minute read

Incident response analyst report 2023
As an information security company, our services include incident response and investigation, and malware analysis. Our customer base spans Russia, Europe, Asia, South and North America, Africa and the Middle East. Our annual Incident Response Report presents anonymized statistics on the cyberattacks we investigated in 2023. All data is derived from working with organizations that requested our expertise in carrying out incident response (IR) or assisting their in-house expert team.
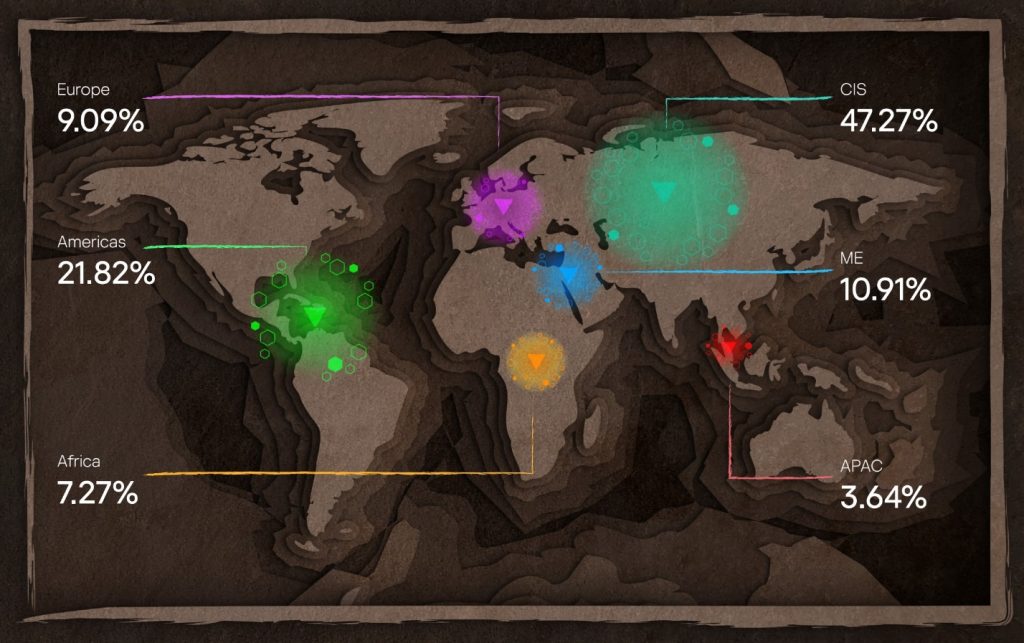
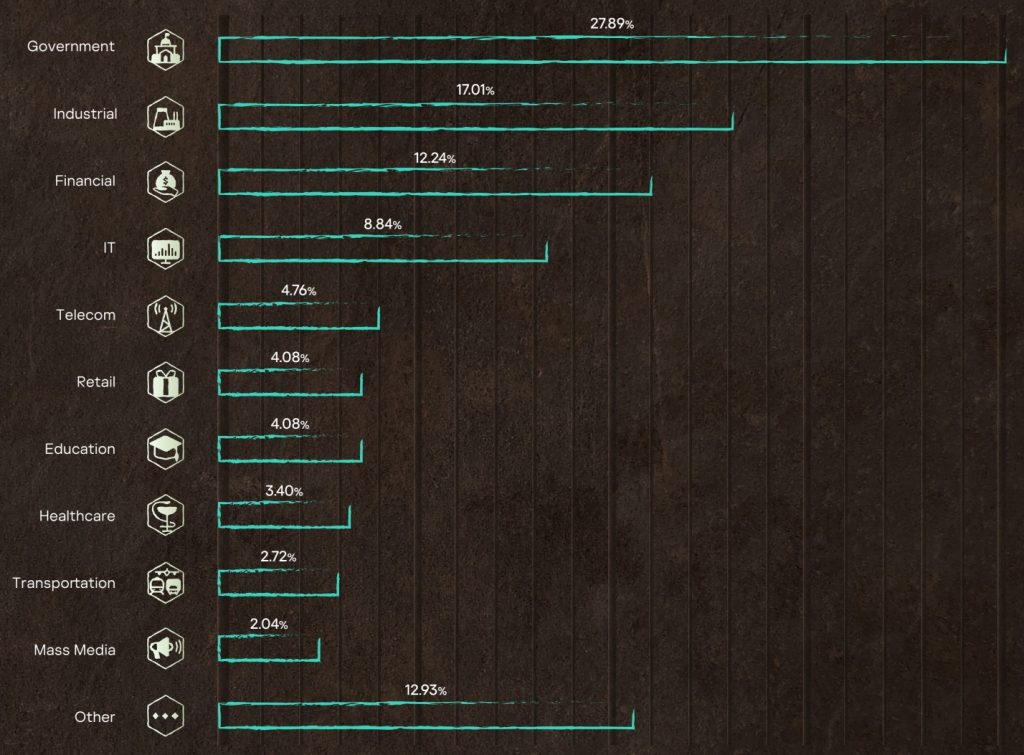
Distribution of incidents by region and industry
The geography of the service has changed somewhat of late, with the share of requests in Russia and the CIS (47.27%) continuing to rise. At the same time, 2023 is notable for the significant increase in the number of IR requests in the second-place Americas region (21.82%).
Looking at the distribution of incidents by industry, we see that in 2023 the majority of requests came from government agencies (27.89%) and industrial enterprises (17.01%).
2023 trends: ransomware and supply chain attacks
In 2023, ransomware remained the most prevalent threat, despite a drop in share to 33.3%, down from 39.8% in 2022. Ransomware targeted organizations indiscriminately, regardless of industry. The most common families we came across in our investigations were LockBit (27.78%), BlackCat (12.96%), Phobos (9.26%) and Zeppelin (9.26%).
Another important trend we observed in 2023 was the significant rise in the number of attacks through trusted relationships with contractors and service providers. This attack vector was among the three most frequently seen in 2023. This is not surprising, for it allows threat actors to carry out large-scale attacks with a great deal more efficiency than if they targeted each victim individually. For many organizations such attacks can be devastating, and detecting them takes a lot longer because the attackers’ actions can be hard to distinguish from those of employees working for a contractor.
Report contents
The full report covers:
- IR statistics: what events prompted organizations to request IR services, at what stages attacks were detected, how long it took on average to respond to them;
- Common tactics, techniques and procedures employed by threat actors at different stages of attack development;
- Legitimate tools used in attacks, with examples of their use in real-world incidents;
- Vulnerabilities most often exploited by threat actors.
Recommendations for preventing cyberincidents
To reduce the risk of a successful cyberattack on your organization, or minimize the damage if attackers do penetrate your infrastructure, we recommend:
- Enforcing a strict password policy and protecting key resources with multi-factor authentication;
- Closing remote management ports to outside access;
- Promptly updating software and deploying additional security measures for services at the network perimeter;
- Cybersecurity awareness training and related activities for employees;
- Restricting the use of legitimate tools that may be utilized for attacks on the corporate network, and creating rules for detecting such tools;
- Conducting regular cyber drills focused on common attacker techniques;
- Backing up data on a regular basis;
- Protecting endpoints with EDR solutions;
- Subscribing to an IR service guaranteed under an SLA.
Read the full 2023 Incident Response Report (PDF).