2024-3-7 22:46:9 Author: cyble.com(查看原文) 阅读量:27 收藏
Key Takeaways
- In India, there has been a noticeable surge in pig-butchering scam, specifically aimed at investors and propagated through counterfeit trading applications.
- Counterfeit trading applications are being distributed via the Google Play Store and App Store, alongside phishing sites, as part of this fraudulent scheme.
- Scammers were detected utilizing compromised developer accounts to disseminate these fraudulent applications.
- Fabricated articles have been observed across multiple news outlets, falsely asserting a strategic collaboration with BlackRock and the creation of a counterfeit trading platform in India, adding more legitimacy to their scam.
- To lend an air of credibility to their operations, scammers are adopting the identities of reputable Indian brokerage firms.
- The pig-butchering scam extends beyond India, targeting countries like Taiwan and Korea, indicating its widespread nature.
- Cybercriminals based in China are often behind these scams, as evidenced by language references in source codes and arrests made by Indian authorities.
Overview
In the ever-evolving landscape of financial markets, the emergence of digital platforms has provided individuals worldwide with unprecedented access to trading opportunities. However, with this accessibility comes the looming threat of exploitation by cyber criminals seeking to deceive unsuspecting traders. Recently, a troubling trend has surfaced in India, where nefarious elements are exploiting investors’ trust through fraudulent piggybacking on the reputation of renowned brokering applications.
These scammers orchestrate an elaborate scheme, deploying fake Android and iOS applications impersonating legitimate trading platforms. With promises of lucrative returns, they lure victims into investing their hard-earned money, only to abscond with their funds, leaving devastation in their wake.
The pig-butchering scam originated in China in 2020 and later spread to several other Asian countries, and has become widely recognized. Scammers have utilized dating apps and social media platforms to identify their victims and establish romantic or friendly connections with potential victims, gradually earning their trust before convincing them to invest in fraudulent cryptocurrency and trading schemes. According to the most recent Bloomberg report, the pig-butchering scam has resulted in the global theft of over $75 million between 2020 and 2024.
Rise in Pig-butchering Scam Apps In India
Recently, Cyble Research and Intelligence Labs (CRIL) has noticed a significant increase in pig-butchering scams targeting individuals in India who seek to profit from investing in the stock market. These scammers are utilizing social media platforms such as Facebook and Instagram to disseminate advertisements promising high returns in the stock market. Furthermore, they have been observed distributing fraudulent applications through platforms like the Google Play Store and App Store. Some counterfeit apps even impersonate reputable Indian brokers to lend an air of legitimacy to their schemes.
The below figure shows the complete activity of this scam:

Figure 1 – Pig-butchering scam activity
As depicted in the aforementioned scenario, the scam commences with an enticing advertisement on social media platforms. Subsequently, users are encouraged to join WhatsApp or Telegram groups to receive recommendations on high-performing stocks promising good returns. According to complaints from several victims, scammers initially provide recommendations on favorable stocks, assisting victims in making profits with minimal investments. However, they later introduce their fraudulent trading applications to victims, urging them to increase their investment amounts by showcasing high returns on their platforms. After significant investments are made, victims encounter difficulties withdrawing funds from the fake application, and communication with the scammers ceases. Furthermore, the scammers take down the website and the application, leaving victims unable to retrieve their investments.

Figure 2 – Pig-butchering scam post on Reddit
During our investigation, we discovered counterfeit trading applications being distributed through both the Google Play Store and the App Store. We immediately reported these applications to the Play Store (At the time of writing the blog, a few applications had been removed, and some were still active). Figure 3 illustrates the presence of fake trading applications like LMT or FIS-SS, published under the developer ID “Design Tunnel Tech.” It was apparent that this developer ID had been compromised, as evidenced by the existence of older applications dating back one or two years that were designed for different purposes and not associated with the scam.

Figure 3 – Fake trading applications distributed via a compromised account
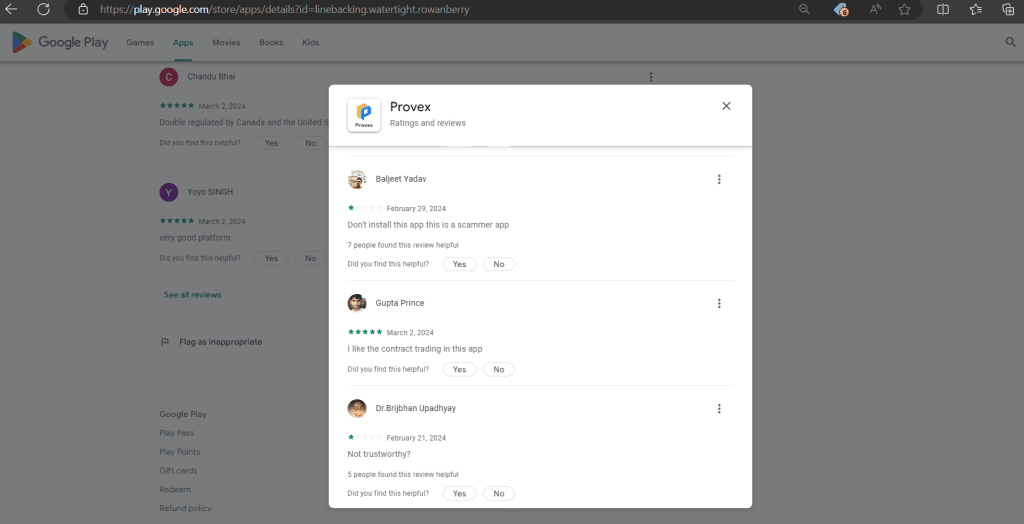
It’s worth mentioning that scammers were observed utilizing identical email IDs, such as alimansoorlahore@gmail[.]com and franciscobenjamimluis28@gmail[.]com, within the support sections of fake applications across various developer accounts. One such fake trading application, “Provex,” is currently being distributed via the Play Store and has garnered over 1,000 downloads with a rating of 4.1.

Figure 4 – Fake trading application named “Provex”
Additionally, the scammer has provided details about the developer, who is purportedly from China. Numerous users have commented in the review section of the application, expressing concerns about its fraudulent nature and labeling it as a scam.

Figure 5 – User’s review on Fake trading application “Provex”
The same application was also available on the App Store.

Figure 6 – Fake trading application “Provex” on Play Store
Notably, we observed an instance where the same application, bearing the same package name, had been previously published under a different developer ID, “Xilli Apps Studio.” This particular account was also found to host multiple pig-butchering scam applications, as illustrated in Figure 8 below.

Figure 7 – Provex application published on the different developer account

Figure 8 – More scam applications on Play Store
We’ve identified the website “hxxps://provexfintech[.]com” linked to the Provex trading platform. Scammers have developed a meticulously designed website featuring product and service descriptions, features, and an “about us” section. Additionally, the website includes links to mobile applications that redirect users to the same fraudulent application hosted on both the Play Store and App Store.

Figure 9 – Fraudulent website of Provex trading platform
The deceptive Provex platform portrays itself as a fresh Fintech Platform dedicated to secure trading. Furthermore, the scammers have been observed publishing fabricated news articles claiming a strategic partnership with BlackRock to establish a trading platform in India. We’ve noticed identical write-ups on legitimate news publisher websites, suggesting that the scammers have published these articles to legitimize their scam.

Figure 10 – Fake news article on partnership with BlackRock

Figure 11 – The same article related to the partnership with Blackrock was published on another news website
The fake Provex application was released on the Play Store on February 7, 2024, and on the App Store on February 16, 2024. Before this, several Provex apps titled “Provex Max” and “Provex PRO” were published on the App Store. These Provex variant applications were removed from the Play Store.

Figure 12 – Another Provex application on the App Store
These deceptive apps utilize a WebView to load a scam website, urging users to either login or register to begin investing and trading. The Provex apps load the URL “hxxps://www[.]protbg.com” into the WebView, redirecting users to a login page. Users need an invitation code to register for the application, which the scammer will share once they identify the potential victim.

Figure 13 – Login and registration page of fake trading application
The invitation code may be shared either through an invite link with the victim or directly via communication through a WhatsApp group. The figure below shows the invitation link for a similar application shared with the victim.

Figure 14 – Invitation link shared by the scammer
Moreover, we have uncovered compromised YouTube channels endorsing similar trading scam applications by including the invitation link in their video titles. This campaign consistently uploaded videos throughout 2023; however, we have not discovered any recent videos on YouTube promoting this scam.

Figure 15 – YouTube videos promoting scam
As previously stated, scammers have recently begun impersonating well-known brokerage applications in India to lend legitimacy to their scams. We have identified several phishing sites distributing counterfeit trading applications impersonating Indian brokers. Below is a list of these phishing sites.
- hxxps://downs[.]fcsdmp.top
- hxxps://downs[.]fxdxp.top
- hxxps://downs[.]fxdst.top
Below are the applications impersonating Indian brokers.

Figure 16 – Fake applications impersonating Indian Brokers
All of these fraudulent applications operate similarly, loading scam websites in their WebView components, prompting users to either log in or register. To register, users are required to enter an invitation code, mirroring the process seen in the “Provex” application.

Figure 17 – Login and registration page of fake trading app impersonating Indian broker
After users complete registration and log in to the fake application, they encounter a simulated trading environment. Scammers then urge victims to deposit funds and initiate trades. As victims begin trading, they may receive promising returns, prompting them to invest more. Once the scammer obtains a significant amount, they disable the withdrawal function and cease communication with the victim.

Figure 18 – Fake trading setup in a fraudulent trading app
Pig-butchering scam targeting Korea and Taiwan
The scam is not confined to targeting individuals solely in India. We have discovered several applications employing similar tactics to target other countries, such as Taiwan and Korea. This indicates the extensive reach and network of this scam.

Figure 19 – Similar login and registration pages of fake apps in Korean and Chinese language
China-based Cyber Criminal Operating Pig-butchering scam
Initially, the pig-butchering scam focused on individuals in China, with cybercriminals from China leading the operation. However, the scam later expanded globally, involving individuals from various countries in luring potential victims.
Recently, according to a report, Indian police have apprehended 18 individuals involved in the pig-butchering scam, who were found to be associated with cybercriminals based in China. Additionally, another arrest related to the pig-butchering scam has been made in India, involving a Chinese national who illegally entered the country. The accused was found in possession of over 500 SIM cards purchased using forged identities of Indian nationals.
Moreover, we have discovered Chinese language references within the source code of phishing sites and in the Android and iOS applications. These strings were employed in logs and comments. Furthermore, the admin panel of the scam website was also designed in Chinese language.

Figure 20 – Chinese strings present in the source code of the phishing website

Figure 21 – Chinese string present in the source code of the Android application
Telegram Task Scam Following Similar Modus Operandi
Recently, there has been a surge in reports of the Telegram Task scam across multiple countries. This scam has gained momentum by offering secondary income or part-time job opportunities. It has attracted numerous individuals with promises of easy tasks and good money in return.
The scam begins with scammers contacting victims through SMS, WhatsApp messages, or Telegram, presenting enticing part-time job offers. Upon expressing interest, victims are added to Telegram channels, boasting hundreds of participants, many of whom are actually scammers posting positive responses to build trust.
Initially, the scammer assigns simple tasks such as liking YouTube videos, visiting websites, or providing reviews. Victims are paid a small amount upon completion to entice them further into the scam. The figure below illustrates examples of task posts within one of these fraudulent Telegram channels.

Figure 22 – Post related to the task on the Telegram channel
As depicted in the image above, one of the tasks involves the victim making a payment to a merchant with the promise of receiving a return of 30 – 40%. Despite initial skepticism, after gaining some profit, the victim may decide to invest a small amount and, indeed, receive the claimed profit. This process continues, with the victim gradually increasing their investment and receiving profits.
As trust in the scam platform builds, the scammer may suggest investing larger amounts. At this stage, they introduce an online fake crypto platform reminiscent of the pig-butchering scam. Victims may end up depositing significant sums of money, as shown in the figure below.

Figure 23 – Fake crypto platform involved in Telegram scam
The victim can view the transaction history detailing the amounts invested, cryptocurrency purchases, and profits earned, as illustrated in the figure below.

Figure 24 – Transaction details on a fake crypto platform
When attempting to withdraw money, the victim may reach out to the scammer. At this juncture, the scammer introduces the victim to the “Credit Score” feature (Figure 23). The victim is informed that they can only withdraw money once their Credit Score reaches one hundred. To achieve this, the victim is prompted to deposit more money.
The scammer implements this step to exploit the victim’s fear of losing money. Having already invested a substantial amount, the victim may deposit more in an attempt to recoup their losses. However, this time, the scammer refuses to return the money, resulting in financial loss for the victim.
This scam employs a similar tactic to the pig-butchering scheme, initially gaining the victim’s trust by providing small profits before introducing the fake crypto platform.
Conclusion
The rise of fraudulent schemes like the pig-butchering scam and the Telegram Task scam underscores the grave risks individuals face in the ever-evolving financial landscape. Enticed by promises of easy money and lucrative returns, victims often find themselves trapped in elaborate webs of deception orchestrated by malicious actors.
The impact on victims is profound, extending far beyond mere financial loss. Many suffer emotional distress, shattered trust, and a sense of betrayal. Falling victim to these scams undermines financial security and erodes confidence in digital platforms and investment opportunities.
The allure of quick wealth, coupled with clever manipulation tactics employed by scammers, often blinds victims to red flags and warning signs. Desperate for financial stability or enticed by the prospect of easy money, individuals may overlook the glaring inconsistencies and dubious promises presented to them.
Ultimately, combating these scams requires heightened awareness, vigilance, and education. By understanding the modus operandi of such schemes and exercising caution, individuals can better protect themselves from falling prey to financial predators in the digital age.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Before investing in any platform or participating in a job opportunity, thoroughly research the company or organization. Look for reviews, check their website and social media presence, and verify their legitimacy.
- Be cautious of unsolicited messages or advertisements promising high returns with minimal effort. Scammers often reach out via SMS, WhatsApp, or social media, enticing individuals with too-good-to-be-true opportunities.
- Stick to reputable and well-established trading platforms, brokers, and job portals. Research the platform’s reputation, security measures, and user reviews before engaging with them
- Before installing any software from official app stores such as the Play Store or the iOS App Store, check reviews and the download count of the applications.
- Using a reputed antivirus and internet security software package is recommended on connected devices, including PCs, laptops, and mobile.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Be careful while opening links received via SMS or emails sent to your mobile device.
- Google Play Protect should always be enabled on Android devices.
- Stay updated on common scam tactics and emerging trends in fraudulent activities
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| faf7a001250ef1dbd2d6eaf8eabbd8d589c0960e871325808a7a1a76619c4b4f 87196e5cda572d63c43d52df200e823a9811e33a ecce84056298bc3bcc8c17d6ed12a29b | SHA256 SHA1 MD5 | Fake trading application |
| app[.]panth-ss[.]vip | Domain | Scam website |
| 0a2fffb84d58dbf3cb2a50fd15d3cda9b3998c85c0424e29bf0964cc6bbda920 2288add2292e026cb32933943d2c9f105e57ed8d a522af373e24042e4b1995a186cfed6a | SHA256 SHA1 MD5 | Fake trading application |
| app[.]yongljt[.]com | Domain | Scam website |
| 52c36d2e1c5df64b96e017625fdd2d1c07e2a0b741c155735d09c068b23d54ad 53c40428b48050ecd851f58b020629f58b6bd18f e1b935f23c49ac0b1176c3b650e5bc12 | SHA256 SHA1 MD5 | Fake Trading application |
| hxxps://www[.]inueyd[.]com/?v=3 | Domain | Scam website |
| Giottusmh[.]com giottusmk[.]com | Domain | Domain involved in Telegram task scam |
| 34.131.1[.]213 | IP | IP hosting multiple scam domains involved in Telegram task scam |
Related
如有侵权请联系:admin#unsafe.sh