2024-7-18 00:35:33 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
First Annual Report Analyzes Millions of Vulnerabilities Against the Industry’s First Supply-Chain Specific Attack Matrix
Software is the foundation on which today’s businesses operate. From standard enterprise applications like customer relationship management (CRM), enterprise resource planning (ERP), and business intelligence (BI), to custom-built applications tailored for specific business use, it’s hard to find an organization — big or small — that doesn’t rely on software as an element of day-to-day operations. As reliance grows, so does its attractiveness to cybercriminals.
Threat actors often target the path of least resistance to enact harm. In many cases, that target is software. Many enterprise applications are ubiquitous across companies, making them attractive targets. For instance, if an exploitable vulnerability is found in Salesforce, HubSpot, or Monday.com, a threat actor could use that one entry point to compromise a large number of companies, as seen in the MOVEit, Microsoft (2023), and SolarWinds breaches.
Another significant issue is the prevalence of reused code. While code reuse isn’t inherently risky, any bugs or vulnerabilities in reused code increase opportunities for exploitation and expand attack surfaces. This risk is especially high when reused code is open source, which is present in 70-98% of applications. For instance, vulnerabilities like the Log4Shell flaw in Apache Log4j can allow remote execution in any software containing the compromised code. Additionally, tracking down code, its components, dependencies, users, and build environments to find potential exposures presents a major challenge for security teams.
With all of the above it’s no surprise that Software supply chain attacks continue to rise and according to OX researchers, Ninety-five percent (95%) of organizations had at least one high, critical, or apocalyptic risk within their software supply chain and AppSec teams struggle to prioritize the hundreds of thousands of alerts generated by their security tools, leaving applications vulnerable to attack.
Unveiling Software Supply Chain Risks
Researchers at OX Security are focused on learning more about software supply chain risk and how adversaries view and target the cyber attack surface. In a new report entitled “OSC&R in the Wild: A New Look at the Most Common Software Supply Chain Exposures,” the researchers release their findings from a nine-month analysis of over 100 million software supply chain alerts and tens of thousands of code repositories and cloud-deployed applications.
This new report doesn’t simply detail the findings; it presents a holistic methodology that can be used by AppSec and broader security teams to investigate, analyze, and understand application and adversarial behaviors. Developed collaboratively by cybersecurity veterans from OX Security, Microsoft, Oracle, GitLab, Fortinet, FICO, and more, the Open Software Supply Chain Attack Reference (OSC&R) framework is a MITRE ATT&CK-like framework that gives organizations a single point of reference for proactively assessing strategies to secure their software supply chain and evaluate the effectiveness of their AppSec programs.
The Challenge of Identifying and Mitigating Severe Security Risks in Software Development
Our analysis indicates that detecting and remediating severe security risks from within the mountain of benign code hygiene alerts issued by traditional AppSec technologies continues to be a challenge and serious vulnerabilities are passing to production code with concerning regularity. Many applications were found to contain multiple vulnerabilities spanning various stages of the kill-chain, leaving them even more vulnerable to a successful attack. A surprising number of vulnerabilities were found quite frequently despite having been documented for years.

Key Findings
AppSec Teams Face an Unmanageable Volume of Alerts:
Based on the active applications collected by our researchers over a nine-month period, security teams must monitor 129 applications and manage over 119,000 alerts per organization on average.
Most Organizations Face High Severity Risks:
Ninety-five percent of organizations had at least one high, critical, or apocalyptic risk within their software supply chain, with the average organization having nine such issues.
One in Five Applications Contain Run-Time Exposure:
Analysis against attack phases showed that 20% of all applications have high, critical, or apocalyptic issues during execution, where attackers aim to deploy malicious code. The most significant number of security issues are typically found in later attack phases, when the potential impact on business operations is higher.
Older Vulnerabilities are Still the Most Common:
While some newer tactics did appear, the three most frequently observed vulnerabilities: command injection (15.4% of applications), sensitive data in log files (12.4% of applications), and cross-site scripting (11.4% of applications) have all been around for many years.
Vulnerabilities Across Multiple Attack Stages Offer Fertile Ground for Attack:
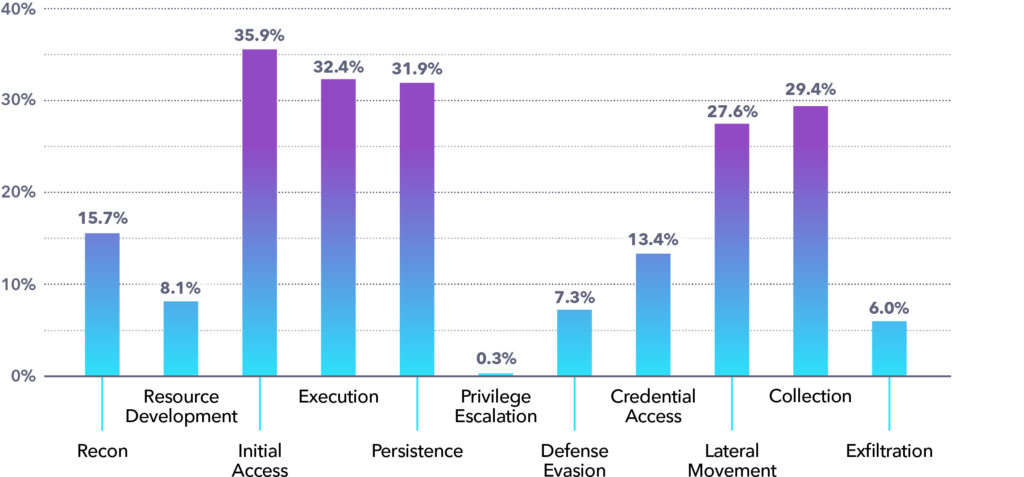
36% of applications were vulnerable to exploits in the Initial Access attack stage. 20% of those were also vulnerable to either Persistence or Execution exploits, and 12% were found to contain vulnerabilities tied to tactics in all three stages.
Automated Alert Analysis Helps Find the Signal in the Noise:
Using a combination of automated consolidation and contextual analysis technologies, our researchers reduced the massive volume of unscrubbed alerts by more than 97%, enabling them to isolate those alerts representing a high, critical, or apocalyptic risk (our three highest rankings of severity).
Final Thoughts
One of the questions this analysis sought to answer was whether there was alignment between the vulnerabilities found in the wild and the focus of AppSec teams. The data suggests that these are not yet aligned. We found significant volumes of vulnerabilities at the beginning, middle, and end stages of the kill chain, indicating that companies are still vulnerable to high-impact vulnerabilities. Progress is being made, but the high volume of vulnerabilities that are passed through the supply chain into live applications, and the large percentage of organizations reporting supply chain security incidents both indicate that greater focus could be put on proactive measures. For example, by integrating OSC&R with Application Detection and Response (ADR) and Application Security Posture Management (ASPM), users can create a dynamic and resilient security posture that continuously evolves to meet emerging threats. This approach not only enhances threat detection and response capabilities but also fosters a culture of continuous improvement and adaptation within an organization’s security practices.
Download the full OSC&R in the Wild: A New Look at the Most Common Software Supply Chain Exposures report here.
For information on how OX can help detect and reduce software supply-chain risk, schedule a call with one of our application security experts.
The post OSC&R Report Exposes Software Supply Chain Security Vulnerabilities appeared first on OX Security.
*** This is a Security Bloggers Network syndicated blog from OX Security authored by Melissa Goldberger. Read the original post at: https://www.ox.security/oscr-report-exposes-software-supply-chain-security-vulnerabilities/
如有侵权请联系:admin#unsafe.sh