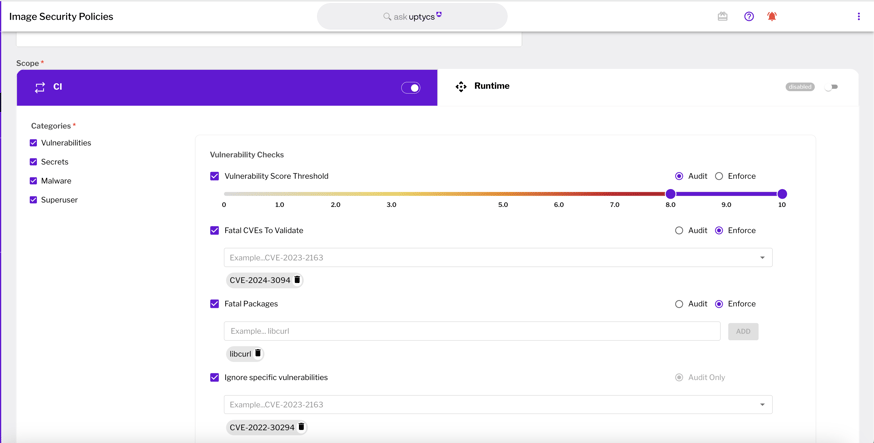
In today's rapidly evolving digital landscape, cloud security emerges as a pivotal concern for organizations worldwide. The complexity of modern cloud-native environments, spanning both cloud and on-premises infrastructures, presents unique challenges. Organizations struggle to effectively prioritize and mitigate security risks, often hindered by multiple layers and silos that increase response times and delay the protection of essential assets. Bad actors exploit vulnerabilities and misconfigurations, but they also engage in phishing attacks and credential theft. No level of hygiene alone is sufficient to protect against these threats. While many market products can indicate what happened after an attack, it's crucial to implement processes, procedures, and technology that prevent future incidents—before it's too late. To combat the risk prioritization challenges and siloed security layers of hybrid-cloud environments, a mitigation-based approach is essential, focusing on: In order to combat alert fatigue and noise from multiple attack surfaces and security signals, Uptycs integrates several innovative features to streamline cloud risk prioritization: Figure 1 - Unified Risk Listing First Uptycs prioritizes risk across different risk factors including static risk and real-time security data such as vulnerabilities and detections across multiple cloud resources and presents findings in one unified view allowing security teams to prioritize their risks. Figure 2 - Unified Risk Prioritization Next, Uptycs allows you to drill into detailed evidence presenting potential attack paths, lateral movements, real-time threat detections, and key security findings all in one single evidence graph along with information on how the risk was scored. Uptycs doesn't just prioritize; it provides a single platform that can integrate with your existing tools and workflows for you to take action through protection, remediation, and prevention. Figure 3 - Real-Time Workload Protection Uptycs gives you real-time workload protection capabilities enabling you to take action to stop malicious activity as well as automatically stopping key threats such as cryptominers, reverse shells, and data exfiltration attacks. Figure 4 - Image Security Policies Implement Shift-Left preventative measures to enable security controls before it affects your cloud runtime using image security policies across CI and Runtime deployments. As cloud environments become increasingly integral to organizational IT infrastructures, the role of sophisticated tools like Uptycs in enabling effective risk prioritization becomes crucial. By focusing on the most critical threats and integrating preventive and reactive security measures, organizations can not only protect their digital assets but also ensure operational resilience against evolving cyber threats.Solving your Hybrid Cloud Risk Through Runtime and Shift Left Visibility, Protection, and Remediation
The expanding cloud attack surface and the Shared Responsibility Model
Can you sleep well at night with just a well-maintained hygienic cloud environment?
In order to prevent future incidents, a more proactive approach is needed. First, it’s important to start with a unified risk prioritization approach that analyzes security signals, not just agentless posture management and static risk, but through runtime insights and shift-left visibility in order to eliminate blind spots. However, with the increase in attack complexity, you need to be able to play defense as well and protect against malicious attacks through automatic workload protection and shift-left prevention in your software pipelines to reduce risk before it reaches your cloud environment.At Uptycs, our customers tell us that our unified risk management platform, be it on- prem or in the cloud, combined with cloud workload protection, real-time remediation, and shift-left prevention allows them to reduce alert fatigue, operate with more efficiency, and protect their business with greater resiliency. Let’s dive deep into risk prioritization and how Uptycs enables you to take your risk management strategy to the next level.
What you need: A mitigation-based risk prioritization approach with Uptycs
How Uptycs works: Deep dive into operational excellence

-2.png?width=874&height=568&name=image%20(7)-2.png)


Conclusion
Risk Prioritization is Not Enough, Mitigation Must Be Part of Your Strategy
2024-5-6 21:0:0 Author: www.uptycs.com(查看原文) 阅读量:5 收藏
2024-5-6 21:0:0 Author: www.uptycs.com(查看原文) 阅读量:5 收藏
文章来源: https://www.uptycs.com/blog/risk-prioritization-is-not-enough-mitigation-must-be-part-of-your-strategy
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh