
2024-3-12 03:45:0 Author: www.tenable.com(查看原文) 阅读量:9 收藏
Discover how contextual prioritization of exposure is revolutionizing OT/IoT security, enabling organizations to shift from reactive to proactive breach prevention.
Connectivity of physical assets— such as heating, ventilation, and air conditioning (HVAC) systems in data centers and office buildings, and cameras on the manufacturing floor – has created an expanding cyberattack surface. As IT, operational technology (OT) and Internet of Things (IoT) assets become increasingly interconnected, pathways are created for threat actors to traverse IT and OT environments, with devastating results. Consequently, today's CISOs find themselves increasingly accountable for securing not only IT environments, but OT and IoT environments as well.
To combat these threats, enterprise security organizations must understand the risks to assets in a business context. This was the focus of part one in this three part blog series, “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform.” In this second installment, we’ll expand on key challenges that impede effective breach prevention. We’ll also explain how enterprises can operationalize exposure management (EM) by using an attacker’s perspective to prioritize, and that way maximize their security team’s limited staff and resources.
Taking vulnerability management to the next level with exposure management
Vulnerability management (VM) is a critical component of any successful security program. It looks to proactively identify weaknesses that could allow attackers to breach the perimeter, move laterally, and achieve a desired objective. VM programs frequently leverage the Common Vulnerability Scoring System (CVSS) to assess the severity of publicly disclosed Common Vulnerabilities and Exposures (CVEs) and prioritize what to remediate first. This is a great starting point. However, a standard CVSS score does not take into account other important variables, such as asset criticality and relationships. These could be used to refine risk assessment and more accurately identify true business exposure. As a result, security teams can end up overwhelmed, chasing an endless mountain of critical and high-severity findings.
To address this challenge, EM introduces additional layers of visibility which are vital for effective prioritization. For example, EM looks to identify the entire attack surface, which includes not only traditional IT assets, such as laptops and servers, but also OT and IoT assets, including those that are unseen and unmanaged, as well as human and machine identities – all of which are potential targets of attackers. EM also looks at all three preventable forms of risk – vulnerabilities, misconfigurations and excessive privileges – that allow attackers to not only gain initial access but to move laterally. With this foundation of broad and deep visibility into assets and risk across the attack surface, EM can apply additional layers of context, beyond CVSS, to more effectively assess and prioritize true risk exposure.
Operationalizing EM to optimize prioritization and remediation
Our Tenable One Exposure Management Platform provides a top-down, business-aligned view of cyber exposure. Assets and identities (regardless of domain or silo) are aligned to what matters most to the organization — the manufacturing plant, business processes or mission-critical applications they support.
In this blog, we explain the importance of having a contextual view of business exposure, and discuss how you can leverage this top-down context to more effectively and precisely prioritize remediation – and that way significantly reduce the risk to your organization.
Business-aligned cyber exposure
With Tenable One for OT/IoT, rather than manually look for risk across the entire attack surface of internally and externally facing assets, organizations can instantly see business-aligned exposure cards, reflecting the overall Cyber Exposure Score (CES) for each critical area of the business. In the hypothetical example below, we can see a manufacturing plant in Chicago that represents a major revenue source for the organization. The plant has an overall CES of 220/1000 (B). This tells us that the relative exposure of the overall plant is low. We can quickly assess what category of assets represents the greatest risk to the plant.
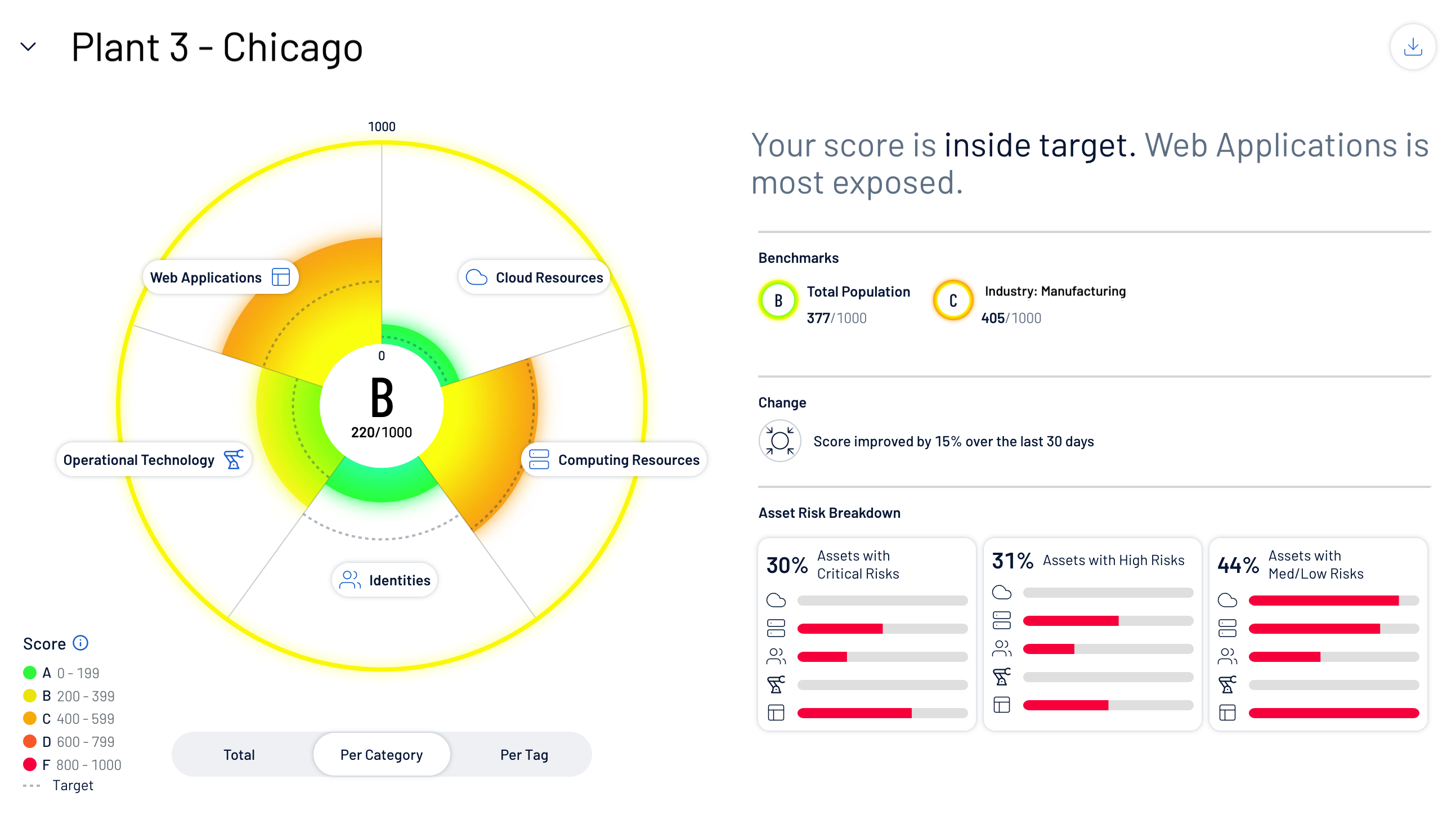
Additionally, Plant 3’s CESs can be used as a benchmark when assessing risk across multiple sites, which is useful in prioritizing future investments in headcount needed for remediation.
Business-aligned asset exposure
But as a primary revenue driver, we also need to understand the specific assets that may represent continued exposure for the manufacturing plant. From the Plant 3 - Chicago exposure card we can access the associated asset inventory view shown below. The asset inventory reflects all assets that are aligned to the plant, along with an Asset Exposure Score (AES) for each asset. The AES is designed to provide a simple to easy-to-understand, prioritized view of assets that represent the greatest risk of exposure.
Worth noting, the CES for the above exposure card is automatically calculated by aggregating and weighing the AES of all assets aligned to this specific plant through the use of machine learning algorithms.
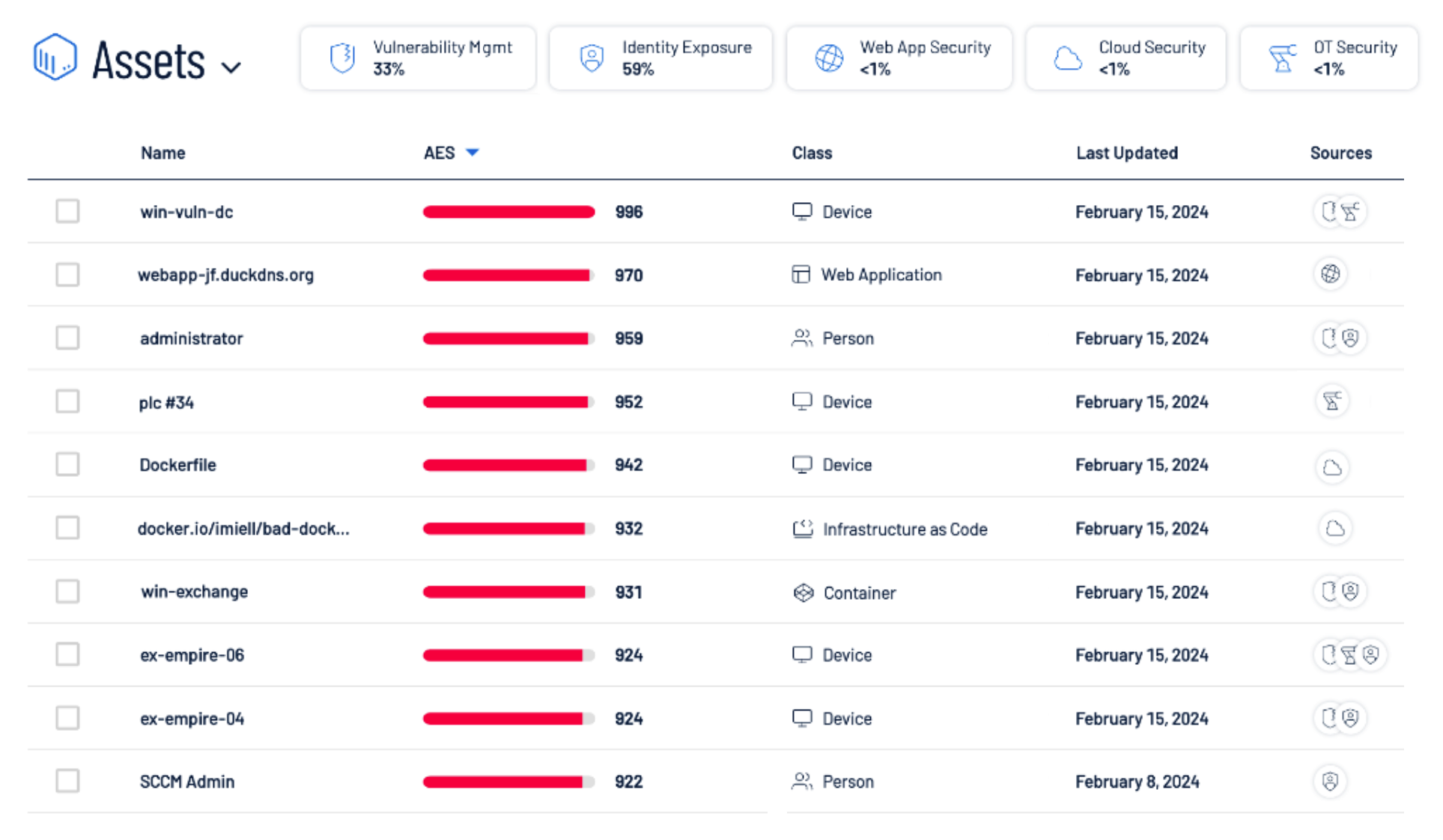
Deep asset context
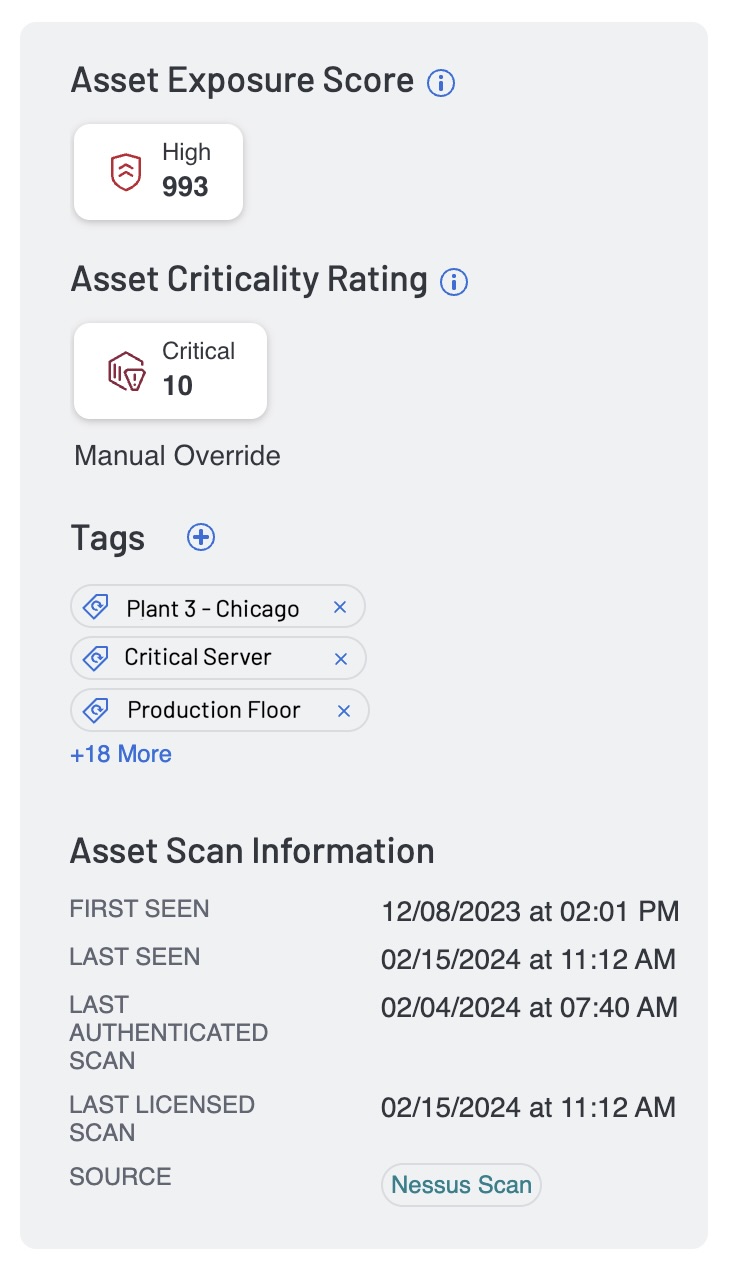
If we are to leverage AES as a key means of improving prioritization, it is important to understand and have direct access to how AES is calculated. The first critical piece of context used to derive AES is the Asset Criticality Rating (ACR). ACR measures the relative importance and potential impact of an asset. ACR is based on several key metrics such as business purpose, asset type, location, connectivity, capabilities and third-party data. For example, a server should have a higher asset criticality than an IoT asset such as a printer. Further, an asset associated with a mission-critical plant should receive a higher criticality rating than one that is not aligned to revenue generation. ACR can be manually tuned to meet an organization’s specific requirements using asset tagging, as reflected in the example below. ACR is expressed as an integer from 1 to 10, with higher values corresponding to the asset being more critical to the business.
The second piece of context used to derive AES is the Vulnerability Priority Rating (VPR). VPR represents the severity and exploitability of a given vulnerability. VPR takes into consideration a range of static (e.g. CVSS) and dynamic variables to calculate the likelihood that a specific risk, such as a CVE or misconfiguration, will be exploited. Key variables used to calculate VPR for a given risk include the availability of exploit code in exploit kits and frameworks, references to exploitation on the dark web and hacker forums, reports of exploitation on social media, public proof-of-concept (PoC) research, and detection of malware hashes in the wild. Such threat intelligence is key in prioritizing weaknesses that pose the most risk to an organization. VPR is expressed as a number from 0.1 to 10, with higher values corresponding to a higher likelihood of compromise and higher impact on a specific asset.
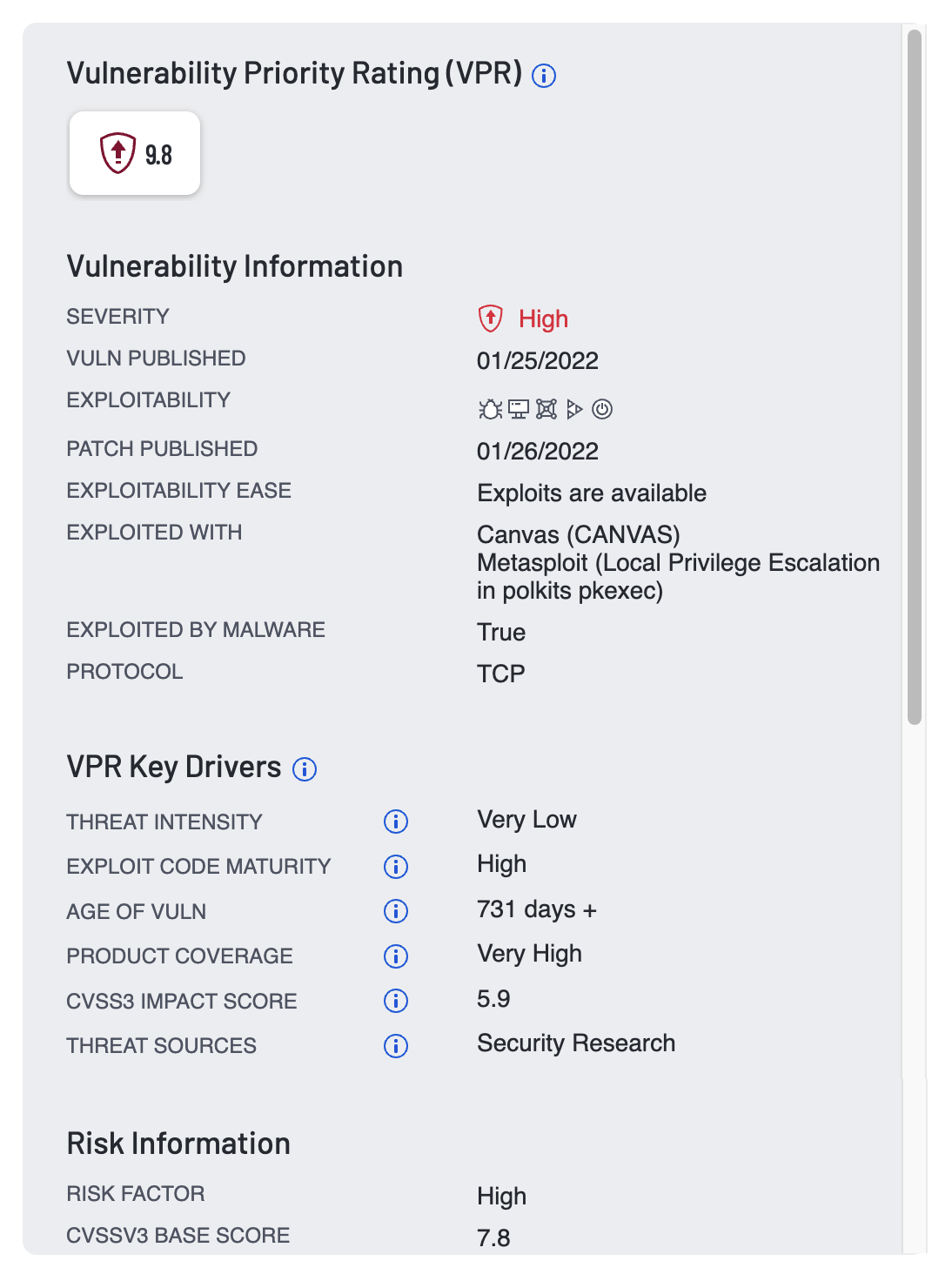
Because it is not unusual for a single asset to have multiple weaknesses, Tenable One aggregates the VPR for all weaknesses associated with a given asset, along with the ACR to calculate an overarching AES. This ensures that total risk is reflected in the overall AES. As a result, AES makes it possible to quickly identify which assets pose the greatest risk of exposure to the business, without the need to manually research all of the potential variables that exist in the wild. On its own, the business context and prioritization provide a significant improvement over less dynamic and holistic approaches.
Enhancing prioritization with attack path analysis
Now that we have a baseline understanding of how AES is calculated, let’s see how we can operationalize AES, and further enhance prioritization by looking at asset exposure from an attacker’s perspective.
In OT-heavy environments, such as our hypothetical manufacturing plant, it is not uncommon to see a cross-section of IT, OT, and even IoT assets. We will also have human and machine identities that have access to the network. As we’ve seen in many breaches, OT assets don’t usually enable initial access for an attacker. It is more often vulnerable IT assets, sometimes known, and other times unseen or unmanaged that provide an open door. Similarly, human and machine identities can be compromised due to poor hygiene or lack of policy, including weak passwords, lack of multi-factor authentication, and even due to the compromise of vulnerable assets used by third party vendors to access the network.
While AES provides a solid foundation for deciding what assets to prioritize and why, the optimal way to minimize exposure to the business is to have visibility into the complete attack path, so that you can determine which risk should be remediated first.
Attack path visualization and prioritization capabilities in Tenable One for OT/IoT provide a proactive response to remove paths that attackers may take. It performs this function by mapping critical risks to the MITRE ATT&CK framework, thus allowing security teams to visualize all viable attack paths continuously. This reveals critical insights on externally facing and newly added assets, communication patterns, relationships, and previously unknown attack vectors. This visibility allows security teams to implement controls to mitigate risk of compromise.
Asset Vulnerability Exploit
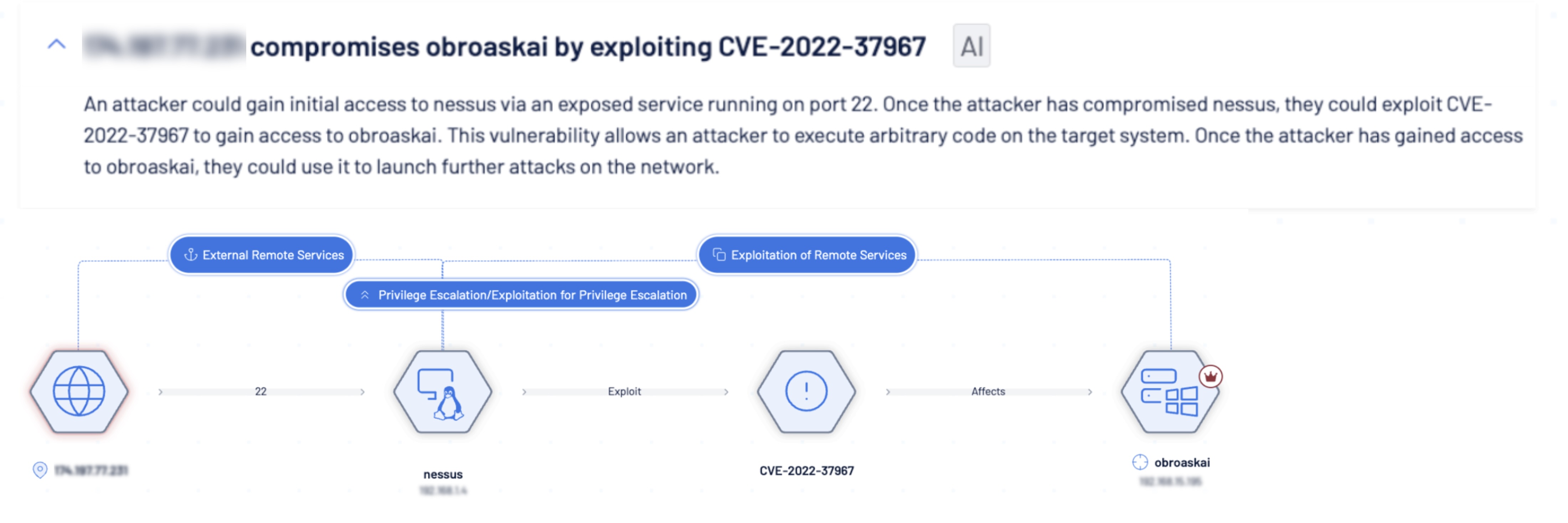
Machine Identity Compromise
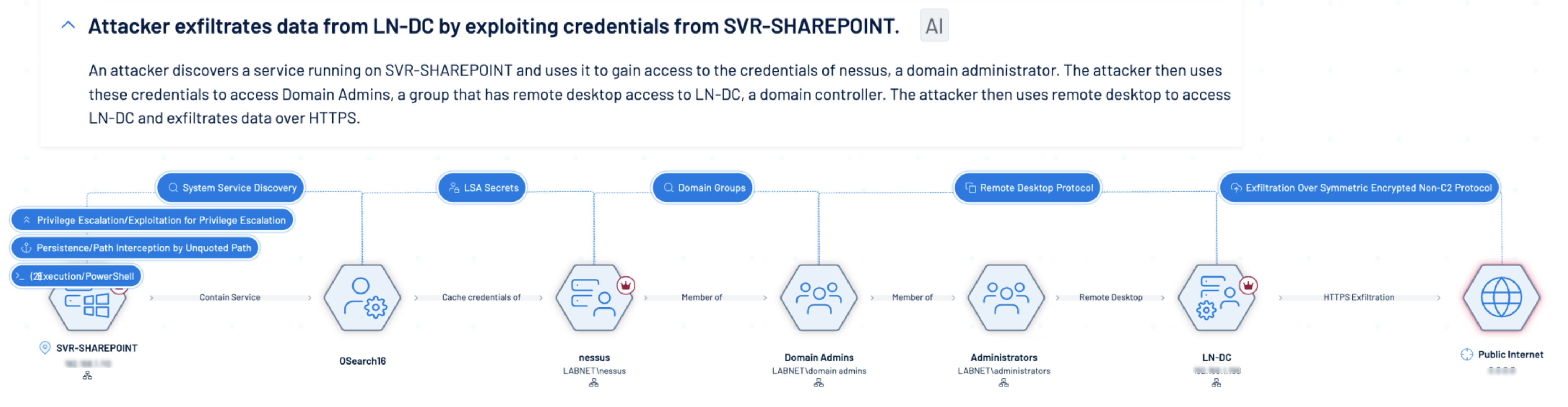
For example, security teams can see human identities with high privileges that, if compromised due to poor password quality, can allow attackers to breach a highly-privileged identity. Similarly, they can identify where air-gapped networks may have been connected to the internet, with open, unrestricted ports, giving attackers a means to ultimately traverse the network and compromise critical OT assets. Equally important, Tenable One allows practitioners to automatically identify choke points, which allow prioritized remediation of the most critical risks that will have the biggest impact on reducing overall exposure.
Choke Point Prioritization
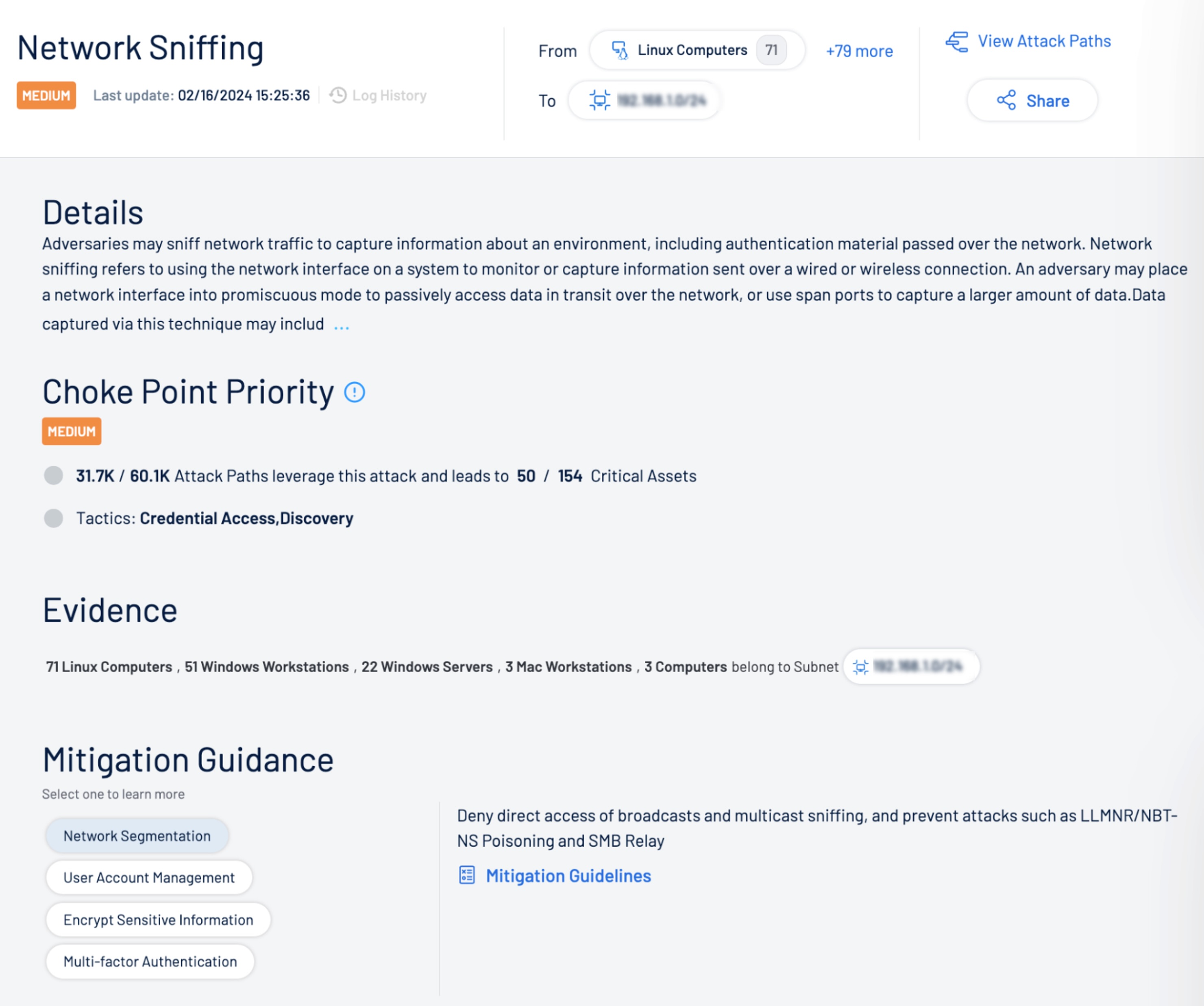
By arming security personnel with a prioritized view of asset exposure with business context, associated attack paths and choke points, and detailed remediation steps and workflow integrations, Tenable One reduces noise while measurably reducing business exposure.
Schedule a free consultation and demo
Want to see what Tenable One for OT/IoT can do for your organization? Schedule a free consultation to receive a quick technical demo and to discuss how we can help improve your security program and results.
For more information about Tenable One for OT/IoT, visit tenable.com/products/tenable-one or sign up for our upcoming webinar “The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT, OT and IoT Environments” for an expert deep dive on topics explored in this post.
Learn more
- The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT, OT and IoT Environments (webinar)
- How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform (blog)
- Tenable Introduces Groundbreaking Visibility Across IT, OT and IoT Domains to Fully Illuminate Attack Vectors and Risks (press release)
- What Is VPR and How Is It Different from CVSS? (blog post)

Jeff Rotberg
In his role as Director of Business Development at Tenable, Jeff Rotberg leads partnerships and strategy for Tenable OT Security. Jeff has over 10 years of experience working in industrial automation and OT environments. Previously, he held multiple sales and technology roles at Rockwell Automation, a leading industrial automation original equipment manufacturer (OEM). Jeff holds a bachelor of science in electrical engineering from UNC Charlotte.
如有侵权请联系:admin#unsafe.sh