2024-6-14 03:56:37 Author: hackernoon.com(查看原文) 阅读量:4 收藏
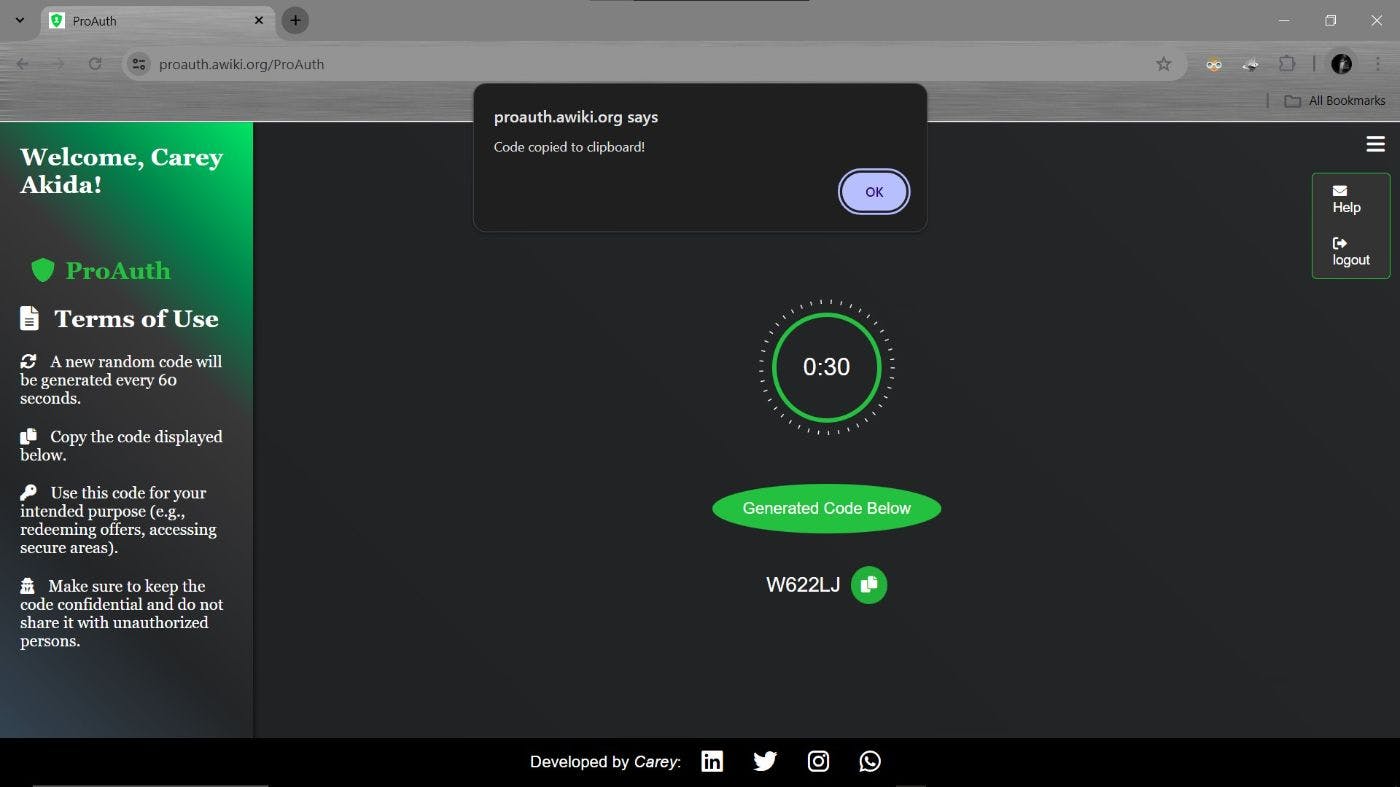
I grew interested in how the 2FA usually works for quite some time, and of course, in a data-driven society, security is key to everything, right? So I thought of maybe developing one of my own and named it ProAuth. Well, it’s not as ideal as someone would hope it to be(I mean feature-like), but for security, it’s…. what could I say SUPERLATIVE! I’m sure you’ll love it. Here’s a recap of how it works: You log in with your Google account, and you’ll be prompted to a dynamic code generator page where unique codes will be generated every 60 seconds. Amazing! I know right?
I’m afraid I didn’t have anyone to join hands with in the build-up process(I know it would’ve been great). Purely, I was targeting organizations that still don’t have their own internal 2FA verification system. If this is what your organization lacks then Viola! Welcome.

You’d be surprised how easy it is to navigate through my app. First, the user is prompted to sign in with Google, and by the way, that’s just another secure user authentication. Once allowed in, the backend is just like I mentioned: time-sensitive code is generated(and an API for validating generated codes). The code is then stored in a global variable (memory), and thereafter, the API endpoint is used for code verification to ensure it matches.
You must have noticed that I used Python (flask) for the entire backend process, with a bit of JS script spiced inside HTML and CSS for the frontend processing and code display. Well, I don’t have to mention the authentication again, right? (it’s Google). For serving this application, I chose WSGI HTTP, which we both know is well-suited and relied on by most, if not all, flask apps. Nginx was just for taking care of reverse proxy and handling incoming HTTP requests, serving static contents, and managing SSL/TLS. Oooh! I used Cerbot to obtain the SSL certificate so that all connections would appear secure and trustworthy on the internet.
I encountered a significant technical challenge that revolved around deploying the app to the server and integrating Google OAuth for user authentication. The challenge became apparent when I repeatedly faced "Resource temporarily unavailable" errors while attempting to SSH into the remote server. Furthermore, attempts to set up OAuth resulted in Google's OAuth service blocking requests, citing security concerns.
After many attempts and consultations with the mentors, it was discovered that the problem stemmed from a network misconfiguration at the server level. The server was incorrectly routed, causing intermittent connectivity issues. Once the server's network settings were corrected, SSH access was restored.
From this project, what I learned as an engineer is the importance of resilience and a methodical approach to solving problems, especially those that involve network settings that can be daunting. It has informed my engineering path to adopt an iterative development approach with continuous testing in environments that closely mimic production, which will be crucial to identifying and resolving issues at an early stage.
Generally about me, I am a dedicated engineer with a passion for creating secure, user-focused web applications. My background focuses on both front and backend development. I thrive in solving complex problems and continuously seek to enhance my technical skills through hands-on projects and collaboration. Beyond coding, I enjoy learning about new technologies and sharing knowledge with my peers, and oh! I love music; perhaps someday I’ll develop an app for this.
- GitHub repo: https://github.com/Carey99/full_proauth
- Deployed Project Page: https://proauth.awiki.org
- LinkedIn Profile: https://www.linkedin.com/in/cery-akida-a619911a8/
Feel free to explore the project and connect with me for further discussions or collaborations!
如有侵权请联系:admin#unsafe.sh