment, leaving systems exposed between scheduled assessments.
- How It Happens: Limited resources, outdated tools, and a lack of awareness about the importance of continuous monitoring contribute to this challenge.
8. Compliance-Driven Vulnerability Management
- The Challenge: Some organizations focus on vulnerability management primarily to meet compliance requirements (e.g., PCI DSS, HIPAA), rather than as part of an overall security strategy.
- Why It’s a Problem: Compliance checklists often miss the bigger picture. Vulnerabilities that may not be covered by regulations can still pose significant risks to an organization. Focusing only on compliance can create a false sense of security.
- How It Happens: Organizations may prioritize compliance audits over proactive vulnerability management due to resource constraints or pressure from stakeholders.
Solution to Overcome Vulnerability Management Challenges
The key to overcoming these challenges lies not in doing more, but in doing it smarter. What if you could simplify the entire process—automate the tedious tasks, prioritize threats based on actual risk, and focus your efforts on the vulnerabilities that matter most? And you don’t need multiple tools or complex setups to do this, just Strobes RBVM is enough to overcome these challenges. Below are the key recommendations for addressing the typical hurdles organizations face, and how Strobes RBVM fits into the solution.
1. Lack of Asset Visibility
- The Solution: Automated Asset Discovery with Strobes RBVM
- How It Helps: Strobes RBVM integrates with various tools and environments (cloud, on-prem, hybrid) to automatically discover and map all assets in real-time. This ensures you have a complete and continuously updated inventory of your digital infrastructure.
- Recommendation: Implement continuous asset discovery to maintain an up-to-date overview of your systems. Strobes’ wide range of integrations ensures every corner of your network is visible.
2. Prioritization of Vulnerabilities
- The Solution: Risk-Based Prioritization and Scoring
- How It Helps: Not every vulnerability needs to be addressed with the same urgency. Strobes RBVM uses contextual intelligence to assess the actual risk of each vulnerability, considering factors such as exploitability, potential business impact, and asset criticality. This allows your team to focus on the vulnerabilities that truly matter.
- Recommendation: Shift from volume-based to risk-based vulnerability management using Strobes’ intelligent scoring system. This way, your efforts are directed towards high-risk vulnerabilities first, reducing exposure to critical threats.
3. Overwhelming Volume of Vulnerabilities
- The Solution: Prioritization with Automation
- How It Helps: Strobes RBVM automates the process of sorting through thousands of vulnerabilities, assigning a risk score to each one based on various factors. This reduces manual effort and alert fatigue, ensuring the team can focus on meaningful tasks.
- Recommendation: Rely on Strobes RBVM’s automation to categorize and prioritize vulnerabilities based on risk, reducing the burden on your team and making sure critical issues are handled quickly.
4. Poor Communication Between Teams
- The Solution: Collaborative Platform with Centralized Dashboards
- How It Helps: Strobes RBVM provides a centralized platform where different teams such as security, IT, and DevOps can access the same vulnerability data. Customizable dashboards ensure that everyone is aligned on priorities, responsibilities, and timelines.
- Recommendation: Use Strobes RBVM’s centralized and customizable dashboards to foster better communication between departments. This ensures vulnerability information is shared in real time and remediation efforts are coordinated effectively.
5. Inconsistent or Delayed Remediation
- The Solution: Streamlined Workflow and Automation
- How It Helps: Strobes RBVM integrates with ticketing systems (like Jira, ServiceNow) to automate the assignment of tasks to the right teams, ensuring vulnerabilities are remediated consistently and promptly. Automated workflows also keep track of remediation progress and notify stakeholders of any delays.
- Recommendation: Implement automated workflows in Strobes RBVM to streamline the remediation process and track progress in real-time, preventing delays in addressing critical vulnerabilities.
6. Insufficient Automation
- The Solution: End-to-End Automation with Strobes RBVM
- How It Helps: Strobes RBVM automates the entire vulnerability management lifecycle from scanning and risk assessment to prioritization and remediation tracking. This frees up security teams to focus on strategic decisions rather than manual tasks.
- Recommendation: Maximize automation within Strobes RBVM to reduce human error, accelerate response times, and keep up with the dynamic threat landscape. Automation also scales easily, meaning your vulnerability management process stays efficient as your organization grows.
7. Lack of Continuous Monitoring
- The Solution: Continuous Vulnerability Scanning and Monitoring
- How It Helps: Strobes RBVM provides continuous vulnerability scanning, ensuring your systems are always being monitored for new weaknesses. Alerts are generated the moment new vulnerabilities are identified, reducing exposure time.
- Recommendation: Switch from periodic assessments to continuous monitoring with Strobes RBVM, ensuring that vulnerabilities are detected as soon as they emerge. This proactive approach closes security gaps quickly.
8. Compliance-Driven Vulnerability Management
- The Solution: Security and Compliance Alignment
- How It Helps: While compliance is important, security should be the primary focus. Strobes RBVM goes beyond mere compliance checklists by aligning vulnerability management efforts with both security best practices and regulatory requirements. This ensures that you’re not just compliant, but also secure.
- Recommendation: Use Strobes RBVM to ensure that your vulnerability management strategy isn’t solely compliance-driven. By focusing on security risks first, you’ll achieve compliance naturally, while maintaining a stronger overall security posture
Conclusion
The goal is clear: minimize your attack surface by identifying and addressing weaknesses before they become entry points for attackers. An effective vulnerability management program empowers you to continuously pinpoint and mitigate risks that could be exploited.
Strobes’ Risk-Based Vulnerability Management (RBVM) solution takes this a step further by focusing on the most critical vulnerabilities, enabling you to prioritize resources where they will have the greatest impact. By integrating effective vulnerability management into your security framework, you not only strengthen your security posture but also support your organization’s compliance objectives. Don’t leave your security to chance! Take action with Risk-Based Vulnerability Management today. Start your 30-day free trial of Strobes RBVM to explore the platform and assess your security needs!
The post What is Vulnerability Management? Compliance, Challenges, & Solutions appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Shubham Jha. Read the original post at: https://strobes.co/blog/what-is-vulnerability-management-compliance-challenges-solutions/
如有侵权请联系:admin#unsafe.sh
