2024-6-28 00:1:56 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
By Source Defense
6.27.24 – Initial Findings (Additional Research will Include Updated Date Stamp)
In the past 48 hours, the cybersecurity community has been reporting on a significant incident involving Polyfill[.]io, a widely used JavaScript CDN service. First reports by Sansec flagged the potential impact to 100k websites around the world. Further reporting from Cloudflare indicates that reach may be ten times greater or more. Initial reporting alerted that the service was found to be redirecting unsuspecting website visitors to undesired, potentially malicious websites. Additional research indicates that the domain was found to be serving malware and the research conducted by Source Defense supports this more alarming reality. While this domain has since been shut down, the owners of the domain have stood up a new domain and are making claims that research and reporting is inaccurate/is defamatory. Be wary!
The credible research by Sansec and Cloudflare is supported by our own findings. Our findings show direct evidence of PII and credential harvesting. A number of our clients were found to be running the service and our redaction policies thwarted attempts to steal this data. Our systems show direct evidence of these data theft attempts connected to Polyfill[.}io and there is a strong likelihood that sites without JavaScript management and protection in place have fallen victim to data theft – potentially for a prolonged period of time – at least since February of 2024.
We have also seen an alarming scope of reach and broad exposure through the digital supply chain where 3rd, 4th and nth parties connected to many of the world’s largest websites have been calling upon the malicious domain. In one instance we investigated yesterday, a world renowned, widely used payment service was found to be calling on the malicious domain.
This supports the theory that the impact is likely many times greater than already reported. Action should be taken immediately and investigations should be undertaken to understand the potential exposure / scope of theft of sensitive data.
Understanding the Polyfill Project and the Polyfill[.]io Incident
As with many open source projects, Polyfill was designed to provide the community with a tool to better the internet experience. As a legitimate service, it allowed developers to use the latest web features while ensuring compatibility with older browsers. As many older browser versions do not support modern web features, this JavaScript helped by detecting these browsers and automatically adding necessary code to enable advanced features.
Simple and pretty much standard practice – a third party is used by website owners and/or their partners (i.e. – a third party calls on a 4th party) to provide much needed features to enrich the web experience.
Polyfill[.]io is NOT and has NEVER been connected to the legitimate Polyfill project. A reality that was flagged for the community back in February of this year…but, as with many things in Security – the message didn’t spread as far as it needed.
The Incident
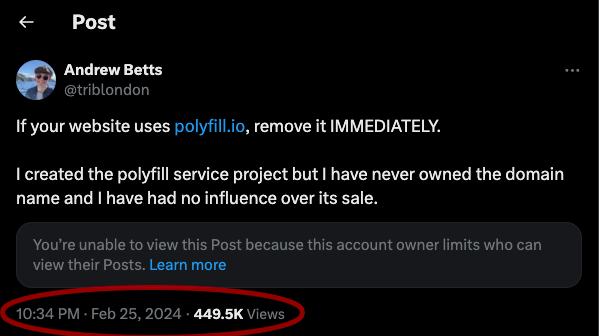
On February 25th of this year, Andrew Betts – the legitimate author behind the project flagged that the domain in question was both illegitimate and potentially harmful. Direct words from Andrew on his X account below:
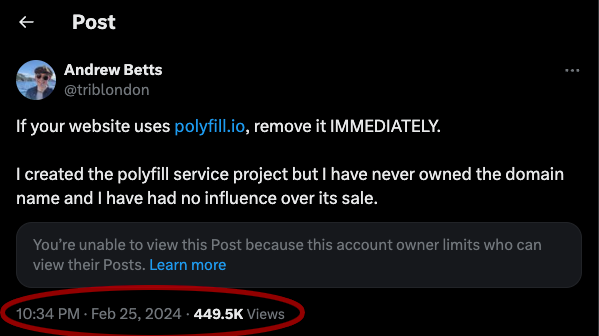
(https://x.com/triblondon/status/1761852117579427975)
Some four months later, we are met with the news that the domain is conducting malicious redirects, dropping malware – and as per our findings, stealing data.
Our Observations at Source Defense
The Polyfill.io incident is a stark reminder of the vulnerabilities inherent in our digital supply chains. At Source Defense, we focus on securing first party and external party (third, fourth, nth party) scripts through real-time monitoring and protection for exactly this reason. Code that is sourced from opensource repositories are a target of adversaries of all types. 3rd, 4th and nth party scripts – many of which are dynamic – cannot be vetted and must have some form of control mechanism in place.
Our proactive measures related to JavaScript management and security ensured that no data was harvested from our client environments – but we still monitor the behavior of these scripts to report on risky and blocked activity.
A quick look into our platform reveals broader malicious activity than what has been reported to this point.
We see signs of attempts to harvest multiple forms of PII and credentials data. In this particular client environment, it should be noted that the FIRST indication of attempts at data theft actually align to the same date that Andrew Betts made his announcement on X.
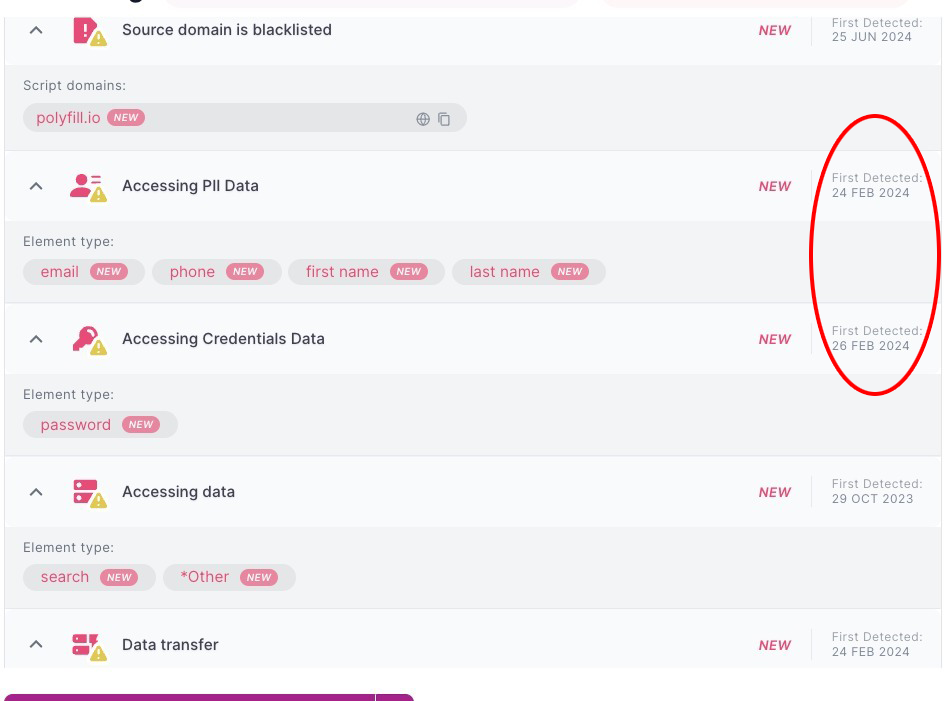
Broad Reach / Exposure Through the Digital Supply Chain
One of the most under recognized issues with the use of JavaScript / with the use of 3rd party partners is the fact that those partners often compile code from other resources or call in additional parties to support their services. In the case of this incident, we see direct evidence of website owners being impacted by their supply chain. As mentioned previously, one incident we investigated yesterday found that a widely used payment service was calling in the Polyfill[.]io domain. The request map shown below demonstrates that relationship / exposure.
Website owner doesn’t directly call on the malicious domain, 3rd party partner does…
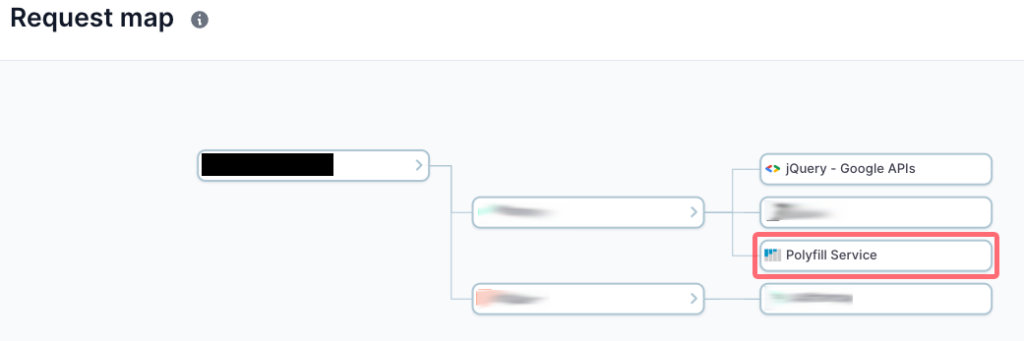
Moving Forward
This incident serves as a powerful reminder that even widely trusted JavaScript libraries can be compromised. Initial validation of third-party scripts is not sufficient; continuous real-time monitoring is crucial. Additionally, vulnerabilities can often stem from fourth-party sources that are beyond the direct control of website owners. Organizations need a robust solution that not only validates these scripts at the start but also actively monitors and prevents vulnerabilities from being exploited over time.
We would encourage all organizations to implement real-time protection systems – whether or not you use Source Defense, this situation highlights the wide scoping vulnerability/gap in web security that we need to address as an industry.
Regular reviews and relying on reputable providers are important, but they are not enough. Real-time monitoring and immediate threat prevention are essential to safeguard against dynamically changing scripts and emerging vulnerabilities.
Source Defense will continue monitoring this situation and provide any updates under a new date stamp to this blog.
The post Polyfill – Additional Analysis and Discovery: Signs of PII and Credential Harvesting, Broad Exposure through Digital Supply Chain appeared first on Source Defense.
*** This is a Security Bloggers Network syndicated blog from Blog – Source Defense authored by [email protected]. Read the original post at: https://sourcedefense.com/resources/blog/polyfill-additional-analysis-and-discovery-signs-of-pii-and-credential-harvesting-broad-exposure-through-digital-supply-chain/
如有侵权请联系:admin#unsafe.sh