2024-3-28 16:43:36 Author: www.vmray.com(查看原文) 阅读量:11 收藏
Introduction
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cybersecurity landscape.
In February 2024, the VMRay Labs team has been specifically focused on the following areas:
- Adding new VMRay Threat Identifiers including:
- Detection of services masquerade
- Detection of renaming system utilities
- Amadey VTI
- New YARA rules and updated configuration extractors for malware families, including:
- Pikabot
- Lumma Stealer
- AutoUI feature enhancements addressing:
- Multi-staged phishing attempt using pages hosted on Adobe InDesign
Now, let’s delve into each topic for a more comprehensive understanding.
New VMRay Threat Identifiers
In a few last blog posts, we’ve introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you on the VMRay Platform after a completed analysis.
1) VTI: Detect renaming system utilities
Category: Masquerade
MITRE ATT&CK® Technique: T1036.003
Security software often relies on specific file names and locations to detect and remove malware. By renaming system utilities to something less recognizable or even mimicking legitimate system file names, malware can evade detection by antivirus and other security tools. Now, let’s explain how this technique can be used in a real-life scenario.
As already mentioned, the primary aim of this technique is to evade detection measures. For instance, manipulating rundll32.exe, a legitimate Windows executable tasked with running Dynamic Link Libraries (DLLs), often raises suspicion due to its potential for executing malicious DLLs. By leveraging rundll32.exe, malware can hide its activities within the guise of a legitimate process, complicating detection efforts. Furthermore, this tactic focuses on potential gaps in security tools. Some security solutions may not actively monitor the execution of rundll32.exe, either due to allowlisting mechanisms or to avoid generating false positives from routine system operations. As a result, malware employing this technique exploits unmonitored areas and detection capabilities of security systems.
Additionally, by disguising rundll32 under a different name, malware can bypass certain detection mechanisms that rely on command-line arguments or binary names. This obfuscation not only aids in concealing the malicious intent but also complicates efforts to identify and mitigate the threat.
To enhance our MITRE ATT&CK® coverage and protect you from this masquerade technique, we enriched our Platform products with this new VTI..

2) VTI: Detect services masquerade
Category: Masquerade
MITRE ATT&CK® Technique: T1036.004
In another observed masquerading technique, malware authors may manipulate the names of services or tasks within the Operating System. These altered names relate specifically to services and tasks generated by the malware itself, rather than pre-existing entities within the system. By doing that, they, of course, try to evade detection by security software and aim to make their malicious activities appear benign. Here’s how they can achieve it:
Service name masquerade – malware may register itself as a service with a name that closely resembles a legitimate Windows service. For example, instead of using the legit “W32Time” name, which is used in Windows to synchronize time accurately between networked computers, they might use a similar-looking name such as “W32Tlme” or “W32Tlmesvc“. This makes it less conspicuous and may prevent users or security tools from identifying it as malicious at first glance.
To enrich our MITRE ATT&CK® coverage, we addressed the technique outlined in https://attack.mitre.org/techniques/T1036/004/ and added this new VTI to our Platform products.

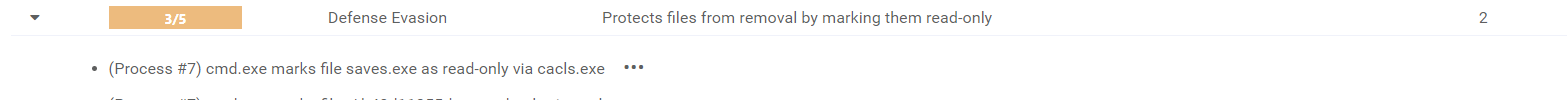
3) VTI: Detect protection method to mark files as read-only via cacls.exe
Category: Defense Evasion
MITRE ATT&CK® Technique: T1222
In a February observation of an Amadey malware sample, we addressed one of its tricky behaviors. One process employed by this Amadey sample led us to the exploitation of the cacls.exe command-line utility.
Let’s stop here to recap what the cacls.exe command line is and how crafty threat authors can use it. cacls.exe is a command-line utility in Windows used to display or modify Access Control Lists (ACLs) for files and directories. ACLs are security descriptors that define which users or groups have permissions to access or modify a particular file or directory. With cacls.exe, administrators can grant or revoke permissions, change ownership of files and directories, and view the current security settings.
However, just like all legitimate actions, malware authors may use it in the same manner as administrators but for malicious purposes. In our analysis within the Platform, we noticed that the Amadey sample employed cacls.exe to modify file permissions, specifically marking files as “read-only”, thereby impeding their removal and facilitating the malware’s persistence.

To stay ahead of this recent threat, we’ve improved the VMRay Threat Identifiers to detect occurrences of similar behaviors in the samples.

New YARA Rules
YARA rule extension for Pikabot
Pikabot loader emerged into the digital landscape at the beginning of 2023, swiftly establishing its presence as a significant threat, with one of the distributing threat actors identified as the ransomware-associated group TA577. Being a loader, Pikabot is designed to load and execute other malicious components onto a victim’s system. It serves as an initial stage in an attack chain, where its primary function is to deliver and execute additional payloads.
Key features that make Pikabot unique are:
- Indirect syscalls are a sophisticated malware evasion technique in which malware disguises its system calls to appear as if they originate from legitimate system components rather than the malware itself. This makes detection more challenging for Endpoint Detection and Response (EDR) systems. Read more about indirect syscalls and other techniques used by Pikabot in our recent blog posts.
- It consists of an loader and core module. The loader-core module architecture enables dynamic payload delivery, allowing the Pikabot’s samples to adapt and evolve over time.
Still, the cat-and-mouse game goes on. While the cybersecurity community delves deeper into understanding this malware family and fortifying their defenses, malware authors continue to evolve their strategies. Remaining underground for some time, Pikabot reemerged in February 2024 with an updated loader, named by researchers as “Pikabot’s (D)evolution”, sparking speculation about its next move.
This new version introduces the following changes:
- Enhanced evasion techniques: The latest iteration of the malware shows advanced anti-debugging methods, significantly increasing their ability to evade detection by security analysts and forensic tools.
- Refined encryption: There is a notable reduction in the usage of inline RC4 functions within the Pikabot’s samples. This modification reflects a strategic shift towards more sophisticated encryption algorithms, enhancing the malware’s ability to obfuscate its payload and communication channels.
- Configuration handling: Previously stored in JSON format, the configuration data is now displayed in plain text during runtime. This change streamlines the retrieval process, eliminating unnecessary parsing overhead and enhancing operational efficiency.
- Refurbished communication protocol: Pikabot’s network communication protocol discontinued the usage of AES (Advanced Encryption Standard) encryption. This departure means that Pikabot’s authors may have explored alternative encryption algorithms or obfuscation techniques to further enhance stealth and evade detection.
In response to Pikabot’s evolving tactics, we enhanced the YARA rules to identify a broader spectrum of this malware’s activities. Furthermore, we refined our Pikabot’s configuration extraction processes to provide the most actionable Indicators of Compromise (IOCs), empowering your Threat Hunting, Threat Intelligence, and Detection Engineering workflows.


New Configuration Extractor & YARA Updates for Lumma Stealer
Lumma Stealer – a digital thief that emerged in 2022, written in the C programming language. This malware has quickly become a significant player in the cyber underworld. Lumma specializes in stealing valuable information, especially crypto wallets and two-factor authentication (2FA) credentials. It is being sold on Russian forums as Malware as a Service (MaaS).
Once Lumma steals your data, it sends it to its Command and Control (C2) server. And here’s the kicker: Lumma leaves absolutely no trace behind, making it a truly elusive adversary. Remember, Lumma isn’t just an average piece of code; it’s a real-life digital thief, ready to snatch your valuable data without a second thought.

As Lumma gains traction, we’re closely monitoring its evolution. In recent campaigns, threat actors have spread Lumma samples through hacked YouTube channels. This channel advertised their installation guides for cracked software. Once users are lured in, the video provides software’s download URLs, often shortened using services like TinyURL, leading to a download of an infected ZIP file. Lumma’s distributors have the cheek! They practically dare you to disable your antivirus, promising clean files. How trustworthy, right? The final destination of these links is far from benign. Users initiate the download of a .NET loader, which acts as the gateway for the retrieval and execution of Lumma Stealer.
To catch up on Lumma’s most recent variants, we’ve improved our configuration extractors, and YARA matches for this malware family’s new behaviors observed in its v.4.0 version.

Auto UI Feature Improvements
AutoUI (Automatic User Interaction) is our advanced functionality designed to simulate user actions during Dynamic Analysis, enabling thorough sample detonation. This feature enables researchers to replicate various user behaviors, such as opening files, clicking buttons, or entering text, providing deeper insights into the behavior and functionality of analyzed samples.
Recently, we detected a phishing attempt originating from a webpage hosted on the official Adobe InDesign services. The page was a PDF interface, displaying what appeared to be a clickable link with the text “Sign in.” Users often trust PDF files more than other file formats due to their perceived reliability and familiarity. Additionally, PDFs preserve the layout and formatting of documents across different platforms and devices. This trust makes users more likely to open PDF attachments or click on links within PDFs without scrutinizing them thoroughly.
Upon closer examination of this attempt, our analysis uncovered, among many more, that none of the apparent buttons within the interface are actually present as separate controls within the page properties. They were, in fact, simulated buttons designed to deceive users into clicking, leading to phishing redirections.
In essence, Adobe InDesign’s service was exploited as part of these phishing campaigns. With this understanding, we are now equipped with an improved AutoUI feature to interact effectively with the page, unveiling the subsequent stages of the phishing attempt.

Final Thoughts
We do hope our constant research of new malware trends and the features we together bring to our products help you in the navigation of the complex landscape of cybersecurity.
Stay tuned for our March signature and detection updates, planned to be published in the weeks ahead.
如有侵权请联系:admin#unsafe.sh