2024-6-26 10:47:11 Author: securityboulevard.com(查看原文) 阅读量:4 收藏

Many organizations today use a jump server (also known as jump box or jump host) as the intermediary device to access a remote network securely. It is the go-to solution for remote administration of servers and devices and for development and testing environments. It is also commonly used to control vendor access to an organization’s internal systems and to meet compliance in certain industries.
While this is definitely a step up in security from using VPNs, jump server can sometimes create a false sense of security because there still exists security risks and loopholes.
In this blog post, we will first explore the security benefits and risks of a jump server. Finally, we will unveil strategies to mitigate those security risks.
TABLE OF CONTENTS
Top 5 Security Benefits of a Jump Server
Top 5 Security Risks of a Jump Server
How to Mitigate Jump Server Security Risks Using Best Practices
Mamori Adds Two Additional Layers of Security to Your Jump Host
Top 5 Security Benefits of a Jump Server
1. Central Access Point for Easy Management
When access is centralized, it is easy monitor and manage who access their network, ensuring all access to protected networks are authorized. Centralized access also simplifies managing permissions and security policies. while also making it easier to monitor and log activities.
2. Easy Monitoring and Session Management
With centralized access, monitoring traffic and logging activities are simplified. Jump servers also allow session recording, session timeout, and the ability terminate sessions to enhance control and security.
3. Reduce Attack Surface from external threats
Jump servers should be isolated from the internet and shouldn’t be able to browse the intranet. This reduces the attack surface and adds a layer of defense against external threats.
4. Reduced Exposure
By limiting direct access to critical systems and databases, jump servers minimize the risk of unauthorized access from any unauthorized sources.
5. Simplifying Audit and Compliance
User activity and traffic passing through the controlled central access point can be logged and recorded, which helps meet regulatory.
Top 5 Security Risks of Jump Server
1. Single Point of Failure
A compromised jump server can jeopardize the entire network. Also, a compromised user account, a privileged user, or an infected device can jeopardize the entire system and database the jump server protects.
2. Setup Complications
A simple jump server contains a Windows Server with RDP and user accounts from Active Directory. Additional setup and tools can be used to create more secure policies. In some cases, coding and debugging is required, which makes it difficult to add additional security policies.
3. Misconfigured Architecture and Database Security
A misconfigured architecture can completely bypass the jump server and access privileged resources, as indicated in the image below with the non-privileged resource. If the non-privileged resource is compromised, then the privileged resource can be accessed, bypassing the jump server. Because privileged resources are usually databases, many mistakenly think that jump server protects the database. Although jump servers do protect database access (in a way), it is NOT database security, as you’ll see later in this article.
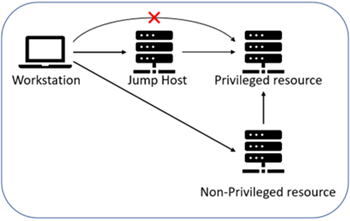
Above: Workstation can circumvent access to privileged resources when the security architecture is misconfigured. Image source: Improsec.
4. Outdated Software and Credentials Management
Running outdated software on the jump server is known to expose the jump server to vulnerabilities. Default and weak passwords should be changed, and strong authentication policies should be enforced.
5. Insider Threats and Incident Response
Disgruntled or malicious employees who have access can cause data loss and data breaches. Although all traffic can be monitored, jump servers by default lack the ability immediately respond to insiders who are mass downloading or deleting data.
How to Mitigate Jump Server Security Risks Using Best Practices
Simply put, the easiest and simplest way to mitigate jump server security risks is to implement security best practices on your jump server. However, that is easily said than done.
Here at Mamori.io, we make it extremely easy to implement jump server security best practices (including ransomware prevention and cybersecurity best practices).
Below lists the jump server security best practices and how they mitigate the security risks mentioned earlier.
1. Implement Two-Factor Authentication (2FA)
2FA adds another layer of security even when your password is compromised, or if you’re using default password.
Security Risk Mitigated: Credentials Management, Database Security
Mamori’s Approach: Mamori.io uses a zero-trust approach that assumes your password has already been compromised. Every access is secured by MFA, from accessing the network using Zero Trust Network Access (ZTNA) to accessing the database using our Database Privileged User Access (DB PAM) via SSO. Even certain operations within the database, such as mass deleting data, can be authorized to certain individuals and secured using 2FA.
2. Regular Updates and Patch
Regularly patching and updating the software and operating system on the jump server is the quickest and easiest way to close security gaps against known vulnerabilities and exploits.
Security Risk Mitigated: Outdated Software
Mamori’s Approach: Even if an external threat uses a known vulnerability to compromise your jump server, your critical resources and database can still be protected by database privileged access controls secured by 2FA.
3. Enforce Role-Based Access
Only grant access to those who need access. Enforce role-based access so users have the minimal necessary permissions (least-privileged access). This limits the number of potential attack vectors and reduces insider threats.
Security Risk Mitigated: Setup Complications, Misconfigured Architecture and Database Security, Insider Threats
Mamori’s Approach: Mamori provides Privileged Access Management (PAM) to limit jump server access to only those who need access. Once the user connects to the database or privileged resource, Mamori provides Database Privileged Access Management (DB PAM) to limit the user’s access to resource, his visibility (eg. data masking) and the types of operations (eg. read, write, delete, etc.) the user can perform onto those resources.
4. Ensure Comprehensive Logging and Monitoring
Comprehensive logging and monitoring allow for the detection of suspicious activities and help with IT audits and compliance. Logging and monitoring also facilitates forensic analysis post-incident, enhancing the overall security posture.
Security Risk Mitigated: Insider Threats, Incident Response
Mamori’s Approach: At Mamori, we believe logging and monitoring is NOT comprehensive if users are able to share accounts. That is why we use a zero-trust approach, where the user, device, location, (and more) needs to be authenticated for access and for certain database operations. Thus, when each session is monitored, logged, and recorded, we ensure that each session can easily be traced back and be used as forensics or incident response.
5. Enforce Strong Password Policies
Strong password policies, such as password complexity, regular changes, and restricting reuse, make it harder for attackers to guess or crack passwords. This strengthens the first line of defense against unauthorized access.
Security Risk Mitigated: Credentials Management and weak passwords
Mamori’s Approach: We encourage the use of strong password policies, but we emphasize on Two Factor Authentication (2FA). That’s because we use a zero-trust approach, where we assume every password is already compromised or will be compromised one day.
6. Segmenting the Network
Jump servers should only have access to select servers. One practice is to isolate the jump server from other parts of the network, which limits the potential damage of the jump server is compromised. Segmenting a network prevents attacks from moving laterally across the network to access other critical systems.
Security Risk Mitigated: Setup Complications, Misconfigured Architecture
Mamori’s Approach: Mamori uses Zero Trust Network Access (ZTNA) to microsegment a network. The microsegmented network can then be used for the jump server to ensure an isolated, secure environment.
Mamori Adds Two Additional Layers of Security to Your Jump Host
Layer 1: Securing Access to the Jump Server
Mamori ensures that only the right user with the right permission has access to the jump server using the following modules and features:
Zero Trust Network Access (ZTNA) – Before a user gets connects to the network, the user’s device and identity is verified using 2FA. Other security policies, such as access restrictions by IP address, can also be enforced.
Privileged Access Management (PAM) – Once a user connects onto the network, policies set forth in the PAM module will restrict or allow that user’s access to the jump server.
Layer 2: Securing Access from the Jump Server to Your Databases
After a person connects onto a jump server, the following Mamori modules and features ensure that the person can only view, access, and perform operations that is needed to do his job:
Database Privileged Access Management (DB PAM) – Once a user connects onto a database via a jump server, DB PAM will determine what resources the user has access to and what database operations the user can execute.
SQL Firewall – DB PAM can create rules and privileges on what SQL commands a user can run. You can choose to block all SQL commands or allow specific types of SQL commands.
Data Privacy Policies – You can easily create policies such as data masking policies, who has access to which tables, rows, or columns, and how users can work with those data.
Bonus Layer: Controlling Uploads and Downloads from Jump Server
By default, jump servers do not allow you to control uploads and downloads to and from the jump server. When someone needs to upload or download, admins might choose to share passwords, or create a new account with excess privileges that is to be a forgotten account – both of which introduce considerable security risks.
With Mamori’s PAM features, you can set permissions that allow what user(s) is able to upload, download, or do both from the jump server. Permission include having the user request access on-demand, limit access by IP address, or setting a time frame where the user account is granted access. This is another form of securing access that improves both security and workflow efficiency.
Deploy Both Layers Using a Simple Dashboard with No Coding Required
Unlike the configuring a jump server, using Mamori requires no coding. We offer a simple dashboard and user interface that even the most non-technical users can create security policies that can mitigate the security risks of your jump server.
Conclusion
By understanding the benefits and addressing the risks associated with jump servers, you can enhance the security of your network while maintaining efficient, controlled, and secure access to critical systems. If you have further questions or need assistance in securing your jump server, feel free to reach out for a detailed consultation.
Schedule a demo with Mamori.io or request your free trial. If you’re a small business with fewer than 20 users, you can use Mamori.io for free.
*** This is a Security Bloggers Network syndicated blog from Zero Trust Data Security Blog - mamori.io authored by Victor Cheung. Read the original post at: https://www.mamori.io/blog/mitigating-jump-server-security-risks
如有侵权请联系:admin#unsafe.sh