
read file error: read notes: is a directory 2024-5-17 21:0:41 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
The Good | International Law Enforcement Charge Crypto Criminals & Take Down a New Iteration of BreachForums
In the past week, law enforcement agencies took down cryptocurrency thieves responsible for a multi-million dollar theft from the Ethereum blockchain, and seized a second iteration of the notorious hacking platform, BreachForums.
The DoJ has unsealed an indictment charging Anton Peraire-Bueno (24) and James Pepaire-Bueno (28) with conspiracy to commit wire fraud and conspiracy to commit wire fraud and money laundering. The brothers allegedly manipulated the blockchain in 12-seconds to pilfer $25 million worth of cryptocurrency in a first-of-its-kind attack.
This was done by tampering with the transaction validation processes on the blockchain, altering pending transactions, and rejecting requests by victims to return the stolen funds. Prior to the attack on the blockchain, the brothers focused on performing reconnaissance on their victims, learning their identities and trading behaviors. If found guilty, each of the brothers face a maximum sentence of 20 years in prison for each count.
A little over a year has passed since the arrest of Conor Brian Fitzpatrick “Pompompurin”, owner and administrator of BreachForums. This week, the FBI have seized the hacking forum for a second time. Working with international law enforcement partners, the FBI have shut down a Telegram channel belonging to Fitzpatrick’s successor, “Baphomet”, along with the second iteration of the BreachForums website. Authorities are currently investigating the site’s backend data and have issued a call for new information.

This iteration of BreachForum, run from June 2023 to May 2024, operated as a clearnet marketplace where cybercriminals could buy, sell, and trade illicit contraband such as hacking tools, compromised databases, stolen access devices, and various illegal services. As forums and dark markets continue to rise and fall multiple times, organizations are reminded to keep their defenses up to safeguard their sensitive data.
The Bad | North Korean APT Kimsuky Abuses Facebook Messenger in Latest Social Engineering Campaigns
Threat actors have found a new way to abuse social media to carry out their cyberattacks. In their latest string of attacks, a DPRK-linked APT known as Kimsuky used fake Facebook accounts to deliver malware via Messenger. Security researchers noted that the campaign leveraged the identity of a real individual in order to specifically target activists within North Korean human rights groups and anti-North Korean sectors.
Unlike traditional spear phishing attacks, this campaign employs Facebook Messenger to lure victims into opening private documents shared by the fake persona. The documents are hosted on OneDrive and pretend to be related to a trilateral summit involving Japan, South Korea, and the U.S. Their use of MSC files, an uncommon file type to carry out the attack, points to Kimsuky’s attempts to avoid detection.
Once opened by the victim, the MSC file triggers a connection to a server controlled by the attackers, displaying a decoy document while executing background commands for persistence and data collection. All of the gathered data is finally exfiltrated to the command and control (C2) server to further harvest IP addresses, User-Agent strings, and HTTP request timestamps, before delivering the payloads.
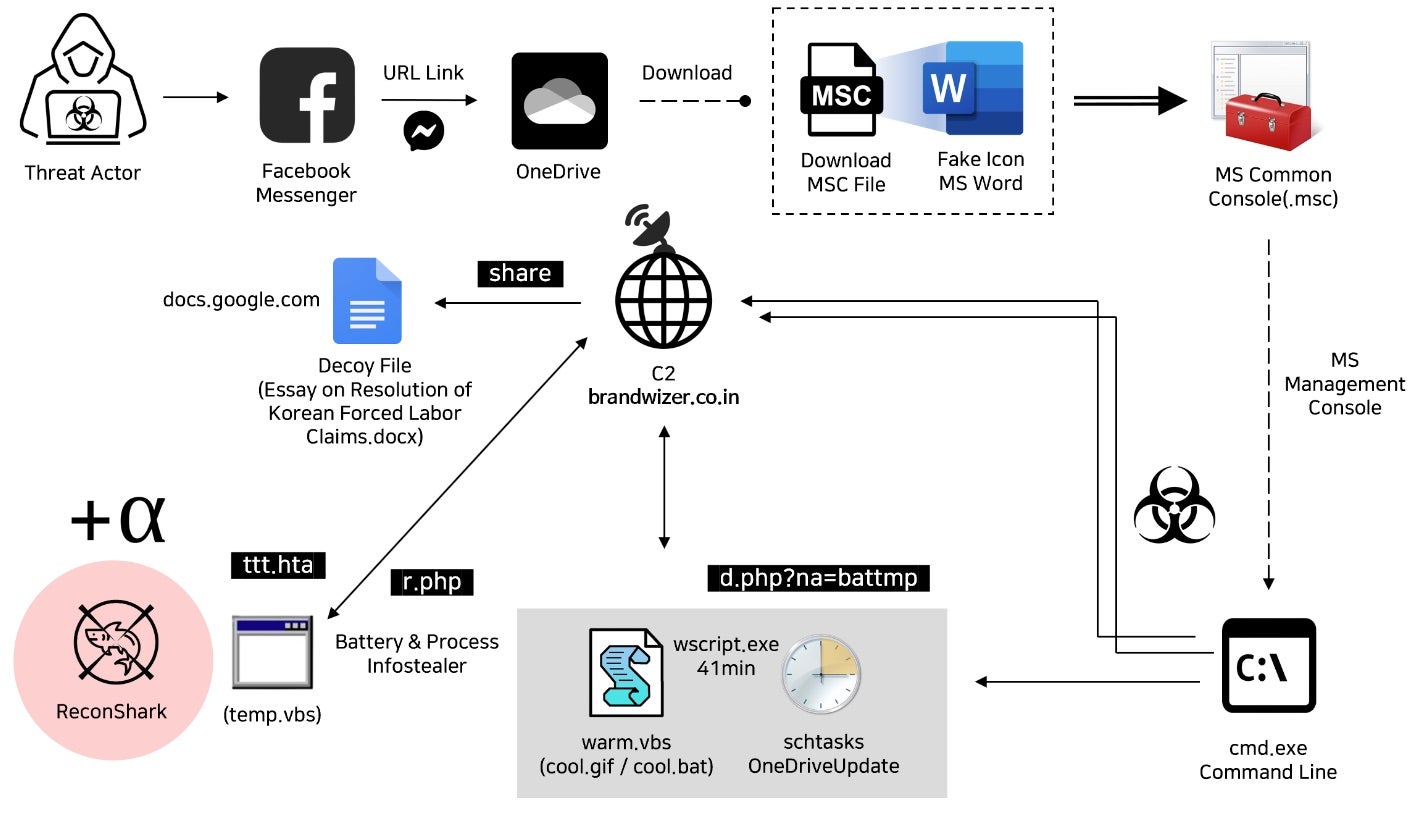
Kimsuky’s latest exploits call back to activity from last spring, such as ReconShark, which also targeted specific individuals through spear phishing emails, a file reconnaissance and data exfiltration campaign using RandomQuery malware, and a social engineering campaign stealing Google ad subscription credentials of a reputable news service focusing on North Korea. The DPRK-linked APTs continued commitment to developing their social engineering attacks highlights the need for organizations to remain vigilant, collaborate with their security partners, and invest in solutions including advanced detection capabilities.
The Ugly | New Lunar Toolset Deployed by GRU-Linked Actors Targets European Government Agencies
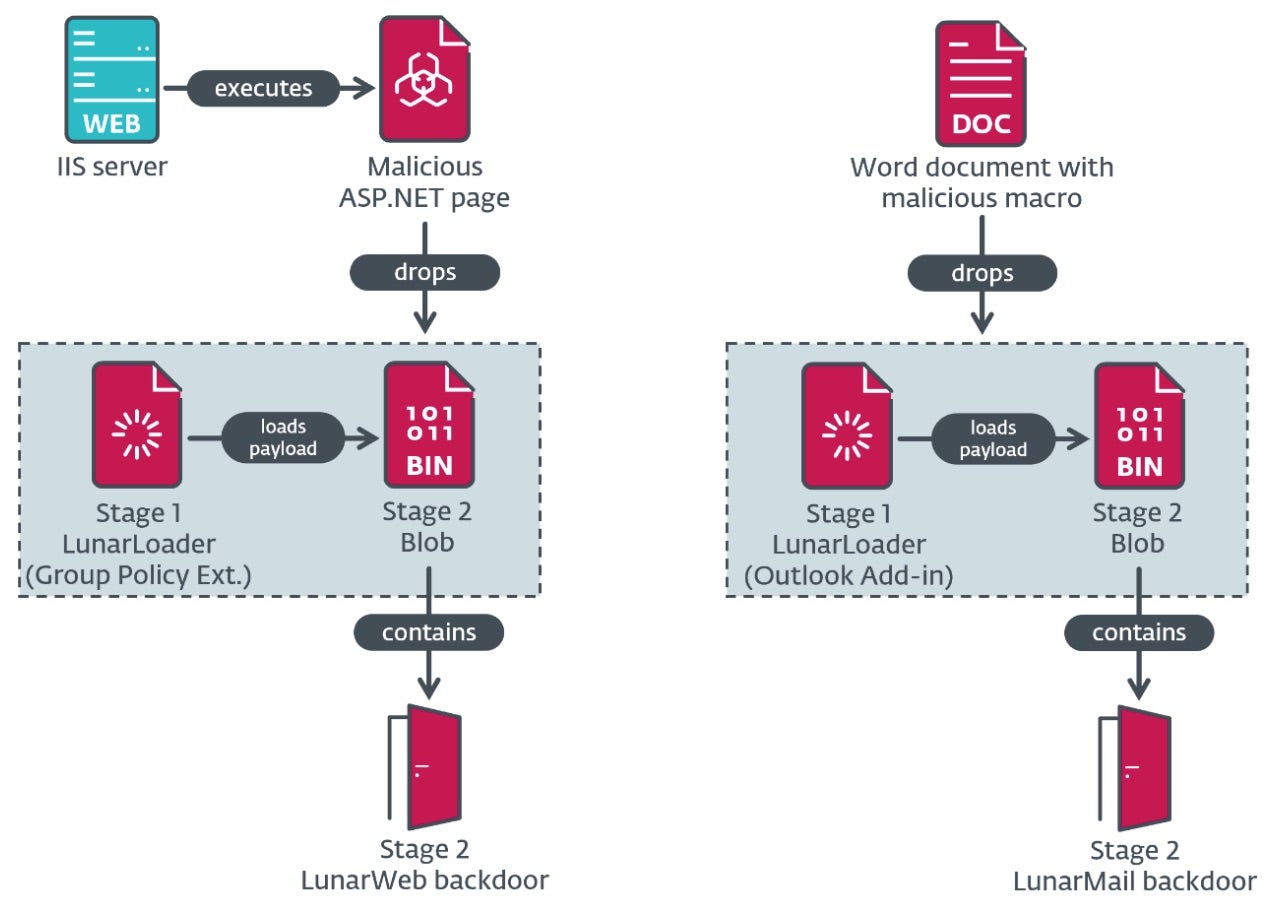
Reports have surfaced this week detailing cyber intrusions of various European foreign affairs ministries. The campaign leverages two previously unknown backdoors, both of which have been active since at least 2020.
Researchers have dubbed the backdoors “LunarWeb” and “LunarMail”, and attribute the campaign with medium confidence to Turla, an APT connected to the Russian Federal Security Service (FSB). Turla (aka Krypton, UNC4210, or Secret Blizzard) has been known to target high profile entities including governments and diplomatic organizations in Europe, Central Asia, and the Middle East.
Initial infection occurs through spear phishing emails carrying Microsoft Word files with malicious macro code to install the LunarMail backdoor. This VBA macro then ensures persistence on the infected system by creating an Outlook add-in that is activated when the email is launched. Researchers also noted the potential abuse of Zabbix, an open-source solution for network and application monitoring, to deploy the LunarWeb payload.
Once active, Lunar backdoors enable direct communication with the C2 server, allowing for lateral movement within the network using stolen credentials and compromised domain controllers. These backdoors are tailored for long-term surveillance, data theft, and maintaining control over compromised systems, particularly in high-value sectors. A complete list of IoCs can be found here.
Recent findings state that Russian-sponsored threats currently pose the greatest amount of risk to election infrastructure. Their goals also include amplifying GRU-linked interests and retaliating against perceived adversaries. In February, SentinelLabs uncovered a Russia-aligned influence operation network dubbed Doppelgänger employing disinformation tactics to influence public opinions within Germany. As major elections are around the corner for both the U.S. and EU members, malicious activities from nation-backed actors are expected to climb, making socio-economic and geopolitical terrains even more complex to navigate.
如有侵权请联系:admin#unsafe.sh