2024-3-21 20:20:17 Author: www.vmray.com(查看原文) 阅读量:11 收藏
The VMRay Labs team actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cybersecurity landscape.
With this bulk update from December 2023 and January 2024, we’d like you to get familiar with our most recent responses to the dynamic changes in the cybersecurity realm.
In December 2023, the VMRay Labs team made improvements and new updates to:
- New VMRay Threat Identifiers including:
- VTI to detect usage of path exclusions to Windows Defender
- VTI to detect CAPTCHA as the only element on the page
- VTI to detect bypassing User Account Control
- and some more!
- New YARA rules including Pikabot and DarkGate malware families
- Reaction to LinkedIn Slinks phishing attempts
- Reaction to phishing attempts via Microsoft’s Customer Voice Service
In January 2024, the VMRay Labs team was specifically focused on the following areas:
- Adding new VMRay Threat Identifiers including:
- VTI to detect file executions from Alternate Data Stream
- VTI to detect attempts to enable SSH access
- VTI to detect attempts to enable WDigest support
- New YARA rules including:
- Detecting using NakedPages phishing kits
- Detecting fake reCAPTCHA pages
- AutoUI feature improvements:
- Enhanced phishing pages detection
- Adding automatic interaction with checkboxes and radio buttons
Now, let’s delve into each topic for a more comprehensive understanding.
New VMRay Threat Identifiers
In a few last blog posts, we’ve introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the submitted sample, is presented to you in the VMRay Platform after a completed analysis.
1) VTI: Detect when a CAPTCHA is the only visible element on the page
Category: Heuristics
We already have a few VTIs triggering on various CAPTCHA contained pages behaviors. In recently observed scenarios, phishing websites may employ CAPTCHA to disguise malicious URLs. Users might be prompted to solve a CAPTCHA before reaching the fake login page, creating a sense of legitimacy and making it harder for automated systems to detect the phishing site.
The new behavior that we address is when the CAPTCHA element is the only thing visible on the webpage. Webpages that consist only of a CAPTCHA and lack any additional content or functionality, could raise suspicion. Legitimate websites usually have other elements, such as navigation menus, branding, content, or functionality beyond just a CAPTCHA.

CAPTCHA – as the only element on the page – VTI
2) VTI: Detect usage of path exclusions to Windows Defender
Category: Defense Evasion
First, let’s explain what the exclusion path refers to in antivirus software, specifically for Windows Defender. Exclusion paths typically refer to directories or files that are excluded from the scanning or analysis process. Security software and malware analysis tools often allow users to specify certain paths that should be excluded from the scanning or analysis to avoid false positives, reduce scanning time, or prevent interference with critical system files.
Based on our research conducted in the end of 2023, we added the new VTI designed to identify suspicious activities involving the modification of exclusion paths within Windows Defender. This improvement aims to baffle a common tactic used by malware, where it exploits the exclusion feature of Windows Defender by adding itself to the path. By doing so, the malware attempts to evade detection and removal by the antivirus software.

Windows Defender exclusion VTI
3) VTI: Extend VTI for disabling Windows Defender
Category: Defense evasion
Additionally, we extended our existing VTI to detect behavior that disables Windows Defender using a registry key. By disabling antivirus protection, malware can operate on a system without being detected by the security software. This allows the malware to execute its functions without triggering alarms or alerts.
4) VTI: Detect enabling RDP using registry
Category: System modification
RDP stands for Remote Desktop Protocol. It is a proprietary protocol developed by Microsoft, which allows a user to connect to another computer over a network connection and interact with it as if they were physically present at that computer. Malware may modify the registry to enable RDP on a system if it’s disabled by default. This could allow the attacker to establish remote connections to the infected system.
To defend against this technique, we added this new VTI that triggers whenever a similar attempt has been detected in the analyzed file.

Enable RDP VTI
5) VTI: Detect bypassing User Account Control
Category: Defense evasion
User Account Control (UAC) is a Windows security tool which aims at protecting the operating systems from any unauthorized changes. It protects the system from malware and unintentional changes by requiring user confirmation or administrator credentials for certain actions that could potentially affect system settings. Sophisticated malware may attempt to disable or manipulate security software, including UAC settings, to operate without detection and interference. To stay ahead of this bypassing method, we added a new VTI to trigger when the UAC prompt is disabled.

Disable UAC prompt VTI
6) VTI: Detect entire webpage loaded via iFrame
Category: Heuristics
An iFrame, short for “inline frame,” is an HTML element used to embed another document or webpage within the current HTML document. It facilitates the display of content from external sources, such as different webpages or media files, directly within the current page. The content within the iFrame is essentially a separate HTML document loaded and displayed within the enclosing document.
In many cases, phishing pages are presented as plain HTML files containing only an iFrame that loads the phishing page, lacking any additional controls. Alternatively, a webpage on a new domain that is not blacklisted might be used to load the phishing page via the iFrame.
This new VTI enhances our capability to track and trigger alerts upon detecting maliciously structured pages designed for increased evasion.
7) VTI: Detect file executions from Alternate Data Stream (ADS)
Category: Execution
An Alternate Data Stream (ADS) is a feature in the NTFS (New Technology File System) file system used by Windows OS. NTFS supports the concept of multiple data streams associated with a single file. While the primary data stream contains the actual file data, Alternate Data Streams can be used to store additional information.
Each file can have one or more Alternate Data Streams, each identified by a unique name. These streams are not immediately visible through typical file management tools, and their existence may not be apparent to users. ADS can be used for legitimate purposes, such as storing metadata or additional attributes related to a file. However, ADS has also been exploited as a technique by malware to hide information, as it allows data to be associated with a file without visibly altering its size or properties.
To enhance our MITRE ATT&CK® coverage, we focused on addressing techniques such as those outlined in https://attack.mitre.org/techniques/T1564/004/. This involves adversaries utilizing NTFS file attributes to conceal their malicious data, thereby evading detection. Given that there are no legitimate reasons for creating files or scripts within an ADS and subsequently executing them, we’ve introduced this new VTI designed to identify and flag such behavior during dynamic execution.

VTI to detect file executions from Alternate Data Stream
8) VTI: Detect attempts to enable SSH access
Category: System Modification
Mitre Mapping: T1219
This VTI is strictly related to the functioning of Bundlore Adware, which is a type of adware that is known to affect macOS systems. The adware infiltrates the user’s computer through deceptive installation methods, such as bundling itself with other software or disguising itself as a legitimate application. Once installed, Bundlore displays intrusive advertisements, redirects web traffic, and may gather user data for targeted advertising purposes.
Bundlore can be challenging to remove completely because it often installs additional components or modifies system settings to evade detection and removal by antivirus software. Users are advised to be cautious when downloading and installing software from untrusted sources to avoid installing Bundlore or other adware.
Some variants of Bundlore adware are also trying to get remote access to victims’ devices by enabling SSH. To counteract this adware’s malicious activities, we’ve added a new VTI to detect such system modifications. This addition expands our coverage of the MITRE ATT&CK® techniques, in this case, further described in https://attack.mitre.org/techniques/T1219/.

VTI to detect enabling SSH access
9) VTI: Detect attempts to enable WDigest support in the registry
Category: Data Collection
Mitre Mapping: T1112, T1003.001
WDigest is a security support provider (SSP) in Windows that is used to implement Digest Authentication. Digest Authentication is a protocol used for authenticating users in network communications, particularly in web applications. In the Windows registry, WDigest support can be configured through various settings to enable or disable its usage. This is important for security purposes, as WDigest authentication is vulnerable to certain types of attacks and those conducted by TrickBot malware.
In Malwarebytes‘ words, “TrickBot (or “TrickLoader”) is a recognized banking Trojan that targets both businesses and consumers for their data, such as banking information, account credentials, personally identifiable information (PII), and even bitcoins. As a highly modular malware, it can adapt to any environment or network it finds itself in.”
In a recent malware campaign orchestrated by Trickbot, the attackers exploited the enabled WDigest support in the Windows registry to infiltrate users’ systems. Afterwards, they activated a screenlocker module, prompting users to log out and log back in. This action re-enabled WDigest support, leading to the caching of user credentials in the Local Security Authority (LSA) memory. Exploiting this vulnerability, the attackers could then scan the cache and retrieve the compromised login details.
To keep this dangerous technique in check, we’ve added the support of this new VTI that will trigger in samples where the WDigest protocols’ values were modified.

VTI to detect enabling WDigest support in the registry
Smart Link Detonation Updates
At the end of December 2023, we’ve made several improvements to the Smart Link Detonation (SLD) mechanism in our Platform products. If you haven’t read about it yet – SLD is a feature that enables the automatic evaluation and detonation of appropriate hyperlinks in document and email samples. Here’s a recap of the most important changes.
DoubleClick URLs
To deliver DarkGate and Pikabot malware, threat actor currently make use of documents that contain a download link hidden behind a DoubleClick URL. To automate the analysis of the delivery chains, we extended the trigger logic of SLD to activate a recursive sample detonation if the URL has been extracted from a document and matches the described pattern.
Malware authors may use DoubleClick URLs to redirect users to malicious websites. By disguising malicious URLs with legitimate-looking DoubleClick URLs, attackers can trick users into visiting harmful sites and then into downloading malicious files leading to DarkGate/Pikabot.
Reaction to LinkedIn Slinks phishing attempts
LinkedIn Slink is a LinkedIn smart link that is a shortened URL redirecting users to a different destination address upon clicking, a technique familiar to anyone who has encountered TinyURL or Bit.ly links. In the past few months, threat actors have been employing Slinks to disguise fake URLs in phishing emails, particularly by utilizing shortened LinkedIn URLs.
In this scheme, LinkedIn is automatically shortening the URLs shared by the users when their length exceeds 26 characters. The URL then looks like:
https://www.linkedin.com/slink?code=
A unique code is appended after the equal sign to redirect users to the intended URL. This method is designed to circumvent certain anti-spam and anti-phishing mechanisms, adding an additional layer of deception to the fraudulent URLs delivered in emails. Shortened links are frequently employed in the arsenal of social engineering tactics due to their ability to obscure the ultimate destination of the link, with well-known shortening services often being perceived as commonplace and trustworthy.
Now, the VMRay Platform’s SLD mechanism is triggered whenever Slinks from LinkedIn in the format given above are detected.
Phishing attempts via Microsoft’s Customer Voice Service
Microsoft offers a service called Customer Voice which is primarily intended to collect customer feedback. However, due to the nature and design of this feature, adversaries can also leverage it to deliver links to phishing pages which are “hidden” behind a legitimate Microsoft service.
After clicking on the “Play Voicemail” button, users are redirected to a phishing link impersonating a real Microsoft login page. At that point, the malware authors attempt to harvest your username and password. To address this recently observed tactic, we’ve enriched the SLD mechanism to detonate URLs that come from the customervoice.microsoft.com.

SLD – Phishing Attempts via Microsoft’s Customer Voice Service
DarkGate YARA rule
DarkGate is a remote access trojan (RAT), which has become the weapon of choice for malicious actors seeking to exploit vulnerabilities in the digital landscape. The DarkGate malware family exhibits a wide range of exploits, including the deployment of remote access software, activation of cryptocurrency mining capabilities, facilitation of privilege escalation, and keylogging. Furthermore, it is also known for seizing control of computing resources and remote desktop capabilities, affording DarkGate to manipulate files—such as moving, copying, viewing, creating, and deleting—exerting a comprehensive range of unauthorized actions.
In recent months, threat actor group TA577, known for the distribution of QBot in 2022/2023, got active again. After the takedown of their infrastructure, they moved away from QBot and now started to distribute DarkGate (besides IcedID and Pikabot). To address this shift in their malware usage, we created a YARA rule which is now capable of successfully detecting DarkGate. Additionally, we will generate high-quality IOCs (Indicators of Compromise) via configuration extraction for this malware family group.

DarkGate Sample Analysis in the VMRay Platform
Gh0stRAT YARA rule
Gh0stRAT is a trojan, discreetly spying on unsuspecting computers from the shadows. It made its first appearance in early 2016. Originally crafted to target the Chinese opposition, this tool quickly expanded its repertoire, becoming a weapon for cyber criminals engaged in a range of malicious activities, including industrial espionage and attacks on various companies.
The operating technique of Gh0stRAT involves discreetly running in the background, evading detection while extracting sensitive information, ultimately serving the malicious intentions of its operators. It is frequently distributed through advertisements on shady websites, exploiting users who unconsciously click on those fake ads.
According to our malware tracking dashboards, Gh0stRAT is currently part of the top 10 malware families observed in the wild. To be able to aptly detect this recently popular trojan, we’ve added a new YARA rule for Gh0stRAT.

Gh0stRAT Sample Analysis in the VMRay Platform
YARA rule to detect NakedPages phishing kit
NakedPages serves as a phishing toolkit primarily advertised and distributed across various cybercriminal channels, including select Telegram groups. Engineered specifically for Linux systems, NakedPages offers a suite of tools tailored for orchestrating malicious activities.
At its core, NakedPages is designed to facilitate phishing campaigns, providing cybercriminals with a diverse array of 50 phishing templates. Moreover, NakedPages operates under a Phishing as a Service (PhaaS) model, with multiple malware authors contributing to its ongoing development and refinement. In addition to phishing, NakedPages is also known for launching malware campaigns, using auto-generated JavaScript code to execute the attacks.
To stay ahead of the NakedPages threat, we’ve added this new YARA rule, which will trigger upon their detection in the analyzed sample.
YARA rule to detect fake reCAPTCHA pages
In previous updates, we delivered a VMRay Threat Identifier that triggers when CAPTCHA is the only element present on the page. Staying with this trending topic – this time, we’ve added a new YARA rule that is able to detect when a fake reCAPTCHA protects a phishing page.
reCAPTCHA is a security measure designed to distinguish between human users and automated bots. We recently stumbled upon a phishing attempt with a website protected via a fake reCAPTCHA that attempts to look like the legitimate one to be more trustworthy. In this relatively new technique, phishing actors may create fake login pages that include a reCAPTCHA widget. These login pages are not reachable unless users interact with the fake reCAPTCHA they created. In this scenario, the fake reCAPTCHA widget is used to evade automated analysis as it requires user interaction. To address this emerging threat, we added a new YARA rule that activates when attempts to mock the original reCAPTCHA are detected.
Auto UI Feature Improvements
Our Automatic User Interaction (AutoUI) engine simulates user actions by interacting with the samples to assess their behavior. In January 2024, we’ve enhanced the effectiveness of the AutoUI feature by improving the link detections and adding automated checkboxes and radio buttons interaction.
Automated checkbox and radio buttons interaction
In the landscape of online security threats, it’s crucial to stay ahead of malicious actors who exploit vulnerabilities in web forms. One recent tactic used by these actors involves the use of radio buttons and checkboxes to evade automated analysis of web pages. For instance, they might require the selection of a radio button to progress to the next stage of a phishing attempt. Without engaging with these elements, detecting such attacks becomes challenging.
Recognizing the importance of proactive defense measures, we’ve refined our AutoUI functionality to better navigate through deceptive elements on web pages. Further to address this behavior, we’ve added a new AutoUI rule to facilitate the automatic interaction with checkboxes and radio buttons, prioritizing those marked with the “required” attribute. This rule will ensure that AutoUI clicks on checkboxes and radio buttons, especially when they resemble CAPTCHAs or human verification mechanisms that might lead to next stages of a phishing attempt.
Enhanced phishing pages detection
Recently, we’ve come across a phishing campaign that attempted to evade detection by using oversized images, imitating an actual web page with clickable buttons. However, there were no real buttons present. With this exploit, phishers hide their malicious content behind innocently looking images rather than text.

An example of a phishing page that is just an image looking like a web page
This evasion technique exploits the fact that traditional detection methods primarily rely on textual cues, leaving them vulnerable to image-based phishing attempts. In response, we have implemented an AutoUI rule specifically designed to recognize and flag such deceptive behavior, improving our defenses against similar threats in the future.
Pikabot’s unexpected return
Pikabot, also known as Beep Loader, reemerged in early 2023 and returned later in the same year, featuring advanced evasion techniques and string obfuscation to increase the complexity of its analysis. The Pikabot’s comeback can be attributed to the recent activities of the threat actor group TA577, which has been actively distributing samples of this malware family. In response, we have improved our detection capabilities by revising its delivery chains and enhancing the Pikabot YARA rule.

Pikabot’s activity November-January 2023
User Experience improvements
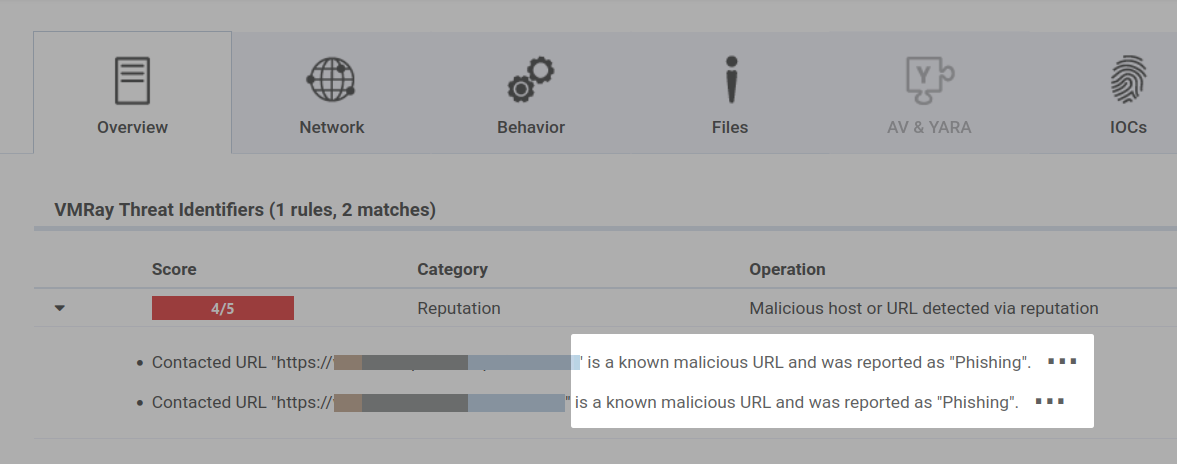
From the introduction of this enhancement in December 2023, you can see the reason of a submitted sample’s malicious or suspicious reputation in the VMRay Threat Identifiers overview. Previously, you might have seen notifications like “Submitted URL ‘xxx’ is a known suspicious URL.” Now, with our update, you will receive a more comprehensive understanding of the sample’s status. For instance, you’ll encounter notifications such as “Submitted URL ‘xxx’ is a known suspicious URL and was reported as ‘spam.’”
This refined level of information enables more informed decision-making and heightened security awareness.

Pikabot’s activity November-January 2023
We do hope our constant research of new malware trends and the features we together bring to our products help you in the navigation of the complex landscape of cybersecurity. Stay tuned for the news from February 2024, which we will share in the upcoming weeks!
如有侵权请联系:admin#unsafe.sh