In modern cybersecurity operations, threat hunting has become an essential proactive defense strategy. Leveraging Security Orchestration, Automation, and Response (SOAR) playbooks enhances this activity, making it more efficient and effective. This blog will explore how SOAR playbooks can revolutionize threat hunting by automating complex workflows, facilitating rapid response, and enhancing overall security posture.
Understanding Threat Hunting
Threat hunting involves actively searching for signs of malicious activities within an organization’s network before any alarms are triggered by automated defense systems. Unlike traditional reactive approaches, threat hunting is proactive and aims to identify threats that have slipped past initial defenses. This requires advanced analytics, threat intelligence, and expert knowledge to uncover sophisticated threats.
The Role of SOAR in Threat Hunting
SOAR platforms integrate various security tools and processes, providing a unified interface for incident response and threat hunting activities. Key features of SOAR include:
- Orchestration: Integrates disparate security tools and systems to work together seamlessly.
- Automation: Automates repetitive tasks to enhance efficiency and consistency.
- Response: Facilitates rapid response to identified threats with predefined actions.
Regularly occurring activities, such as SBOM analysis and vulnerability assessments, can be time-consuming and often get overlooked when the security team is overwhelmed with alerts and urgent short-term tasks. To address these challenges, Smart SOAR enables users to build and deploy scheduled automations that handle essential security processes, including threat hunting.
The threat hunting capabilities in Smart SOAR are extensive, thanks to its built-in long-term data storage and advanced artifact repository. Users can search through event or incident data and query any connected tools to compile a comprehensive view of activity. This holistic approach to data allows security teams to uncover patterns and anomalies that may indicate a security threat.
Key Components of SOAR Playbooks
A SOAR playbook is a set of automated procedures that guide the response to specific types of threats. Key components include:
- Trigger: The event or condition that initiates the playbook.
- Actions: The steps taken to investigate and respond to the threat.
- Decision Points: Conditional logic that guides the flow of actions based on the information gathered.
- Notifications: Alerts and reports sent to stakeholders during and after the playbook execution.
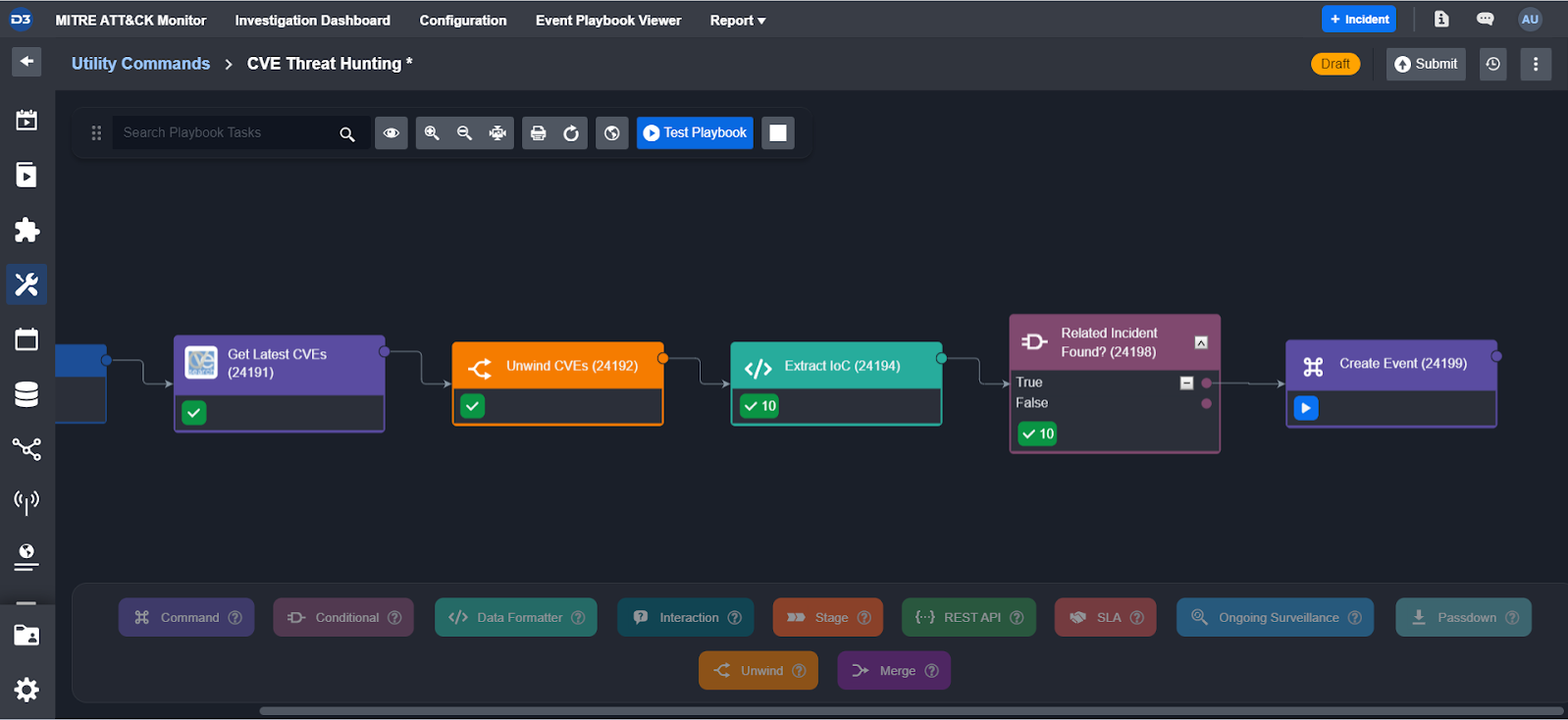
Example SOAR Playbook: Internal CVE Search
This workflow exemplifies how Smart SOAR can automate threat hunting:

- Pull Latest CVEs: The system retrieves the latest Common Vulnerabilities and Exposures (CVEs) from a trusted source. Each CVE includes critical information such as the date of modification, publication date, CVSS score, related references, and a summary of the vulnerability.
{
"Modified": "2024-07-03T21:15:00",
"Published": "2024-04-30T19:15:00",
"id": "CVE-2024-3411",
"summary": "Implementations of IPMI Authenticated sessions does not provide enough randomness to protect from session hijacking...",
"references": [
"https://kb.cert.org/vuls/id/163057", "https://www.intel.la/content/dam/www/public/us/en/documents/specification-updates/ipmi-intelligent-platform-mgt-interface-spec-2nd-gen-v2-0-spec-update.pdf",
"https://www.dell.com/support/kbdoc/en-US/000226504/dsa-2024-295-security-update-for-dell-idrac8-ipmi-session-vulnerability"
]
}
- Process Each CVE: Each CVE is processed as a unique instance, extracting Indicators of Compromise (IoCs) or vulnerabilities to use as keywords for searching through Smart SOAR’s incident database.
- Incident Matching: If a matching incident is found in the database, the system generates an alert with relevant information attached and notifies the investigator for further action.
Advantages of Automated Threat Hunting
Automated threat hunting with Smart SOAR offers several key benefits:
- Proactive Security: By continuously monitoring and hunting for threats, organizations can stay ahead of potential security issues. This proactive approach minimizes the window of opportunity for attackers and helps in mitigating risks before they can cause significant damage.
- Time Efficiency: Automated processes save valuable time and ensure consistency in threat detection and response. Manual threat hunting is labor-intensive and prone to human error, but automation ensures that these tasks are performed accurately and swiftly.
- Utilization of Active Data: The system leverages data from both internal and external sources, providing a comprehensive view of potential threats. This integration of diverse data sources enhances the accuracy and depth of threat analysis.
- Integration with Case Management: Identified risks are seamlessly integrated with case management systems, ensuring they are promptly addressed by the SOC. This integration streamlines the workflow and enhances the efficiency of incident response.
Key Takeaways
Integrating SOAR playbooks into threat hunting operations is a game-changer for cybersecurity teams. By automating routine tasks and orchestrating complex workflows, organizations can enhance their ability to detect, investigate, and respond to threats quickly and efficiently. As cyber threats continue to evolve, leveraging SOAR technology will be crucial in maintaining a robust security posture and staying ahead of adversaries.
Investing time and resources into developing and refining SOAR playbooks will pay dividends in the long run, ensuring that your threat hunting efforts are both effective and resilient.
The post Threat Hunting in Smart SOAR appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Pierre Noujeim. Read the original post at: https://d3security.com/blog/threat-hunting-in-smart-soar/
如有侵权请联系:admin#unsafe.sh