
2024-6-18 16:39:41 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Reading Time: 11 min

Experts warn that by 2025, the world could lose at least $10.5 trillion annually to cybercrime. The relentless digitization of logistics companies has spurred more advanced and expensive cybersecurity threats.
This article discusses ways to strengthen your logistics company’s digital security infrastructure. From firewalls to security audits, these strategies address a specific vulnerability. As a result, you effectively bolster your defenses against cybercrime. These strategies focus on protecting you before any incidents cause massive damage to your system, operations, and reputation.
As you create your digital data and operations masterplan, here are five proactive steps you can incorporate for good measure:
1. Develop and Enforce Strong Password Policies
To be secure online, start with strong password policies. Passwords protect you against attacks but must be complex, unique, and updated to be effective.
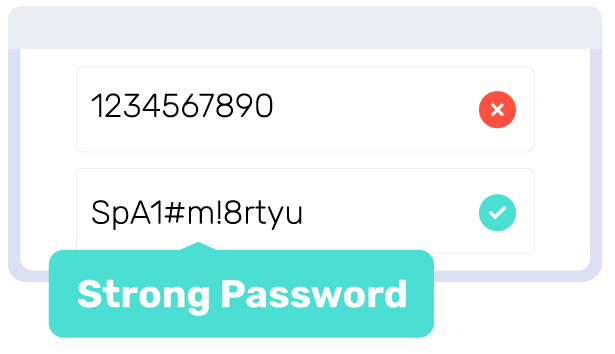
Establishing policy guidelines
The first step is establishing policy guidelines on password requirements and best practices. These rules dictate optimal password length and character diversity. They should require using alphanumeric characters, special symbols, and upper and lower case. The goal is to create complex passwords that are resilient against brute-force attacks. A study shows that 30 percent of internet users suffered data breaches due to weak passwords.
Educating employees
Employee education and awareness are crucial to your logistics company’s security. Your staff must master creating secure passwords and avoid common attacks like phishing. They should also know the risks of password reuse. Additionally, password policy reminders and updates must be part of your training initiatives.
Updating passwords regularly
Regular password updates mitigate the risk of credential theft. It means changing them periodically and using different passwords across multiple accounts. Automated reminders or password change prompts at preset intervals help enforce this practice.
Monitoring and enforcement
To detect suspicious behavior early, regularly monitor password-related activities. For instance, keep track of failed login attempts and password changes. Robust logging and auditing mechanisms help track user activity and enforce password compliance.
2. Install Robust Firewalls and Security Software
These security tools are essential for safeguarding your logistics company against cybersecurity threats. Firewalls separate your internal network from external environments and control traffic.
Security software intercepts attacks and gives you a heads-up during or after an incident. With this ability, you get more cybersecurity protection.
Firewall configuration and management
Proper configuration and regular management of firewalls are crucial. If your firewall is poorly configured, it would be as if you had no firewall. Hence, ensure that your firewall rules are aligned with your specific needs so you can still receive necessary traffic while blocking potentially harmful connections.
Regular updates and patches are necessary to address vulnerabilities that attackers could exploit. Monitoring and logging firewall activity can help you promptly detect and address suspicious behavior.
Advanced security features
Incorporating advanced security features can enhance the effectiveness of firewalls. For example, you can integrate intrusion detection and prevention systems. This will make it easier to identify and address threats as they occur.
With Deep Packet Inspection (DPI), you can even dig deeper into data packets. DPI is remarkably effective when it comes to spotting and blocking advanced attacks. You can install Virtual Private Networks (VPNs) for safer communication with remote workers.
Comprehensive security software
Your security software should offer more than essential protection for your system. It should have sophisticated features like real-time scanning, automatic updates, and behavioral analysis. These are powerful tools for identifying threats and stopping new and emerging threats in their tracks.
Endpoint protection is also crucial. Cybercriminals are known to jump at every entry point to your system. You can further protect sensitive data with solutions like encryption and multi-factor authentication (MFA).
Employee training and awareness
Nothing can protect your data enough if your workers are uninformed or reckless. This makes regular cybersecurity training a must.
3. Use an Address Verification API
An address verification API is a powerful tool for your logistics company to ensure accurate delivery and protect against cybersecurity threats. With this technology integrated into your system, you can verify addresses in real time and avoid delivery errors and data breaches. According to a study, cyber-attacks cost victims an astounding $4.45 million last year — relatively high compared to earlier figures.
Enhanced data security
An address verification API enhances data security by checking addresses prior to shipments or transactions. This helps you ensure that your customer information is accurate and legitimate, protecting you against cyberattacks or fraudulent transactions.
Circumventing fraud
When an API successfully confirms the addresses provided by your customers, it effectively prevents potential hackers from exploiting your system, such as by intercepting your deliveries, rerouting shipments, or simply gaining access to confidential data.
Streamlined operations
An address verification API can assist you in streamlining efforts for your logistics company’s operations through automated address verification. This feature increases your efficiency and makes your workers less likely to make mistakes on the job. You also become more confident that your deliveries will go to the intended recipients.
Radar: A reputable address verification API provider
Any logistics company looking for a reputable address verification API provider should consider Radar. It has a solid track record of performing accurate and reliable address checks and providing advanced and effective security features. Radar’s API is proven to perform precise, real-time address checks through its geocoding and data enrichment technologies. Through the years, it has been the go-to partner for various logistics and other businesses looking to boost their efficiency and cybersecurity.
4. Assess Your Defenses Regularly
Performing security audits from time to time is essential for your logistics company to know the strength of its defenses against attacks. These audits call for a total review of your IT infrastructure, including any policies and procedures affecting it.
Identifying vulnerabilities
Security audits help you see which areas of your system and processes can be used by cyber crooks to hatch their malicious plans. Through regular assessments, you will know your exact weak spots and address them before hackers can abuse them.
Ensuring compliance
The most apparent benefit of conducting security audits is finding weak spots in your system. However, this practice can do more than that. You can also use it as a guide as you comply with industry standards such as GDPR and PCI DSS. Moreover, it can shield you from unwanted complications, from regulatory penalties to reputational damage.
Finding loopholes through penetration testing
In penetration testing or pen testing, you attack your own infrastructure and observe how it reacts. You can then analyze this reaction to gauge your security defenses’ effectiveness. This step will expose potential entry points in your system and tell you what specific interventions are needed to address them. In the long term, this will boost your resilience if you are exposed to an actual attack.
5. Safeguard Your Supply Chain
So many things can happen after a supply chain breach. You can lose precious customer data and tarnish your reputation as a result. A breach can also throw your operations in disarray and lead to even more losses. It affects your customers and stakeholders.
Cybercrime will continue to be a sore spot for the world this year, says the World Economic Forum. Hence, keep an eagle eye on your supply chain this year, beginning with the pointers detailed below:
Risk evaluation and vendor proactivity
As the first step in safeguarding your logistics company, perform a comprehensive risk assessment of your supply chain risk. This begins with determining existing vulnerabilities and assessing your partners’ security practices. You must have due diligence processes in place to ensure you are in step with regulatory and industry standards.
Well-defined security protocols
These guidelines throughout your supply chain are essential for mitigating cybersecurity risks. They include implementing robust access controls, encryption measures, and secure communication channels to protect sensitive data during transit. Standardizing security practices across all stakeholders can reduce unauthorized access risk.
Continuous monitoring and incident response
Detecting a potential breach of your supply chain can be as straightforward as monitoring it 24/7. You’ll appreciate the tools available to help you do that in real-time. You can thwart threats as they occur and stay safe as you go.
Of course, you still need a comprehensive incident response plan to achieve this successfully. While you want to act on each threat before it becomes serious, you don’t want to sacrifice any other aspect of your supply, such as by decreasing efficiency or incurring unnecessary costs.
Training and awareness programs
On top of educating your employees regarding passwords, firewalls, and security software, teaching them about cybersecurity best practices, threat awareness, and incident response protocols will also go a long way in protecting your supply chain. This knowledge allows them to recognize risks and act promptly. They can help in minimizing potential damage and insider threats.
Collaboration and information sharing
Working with others in your industry, the government, and cybersecurity groups helps everyone share information and defend against changing cyber attacks. It prepares your logistics company for new threats and enables you to adopt a preventive approach toward security.
Strengthen Security to Protect Your Business
Protecting your logistics company from cybersecurity threats requires a comprehensive approach that covers various strategies. Implementing robust firewalls and security software, utilizing address verification API, conducting regular security audits and penetration testing, securing your supply chain, and enforcing strong password policies are all critical steps in safeguarding your business.
Taking on those measures protects your business from cyber threats, ensuring your operations are safe and trustworthy in the eyes of your customers.
Experts warn that by 2025, the world could lose at least $10.5 trillion annually to cybercrime. The relentless digitization of logistics companies has spurred more advanced and expensive cybersecurity threats.
This article discusses ways to strengthen your logistics company’s digital security infrastructure. From firewalls to security audits, these strategies address a specific vulnerability. As a result, you effectively bolster your defenses against cybercrime. These strategies focus on protecting you before any incidents cause massive damage to your system, operations, and reputation.
As you create your digital data and operations masterplan, here are five proactive steps you can incorporate for good measure:
1. Develop and Enforce Strong Password Policies
To be secure online, start with strong password policies. Passwords protect you against attacks but must be complex, unique, and updated to be effective.
Establishing policy guidelines
The first step is establishing policy guidelines on password requirements and best practices. These rules dictate optimal password length and character diversity. They should require using alphanumeric characters, special symbols, and upper and lower case. The goal is to create complex passwords that are resilient against brute-force attacks. A study shows that 30 percent of internet users suffered data breaches due to weak passwords.
Educating employees
Employee education and awareness are crucial to your logistics company’s security. Your staff must master creating secure passwords and avoid common attacks like phishing. They should also know the risks of password reuse. Additionally, password policy reminders and updates must be part of your training initiatives.
Updating passwords regularly
Regular password updates mitigate the risk of credential theft. It means changing them periodically and using different passwords across multiple accounts. Automated reminders or password change prompts at preset intervals help enforce this practice.
Monitoring and enforcement
To detect suspicious behavior early, regularly monitor password-related activities. For instance, keep track of failed login attempts and password changes. Robust logging and auditing mechanisms help track user activity and enforce password compliance.
2. Install Robust Firewalls and Security Software
These security tools are essential for safeguarding your logistics company against cybersecurity threats. Firewalls separate your internal network from external environments and control traffic.
Security software intercepts attacks and gives you a heads-up during or after an incident. With this ability, you get more cybersecurity protection.
Firewall configuration and management
Proper configuration and regular management of firewalls are crucial. If your firewall is poorly configured, it would be as if you had no firewall. Hence, ensure that your firewall rules are aligned with your specific needs so you can still receive necessary traffic while blocking potentially harmful connections.
Regular updates and patches are necessary to address vulnerabilities that attackers could exploit. Monitoring and logging firewall activity can help you promptly detect and address suspicious behavior.
Advanced security features
Incorporating advanced security features can enhance the effectiveness of firewalls. For example, you can integrate intrusion detection and prevention systems. This will make it easier to identify and address threats as they occur.
With Deep Packet Inspection (DPI), you can even dig deeper into data packets. DPI is remarkably effective when it comes to spotting and blocking advanced attacks. You can install Virtual Private Networks (VPNs) for safer communication with remote workers.
Comprehensive security software
Your security software should offer more than essential protection for your system. It should have sophisticated features like real-time scanning, automatic updates, and behavioral analysis. These are powerful tools for identifying threats and stopping new and emerging threats in their tracks.
Endpoint protection is also crucial. Cybercriminals are known to jump at every entry point to your system. You can further protect sensitive data with solutions like encryption and multi-factor authentication (MFA).
Employee training and awareness
Nothing can protect your data enough if your workers are uninformed or reckless. This makes regular cybersecurity training a must.
3. Use an Address Verification API
An address verification API is a powerful tool for your logistics company to ensure accurate delivery and protect against cybersecurity threats. With this technology integrated into your system, you can verify addresses in real time and avoid delivery errors and data breaches. According to a study, cyber-attacks cost victims an astounding $4.45 million last year — relatively high compared to earlier figures.
Enhanced data security
An address verification API enhances data security by checking addresses prior to shipments or transactions. This helps you ensure that your customer information is accurate and legitimate, protecting you against cyberattacks or fraudulent transactions.
Circumventing fraud
When an API successfully confirms the addresses provided by your customers, it effectively prevents potential hackers from exploiting your system, such as by intercepting your deliveries, rerouting shipments, or simply gaining access to confidential data.
Streamlined operations
An address verification API can assist you in streamlining efforts for your logistics company’s operations through automated address verification. This feature increases your efficiency and makes your workers less likely to make mistakes on the job. You also become more confident that your deliveries will go to the intended recipients.
Radar: A reputable address verification API provider
Any logistics company looking for a reputable address verification API provider should consider Radar. It has a solid track record of performing accurate and reliable address checks and providing advanced and effective security features. Radar’s API is proven to perform precise, real-time address checks through its geocoding and data enrichment technologies. Through the years, it has been the go-to partner for various logistics and other businesses looking to boost their efficiency and cybersecurity.
4. Assess Your Defenses Regularly
Performing security audits from time to time is essential for your logistics company to know the strength of its defenses against attacks. These audits call for a total review of your IT infrastructure, including any policies and procedures affecting it.
Identifying vulnerabilities
Security audits help you see which areas of your system and processes can be used by cyber crooks to hatch their malicious plans. Through regular assessments, you will know your exact weak spots and address them before hackers can abuse them.
Ensuring compliance
The most apparent benefit of conducting security audits is finding weak spots in your system. However, this practice can do more than that. You can also use it as a guide as you comply with industry standards such as GDPR and PCI DSS. Moreover, it can shield you from unwanted complications, from regulatory penalties to reputational damage.
Finding loopholes through penetration testing
In penetration testing or pen testing, you attack your own infrastructure and observe how it reacts. You can then analyze this reaction to gauge your security defenses’ effectiveness. This step will expose potential entry points in your system and tell you what specific interventions are needed to address them. In the long term, this will boost your resilience if you are exposed to an actual attack.
5. Safeguard Your Supply Chain
So many things can happen after a supply chain breach. You can lose precious customer data and tarnish your reputation as a result. A breach can also throw your operations in disarray and lead to even more losses. It affects your customers and stakeholders.
Cybercrime will continue to be a sore spot for the world this year, says the World Economic Forum. Hence, keep an eagle eye on your supply chain this year, beginning with the pointers detailed below:
Risk evaluation and vendor proactivity
As the first step in safeguarding your logistics company, perform a comprehensive risk assessment of your supply chain risk. This begins with determining existing vulnerabilities and assessing your partners’ security practices. You must have due diligence processes in place to ensure you are in step with regulatory and industry standards.
Well-defined security protocols
These guidelines throughout your supply chain are essential for mitigating cybersecurity risks. They include implementing robust access controls, encryption measures, and secure communication channels to protect sensitive data during transit. Standardizing security practices across all stakeholders can reduce unauthorized access risk.
Continuous monitoring and incident response
Detecting a potential breach of your supply chain can be as straightforward as monitoring it 24/7. You’ll appreciate the tools available to help you do that in real-time. You can thwart threats as they occur and stay safe as you go.
Of course, you still need a comprehensive incident response plan to achieve this successfully. While you want to act on each threat before it becomes serious, you don’t want to sacrifice any other aspect of your supply, such as by decreasing efficiency or incurring unnecessary costs.
Training and awareness programs
On top of educating your employees regarding passwords, firewalls, and security software, teaching them about cybersecurity best practices, threat awareness, and incident response protocols will also go a long way in protecting your supply chain. This knowledge allows them to recognize risks and act promptly. They can help in minimizing potential damage and insider threats.
Collaboration and information sharing
Working with others in your industry, the government, and cybersecurity groups helps everyone share information and defend against changing cyber attacks. It prepares your logistics company for new threats and enables you to adopt a preventive approach toward security.
Strengthen Security to Protect Your Business
Protecting your logistics company from cybersecurity threats requires a comprehensive approach that covers various strategies. Implementing robust firewalls and security software, utilizing address verification API, conducting regular security audits and penetration testing, securing your supply chain, and enforcing strong password policies are all critical steps in safeguarding your business.
Taking on those measures protects your business from cyber threats, ensuring your operations are safe and trustworthy in the eyes of your customers.

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Ahona Rudra. Read the original post at: https://powerdmarc.com/logistics-company-protect-fraud/
如有侵权请联系:admin#unsafe.sh

