2024-7-17 19:56:26 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Email security tools such as Secure Email Gateways (SEGs) often encode URLs that are embedded in emails. This enables the security appliance to scan the URL before the recipient visits the website. Oftentimes when SEGs detect URLs in emails that are already SEG encoded they do not scan the URLs, or the scanning shows only the security tool’s scanning page and not the actual destination. As a result, when an email already has SEG encoded URLs the recipient’s SEG often allows the email through without properly checking the embedded URLs. Threat actors have abused this for some time, but Q2 of this year, and May in particular, saw an increase in threat actors taking advantage of SEG encoding malicious URLs before sending them to victims.
Tools Used in The Wild
The 4 tools most commonly seen in use by threat actors to encode URLs and bypass SEGs in Q2 2024 are VIPRE Email Security, BitDefender LinkScan, Hornet Security Advanced Threat Protection URL Rewriting, and Barracuda Email Gateway Defense Link Protection. Email campaigns using these tools to bypass SEGs have been seen in environments protected by everything from Proofpoint to Microsoft ATP.
VIPRE Email Security
URLs encoded by VIPRE Email Security, especially URLs encoded by url[.]emailprotection[.]link were seen with 12 unique subjects in early June 2024. These emails had subjects similar to the following subset:
| Common Email Subjects |
| Review & Sign: Partnership_Investment_Proposal.DOCX |
| New Contract and Termination Agreement.pdf |
| You have a new encrypted VM from <recipient name or identifiable information> |
| Complete: Increment Policy and Standard Termination Agreement.pdf. |
| Salary Compensation Report 2024 |
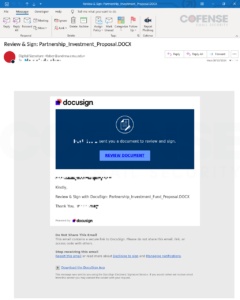
Figure 1: Email with embedded URL encoded by VIPRE Email Security’s url[.]emailprotection[.]link.
URLs encoded with VIPRE Email Security’s other encoding URLs: url2[.]mailanyone[.]net, url10[.]mailanyone[.]net, url12[.]mailanyone[.]net, etc. were seen primarily in May of 2024 with over 200 unique subjects. These emails had subjects similar to the following subset:
| Common Email Subjects |
| 7167-<recipient name or identifiable information>: Accept the proposal and return |
| One Time Authentication Prompt |
| Notification Access #27 -May 15, 2024, 07:49:27 AM |
| 8533-<recipient name or identifiable information>: Sign and Return to process |
| <recipient name or identifiable information> Termination Agreement……623.docx |

Figure 2: Email with embedded URL encoded by VIPRE Email Security’s url10[.]mailanyone[.]net.
BitDefender LinkScan
URLs encoded by BitDefender LinkScan, especially URLs encoded by lsems[.]gravityzone[.]bitdefender[.]com were seen most often in early June 2024 with 8 unique subjects. These emails had subjects similar to the following subset:
| Common Email Subjects |
| Urgent Action Required: Secure Email Alert !!! |
| Oops, We Withheld Some Messages From you June 09 Case- #UMMQEGA7 |
| <recipient name or identifiable information> e-Secure/e-File/0B6UCG Tuesday, June 11, 2024 |
| Timesheet Update Notification: View Ref-VJ7N8GO012P changes made to your timesheet |
| Report Ticket 0168724 For <recipient name or identifiable information> |
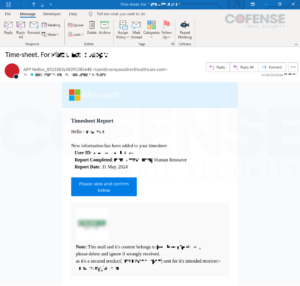
Figure 3: Email with embedded URL encoded by BitDefender LinkScan’s lsems[.]gravityzone[.]bitdefender[.]com.
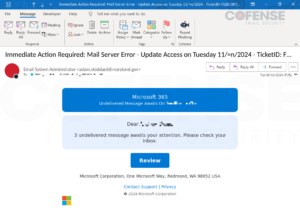
URLs encoded with BitDefender LinkScan’s other encoding URL, linkscan[.]io, were only seen in two campaigns in June of 2024. These emails had subjects similar to the following subset:
| Common Email Subjects |
| Immediate Action Required: Mail Server Error – Update Access on Tuesday 11/Jun/2024 – TicketID: LCCP-YLSNYA-FLLWK |
| Time-sheet For <recipient name or identifiable information> |
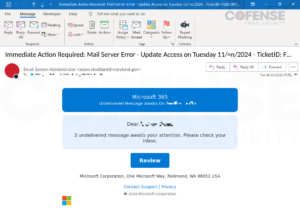
Figure 4: Email with embedded URL encoded by BitDefender LinkScan’s linkscan[.]io.
Hornet Security Advanced Threat Protection URL Rewriting
URLs encoded with Hornet Security Advanced Threat Protection URL Rewriting (seclinks[.]cloud-security[.]net) were seen primarily in late May and early June of 2024 with 8 unique subjects. These emails had subjects similar to the following subset:
| Common Email Subjects |
| PVX #5LOA: Complete: Please Sign&Return #Ref-D786DYY37B(2) |
| Oops, We Withheld Some Messages From you June 09 Case- #UMMQEGA7 |
| <recipient name or identifiable information> e-Secure/e-File/0B6UCG Tuesday, June 11, 2024 |
| Timesheet Update Notification: View Ref-VJ7N8GO012P changes made to your timesheet |
| Time-sheet Submission: Please confirm your new time-sheet |

Figure 5: Email with embedded URL encoded by Hornet Security Advanced Threat Protection URL Rewriting’s seclinks[.]cloud-security[.]net.
URLs encoded with Hornet Security Advanced Threat Protection URL Rewriting’s other encoding URL, atpscan[.]global[.]hornetsecurity[.]com, were only seen in campaigns in late May and early June of 2024 with 16 unique subjects. These emails had subjects similar to the following subset:
| Common Email Subjects |
| Approved for only 83574 – <recipient name or identifiable information> |
| #0IU6IB Review Monday, June 10, 2024 |
| YV8 72Q: Sign&Return #Ref-JB0UOYAY19P |
| 4700-27Z Please complete: Sign&Return #Ref-04020427Z |
| Action Required: We witheld 9 messages from you. |

Figure 6: Email with embedded URL encoded by Hornet Security Advanced Threat Protection URL Rewriting’s atpscan[.]global[.]hornetsecurity[.]com.
Barracuda Email Gateway Defense Link Protection
URLs encoded by Barracuda Email Gateway Defense Link Protection, especially URLs encoded by linkprotect[.]cudasvc[.]com were seen with 19 unique subjects in Q2 2024. These emails had subjects similar to the following subset:
| Common Email Subjects |
| #23321041 |
| Your DocXXX Await Your Approval Ref:#ezgyo4r |
| Comprehensive Wellness Program for <recipient name or identifiable information> Employees |
| Your DocXXX Await Your Approval Ref:#hlufnew |
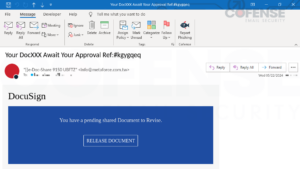
Figure 7: Email with embedded URL encoded by Barracuda Email Gateway Defense Link Protection’s linkprotect[.]cudasvc[.]com.
Types Of Campaigns Seen Using SEG Encoded URLs
There were many different types of campaigns making use of SEG encoded URLs in Q2. Some of the most common themes were content requiring a signature and voicemail or withheld email notifications. As can be seen from the above Figures, DocuSign and Microsoft were often spoofed.
DocuSign
A large number of campaigns themed around content requiring a signature spoofed DocuSign. Despite this spoofing, relatively few of the campaigns made use of an actual DocuSign link which is not uncommon among Credential Phishing emails spoofing DocuSign. This is likely because the DocuSign links are typically used to bypass SEGs and if the threat actor is already bypassing a SEG by encoding the malicious URL then they have no need for an extra step that might get taken down.
Microsoft
Second only to DocuSign, Microsoft was the most commonly spoofed brand in email campaigns making use of SEG encoded URLs in Q2 2024. Although not all the Microsoft spoofing made sense, for example, the Microsoft spoofing Time Sheet Report in Figure 3, it was still commonly seen. This is a common tactic for threat actors seeking to abuse victims’ inherent trust in well-known brands.
The post SEG vs. SEG: How Threat Actors are Pitting Email Security Products Against Each Other With Encoded URLs appeared first on Cofense.
*** This is a Security Bloggers Network syndicated blog from Cofense authored by Hillary Long. Read the original post at: https://cofense.com/blog/seg-vs-seg-how-threat-actors-are-pitting-email-security-products-against-each-other/
如有侵权请联系:admin#unsafe.sh