2024-5-26 15:30:31 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Protecting credentials has become increasingly critical in recent years, with everyday employees using more passwords, devices, and systems than ever before.
Remote work has significantly increased the risk of identity attacks. 55% of remote workers say they receive more phishing emails than they used to while working in the office and attempted password attacks are up tenfold.
In 2023, Microsoft detected 156,000 business email compromise (BEC) attacks every day over twelve months. As a result, tools such as Microsoft’s Azure Identity Protection have become a staple in protecting against compromised identities, account takeover, and misuse of privileges.
With a strong identity protection foundation, your organization can adopt zero trust and confidently progress toward a dynamic, identity-centric model that keeps credentials safe.
What is Azure Identity Protection?
Azure Identity Protection is a security service that provides a robust defense mechanism for user identities and access privileges within the Azure ecosystem. It analyzes data from various sources, such as user logins, device profiles, and application usage, to comprehensively assess potential identity-based risks.
Azure Identity Protection is a feature of the Azure Active Directory (AD), which employs machine learning capabilities to detect inconsistent access patterns, atypical login behavior, and potential identity threats. The Azure AD service ensures that organizations can automate the detection and remediation of identity-based vulnerabilities and provide conditional access to applications and data in line with your data security policy.
Why does your organization need Azure Identity Protection?
Real-Time Risk Detection
Azure Identity Protection evaluates real-time sign-in detections during each sign-in attempt to assign a risk level to the session. This continuous monitoring helps identify suspicious activities such as the use of anonymous IP addresses, password spray attacks, and credential exposure.
Automated Response Policies
Depending on the risk level assessed during the sign-in attempt, automated policies are enforced to safeguard both the user and your organization. These policies are essential in mitigating potential threats before they escalate and contributing to your anti-phishing toolkit.
Comprehensive Reporting Tools
Azure Identity Protection offers three critical reports for administrators: Risk Detections, Risky Sign-ins, and Risky Users. These reports are crucial for tracking and analyzing identified risks, allowing for timely intervention.
Integration with Azure Active Directory
As a feature within Azure Active Directory, Azure Identity Protection benefits from seamless integration with other Microsoft security tools. This integration enhances the overall security architecture, providing a unified identity and access management approach. Similarly, other tools like AWS Access Analyzer are designed to complement and meet the specific needs of other cloud providers, such as AWS.
Exportable Data for Further Analysis
Data concerning identity risks can be exported to various tools for additional analysis. This capability allows your organization to archive data, conduct further investigations, and correlate findings with other security events.
Access Control and Licensing Requirements
Access to Azure Identity Protection features requires users to have specific administrative roles such as Security Administrator, Security Operator, or Security Reader. Additionally, utilizing this service requires Microsoft Entra ID P2 licenses, ensuring that only authorized personnel handle sensitive security tasks.
3 Key Features of Azure Identity Protection
- Risk-based Conditional Access
Unfortunately, in cybersecurity, no one size fits all. Azure Identity Protection acknowledges this by offering risk-based conditional access, a feature that tailors security measures to the specific risk level of a sign-in attempt or user profile. This adaptive approach ensures that access to resources is granted in a manner that balances security and user convenience.
Risk-based conditional access operates on the principle of evaluating the risk associated with a user’s sign-in behavior. Azure Identity Protection considers factors such as the user’s location, the device being used, and the application being accessed. Depending on the assessed risk, conditional access policies can then enforce appropriate security measures in line with your IT security policy, ranging from requiring multi-factor authentication (MFA) to blocking access entirely.
This feature shines in its ability to provide dynamic protection. For instance, if an employee attempts to access corporate resources from a previously unknown location using an unfamiliar device, the system might flag this activity as high risk. Consequently, it could prompt additional authentication steps or restrict access, mitigating potential threats in real time.
- Identity Protection Policies
Central to Azure Identity Protection’s arsenal are its identity protection policies. These policies serve as the framework for organizations to define and enforce their security protocols. By customizing policies, your business can tailor the security mechanisms of Azure Identity Protection to meet your unique needs and requirements.
Identity protection policies encompass a wide range of settings and options. They allow administrators to specify the conditions under which users must undergo multi-factor authentication, define risk levels for different identity threats, and set up automated responses to detected risks. This level of customization ensures that organizations can enact security measures that are both effective and aligned with their operational practices.
Moreover, these policies are not static, especially if you use processes like a dynamic risk assessment. As the threat landscape evolves, so can the policies, enabling your organization to adapt its security stance in response to new challenges. This flexibility is crucial in maintaining a robust defense against cyber threats and ensuring security measures remain effective over time.
- Identity Risk Events and Alerts
Awareness and timely response are vital in mitigating identity-related threats. Azure Identity Protection excels in this aspect by providing comprehensive monitoring and alerting capabilities. Through its dashboard, administrators gain visibility into identity risk events and alerts, enabling them to assess and respond to potential security incidents quickly.
Identity risk events encompass a range of anomalies and indicators of compromise, such as atypical sign-in activities or patterns that suggest a user account may have been compromised. Azure Identity Protection detects these events and categorizes them based on severity, allowing administrators to prioritize their response efforts.
Alerts serve as the immediate notification system for these risk events, ensuring that the right personnel are informed of potential issues in a timely manner and facilitating swift action. Whether initiating an investigation, resetting a user’s password, or enforcing additional authentication measures, alerts empower your organization to react quickly and decisively to mitigate risks.
7 Steps to a Seamless Setup With Azure Identity Protection
You can follow these seven steps to ensure a seamless setup with Azure Identity Protection as part of a multi-layered security strategy. These tips provide peace of mind that user identities are being actively guarded against ever-evolving cyber threats like social engineering and credential stuffing.
- Enable Azure Identity Protection
Sign in to the Azure portal with an account that’s been assigned at least the Security Administrator role. Navigate to the “Azure Active Directory” > “Security” > “Identity Protection” and enable the service.
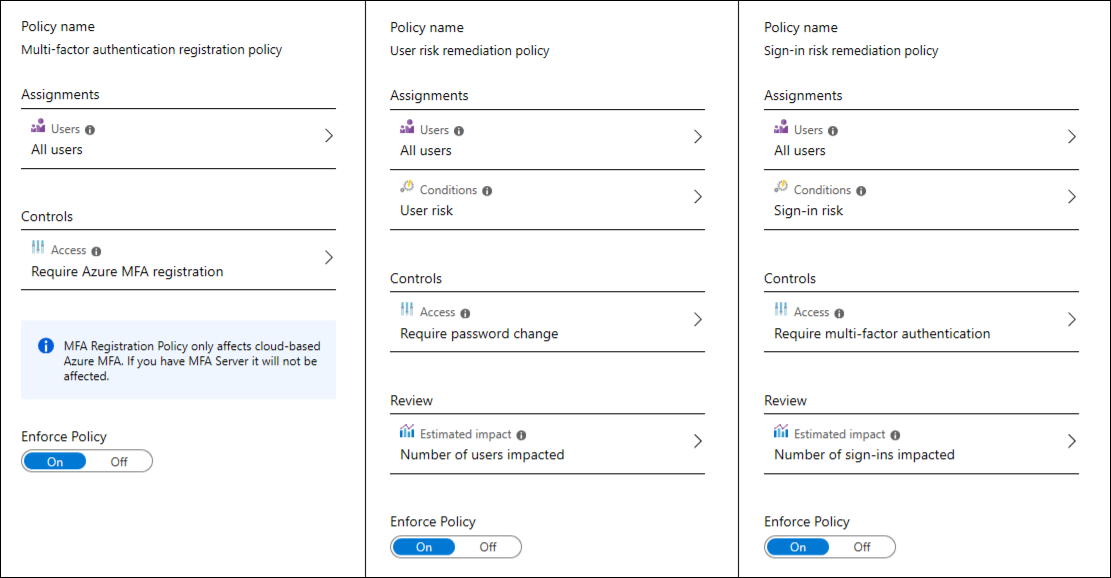
- Configure User Risk Policies
Set up policies to define what constitutes risky behavior for your organization. These policies can include sign-in risks based on user actions that suggest their credentials have been compromised. Configure appropriate responses, such as requiring a password change or multi-factor authentication (MFA), when risky behavior is detected.
- Configure Sign-in Risk Policies
Like user risk policies, sign-in risk policies monitor the sign-in process for suspicious activities. Based on the risk level detected (low, medium, and high), automatic responses can be triggered to prevent unauthorized access.
- Review Risky Users Report
Regularly review the “Risky Users” report provided by Azure Identity Protection to understand which users are considered at risk and why. This will help fine-tune your policies and ensure they align with your security requirements.
- Investigate Risk Events
Utilize the risk event investigation features to investigate suspicious activities more thoroughly. Check out corresponding logs, user profiles, and related events that could provide insights into potential security issues.
- Automate Responses
Take advantage of automated responses to address identity risks efficiently. For instance, you can automate MFA enforcement or temporarily block access while investigating a potential threat.
- Monitor and Adjust
Security is an ongoing process, and you can implement continuous security automation and monitoring to keep an eye on the effectiveness of your Azure Identity Protection setup. Based on evolving threat patterns and organizational needs, make adjustments as necessary.
You can also integrate other tools as necessary, including Microsoft-specific offerings. For example, by using Azure AD Security Groups, your organization can streamline access management, and when combined with Azure Identity Protection, you can ensure that these identities are monitored for suspicious activities. This dual approach enhances the overall security posture by protecting both the infrastructure and the identities accessing it.
Azure Identity Protection and Apono
Organizations are increasingly seeking additional layers of protection in tandem with the security services Azure Identity Protection provides. The Apono platform enables your business to create, manage, and enforce fine-grained access policies across cloud environments. Apono complements existing IAM solutions, such as Azure Identity Protection, by adding another layer of control and visibility.
With an intuitive interface, Apono simplifies the management of access permissions, ensuring that only authorized individuals have access to sensitive resources. Integrating Apono with Azure Identity Protection helps your organization achieve a more holistic approach to IAM. By using Azure Identity Protection’s advanced detection capabilities alongside Apono’s policy enforcement tools, your business can achieve a more secure and compliant posture. This integration can be especially effective in industries where regulation requires strict control over data access and user authentication.
Get started with Apono for free.
*** This is a Security Bloggers Network syndicated blog from Apono authored by Ofir Stein. Read the original post at: https://www.apono.io/blog/what-is-azure-identity-protection-and-7-steps-to-a-seamless-setup/
如有侵权请联系:admin#unsafe.sh