2024-5-7 11:13:45 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
Cyber threats are relentless, and the methods used by cybercriminals are constantly evolving. To strengthen your security posture, it’s crucial to have timely and actionable threat intelligence. However, while technology is vital to your defense, the human element remains a significant potential vulnerability.
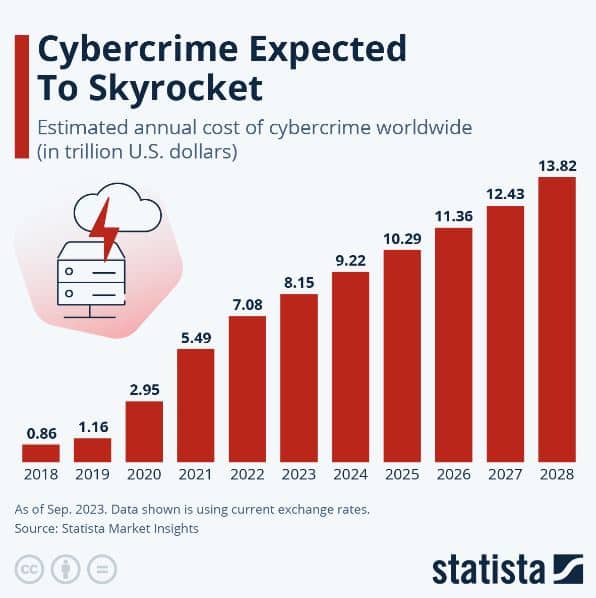
Consider how these two disparate items intertwine. In the recent Microsoft breach, a threat actor compromised a legacy non-production account with a password-spraying attack. The breach would have been preventable if Microsoft had intel on this threat actor’s typical actions or about the previous leakage of an employee’s password. With the global cost of cybercrime expected to rise by over $1 trillion in 2024, having the right intelligence to protect your business against expensive breaches is urgent.
Cybersecurity awareness training is often overlooked but can significantly augment your organization’s threat intelligence. Integrating cutting-edge, AI-powered training from CybeReady’s innovative platform can transform your employees into a crucial part of your threat intelligence strategy.
Let’s explore the fascinating and valuable link between threat intelligence and security awareness training and how you can leverage CybeReady to elevate your organization’s cybersecurity.
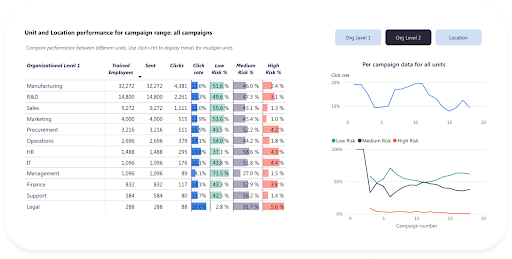
Understanding Threat Intelligence
Threat intelligence is actionable information about potential or current cyber attacks that threaten your company. You can gather this data from diverse sources, such as past attack data, real-time incident reports, dedicated intelligence feeds shared among collaborators and predictive analyses of emerging threats.
Gathering good threat intelligence lets you shift your security posture from reactive to proactive. Understanding adversaries’ tactics, techniques, and procedures (TTPs) allows you to anticipate potential attacks and strengthen defenses accordingly.
If an attack does occur, having detailed threat intelligence allows your incident response team to quickly understand the nature of the attack, identify the attackers, and implement specific defenses to mitigate damage.
Good threat intelligence must be timely. If it’s disseminated, collected, or analyzed too late, the threat might have already infiltrated and harmed your company. Another key characteristic is actionable information—threat intel must be specific enough to drive immediate security actions.
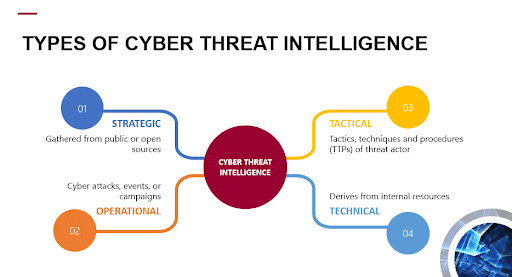
The Challenges of Threat Intelligence
Organizations of all sizes face challenges in effectively gathering, analyzing, and applying threat intelligence that’s timely and actionable. These challenges include:
- Data overload problems from sifting through an overwhelming volume of threat data and trying to figure out what’s relevant and quality enough to count as useful threat intel
- A shortage of skilled personnel who can accurately analyze and interpret threat data
- Keeping up with evolving cyber threats and understanding the implications of new threats
- Integrating threat intelligence into existing security systems and workflows, ensuring the threat data you collect can be effectively used by your security tools and that they can respond dynamically
Recognizing the challenges of threat intelligence highlights a crucial opportunity: enhancing cybersecurity through targeted training. As organizations tackle these obstacles, integrating threat intelligence into cybersecurity awareness training emerges as an effective strategic response.
Two Sides of the Same Coin: Cybersecurity Awareness Training and Threat Intelligence
Threat intelligence and cybersecurity awareness training work together to strengthen your security posture, with threat intel informing training and training empowering informed decisions that protect your organization.
How Threat Intelligence Informs Training
Threat intelligence provides detailed insights into cybercriminals’ latest methods. The insights can be used to tailor and target cyber awareness training programs.
For example, if threat intelligence identifies a spike in specific phishing attacks targeting similar industries, you can customize training to focus on those attacks. This ensures the training is relevant and timely in addressing the most pressing threats your employees will likely encounter.
One of the most effective ways to teach is through real-world examples. Threat intelligence offers a reservoir of recent and relevant scenarios that can help design better training modules. These examples help to contextualize risks for employees and show them the tangible consequences of security breaches.
How Training Empowers Informed Decisions
Ultimately, obtaining and acting on reliable threat intelligence is about empowering smart decision-making. Cybersecurity awareness training serves as a unique form of threat intelligence tailored for your employees. It provides the knowledge to make informed decisions that protect themselves and your business.
Ongoing training promotes a security-conscious culture where employees understand cybersecurity practices and their role in safeguarding assets. This shift empowers them to become proactive participants in security by reporting unusual activity and potential red flags, which, in turn, bolsters overall threat intelligence.
The crucial question for CISOs and IT managers is: how can we access effective training that transforms our employees into a robust human firewall?
CybeReady’s Solution: A Training Style that Stands Apart
CybeReady is a leading cybersecurity training and awareness platform that empowers organizations with actionable threat intelligence through up-to-date phishing simulations and easy-to-retain microlearning modules called ‘security awareness bites.’
Our autonomous solution uses a unique approach to cybersecurity training that is:
Data-driven
We ensure that your business receives the right set of phishing simulations based on real-world data to ensure relevant training. We also focus heavily on providing detailed analytics to improve training and overall security.
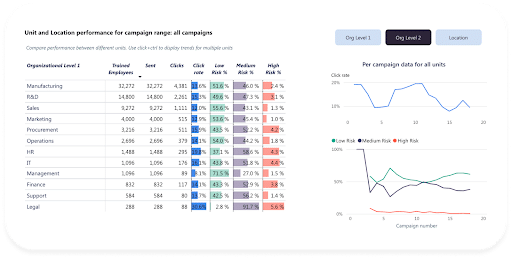
AI-powered
A machine learning model uses available data to refine training programs, with features like optimized learning experiences, varied training intervals, and varied stimuli to keep people engaged.
Customizable
Risk-based programs help you tailor the training approach depending on how employees perform in phishing simulation tests. Some might need more intense training, while others require a more hands-off approach.
But CybeReady’s impact on your business extends beyond reducing the risk of security incidents that stem from employee mistakes.
CybeReady’s Impact on Threat Intelligence
CybeReady’s solution features three critical differentiators that help bolster your threat intelligence:
1. Just-in-time Phishing Training
Just-in-time phishing training is a powerful strategy that turns a potential security misstep into a teachable moment. By providing training immediately after an employee clicks on a simulated malicious link, this approach not only educates but also empowers your employees. It captures the moment of error and transforms it into a learning opportunity, enhancing your overall threat intelligence capabilities.
Initiating training immediately after an employee clicks on a simulated phishing link ensures the lessons are contextually relevant and impactful. This method reinforces the correct behaviors and protocols when employees are most attentive, helping solidify learning and foster behavioral change.
Furthermore, just-in-time training extends beyond individual experiences to benefit the entire organization. Each session serves as a real-time demonstration of current threats, educating the involved employees and providing case studies for broader discussion. These discussions enhance organizational learning and awareness by effectively using collective experiences to crowdsource threat intelligence.

Additionally, each interaction with a simulated phishing attempt yields valuable data that reveals specific vulnerabilities within your organization’s human firewall. Cybersecurity teams can identify patterns and common vulnerabilities by analyzing these incidents, allowing for more tailored and effective security strategies and threat intelligence efforts.
This comprehensive approach addresses immediate learning needs and fortifies your overall cybersecurity posture.
2. PhishCage Reporting Button
The PhishCage Reporting button, available as an add-on for Google Workspace and Office 365, significantly enhances your threat intelligence capabilities. This tool not only empowers employees to actively engage in identifying potential phishing threats but also serves as a vital point for data collection and analysis.
When employees use the PhishCage button to report suspicious emails, it immediately collects data, providing real-time insights into potential threats as they are identified. This prompt reporting facilitates a quicker response to mitigate risks and enriches your threat intelligence with current, relevant examples of phishing attempts.
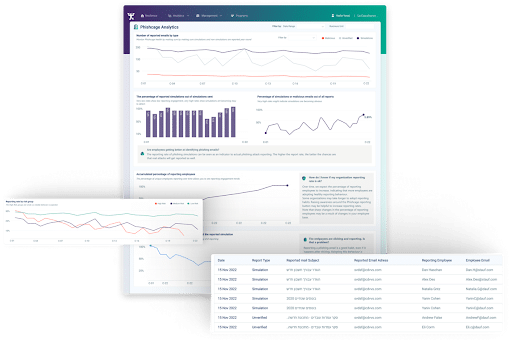
Moreover, the analytics from the PhishCage button reveal patterns and trends in phishing attacks, such as frequently used subject lines, the types of attachments that commonly deceive users, and the times when attacks are most prevalent. Access to the actual content of reported emails allows for a deeper understanding of these trends.
This detailed knowledge enables your security team to refine defensive strategies and develop targeted educational initiatives that better prepare employees to recognize and report phishing attempts.
3. User Engagement and Retention
CybeReady’s training methodology emphasizes a hands-on approach that includes continuous learning, concise and positive content, a varied learning environment, and immediate feedback. This strategy does more than educate; it actively engages users and enhances knowledge retention.
Our commitment to continuous training reflects the principles of repetition found in athletic training regimes. By regularly exposing employees to cybersecurity concepts and practices, CybeReady aids in forming and reinforcing neural connections that are crucial for threat detection and response.
This consistent exposure ensures that employees are not only familiar with cybersecurity tactics but are also quick to recognize and respond to potential threats efficiently.
Threat Intelligence in Practice: The Avid Technology Success Story
The question you may be asking now is, how does this work in practice?
Avid Technology has significantly enhanced its cybersecurity defenses through CybeReady’s innovative training solutions. Since integrating CybeReady, Avid has successfully boosted its threat intelligence and reduced phishing susceptibility. Here’s what their VP and CSO/CISO reported:
Effective, Realistic Training
CybeReady’s simulations are regularly updated to reflect the latest real-world scenarios, keeping training relevant and engaging. The micro-training sessions are concise and designed to deliver crucial security knowledge without overwhelming employees. The training is educational and practical, enabling employees to apply what they have learned immediately.
Dramatic Results
Avid Technology has experienced a dramatic decrease in phishing incidents, with no events reported in the last two and a half years. Additionally, the frequency of employees clicking on phishing links has dropped from the industry average of about 15-16% to below 7%, and the number of high-risk users has been reduced by 300%.
“CybeReady has been very effective in increasing the number of people who think about information security and…the amount of time they think about it. We haven’t had a single phishing-based incident in the past two and a half years.” – Dmitriy Sokolovskiy, VP and CSO/CISO at Avid Technology
Immediate Return on Investment
Implementing CybeReady has given Avid Technology quick and substantial returns. The platform’s efficiency and automation have minimized the need for extensive oversight, allowing the company to focus more on strategic initiatives rather than training management.
Behavioral Improvement
The training has significantly altered employee behavior toward cybersecurity, making them more aware and proactive in identifying threats. This change has improved the company’s overall cyber resilience and enhanced the security culture within the organization.
CybeReady’s solution has enabled Avid Technology to fortify its defenses against cyber threats, proving that proper training and awareness work hand-in-hand with threat intelligence to elevate cybersecurity.

Experience the CybeReady Difference
CybeReady revolutionizes cybersecurity training with its focus on real-world simulations and adaptive learning. This approach ensures that employees are not merely passive participants but are actively engaged and continually evolving in their cybersecurity knowledge. Integrating this training into their daily routine makes all team members integral to your organization’s threat intelligence efforts.
CybeReady’s training continuously adapts to the ever-changing cybersecurity landscape, ensuring that your staff remains well-prepared to effectively face current and emerging threats. Driven by data science, CybeReady changes employee behavior by decreasing your employee high-risk group by 82% and increasing your employee resilience score by 5x within months of training.
Discover how CybeReady can transform your approach to threat intelligence. Schedule a demo today.
The post Elevating Cybersecurity: How CybeReady Transforms Threat Intelligence for Businesses appeared first on CybeReady.
*** This is a Security Bloggers Network syndicated blog from Cyber Security Awareness Training Blog | CybeReady authored by Nitzan Gursky. Read the original post at: https://cybeready.com/security-culture/elevating-cybersecurity-how-cybeready-transforms-threat-intelligence-for-businesses
如有侵权请联系:admin#unsafe.sh

