This post recounts an attempt at fraud via SMS and voice call with a fake voice, targeting an elderl 2024-3-27 20:16:23 Author: www.adainese.it(查看原文) 阅读量:18 收藏
This post recounts an attempt at fraud via SMS and voice call with a fake voice, targeting an elderly person. Although this type of fraud is not new, the way it was executed deserves further examination. The article aims to be informative and comprehensible, in order to increase awareness among non-professionals.
I especially thank the friend who allowed me to experience and analyze this type of attack.
The Facts
The mother (hereafter referred to as M) of a friend (son of M, hereafter referred to as F) receives an SMS at 12:32 that appears to be a simple scam:
Hi Mom, I lost my phone. This is my new number. +393791234567 Please send me a message on WhatsApp. I can be reached there! ( Attachment 1 )
We should be trained not to believe in this type of SMS, however, the sender of the message provides the full name of F. This detail makes it more credible.
Anomalies:
- Why does a new phone number appear already in M’s address book?
- Why does M have to use WhatsApp instead of a text message or a simpler and more convenient phone call?
Understandably, a few minutes later, M responds to the SMS message with a confirmation. Almost instantly, M receives a call from the attacker (hereafter referred to as A). The sender’s number is still +393791234567 but the phone displays it with F’s name. The voice on the phone is that of F, claiming to have lost the cellphone, dictating the new number, and then hanging up.
Anomalies:
- Why is the phone call just a simple monologue from F?
Fortunately, shortly thereafter, F goes to M’s house, understands the situation, and calls me for advice. The attack is stopped, and the involved individuals are made aware and secured.
Analysis
The attack drew my attention to two extremely relevant facts that make it extremely credible and effective:
- The use of F’s voice.
- The cell phone number displayed on the phone with F’s full name.
By indirectly analyzing the various evidence left by A, I noticed that M’s address book contained two entries for F: the first one correct, saved on the cellphone, the second one fake, saved on Gmail. Since the cellphone is an Android, M’s address book displays a combination of local and Google elements. Without specific investigations, the elements appear identical. Upon closer examination of the fake element, I noticed that it was created moments before the first SMS.
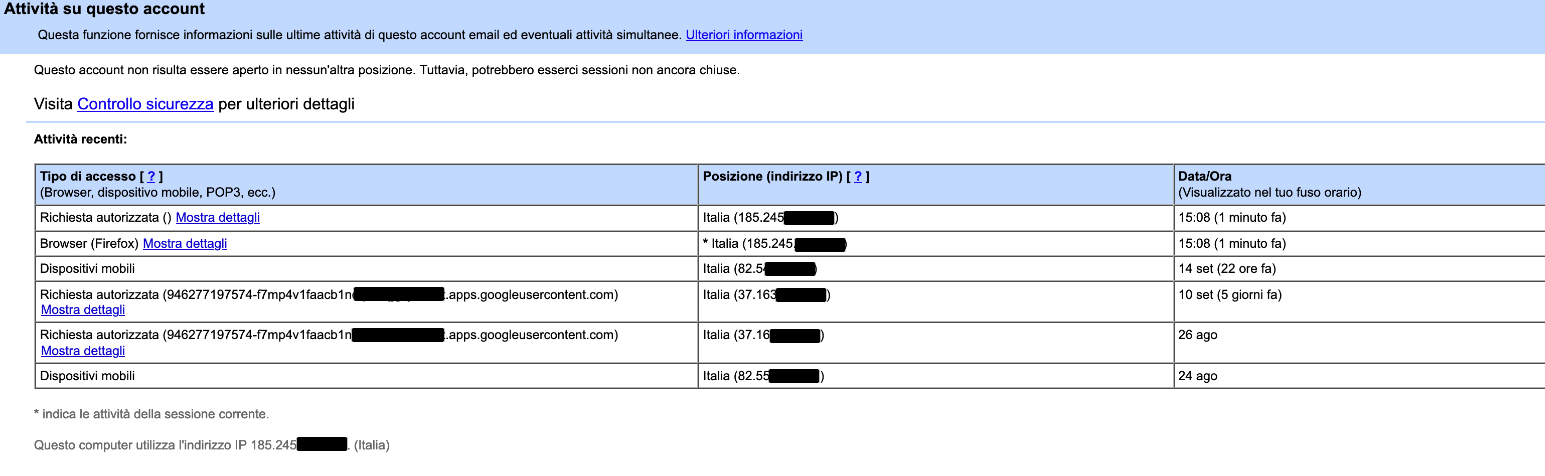
Accessing Gmail allows us to see the latest events ( Attachment 2 ):
We see that:
- The first two entries concern me logging in.
- The one labeled “Mobile devices” was made near the time of the attack (unfortunately, the details did not allow me to understand exactly when).
- The next two (Authorized request) relate to applications requesting authorization (via OAuth2) to access part of Google’s data. I assume these are applications (websites or installed on the phone) that need to use Google’s data, for example: applications for managing contacts, calendars, but also WhatsApp itself that wants to make a backup.
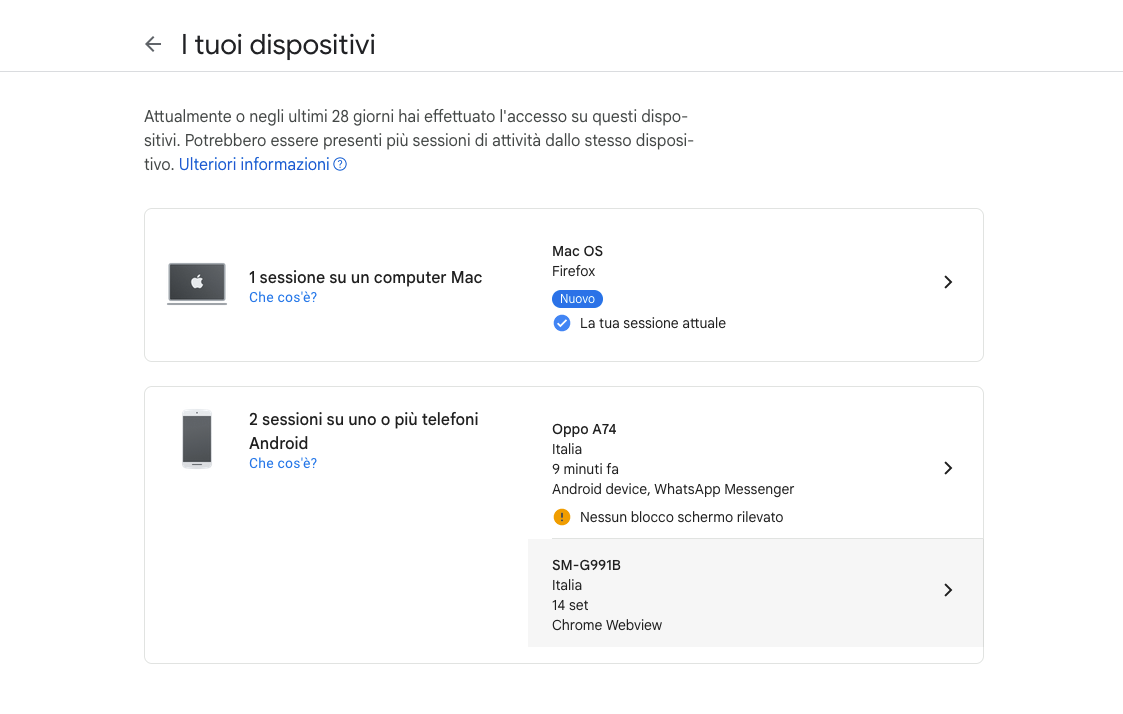
In the Google account management, it is possible to check which sessions are active, and in particular which devices are connected ( Attachment 3 ):
We see that:
- The Firefox session on Mac concerns me.
- The first cellphone (Oppo) is M’s.
- The cellphone SM-G991B concerns F’s sister (hereafter referred to as S). In particular, we see that S performed an activity on the Google account on the day of the attack, via Chrome Webview.
From there onwards, unfortunately, the Google data was not helpful enough. Checking M’s cellphone remotely, I found nothing abnormal; while I find the activity on S’s cellphone on the day of the attack to be a very interesting coincidence.
Securing
The analysis tells us that:
- M’s account was violated, as a fake entry was added to the address book. We can assume that all data associated with Google has been compromised. In this specific case, these are: contacts, Google Drive, email.
- Probably the attack originated from S’s cellphone, so the same applies to her Google account.
Securing requires:
- that the involved individuals (M, F, S) are aware of what happened and can identify even more realistic attacks, which will be possible thanks to the data stolen from the two Google accounts;
- changing the passwords of the two Google accounts;
- enabling multi-factor authentication (or MFA);
- deleting all active sessions;
- removing all connected applications;
- securing all accounts that have the same password as the Google accounts, are connected to them, or are used within potentially compromised devices.
In this specific case, the cellphones were mainly used as phones. I breathed a sigh of relief when I realized that there were no banking applications present.
The Attack
It is now clear how the attack was structured:
- Through a compromise of the Google account (via application, vulnerability, or credential theft), the attacker creates a fake entry in the target’s address book.
- The attacker creates an audio file, impersonating the voice of a relative of the target.
- The attacker sends a series of bait SMS messages, attempting to move the conversation to WhatsApp.
- To people who respond via SMS (and presumably also to those who respond via WhatsApp), the attacker calls the target using the previously created audio.
- The attacker tries to convince the target that there is an emergency situation and that they need money, to be sent via bank transfer.
If the attack I witnessed was thwarted, a brief investigation led me to understand that it is currently widespread and that unfortunately some elderly parents have fallen into the trap, losing several thousand Euros.
Lesson Learned
Current deep learning technologies that allow the creation of audio files with the voices of others are extremely dangerous. Outdated phones and insecure applications provide attackers with tools that allow them to create false identities very easily and effectively.
We should expect even more complex attacks, where phone calls are no longer simple monologues but real conversations.
We must be able to identify anomalies and perform control tests to understand if the person communicating digitally with us is who they claim to be or if they are simply impersonating someone else based on information easily available on the internet.
We must understand that since digital life blends with physical life, it requires the same level of attention: if driving on the road requires a license and attention, “driving” a cellphone that contains access to the bank account requires the same level of awareness and attention. Saving and using outdated cellphones, not updated or installing anything that appears on the screen out of curiosity, is NOT a good idea and can have serious consequences.
In this case, it turned out well, but in others that I have experienced, the attack was successful, and the bank account was emptied.
References
如有侵权请联系:admin#unsafe.sh