2024-7-9 17:18:53 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
Reading Time: 5 min

Cloudflare is one of the biggest content delivery network service providers in the world. Cloudflare can be used as your DNS host to add and edit DNS records for various operations. If you wish to enable DMARC, SPF, and DKIM for your domain, and your DNS hosting provider is Cloudflare – this guide is for you!
DMARC or Domain-based Message Authentication Reporting and Conformance is a protocol used to authenticate emails. Domains with DMARC implemented enjoy better security against spoofing, phishing, and impersonation attacks. DMARC also provides visibility into your email’s behavior and delivery channels.
SPF and DKIM are essential processes for email authentication which allows senders to authorize sending sources and make sure attackers in the middle do not alter email contents.
Let’s find out how you can set up SPF, DKIM, and DMARC for Cloudflare with a few easy steps.
How to Add DMARC Record to Cloudflare
You can setup DMARC records in Cloudflare DNS by following these steps:
1. Log in to Cloudflare
2. Select your account and domain.
3. Navigate to DNS > Add Record.
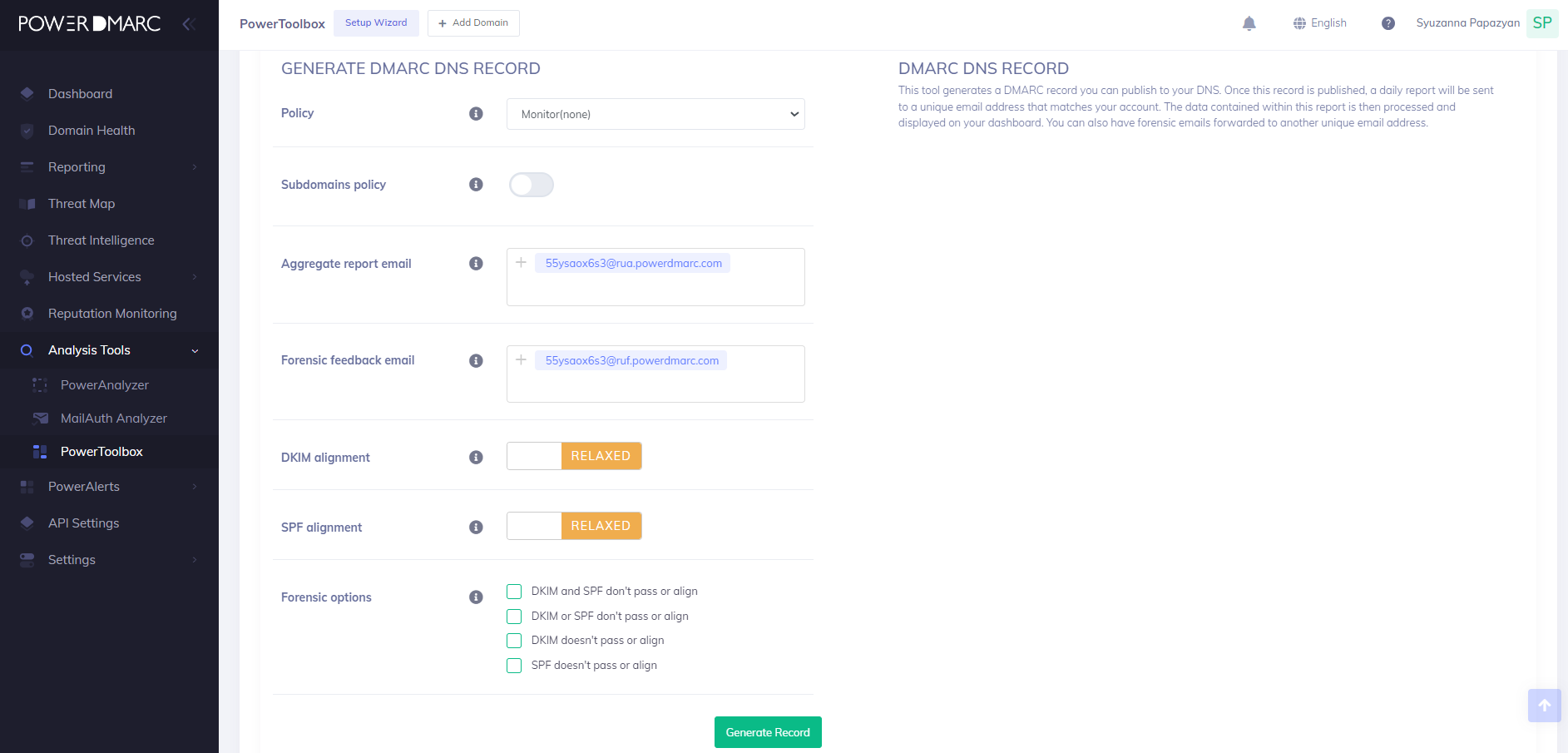
4. Keep this page open and sign up with PowerDMARC for free to access our DMARC record generator tool. Use this tool to create a DMARC record and copy the record syntax.
Note that the v= (version) field and p= (policy) field are mandatory fields in your DMARC Cloudflare record. Omitting any of these two fields will lead to an erroneous record. The value for the v= tag is always DMARC1. Your DMARC policy can be either of the three options depending on how strictly you wish to handle messages that fail DMARC:
1. None: take no action and deliver all emails
2. Reject: Discard emails that fail DMARC
3. Quarantine: Quarantine emails that fail DMARC
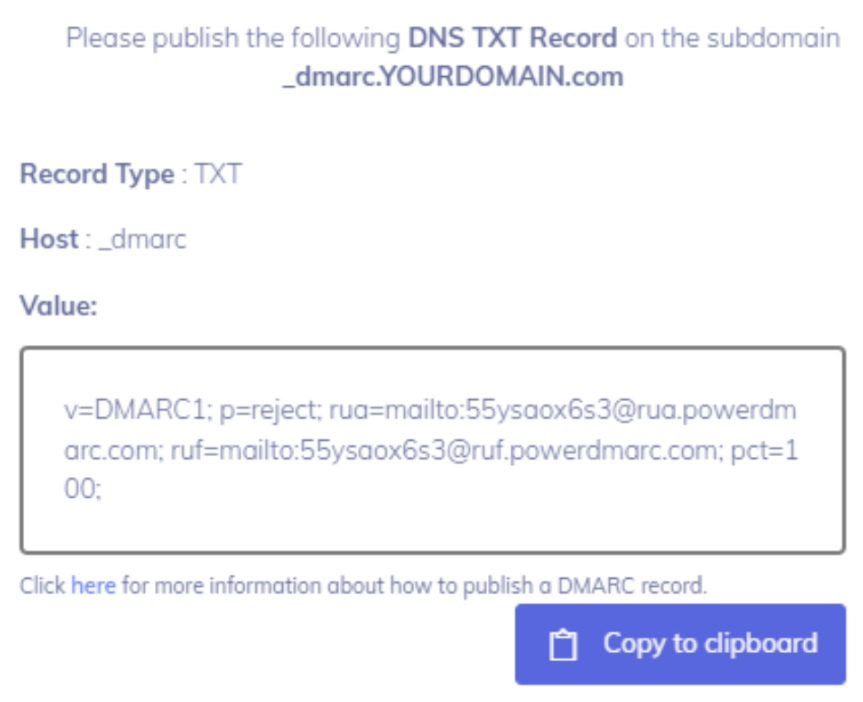
4. Head back to Cloudflare DNS and add your DMARC record, entering the following configurations.
Type: TXT
Name: _dmarc
Content: [paste the contents of your generated DMARC record]
TTL: Auto
Example: v=DMARC1; p=quarantine; rua=mailto:[email protected]; ruf=mailto:[email protected]; pct=100;
5. Click on Save to save changes. Cloudflare may take some time to process these changes.
Editing and Deleting Cloudflare DMARC Records
To edit and delete DMARC record entries for Cloudflare or any DNS records on Cloudflare:
1. Login to Cloudflare
2. Select your account and domain
3. Select DNS > Records
4. Click on Edit to edit the record of your choice and then you can either continue to edit or click Delete to delete the record entry. Confirm your deletion by clicking on Delete again
5.Click on Save to save your changes
How to Add SPF Records to Cloudflare
To add an SPF record to your Cloudflare DNS, follow the steps below:
1. Log in to Cloudflare

2. Select your account and domain.
3. Navigate to DNS > Add Record.
4. Keep this page open and sign up with PowerDMARC for free to access our SPF record generator tool. Use this tool to create an SPF record and copy the record syntax.
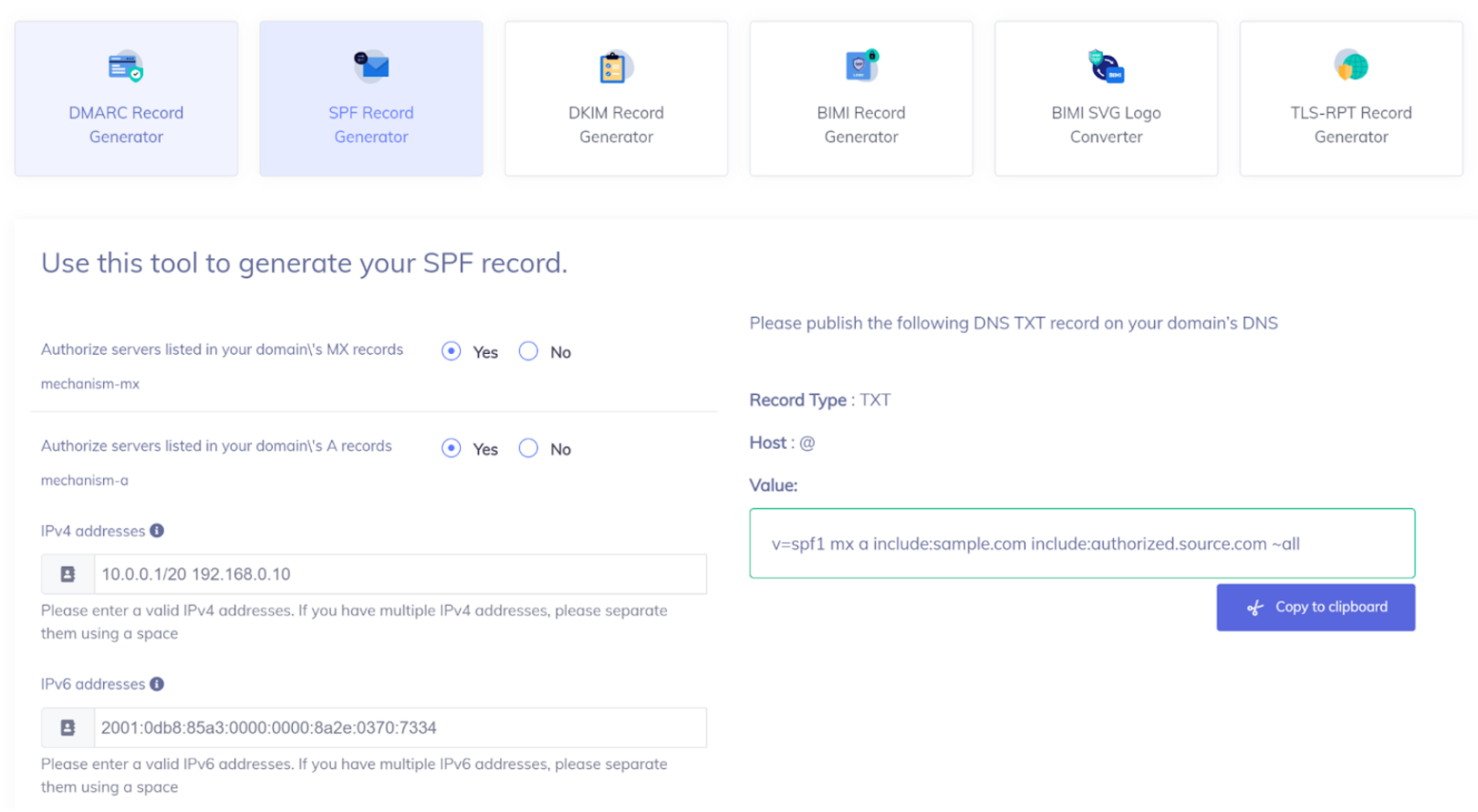
Make sure you are authorizing all your legitimate email sending sources in your SPF record. You can also authorize your third-party email vendors (eg. SendGrid, Google, etc) using the “include” mechanism.
5. Head back to Cloudflare DNS and add your SPF record, entering the following configurations.
Type: TXT
Name: @
Content: [paste the contents of your generated SPF record]
TTL: Auto
Example: v=spf1 mx a include:sample.com include:authorized.source.com ~all
6. Click on Save to save changes. Cloudflare may take some time to process these changes
How to Add DKIM Records to Cloudflare
Note that if you are using third-party email vendors like Google, Microsoft, SendGrid, etc to send your emails, you won’t need to generate DKIM keys manually. You can get in touch with your ESP to learn about the steps to generate DKIM keys directly on the admin portal. You can also refer to our knowledge base for guidance.
However, if you need to generate your DKIM record, we recommend using our DKIM record generator tool for quick and instant record creation with accurate, error-free results!
To add a DKIM record to your Cloudflare DNS, follow the steps below:
7. Log in to Cloudflare

8. Select your account and domain.
9. Navigate to DNS > Add Record.
10. Add the DKIM public key by entering the following:
Type: TXT/CNAME (This field will have value “TXT” if you generate the record using PowerDMARC’s tool, else, it can be a “CNAME” or “TXT” type record depending on the value generated on your ESP’s portal.)
Name: (selector).domainkey.(yourdomain.com)
Content: [paste the contents of your generated DKIM public key or the one provided to you by your ESP]
TTL: Auto
Example: v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAo6qEWvbgBO969zJqeONDkVV8NPA6cz7Arb+E5CVS0PasNRyARAl4ek5FbGUPLqZziAmt8Tp0s4+hENz+feAfiDBnZL72GDsm4JVqJ9Ev08xvfwaY1dsz9cgFFkjb35bi5kug7Ht+adEICnMi5zJ/QyBA8cn3oChWpxx1sDHZsDOUIdwQqa59z7WR0nYlHs16egtZCkbc1mmglWdLw5dxIeCBkoFUsQ90b5dlnnAJkKRKkZh6pNXbbyJFaNYQjDAKGHMRNaUnx19kPc5vugEoGw4rlt5vw1QLs/xOX6bU4COXmLCfBFWdXBe8kqKMV2CnKnBszFjYe68deH3C+1XLVQIDAQAB
11. Click on Save to save changes. Cloudflare may take some time to process these changes.
Verifying DMARC, SPF, and DKIM Records on Cloudflare
Checking your Cloudflare DNS records is essential to ensuring they perform properly at authenticating your emails. You can do so by using the following DNS lookup tools from our portal:
- Cloudflare DMARC record checker
- Cloudflare SPF record checker
- Cloudflare DKIM record checker
Final Words
Enabling email authentication with DMARC, SPF, and DKIM can aid in your battle against brand impersonation. However, the benefits are only visible when done correctly. PowerDMARC automates setup processes, generates DNS records, and provides real-time monitoring and reporting of authentication status.
With policy enforcement capabilities and insights into email traffic, PowerDMARC enables organizations to enhance security, comply with regulations, and maintain a positive email reputation, ultimately protecting against phishing attacks and ensuring the authenticity of their communications.
Get your free DMARC trial today!

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Yunes Tarada. Read the original post at: https://powerdmarc.com/coudflare-dmarc-spf-dkim-setup/
如有侵权请联系:admin#unsafe.sh