2024-10-10 17:46:58 Author: blog.sekoia.io(查看原文) 阅读量:5 收藏
Table of contents
- Managing access across teams: The challenge in SOC models
- How Sekoia Defend streamlines SOC access management
- Use-cases
- Multi-Tenant architecture: Simplifying complex environments
- Data segregation by Intakes: Fine-tuned data access control
- Maximizing Efficiency by Combining Multi-Tenant and Data Segregation
- Conclusion: Empowering security operations with Sekoia Defend
In today’s evolving cybersecurity landscape, organizations face the challenge of monitoring and responding to threats efficiently through their Security Operations Centers (SOC). Depending on an organization’s size and security priorities, different SOC models are adopted, each with its own approach to security management.
Some companies opt for a fully in-house SOC, with internal teams managing all aspects of security operations. Large corporations, in particular, benefit from this model, given their resources to maintain a dedicated security staff. On the other hand, hybrid SOCs combine internal expertise with external Managed Security Service Providers (MSSPs), allowing businesses to maintain control over some aspects of security while outsourcing monitoring and threat detection. Smaller organizations often rely on outsourced SOCs, entirely managed by MSSPs, which offer scalability and expert monitoring without the need for a full in-house team.
Each SOC model offers unique advantages:
- In-house SOCs provide complete control over security operations.
- Hybrid SOCs offer a balance of internal oversight and outsourced expertise.
- Outsourced SOCs bring cost-effective security solutions with scalability.
However, each SOC model presents challenges, particularly when it comes to managing access to sensitive security data across multiple teams.
Managing access across teams: The challenge in SOC models
In hybrid and outsourced SOC models, managing access for different stakeholders—including internal security teams, MSSP personnel, and other IT departments—can be complex. Even different teams than security ones may need access to specific data, such as network logs for infrastructure team, without being exposed to broader security intelligence. This situation calls for fine-grained control over permissions, ensuring teams only access the data necessary for their role, while maintaining strict data segregation to prevent unauthorized exposure.
Effective access management becomes increasingly complex as organizations rely on both internal and external teams, requiring robust security tools to manage permissions and safeguard sensitive information.
How Sekoia Defend streamlines SOC access management
Sekoia Defend addresses these access challenges with two standout features: multi-tenant support and data segregation by Intakes (data sources). These features offer flexibility and control, allowing organizations to segment security environments and manage data access with precision.
Multi-Tenant architecture: Enhancing large operations
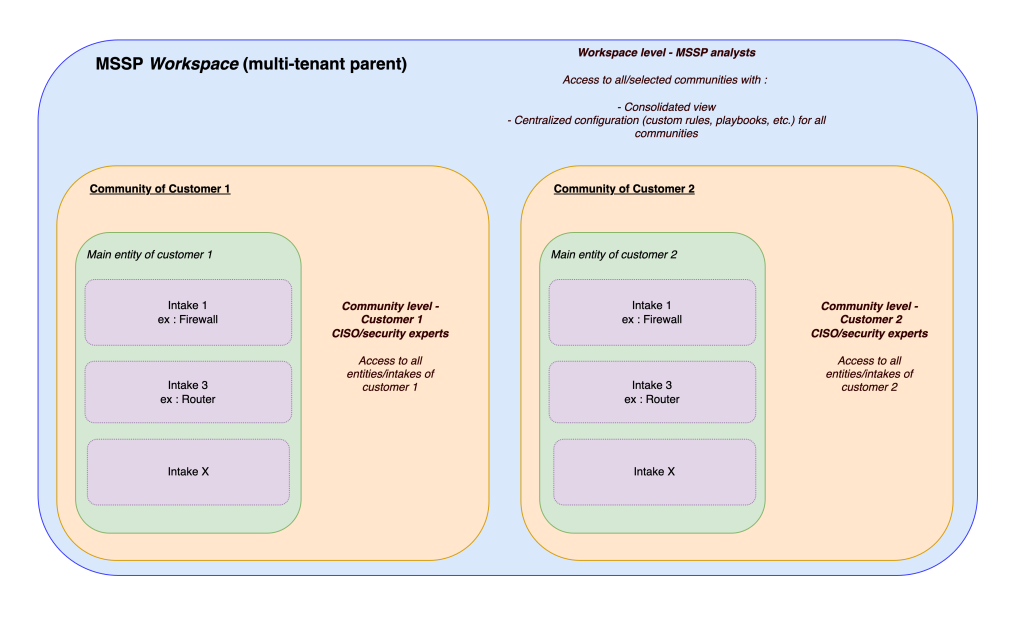
For MSSPs managing multiple clients or large companies managing multiple subsidiaries, multi-tenant architecture is crucial. Sekoia Defend allows to operate a parent tenant (called “workspace”) to oversee all clients, while each client is provided with an isolated child tenant (called ****“community” ****in the product). This ensures complete data segregation between clients while enabling centralized management from the parent tenant. MSSPs or large companies can customize security configurations for each client, maintaining full control without cross-contaminating environments. This structure simplifies complex environments, enabling flexible management of security operations across multiple structures.
Entities & Intakes: The foundation for segmentation
In Sekoia Defend, an entity represents a distinct organizational unit within a community. Each entity serves as a functional container for grouping related resources and data, which simplifies both data management and access control. This structure allows organizations to manage multiple departments, teams, or subsidiaries within a single platform. Intakes in Sekoia Defend act as the primary gateway for data ingestion. Each intake is a specialized entry point that processes various types of data, such as logs and alerts, from different sources. This system ensures data is efficiently parsed and normalized for accurate analysis. Each Intake needs to be configured within an entity in the platform, allowing accurate segregation of data through Sekoia Defend’s RBAC model.
Role-Based Access Control (RBAC): Ensuring secure permissions
Sekoia Defend’s RBAC is an essential security model designed to restrict system access to authorized users based on their specific roles within a community. Each role corresponds with a set of permissions that dictate what actions a user can perform and which part of the product they can access. This method enhances overall security by ensuring that users have only the permissions necessary to perform their job functions, thereby reducing the risk of data breaches or unauthorized actions. The platform offers three built-in roles: Admin, Analyst, and Guest. Additionally, in Sekoia Defend’s Prime plan, administrators have the flexibility to create custom and/or restricted roles that are tailored to the specific needs of their organization.
Restricted roles to segregate access to data by Intakes
Thanks to this RBAC model, Sekoia Defend allows data segregation through Intakes. Access to these Intakes can be controlled by intake restricted roles, enabling organizations to compartmentalize data streams so that only users with the appropriate permissions can access specific subsets of data in a read-only mode, accessing to this specific events & alerts only. This integrated approach between custom roles and Intakes adds an additional layer of security by ensuring that data segregation aligns with organizational requirements. By combining RBAC with data segregation through Intakes, Sekoia Defend provides a robust framework for managing permissions, aligning closely with both security best practices and compliance requirements.
This architecture of entities, intakes and RBAC model forms the backbone of Sekoia Defend’s flexible and secure data handling system, enabling organizations to efficiently manage and analyze their security data while maintaining strict control over data access and processing.
You will find some use-cases below showcasing the benefits of this architecture in different environments.

Use-cases
Multi-Tenant architecture: Simplifying complex environments
Use Case 1: MSSP managing multiple clients
As the head of a Security Operations Center (SOC) within an MSSP, you are tasked with protecting the IT infrastructures of multiple clients, each with unique requirements. Sekoia Defend’s multi-tenant feature allows you to configure a parent tenant (Workspace) to centralize your operations while creating child tenants (communities) for each client.
With this architecture, you can:
- Completely separate the environments of each client, ensuring their logs, incidents, and data remain isolated.
- Administer each child tenant independently while maintaining global control over all environments from the parent tenant.
- Tailor detection rules and playbooks to the specific needs of each client without risking cross-contamination of security configurations.

Use Case 2: Large companies with subsidiaries
Consider a multinational corporation with several subsidiaries worldwide. As the Chief Information Security Officer (CISO), you need to ensure that each subsidiary’s security is managed appropriately while maintaining centralized oversight from headquarters. The multi-tenant feature of Sekoia Defend allows you to create a parent tenant for headquarters and child tenants (communities) for each subsidiary, enabling you to:
- Grant local teams in each subsidiary control over their security environment only while maintaining centralized visibility and governance from headquarters.
- Customize security strategies based on the regional or operational specifics of each subsidiary while ensuring global consistency in incident management.
This approach simplifies incident response management and aligns security practices with the specific needs of each entity.

Data segregation by Intakes: Fine-tuned data access control
Use Case 3: Managing access for IT and security teams
Not all IT teams need access to the same data. For example, a network infrastructure team may only require access to network logs, whereas a security team needs broader access across all logs to monitor for threats. Sekoia Defend’s data segregation by Intakes ensures:
- Specific teams can only access data relevant to their responsibilities.
- Security teams can monitor the entire environment without compromising data segregation.
- Each team operates within its scope, reducing unauthorized access risks.
This feature enables organizations to efficiently manage responsibilities and ensure data confidentiality.

Maximizing Efficiency by Combining Multi-Tenant and Data Segregation
Use Case 4: Managing global security in international groups
By combining the multi-tenant and data segregation features, you can optimize security management in complex environments. Take the example of an international group with multiple subsidiaries, each having specialized IT teams (network, security, systems administration).
With this combination:
- The parent tenant (headquarters) oversees global security with comprehensive visibility across all subsidiaries.
- Each child tenant (subsidiary) has its own local IT teams, with restricted access to specific data based on their responsibilities. For example, the network infrastructure team at a subsidiary can access only network logs, while the security team has access to all logs.
This hybrid approach not only segments environments between different entities but also provides fine-grained access control within each subsidiary. Teams can work autonomously within their respective areas, while benefiting from the central protection and supervision of the parent tenant.

Use Case 5: MSSPs streamlining operations
For MSSPs, combining multi-tenant and data segregation features streamlines operations by:
- Isolating client environments for secure management.
- Allowing each client to manage their internal access controls.
- Tailoring security services to each client’s needs while ensuring strict data isolation.
This combined approach supports scalability and ensures the highest levels of client data protection.

Conclusion: Empowering security operations with Sekoia Defend
Sekoia Defend’s multi-tenant and data segregation by Intakes features provide an unparalleled solution for managing complex security environments. Whether for large enterprises or MSSPs, these features offer:
- Granular data access control to protect sensitive information.
- Centralized management for better oversight of distributed teams or clients.
- Operational flexibility to customize security workflows to specific needs.
By leveraging these features, organizations can optimize their SOC operations, enhance data security, and streamline access management, ensuring a robust and adaptable cybersecurity infrastructure.
Thank you for reading this blogpost. Feel free to share your feedback, and read other contents:
如有侵权请联系:admin#unsafe.sh