
2024-10-15 01:45:5 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Recently, U.S. and U.K. cyber agencies have warned of a renewed wave of attacks led by Russian APT29 hackers. These sophisticated threat actors have been actively exploiting vulnerabilities in Zimbra Collaboration Suite and JetBrains TeamCity, specifically CVE-2022-27924 and CVE-2023-42793, to target critical systems.
At Imperva, we are committed to ensuring our customers remain secure from such exploits, and Imperva customers have been protected against these vulnerabilities since day one.
The Threat Landscape: Zimbra and TeamCity Vulnerabilities
APT29, a notorious Russian state-backed group connected to the SVR, has been linked to a series of advanced cyber espionage campaigns, focusing on government organizations, technology firms, and key infrastructure. Their recent exploits target vulnerabilities in widely used platforms Zimbra and TeamCity:
- CVE-2022-27924: This vulnerability in Zimbra is an email compromise attack that allows unauthenticated remote attackers to steal login credentials via a vulnerable mail server, potentially leading to a full system compromise. Exploiting this flaw can give attackers privileged access to emails and sensitive communications, making it a prime target for espionage. This vulnerability has been exploited since as early as August 2022 to steal email account credentials.
- CVE-2023-42793: This vulnerability in JetBrains TeamCity is an arbitrary file read flaw that allows attackers to access sensitive files on the server. This breach of sensitive data can be used to escalate privileges and further infiltrate the organization’s network, posing significant risks to development pipelines. This vulnerability was exploited by both ransomware gangs and North Korean hacking groups for initial access and attempted supply-chain attacks.
What We’ve Seen
Imperva has seen several attacks attempting to exploit these vulnerabilities.
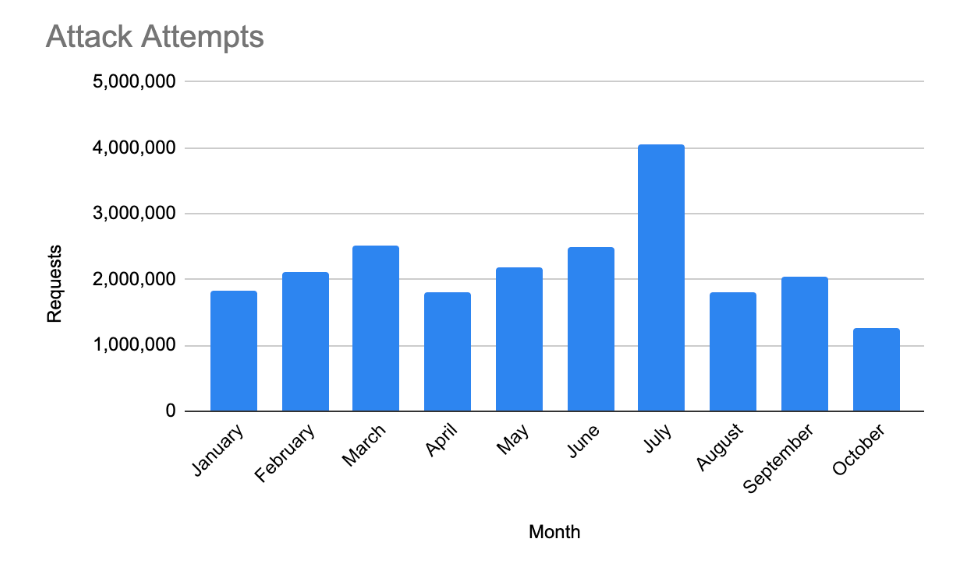
For Zimbra, we’ve recorded several attack attempts targeting a single financial services (FSI) site, with the majority of the activity concentrated on August 17th. The attacks were carried out using automated bots originating primarily from the United Kingdom, with the goal of exploiting the email compromise vulnerability.
In contrast, the attacks exploiting the JetBrains TeamCity vulnerability have been far more aggressive. We’ve detected millions of requests across several industries, including FSI, business services, computing, and telecommunications. The malicious traffic came from a broader range of countries, including the U.S., Germany, India, France, and Russia, with attackers leveraging both bots and browser impersonators to maximize the effectiveness of the exploit attempts. These patterns suggest a coordinated and wide-reaching campaign, with a focus on compromising CI/CD pipelines and sensitive development environments.
Attacks primarily target US-, Australia-, and India-based sites, primarily in the FSI and Business industries. There are several overlapping IP addresses that we’ve seen exploit both CVEs, which might suggest a threat actor’s joint infrastructure.
Staying Ahead of APT29 and Other Threat Actors
As state-sponsored attackers become more aggressive and sophisticated, defending against targeted exploits like CVE-2022-27924 and CVE-2023-42793 is more crucial than ever. APT29’s focus on compromising Zimbra and TeamCity highlights the importance of securing enterprises’ operation services, including email systems and CI/CD pipelines.
By leveraging our advanced security tools, we can ensure that your systems are protected from exploitation by even the most persistent adversaries. Imperva’s Web Application Firewall (WAF) provides out-of-the-box security for your web applications. It detects and prevents cyber threats, ensuring seamless operations and peace of mind. Protect your digital assets with Imperva’s robust, industry-leading solution.
We stand ready to defend your infrastructure and keep your sensitive data secure.
The post Imperva Defends Against Targeted Exploits Used By APT29 Hackers appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Gabi Sharadin. Read the original post at: https://www.imperva.com/blog/imperva-defends-against-exploits-used-by-apt29-hackers/
如有侵权请联系:admin#unsafe.sh

