2024-4-25 18:10:24 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
TL;DR
- Kovrr is proud to announce the release of its new Drill Down features, allowing chief information security officers (CISOs) and cybersecurity leaders to access deeper insights regarding cyber events and risk drivers.
- The new Drill Down feature offers highly targeted mitigation recommendations based on these event types and initial attack vectors, equipping CISOs to create cybersecurity programs that reduce the risk of specific risk elements.
- The feature also offers key metrics, such as Average Annual Loss and 1:100 Annual Loss. Users can also review event statistics, such as media financial damage, outage time, and data record losses.
- The Drill Down capability likewise provides additional event benchmarks. The platform offers comparison metrics for industry and revenue sizes, allowing organizations to gauge their relative risk.
- In addition to optimizing risk mitigation strategies and budget allocations, the Drill Down feature also facilitates more effective communication, offering CISOs more data to justify cybersecurity spending to non-technical stakeholders.
Kovrr Releases Drilled Down Cyber Risk Quantification Metrics
The power of an on-demand cyber risk quantification (CRQ) platform lies in its ability to harness an extensive amount of data, filter it, and consequently produce an objective assessment that offers key stakeholders an understanding of how likely their organization is to experience certain cyber events, along with the respective financial losses.
Key metrics, such as the Average Annual Loss (AAL) of specific incidents and initial attack vectors, provide a wealth of insights that can be leveraged to optimize resources and drive targeted mitigation plans. However, Kovrr’s new Drill Down feature equips chief information security officers (CISOs) to dive even further into these risk drivers, revealing more than ever about their organization’s unique risk landscape.
Armed with these more granular data points, cybersecurity leaders not only can significantly bolster their cybersecurity program with sharper, more cost-effective initiatives but also enhance high-level communication, offering non-technical executives a clearer explanation of why they are allocating the budget to specific campaigns versus others.
Drill Down Feature Adds Multiple Cyber Data Components

The new Drill Down feature introduces:
- Highly targeted mitigation recommendations, illuminating which security upgrades will reduce an organization’s financial exposure due to a specific event type or initial attack vector.
- Key metrics, such as Average Annual Loss and 1:100 Annual Loss, which are also broken down according to event and vector.
- Event statistics, such as expected financial damages, outage times, and data record losses per unique cyber event or initial vector.
- Greater insights regarding the attack vectors most likely to cause certain events and the resulting financial damages.
- information about which events specific initial attack vector exploitation is most likely to lead to and how much it will cost the company.
- Additional event benchmarks, allowing for a deeper comparison of the cyber risk landscape with other industries and revenue bands based on events or vectors.
In Figure 1, for example, the Drill Down feature showcases the new information and metrics specifically related to eMerchify’s ransomware risk landscape. Each of these novel elements empowers CISOs to devise high-end risk migration strategies and subsequently justify these decisions to key stakeholders.
Highly Targeted Mitigation Recommendations per Event or Vector

One of the most valuable aspects of the new Drill Down feature is a user’s ability to quickly gain an understanding of the mitigation efforts that will have the most significant effect in reducing their organization’s financial exposure to the specific event or initial attack vector. In the case of Figure 3, the top recommended actions highlight the security upgrades that will have the greatest impact on minimizing the cost of a ransomware event.
Moreover, the Top Recommended Actions section is customized according to the business’s chosen cybersecurity framework, such as CIS, NIST, and ISO, and current maturity levels. In Figure 3, the initiative that would lead to the largest decrease in financial exposure due to a ransomware event, on average, is upgrading NIST Control PR.AC focused on identity management, authentication, and access control from Level 4 (Managed) to Level 5 (Optimized).
Average Annual Loss, 1:100 Annual Loss

With the new feature, organizations are also provided a description of the event type or attack vector, along with the Average Annual Loss (AAL) and the 1:100 Annual Loss, both within the chosen parameters. In Figure 3, for example, the enterprise’s AAL for ransomware events amounts to $9.45 million, and it has a 1% chance of losing more than $198.96 million due to this type of incident. Such figures bolster financial investment optimization and decision-making.
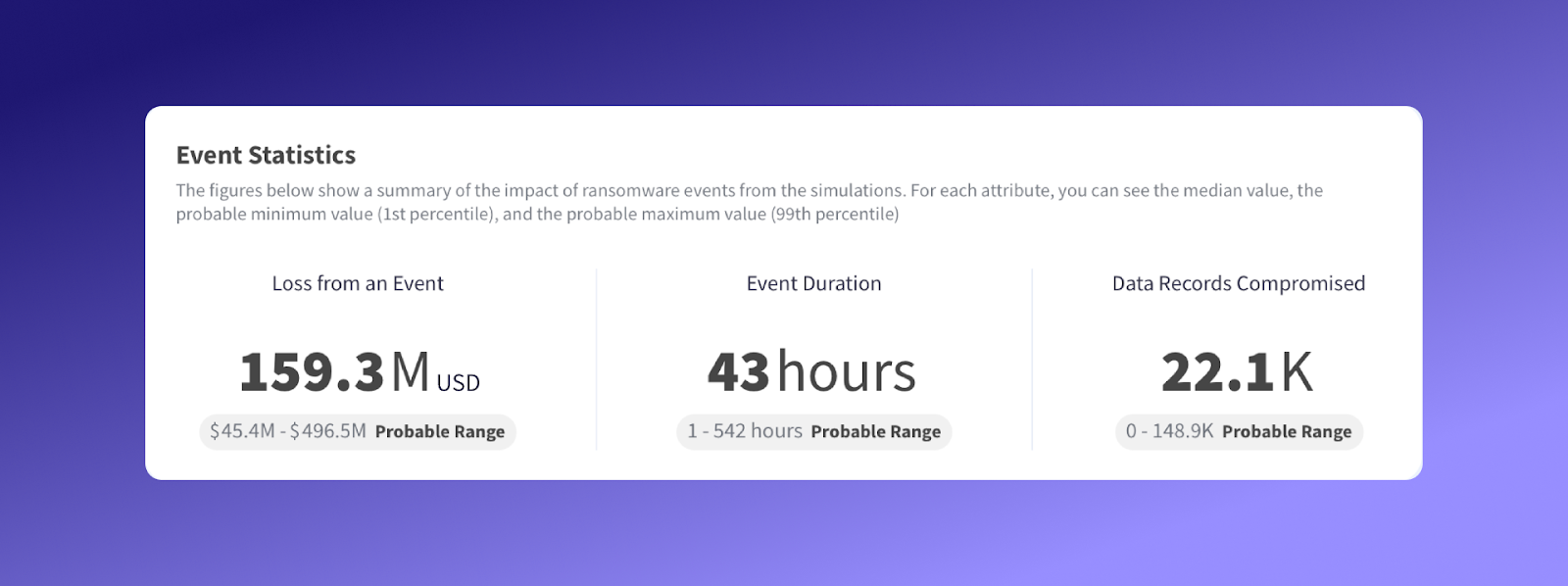
Event Statistics

Kovrr’s Drill Down feature highlights other core information regarding, in the case of Figure 4, a ransomware attack. The Event Statistics are also available when leveraging the new feature to explore other event types, as well as specific initial attack vectors.
The figures provided are the medians of the dataset, offering a more robust measure of the cyber risk landscape’s effect on the organization. This dataset, or bespoke event catalog, consists of all 10,000 scenarios simulated in the CRQ’s Monte Carlo analysis.
- Loss From an Event: Unlike the AAL, totaling $9.45 million, the median loss per ransomware incident within this organization’s CRQ simulation results is $2.3 million.*
- Event Duration: The median duration of the ransomware event in Figure 4, indicating how long the organization’s critical systems are nonoperational, is 9 hours.
- Data Records Compromised: According to the CRQ outcomes in Figure 4, the organization’s median data record loss after a ransomware attack is 4.2 million.
In addition to the median figure, the Event Statistics section displays both the probable minimum and maximum values, offering insight into how the median was determined.
*The Average Annual Loss (AAL) is calculated based on all of the yearly cyber loss scenarios run in the simulation, including those years that experienced no financial loss. The median loss, however, is calculated from a dataset that does not include those zero-loss years.
Initial Attack Vectors According to Cyber Event

Another invaluable element of the new Drill Down feature is the ability to now review which initial attack vectors are most likely to lead to a specific event and how much financial loss will ensue accordingly.
For the organization evaluated in Figure 5, ransomware events that have been the result of a phishing scam will result in roughly $2.07 million worth of damage, amounting to 21.88% of the total average loss due to this type of event.
Similarly, the new feature also illuminates that there is only a 0.69% likelihood that a ransomware event will, indeed, be driven by a phishing scam as the initial attack vector. These additional insights offer CISOs more sharply defined scenarios that can be used for mitigation planning and resource allocation.
With Kovrr’s CRQ platform, initial attack vectors are broken down according to the MITRE attack framework (ATT&CK) and include:
- Valid Accounts
- Human Error
- Exploit Public Facing Application
- Attritional
- Trusted Relationship
- Malicious Insider
- Phishing
- Lost or Stolen Devices
- External Remote Services
- Drive-By Compromise
- Supply Chain Compromise
- Hardware Additions
- Replication Through Removable Media
Greater Details Regarding Initial Attack Vectors
Drilling down to the more granular details of an organization’s isolated event forecasts is merely one way to gain a sharper understanding of the factors driving financial exposure. Another approach is to isolate the losses according to the event’s initial attack vector. With these metrics, CISOs can plan more targeted initiatives that reduce both the likelihood and loss potential.

In Figure 6, the Drill Down feature reveals core metrics as they relate to incidents and losses caused by a phishing scam. Just as with the “Event Type” component of Drill Down, the Initial Vector explorations offer:
- Top recommended actions for reducing the financial exposure of this vector (also highlighted in Figure 7 below).
- Insights into the forecasted loss data, explaining that they are derived from events initiated by the respective vector.
- The Average Annual Loss (AAL) and 1:100 Annual Loss the organization faces due to the attack vector.
- Key event impact statistics, including the medians, probable minimums, and probable maximums of the dataset.

It’s important to note that the Drill Down feature enables CISOs to explore greater insights for all of the attack vectors, except for attritional, and those that amount to a 1% or less chance of being the initial entry point that leads to an event. For example, if an organization has a 0.98% likelihood of “hardware additions” being the attack vector, the Drill Down feature will not be available for “hardware additions.”
Cyber Event Types According to Initial Vector

When exploring the more granular risk details and loss metrics according to the Initial Vector, organizations also now have the ability to determine which type of event an exploitation of the selected attack vector will lead to, as well as the respective financial losses.
In Figure 8, for instance, there is a 0.25% likelihood that the organization will experience a business interruption if an attack is initiated by a phishing scam. If this scenario takes place, and the organization experiences a business interruption caused by a successful phishing attack, they are expected to suffer, on average, $190.71 thousand in monetary damages.
Additional Event Benchmarks

Kovrr’s new Drill Down feature provides further cybersecurity benchmarking metrics. This information is available on the Risk Evaluation dashboard, offering organizations insights into how their industry’s average annual likelihood of experiencing any cyber event compares to other industries.
Similarly, CISOs can view this metric comparison based on organizational size, discovering how likely, on average, companies with both larger and smaller revenue bands are to experience a cyber incident.
Event Benchmarks Based on Event Type and Initial Vector

Additional Events Benchmark Insights are also available for both event types and initial attack vectors within the Drill Down feature. The benchmarks in Figure 10 display eMerchify’s average likelihood of experiencing a data breach, marked in comparison to its industry competitors (Peer Base Rate). Likewise, eMerchify risk managers can evaluate this Peer Base Rate in comparison to other industries, as represented above, or with organizations across revenue bands.
If CISOs leverage the Drill Down feature to explore peer benchmarking data related to initial attack vectors, they will find the exact same information as it relates to the likelihood of experiencing an event derived from the vector under examination.
Accessing More Granular Cyber Risk Details With the Drill Down Feature
With its ability to offer more granulated quantified metrics regarding specific cyber events, initial attack vectors, and event benchmarks, the new Drill Down feature on Kovrr’s CRQ platform empowers CISOs and cybersecurity professionals to make more informed, targeted decisions that strengthen risk mitigation strategies.
Moreover, these finer insights provide an opportunity to optimize budget allocation, ensuring resources are invested in the areas most prone to risk. The metrics can also be leveraged during high-level communications with non-technical stakeholders, not only to justify these investment decisions but also to showcase the tangible benefits of Kovrr’s CRQ solution.
To learn more about the Drill Down feature, get started with cyber risk quantification, and gain valuable insights that can enhance your cybersecurity program, contact our cyber risk experts or schedule a free demo today!
如有侵权请联系:admin#unsafe.sh
