2024-4-26 00:31:46 Author: cyble.com(查看原文) 阅读量:44 收藏
Key Takeaways
- A new Android Banking Trojan, “Brokewell”, was identified as distributing via a fake Chrome Update phishing site.
- The malware’s development is attributed to the developer, “Baron Samedit,” who manages the “Brokewell Cyber Labs” project.
- Utilizing Gitea, the malware developer hosts the Brokewell Android Loader project repository and shares underground forum links related to their profile.
- Brokewell Android Banking Trojan initially targets users in Germany but demonstrates potential expansion with references in multiple languages.
- Leveraging the Accessibility service, the malware implements key features such as keylogging, overlay attack, and cookie stealing.
- In its early development phase, the malware is expected to evolve with additional features and expanded targets shortly.
Overview
Mobile banking has become increasingly prevalent in recent years, offering users convenient access to financial services at their fingertips. However, with this convenience comes the risk of cyber threats targeting mobile devices, such as Android Banking Trojans. These Banking Trojans are designed to stealthily infiltrate smartphones, posing significant risks to users’ sensitive financial information. In this blog, we delve into the latest findings from Cyble Research And Intelligence Labs (CRIL) regarding a newly discovered Android Banking Trojan known as Brokewell. Uncovering its sophisticated capabilities and the activities of its associated with its developer.
CRIL identified the phishing site “hxxp://makingitorut[.]com” impersonating a Chrome Update website that is downloading a malicious APK file “Chrome.apk” from URL “hxxps://www[.]makingitorut[.]com/Chrome/Chrome.apk”.

Figure 1 – Phishing site downloading Chrome.apk file
The downloaded APK file appears to be a new Android Banking Trojan, equipped with features such as screen recording, overlay attack, and keylogging and boasting over 50 implemented commands. This malware was observed communicating with the Command and Control (C&C) server located at “mi6[.]operationanonrecoil[.]ru,” hosted on the IP address “91.92.247[.]182”.
Additionally, we discovered the git repository for the Brokewell Android Loadermhosted by a malware developer named “Baron Samedit” using Gitea.

Figure 2 – Malware developer hosting Git repository for Android Loader
The malware developer described this loader as capable of circumventing permission restrictions on Android versions 13, 14, and 15. They also shared links to profiles on underground forums, a Tor page, and a Telegram channel.

Figure 3 – Description of Brokewell Android Loader and Developer’s Profile link
Upon checking the C&C server, it displays the Git home page mentioning the name of the project, “Brokewell Cyber Labs,” operated by the developer, as shown in the figure below.

Figure 4 – Homepage of Git Repo mentioning project operated by the malware developer
Upon examining one of the provided profile links on an underground forum, it became apparent that the malware developer had posted about the Android loader. Furthermore, the Tor link was directed to the developers’s personal page, where they introduced themselves and shared a link to Brokewell Cyber Labs.

Figure 5 – Developers’s post on an underground forum

Figure 6 – Landing page of the Malware Developer
The malware developer’s personal landing page includes a Tor link to Brokewell Cyber Labs. This Tor site showcases a range of products developed by the Malware Developer, including checkers, validators, stealers, and ransomware, as illustrated in the figure below.

Figure 7 – Products listed on Brokewell Labs
We did not observe the mentions of the Android Loader or Android Banking Trojan on their site. This leads us to suspect that the malware has recently begun developing these tools and has not yet added them to their list of products. However, we will likely see these products featured on their site in the coming days.
Technical Details
This section presents a technical analysis of the Brokewell Android Loader and the Android Banking Trojan.
Brokewell Android Loader
After examining the source code, we gained insight into how the loader operates and installs the payload APK file. The loader saves the payload file in the /res/raw directory, which the malware developer referred to as the “implant.” Since the file is loaded from /res/raw, the loader does not prompt the user for any read/write external storage permissions.

Figure 8 – The main activity of the Brokewell Android Loader
The Brokewell Android Loader employs a session-based package installer to install the dropped file. Recently, the malware developer has been observed using this technique to bypass restricted settings.

Figure 9 – Android loader using the session-based package installer
The Brokewell Android Loader utilizes the package name “com.brkwl.apkstore”. Interestingly, we noticed the same package name referenced in the Android Banking Trojan. This suggests that the Loader will likely be employed to distribute the Brokewell Android Banking Trojan.
Brokewell Android Banking Trojan
The Brokewll Banking Trojan is currently in its initial stages of development and possesses limited functionalities. Its main approach to pilfering users’ credentials involves overlay attack and keylogging techniques. Nevertheless, additional features may be incorporated into the malware in subsequent iterations.
The Brokewell Banking Trojan possesses the following capabilities:
- Overlay attack
- Keylogging
- Cookie stealer
- Root detection
- Preventing uninstallation
- Steals call logs, recorded audio and screen recordings
- Sending SMSs
- Auto uninstallation
String Encryption
The malware employs string encryption utilizing the AES encryption algorithm. Furthermore, the malware appends the string “aWlpaWlpaWlpaWlpaWlpa” at the beginning of the encrypted string, which is subsequently removed during decryption. The following code snippet illustrates the encryption mechanism utilized by the malware.

Figure 10 – String encryption used by malware
To simplify the analysis process and enhance comprehension, we have replaced the encrypted strings with their respective decrypted counterparts throughout the blog.
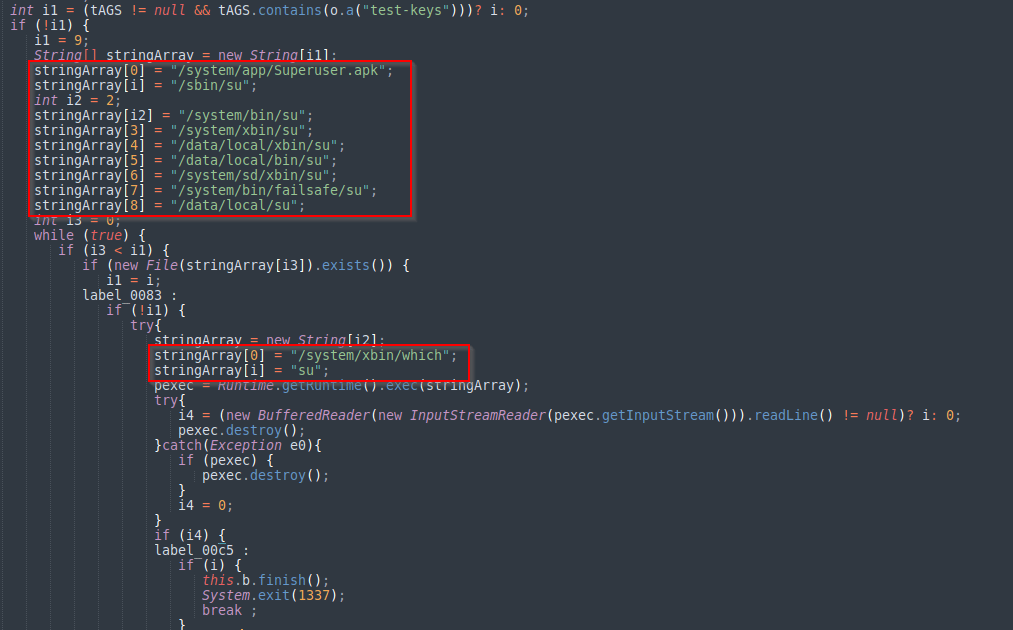
Root Detection
The malware conducts root detection checks by executing the following commands to determine whether the device has been rooted. If the malware detects that it is operating on a rooted device, it will halt its execution.
- /system/app/Superuser.apk
- /sbin/su
- /system/bin/su
- /system/xbin/su
- /data/local/xbin/su
- /data/local/bin/su
- /system/sd/xbin/su
- /system/bin/failsafe/su
- /data/local/su
- /system/xbin/which

Figure 11 – Malware executing commands to check if the device is rooted
Apart from executing commands, the malware checks for the presence of three application package names: “com.emanuelef.remote_capture”, “com.gmail.heagoo.apkeditor.parser”, and “com.joeykrim.rootcheck”. These apps are related to network monitoring, root verifier, and APK parser, respectively. If any of these applications are detected, the malware ceases its execution. This check aims to ensure that the malware is not running on a device where specific root-related or surveillance applications are installed, potentially indicating a rooted or monitored device.

Figure 12 – Malwware ceasing execution upon identifying the analysis or network monitor-related applications
Abusing Accessibility Service
Once the malware determines that the device is not rooted and does not have any network monitoring or root checker applications installed, it proceeds with its execution. It then prompts the victim to grant the Accessibility service, which the malware subsequently abuses to automatically grant permissions and carry out other malicious activities.

Figure 13 – Malware prompting to grant Accessibility service
After the victim grants Accessibility Service access, the malware automatically grants permissions for “Display over other apps” and “Unknown sources” installation, along with other necessary permissions. Once the auto-granting of permissions is completed, the malware displays a fake device lock PIN window, prompting the victim to enter the device password. The entered PIN is then saved to a text file named “already_submit_lockpin.txt”.
Notably, the fake device lock PIN window is observed in German, suggesting that the malware is specifically targeting users in Germany. Additionally, several samples of the Brokewell Android Banking Trojan submitted from Germany have been observed on VirusTotal.

Figure 14 – Fake device lock PIN window in German Langauge
Apart from references to the German Language, we observed strings in Chinese, French, Finnish, Arabic, Indonesian, Swedish, Portuguese, and English, indicating that this malware is capable of targeting other countries too.

Figure 15 – Malware has mentioned strings in various languages for the fake Device lock PIN window and Accessibility activity
KeyLogging
Right after obtaining Accessibility service permissions, the malware initiates the transmission of Accessibility logs about clickable, editable, scrollable, and focused events. These logs can contain the sensitive data entered by the victim. These logs are sent to the server using the endpoint “/acs/log-event”.

Figure 16 – Malware sending Accessibility logs to the server
C&C Communication and Ports
The malware utilizes a socket connection to communicate with the C&C server, enabling it to receive commands and transmit stolen data. Notably, we observed the malware creating an SQLite database named “implant.db” with table “tb_config” which saves the C&C domain with four uncommon ports (56231, 44478, 44479, and 45901), and based on server commands, the malware will update C&C domain and ports.

Figure 17 – Malware creates a database with C&C domain and ports
Overlay Attack And Cookie Stealer
Like numerous other prominent Banking Trojans, the Brokewell Android Banking Trojan leverages the overlay attack to target banking applications and pilfer credentials.
The Brokewell Android Banking Trojan utilizes the following commands to execute its overlay attack activity:
- openWebViewInject: Accepts the HTML injection page URL and loads it into the WebView.
- setInjectList: The malware receives the package name of the targeted application, injection page URL, and Toast message and stores them in a hashmap.
- ClearInjectList: Clears the injection list.
As mentioned in the command descriptions, the malware receives the Injection page URL link and loads it into the WebView. Upon loading the link into the WebView, the malware collects the cookie in the onPageFinished method. It transmits it to the server at the endpoint “/webv/dump-cookies”, along with the injection page URL and details of the infected device, as depicted in the figure below.

Figure 18 – Malware steals cookies upon overlay attack
Screen Recording
The Brokewell Android Banking Trojan employs Media Projection for screen recording and exploits Accessibility service to automatically commence screen capturing. Subsequently, the malware begins the screen recording process and transmits the recorded content to the C&C server through port 50002.

Figure 19 – Malware initiating screen recording using Media Projection
Upon receiving the command “doStartProjection” from the server, the malware triggers the screen recording process. During our investigation into the functionality of this command, we noticed a log message “CLICKING VNC COORD BTN:” within the malware, suggesting a focus on providing VNC functionality. Presently, the malware has incorporated commands associated with automatically executing gestures, capable of perpetrating on-device fraud.

Figure 20 – Malware log mentioning VNC while despatching gesture
In addition to the features mentioned above, the malware possesses the capability to capture screenshots, gather call logs, send SMS messages from the infected device, and perform various other actions. The table below presents the comprehensive list of commands executed by the malware.
| Command name | Description |
| Disconnect | Disconnects C&C server connectivity |
| doPING | Pings server |
| doINIT | Initiates C&C activity by sending basic device information |
| getInstalledPackages | Sends installed application package name list |
| checkIPexit | Sends infected device’s IP |
| getBattery | Sends infected device’s battery information |
| runSHELL | Run shell command received from C&C server |
| setC2addr | Updating C&C address in SQLite database |
| showNotif | Shows notification with the content received from the server |
| showOVLAY | Shows fake Android update overlay screen |
| AcsDumpCurrentNode | Get description and text from the currently active window |
| openCertainAPK | Starts APK with the package name received from the server |
| openWebvInject | Opens WebView for injection |
| askLOCKPIN | Displays fake lock screen window and saves entered password in the already_submit_lockpin.txt file |
| simulateVIBRATE | Creates vibration effect |
| doSendSMS | Sends SMS from the infected device |
| doPhoneCall | Makes a call from the infected device |
| doUninstallPKG | Uninstalls application |
| setInjectList | Saves the target application package name list for overlay attacks received from the server |
| ClearInjectList | Clears injection list |
| doEnableUnknownSourceInstall | Auto grants unknown source install permission |
| doSelfUpdateAPK | Downloads new APK and update itself |
| doInstallPKG | Download and install other applications |
| doRecordAudio | Initiates audio recording and sends recorded audio file to the server |
| doStartProjection | Initiates screen recording and sends the recorded file to the server |
| doStopProjection | Stops screen recording |
| doScreenshot | Captures screenshot |
| doClickElem | Auto-clicking particular elements based on element ID |
| doClickXY | Auto-clicking element based on coordinate |
| doSwipeXY | Auto swipes element based on coordinate |
| doDrawXY | Dispatch gesture based on coordinates |
| doTypingElem | Auto-type into the edit field |
| doScrollElem | Auto scrolls element |
| doGetGeoloc | Collects location |
| doCheckKeyguardState | Check if the device is locked |
| doHideIcon | Hides application icon |
| doUnHideIcon | Unhide application icon |
| doEnabAggressiveReconnect | Increasing counter to reconnect to C&C |
| doDisabAggressiveReconnect | Decreasing counter to reconnect to C&C |
| doWakeScreen | Waking up screen |
| openDeveloperOptions | Opens Developer Options setting |
| doGetCallHistory | Collects call history |
| doActivateAdminPermit | Activates device admin |
| doOpenNotifSettings | Opens application’s notification settings |
| doStopAcsSrvc | Stops Accessibility service |
| doSelfDestroy | Uninstall itself |
| doFlipANTI_UNINSTALL | Sets value to prevent uninstallation and allow installation |
| doGetPKGINFO | Getting the application name and package name |
| DoGlobalActionHome | Taking a user to the home screen |
| DoGlobalActionBack | Taking a user to the back screen |
| DoGlobalActionRecents | Toggles to show an overview of recent apps |
| DoSwipeUp | Swipes up |
| DoSwipeBottom | Swipes down |
| DoSwipeRight | Swipes right |
| DoSwipeLeft | Swipes left |
| DumpTelephonyInfo | Collects telephony information |
Conclusion
The Brokewell Android Banking Trojan poses a significant threat to mobile banking security with its advanced features, including screen recording, overlay attack, and keylogging. While our investigation indicates that the malware is currently in its initial development phase, it’s crucial to anticipate the emergence of more advanced versions with additional features and new targets. In the coming days, we may expect to see increased advertising on underground forums and features on the malware developer’s portal, highlighting the evolving nature of this threat and emphasizing the need for continuous vigilance and proactive cybersecurity measures.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Only install software from official app stores such as the Play Store or the iOS App Store.
- Using a reputed antivirus and internet security software package is recommended on connected devices, including PCs, laptops, and mobile.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Be careful while opening links received via SMS or emails sent to your mobile device.
- Google Play Protect should always be enabled on Android devices.
- Be wary of any permissions that you give an application.
- Keep devices, operating systems, and applications up to date.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | Malware distribution via phishing site |
| Execution (TA0041) | Command and Scripting Interpreter: Unix Shell (T1623.001) | Brokewell Malware can execute shell commands |
| Persistence (TA0028) | Event-Triggered Execution: Broadcast Receivers (T1624.001) | The malware registered broadcast receivers to steal incoming SMS |
| Defense Evasion (TA0030) | Download New Code at Runtime (T1407) | Malware can download and install APK file |
| Defense Evasion (TA0030) | Hide Artifacts: Suppress Application Icon (T1628.001) | Hides application icon |
| Defense Evasion (TA0030) | Impair Defenses: Prevent Application Removal (T1629.001) | Malware prevents uninstallation |
| Defense Evasion (TA0030) | Masquerading: Match Legitimate Name or Location (T1655.001) | Malware uses Chrome Icon and name |
| Defense Evasion (TA0030) | Virtualization/Sandbox Evasion (T1633) | Malware implemented anti-emulation check |
| Defense Evasion (TA0030) | Impair Defenses: Disable or Modify Tools (T1629.003) | Malware can auto-enable unknown source install permission and device admin permission |
| Defense Evasion (TA0030) | Indicator Removal on Host: Uninstall Malicious Application (T1630.001) | Malware can uninstall itself |
| Defense Evasion (TA0030) | Input Injection (T1516) | Malware can mimic user interaction, perform clicks and various gestures, and input data |
| Collection (TA0035) | Input Capture: Keylogging (T1417.001) | Malware can capture keystrokes |
| Discovery (TA0032) | Software Discovery (T1418) | Malware collects installed application package list |
| Discovery (TA0032) | System Information Discovery (T1426) | The malware collects basic device information. |
| Discovery (TA0032) | System Network Configuration Discovery (T1422) | Malware collects device IP and SIM Information |
| Collection (TA0035) | Screen Capture (T1513) | Malware can record screen content |
| Collection (TA0035) | Audio Capture (T1429) | Malware captures Audio recordings |
| Collection (TA0035 ) | Call Control (T1616) | Malware can make calls |
| Collection (TA0035 ) | Data from Local System (T1513) | Malware can collect cookies |
| Collection (TA0035 ) | Location Tracking (T1430) | Malware collects device location |
| Collection (TA0035 ) | Protected User Data: Call Log (T1636.002) | Malware steals call logs |
| Collection (TA0035) | Protected User Data: SMS Messages (T1636.004) | Steals SMSs from the infected device |
| Command and Control (TA0037) | Non-Standard Port (T1509) | Malware communicates with the C&C server using ports 56231, 44478, 44479, 45901 |
| Exfiltration (TA0036) | Exfiltration Over C2 Channel (T1646) | Sending exfiltrated data over C&C server |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 99f263fa87f13c7e6829dff73cc9c018d5f8165a5a7af3af8bc5ca6d52762ea9 8ae5196842dee3ba85dfc6a5e8d4e9aa40caa5e0 de1ab49d5ce82fd4f250579cf16df28a | SHA256 SHA1 MD5 | Brokewell Android Banking Trojan |
| d807070973bde0d85f260950dc764e46a0ba486f62da3e62f3b29ca3ea322f1 b9f55f4cb8ba6a4529ad955b4bdad36faf6b7476 4eb2573387c0c1bb248cbfb0f1f8936f | SHA256 SHA1 MD5 | Brokewell Android Banking Trojan |
| hxxps://www[.]makingitorut[.]com/Chrome/Chrome.apk | URL | Phishing site and Download URL |
| mi6.operationanonrecoil[.]ru | Domain | C&C server |
| 2ac038c44f1be53a1b652cafa4eba23af29831c7ebb75aaa00743b11c33665ea 3d88ba457dc75e29381213a38ebcf0ebfa59a406 0360fb17d1e7a9d9bf3197508323c156 | SHA256 SHA1 MD5 | Brokewell Android Banking Trojan |
| 00d35cf5af2431179b24002b3a4c7fb115380ebda496d78849bf3d10055d8a88 f5e24d031edf0ec9c67d98c9294d5904dae34394 8932768daaa490e27c7049ba772c8713 | SHA256 SHA1 MD5 | Brokewell Android Banking Trojan |
| 5ebb9e5cfe091ee8e00aa67c50a4aff2da90ce9eb6aa2b703a6e0bb3364359ce 4a870447d1ade26822f4ad03e21b9fdc3b3a658e a3dcd9c20ab80f0ebf20dc2f447e9388 | SHA256 SHA1 MD5 | Brokewell Android Banking Trojan |
| fsb[.]operationvenetic[.]ru | Domain | C&C server |
Related
如有侵权请联系:admin#unsafe.sh