2024-7-19 00:56:5 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
If you work in cybersecurity, follow regulatory changes, or are part of the industry, you’ve likely been closely monitoring recent regulatory developments. The SEC’s cybersecurity incident disclosure rules and the EU’s Cyber Resilience Act (CRA), have pushed organizations to reevaluate and reshape their strategies. Now, with the rapid advancement of AI, it’s time for responsible use and stricter regulatory oversight.
While the secure development and use of AI is not regulated yet, one notable cybersecurity regulation from last year was the SEC’s new rules on cybersecurity risk management and incident disclosure. It now requires public companies to:
- Disclose significant cyber incidents to the SEC within four business days.
- Provide detailed information about their board’s oversight of cybersecurity risks.
To better understand the impact of these changes, we partnered with Sapio Research to survey 500 cybersecurity decision-makers from large enterprises in the US and UK. Download the full report: 2024 Regulation vs. Reality: Are the Fed’s Attempts at Wrangling Incident Disclosure Effective?
The Cost of Neglecting Cybersecurity Regulations
As the Chief Information Security Officer (CISO) of Swimlane, I’ve seen firsthand how regulatory changes are reshaping our industry, and what happens if you neglect them. For example, high-profile incidents like the ransomware attack on Change Healthcare, have continually decreased public trust.
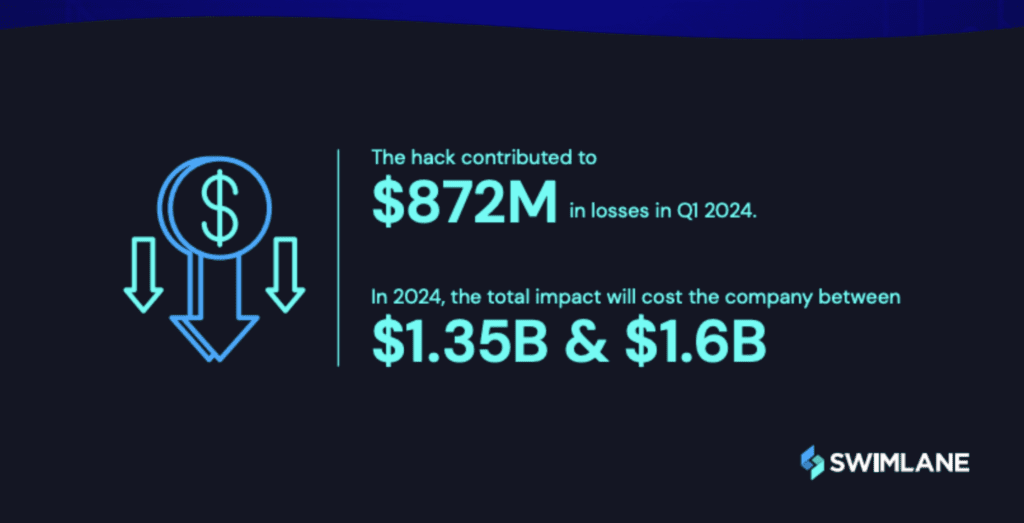
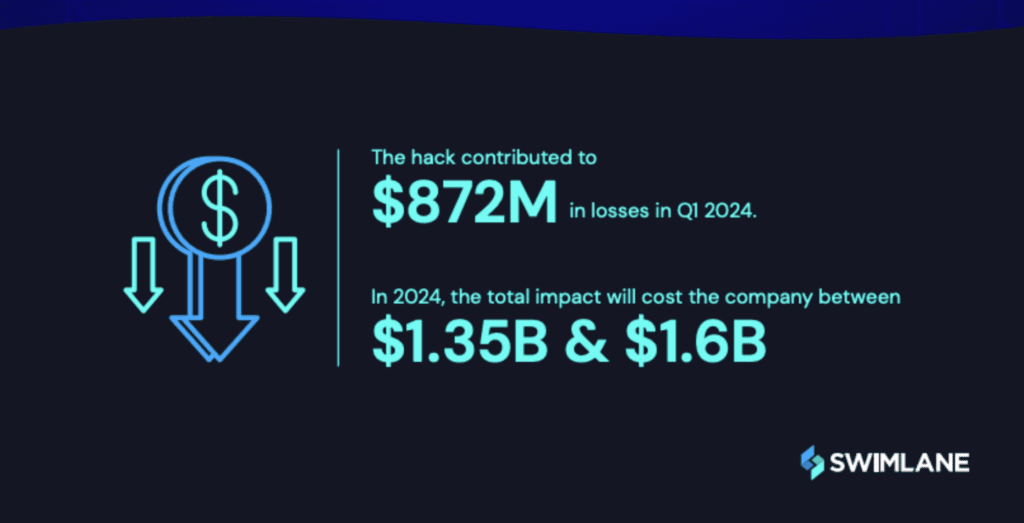
The Change Healthcare ransomware attack is one of several incidents this year that highlights the severe repercussions organizations can face if they neglect risk management. This includes:
- Reputational damage
- Financial losses
- Business Downtime
- Sensitive data loss
Look at that number again… $1.6B could be the total financial impact on Change Healthcare. In my recent blog, The “Materiality” Mystery: A CISO’s Guide to SEC Compliance, I highlighted the importance of understanding the definition of materiality, the risks, and the potential financial impact if you don’t. Some financial impacts include legal fees, regulatory fines, remediation costs, and customer notifications. Another major issue under the SEC’s cybersecurity regulations is the unclear definition of “materiality”. Without clear guidance, organizations must be proactive to define what’s a “material” cybersecurity incident.
With this in mind, it’s safe to say the recent heightened regulatory scrutiny is crucial to rebuilding trust and ensuring companies prioritize cybersecurity.
3 Proactive Cybersecurity Tips to Address Regulations
Meeting recent regulatory requirements involves numerous “to-do’s” and SecOps tactics. However, it’s important to distinguish between simply meeting compliance and truly building a proactive risk management strategy. Doing the bare minimum and settling for “good enough” security won’t protect your organization. Don’t just take my word for it—look at the numerous companies that suffered from data breaches and cyber attacks in 2024 alone.
Here are three ways you can be proactive with risk management strategies:
- Implement Company-Wide Cybersecurity Expertise
The “check-the-box” approach falls short time and time again. As leaders, we must commit from the top down to cybersecurity. This commitment is essential for mitigating risks and preventing cyber attacks.
This starts with board-level cybersecurity expertise. Our recent report highlights:
- 81% said that all companies with a Board of Directors should have at least one member with cybersecurity expertise.
- Although, only 55% of respondents said they have one board member with cybersecurity expertise.
Investing in the right cybersecurity tools and training for your team will significantly enhance your overall processes. This proactive approach ensures that everyone, from entry-level employees to top executives, understands the importance of cybersecurity and is prepared to respond effectively to incidents with the correct tools in place. Doing so will bolster defenses, improve risk management, streamline incident response, and create a more resilient organization.
Keep in mind, governance and compliance does not equal risk reduction or improved cybersecurity. However, security posture, resilience, technical controls, and Zero Trust does. You must master the basics first.
- Shift Focus in Cyber Event Disclosure
Organizations need to shift focus when disclosing cyber events to regulators and the public eye. It’s important to move beyond the technical aspects of a cyber event and evaluate broader financial, operational, and reputational risks for accurate reportability. Our report states:
- Only 25% of respondents report security incidents within 3-4 business days.
- And 43% have faced longer reporting times over the past year.
This highlights the challenge many organizations have in maintaining quick and streamlined processes. However, utilizing a security automation platform, like Swimlane Turbine, can help remediate this problem.
- Automate Incident Response
Leverage playbooks to automate incident response processes. This streamlined approach facilitates quicker decision-making, empowering organizations to respond swiftly to cybersecurity incidents and promptly mitigate risks. At Swimlane, we leverage our own security automation platform to build incident response playbooks. This results in simpler processes that allow me to make informed decisions and report critical incident response details more clearly to the leadership team.
Balancing Human Expertise and AI-Enhanced Automation
When you prioritize a balance between human expertise and AI-enhanced automation tools, you alleviate operational strain. It’s time to automate routine tasks like threat detection and log analysis to free up security professionals for critical, judgment-based decisions. This boosts efficiency and effectiveness, ultimately making decision-makers more confident in their ability to stay compliant.
As your organization adapts to new regulations and cybersecurity challenges I hope that these insights help guide you toward resilience and proactive risk management. Meanwhile, I hope all my fellow security leaders connect with me on LinkedIn to further proactive conversations.
Are the Fed’s Attempts at Wrangling Incident Disclosure Effective?
Download the full research report now to understand how these regulatory shifts are impacting security practices and compliance strategies. Read the report to learn more about how the regulatory environment is impacting cybersecurity strategies, priorities, and budgets.
如有侵权请联系:admin#unsafe.sh