
An open internet is a cornerstone of civil society, underpinning access to informati 2024-3-2 00:12:58 Author: www.bellingcat.com(查看原文) 阅读量:20 收藏
An open internet is a cornerstone of civil society, underpinning access to information in peacetime but even more so in times of conflict and under repressive regimes, according to leading experts.
Following Russia’s full-scale invasion of Ukraine in early 2022, over 50 digital and human rights groups including Access Now, the Committee to Protect Journalists, and Human Rights Watch jointly explained in a letter to the US Government that restrictions on the internet to Russia or Belarus could “hurt individuals attempting to organise in opposition to the war, report openly and honestly on events in Russia, and access information about what is happening in Ukraine and abroad,” adding such measures could “also unnecessarily facilitate further repression by the Russian government.”
This is why telecommunications services are often treated differently than other sectors of the economy when it comes to global sanctions, and why the United States made internet services exempt from its sanctions against Russia over the war. That has not stopped major internet service providers from electing to cut services to Russia, or measures from Moscow limiting access to social media including Facebook, Instagram and X.
And while the right to a free and open internet is not in doubt, an analysis of over a thousand companies and organisations connected to European internet service providers (ISPs) by Dutch outlet Investico and Bellingcat reveals that some sanctioned entities are able to exploit the free flow of the world wide web. For example, five major Russian banks sanctioned by the EU appear to have a business agreement with British internet service provider RETN.
Experts told Investico, and media partners Trouw and De Groene Amsterdammer, that economic sanctions on the internet are “a very complicated question.” After the Russian invasion of Ukraine, RIPE, the centralised internet registry for Europe and Central Asia, was pressured by Ukrainian politicians to revoke Russian internet registrations. Ultimately, RIPE received guidance from Dutch authorities that internet resource registration was exempted from sanctions, and maintained an “apolitical” policy.
In an interview with Investico, University of Amsterdam internet researcher Dr Niels ten Oever said that he was initially critical of telecommunication exemptions for RIPE. “But the risk is that if we intervene in RIPE, we intervene in the basic conditions of communication networks. And that means we encourage fragmentation. China could design its own system, so there would be a Chinese and a European internet.” However, the lack of clarity on sanctions has led to ISPs, data centres, and other internet actors choosing their own interpretation. And this instability itself poses risks to the ideal of the global Internet.
Some, but not all, of these questions can be explored with open data. In this guide, Bellingcat will show you how we used open tools to explore Sberbank, one of ten sanctioned Russian banks banned from the international SWIFT banking system. You can read Investico’s full investigation here.
To understand how open source tools allow investigators to discover these connections, we first need to have a clear definition of the Internet. While networks, the web, an internet, or the Internet (with a capital I) are often used interchangeably, they refer to distinct things.
Computer networks existed before the Internet. What the Internet created was a framework for these separate computer networks to talk to each other as a network of networks. A single company’s computer network is referred to as an Autonomous System, or AS, registered with a unique number. They are autonomous in the sense that it is a self-contained, independent network. To form an internet, this AS must be connected to other ASes.
If every AS could only exchange data with the ASes it was directly connected with, the Internet wouldn’t reach very far. Instead, these connections are publicised using the Border Gateway Protocol, or BGP. There is no centralised switchboard for internet traffic. Instead, BGP allows networks to advertise the routes that they offer to reach other networks, and data centre switches route traffic accordingly. There are many online resources for collecting, processing and visualizing this routing information to make sense of the internet: BGP Tools is one.
So-called “tier 1 ISPs” form the backbone of the Internet. These ISPs are those that have a reach global enough to allow them to send and receive data from any internet connected computer without paying another network operator for the privilege. Smaller networks generally do not lay hundreds of thousands of kilometres of their own fibre optic cables and are not capable of this. Generally, they will pay to “transit” their traffic — either by contracting with a Tier 1 ISP directly or by going through a transit network, such as RETN.
From a technical perspective, every “peering” relationship is equivalent. Two networks either allow bits to move back and forth, or they don’t. But from an economic point of view, there are different types of relationships. The simplest is known as “settlement-free peering,” where no money is exchanged. For example, two small ISPs might agree to peer directly with each other without financial exchange, so that customers of ISP A can network with customers of ISP B and vice versa. Most often, however, a small network will pay to transit data through another network to reach a Tier 1 ISP so that their computers or customers can reach the global network. However, since these relationships are identical from a technical perspective, there is no direct way to identify these economic relationships.
Websites like BGP Tools attempt to determine these relationships by looking at the overall structure of the network. BGP Tools consider any network between a network and a Tier 1 ISP to be a relationship where the peering is not settlement-free (or in other words, where a business relationship exists.)
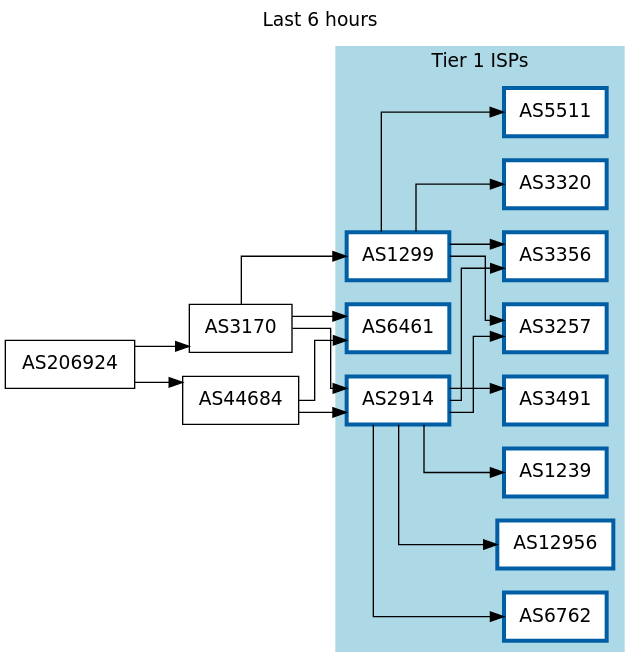
For example, in the image above, traffic from network AS206924 must flow to AS3170 or AS44684 before it reaches a Tier 1 ISP. Since these intermediary networks would have no reason to provide free transit to AS206924, this implies that they are being paid to provide connectivity between the Tier 1s and AS206924. BGP Tools calls these “upstream” peers of AS206924 (or, vice versa, AS206924 is a downstream network of AS3170 and AS44684.)
It is also important to note that these connections only represent flows for traffic inbound to a network, i.e., the route that data would take from a Tier 1 ISP to AS206924. Outbound traffic could follow different paths.
With that out of the way, we can use BGP Tools to look at a network and see how it is connected to the broader Internet. Let’s examine Sberbank, a Russian bank that has been sanctioned by the EU, UK and US since 2022.
A search for Sberbank on BGP Tools reveals that they have several ASes (networks).
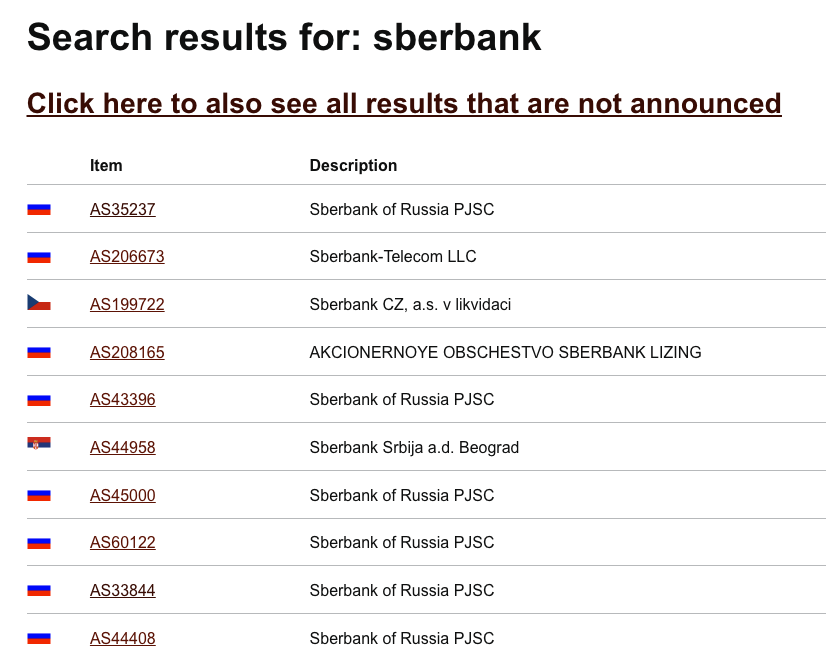
Most are registered in Russia (more on registration later), but we can also see a Czech registration for Sberbank CZ and a Serbian registration for Sberbank Srbija. Both international branches are now defunct.
Search results are generally sorted by size so let us examine the first one, AS35237.
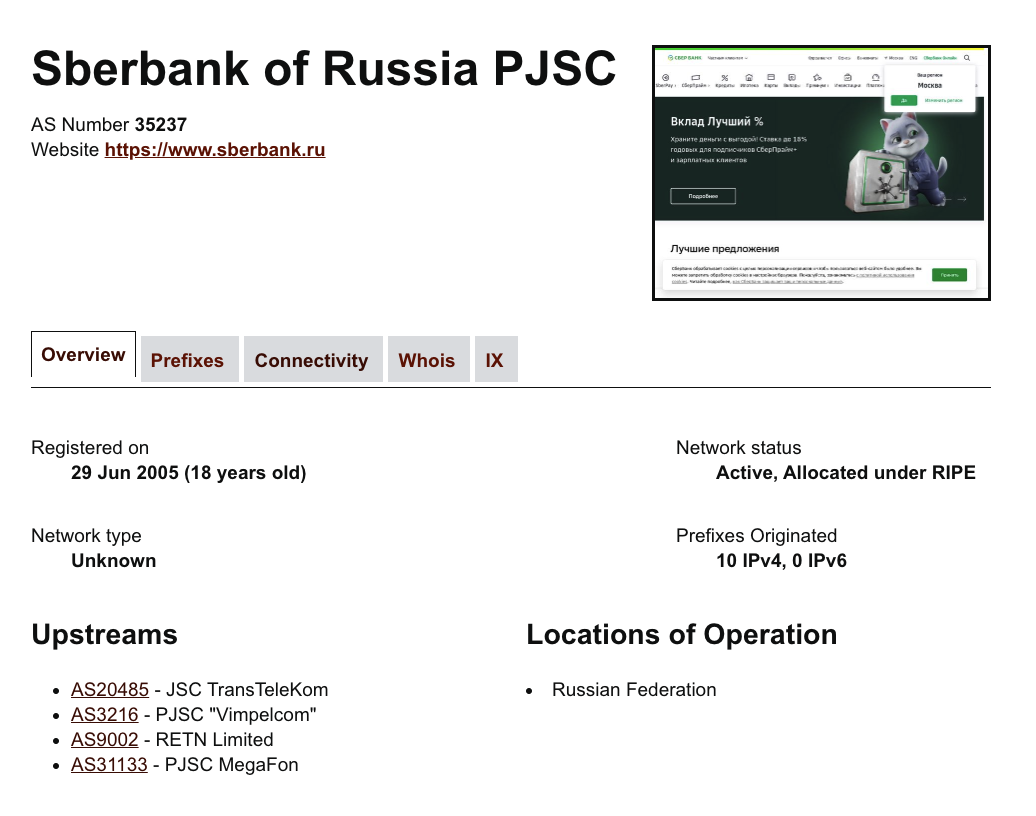
This network has four upstreams according to BGP Tools. On the connectivity page, a graph can be seen that visually represents these connections towards Tier 1 ISPs. Note that for larger networks the “Global Aggregation” view might not be visible – instead, many different graphs represent possible routes for traffic flow.
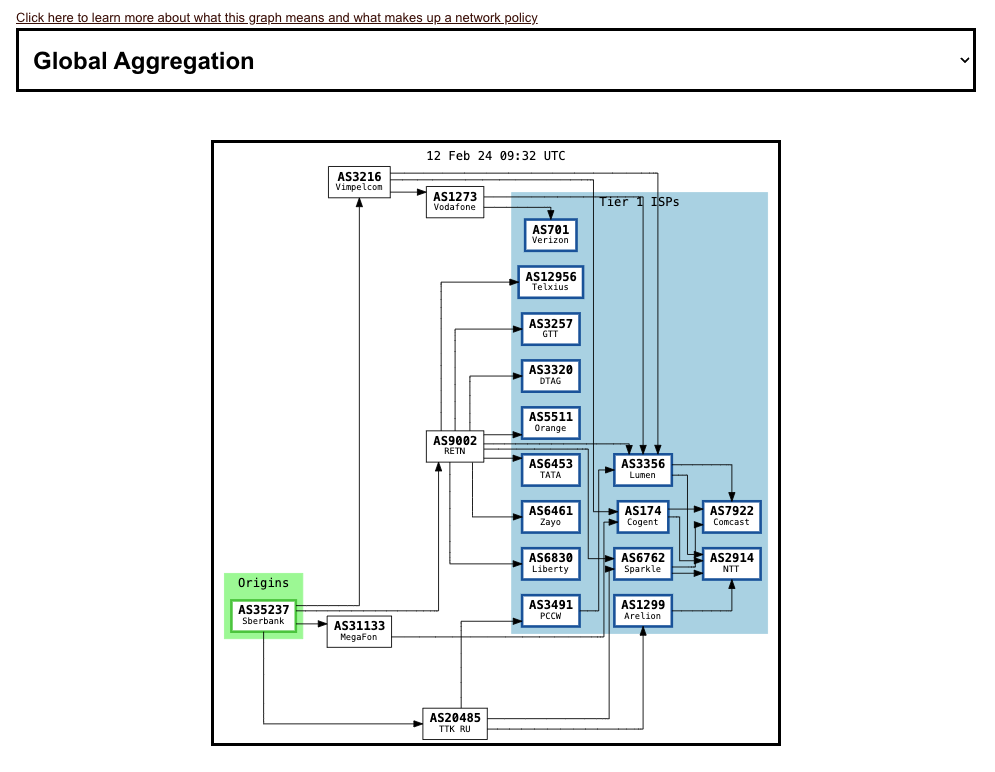
With this graph, we can see the paths that traffic flows from Tier 1 ISPs to Sberbank. To reach Telxius, GTT, DTAG, Orange, TATA, or Zayo, traffic flows through RETN, a UK-based network transit provider. Connections to other Tier 1 ISPs flow through Russian ISPs, Vimpelcom, TTK RU and MegaFon.
This implies that Sberbank has a business relationship with RETN and these three Russian ISPs, where Sberbank pays for their traffic to be carried through those networks.
In addition to these four “upstream” networks, there are also many peers listed.
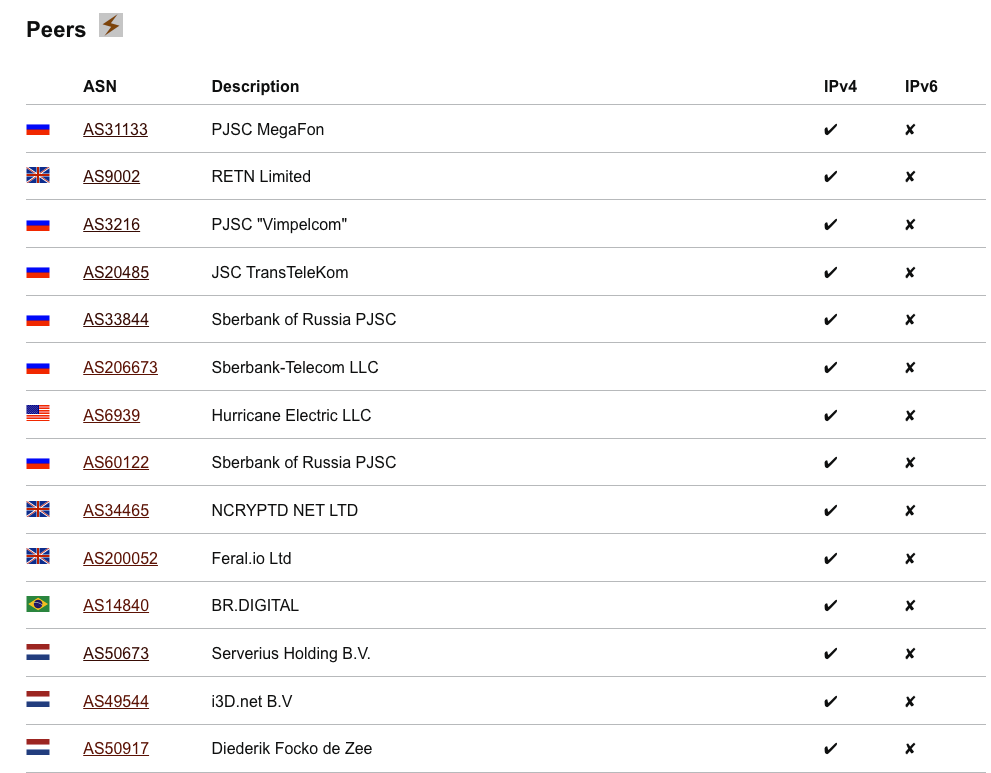
Note that this list includes the upstream connections we looked at previously – every connection is also a peer.
Networks listed here that are not upstreams do not carry traffic from Tier 1 ISPs to Sberbank. This could be settlement-free (unpaid) peering, like in the example of two small ISPs earlier, but this does not necessarily have to be true as these business relationships are not directly visible in the BGP data.
The Dutch entity at the bottom, AS50917, doing business as Backbone Direct, has connectivity prices listed on their website but also has an open peering policy for certain kinds of traffic. Others are almost certainly settlement-free – for instance, Sberbank’s connections to other Sberbank networks, like AS33844 or “Sberbank-Telecom LLC” are likely internal.
Let’s look at an example of a larger network, PJSC Tattelecom, a mid-size ISP serving customers in Russia’s Republic of Tatarstan.
With PJSC Tattelecom, we can see that there is no Global Aggregation graph to view. Instead, there are many different representations of data flows, showing the different possible paths that the AS can be connected to Tier 1 ISPs. Note that the policy names generated by BGP Tools are arbitrary and ephemeral.
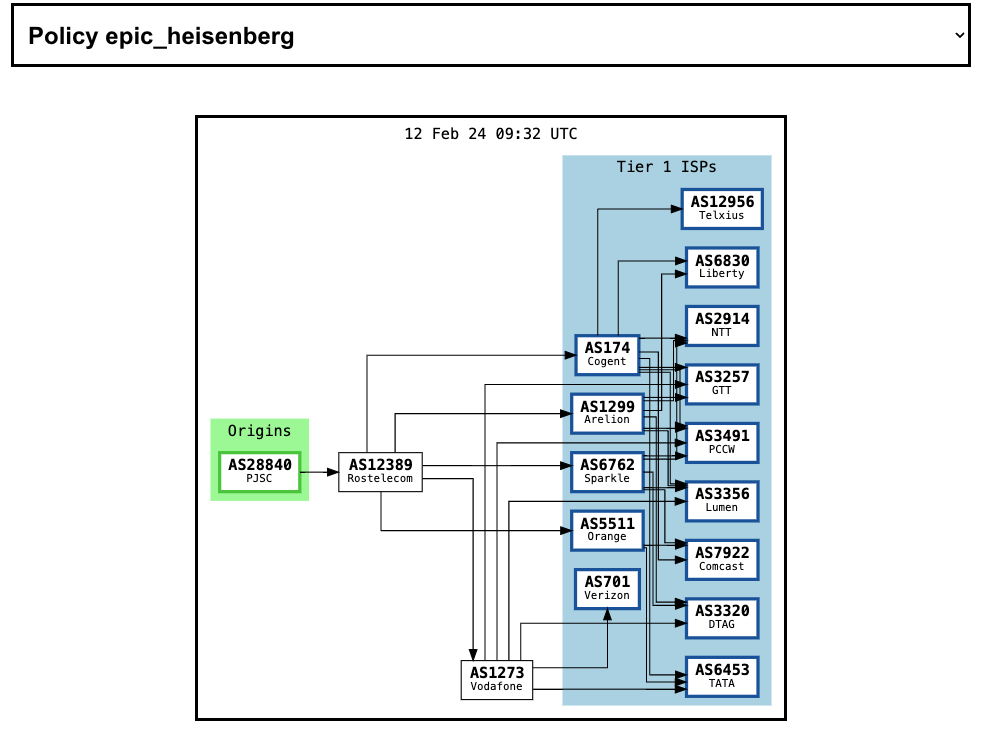
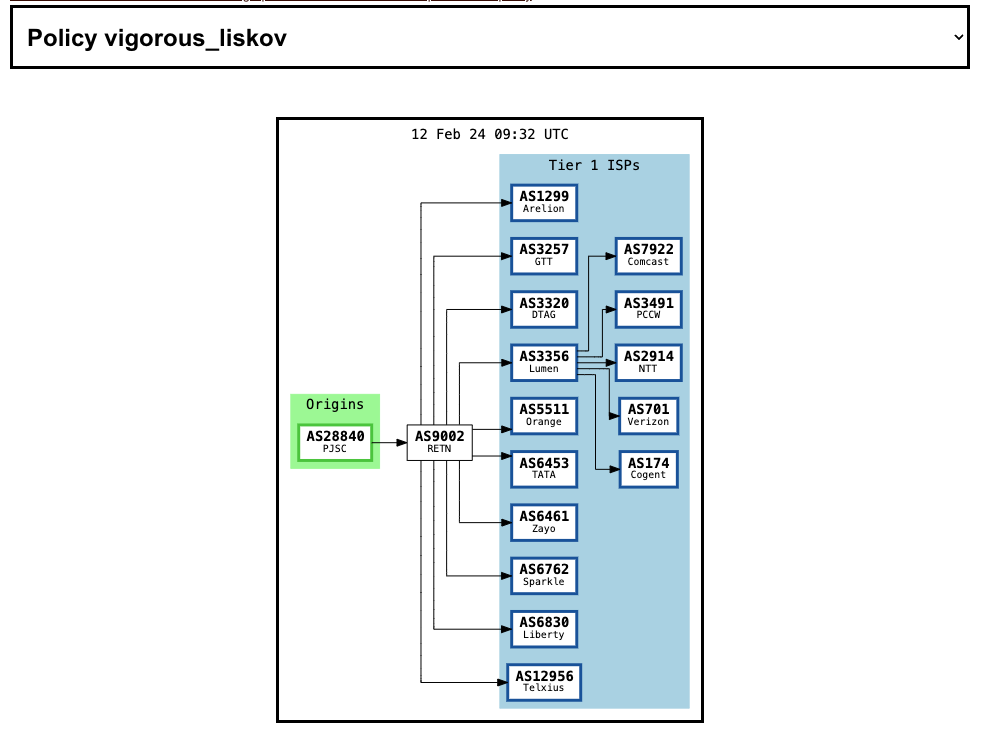
From this information, we can see that traffic to Tier 1 ISPs might flow through several different routes — possibly through Rostelecom as in the left-hand graph, or possibly through RETN as in the right-hand graph.
In the case of an ISP like Tatellecom, these paid connections to Western companies such as RETN allow Russian citizens to access the global Internet, including international news, opinions and information that might be censored or restricted in other forms of local media, like TV and newspapers. For this reason, sanctions regimes applied in the West typically include exemptions for telecommunications. This is a deliberate policy to prevent isolating citizens of autocratic regimes in an information desert, just as exemptions for food are deliberate policies to prevent famine.
This is clear for an ISP, but it becomes murkier when considering a sanctioned bank such as Sberbank. The connection Sberbank has with RETN, rather than with Vimpelcom or its other Russian ISP upstreams, could provide cheaper or more efficient ways to move money over the wires and send data to clients worldwide. Arguably this is an example of economic services being provided by a UK company to a sanctioned Russian one.
This is likely allowed under the telecommunication exemptions in Western sanctions, but the ambiguity creates risks that threaten internet interconnectivity and was identified as a serious problem in several interviews by our investigative partners Investico. Six lawyers whom Investico spoke with have “no idea” whether the exemptions would apply in the case of a sanctioned bank. One that specialises in sanctions law calls it “a complicated question,” and another specialising in telecommunications says it is “open to interpretation” based on whether or not the services are essential. In the absence of clarity on sanctions, companies are choosing their own path. Cogent Communications, an American backbone provider, disconnected many Russian customers in March 2022, while others such as RETN have continued to provide connectivity to Russia.
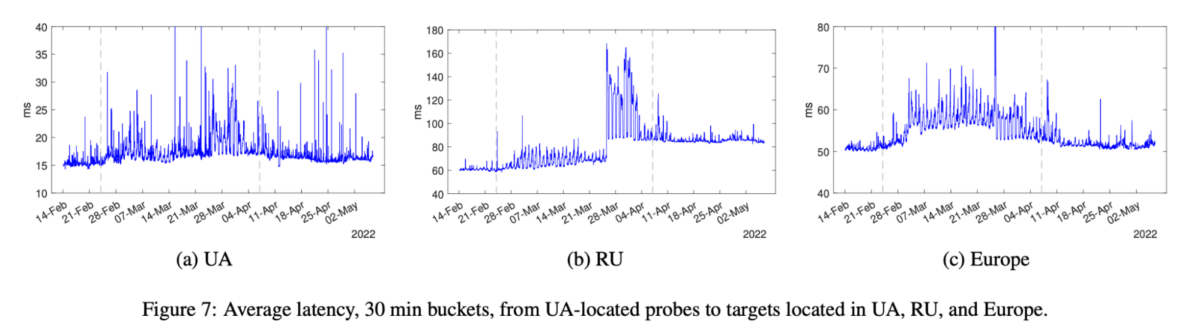
The Internet is designed to be robust, and most networks are connected in such a way that if another network were to go offline or disconnect, traffic could be re-routed via a different path. However, these disconnections could still carry consequences in terms of speed, capacity and cost for networks. For example, research by Roman Khavrona at the University of Twente found that the length of BGP paths in Ukraine grew significantly after the full-scale invasion of Ukraine by Russia. This was due to a combination of factors, including damage to infrastructure and network disconnections. Path length also increased for Russia, albeit more gradually, hypothesised to be due to network disconnections.
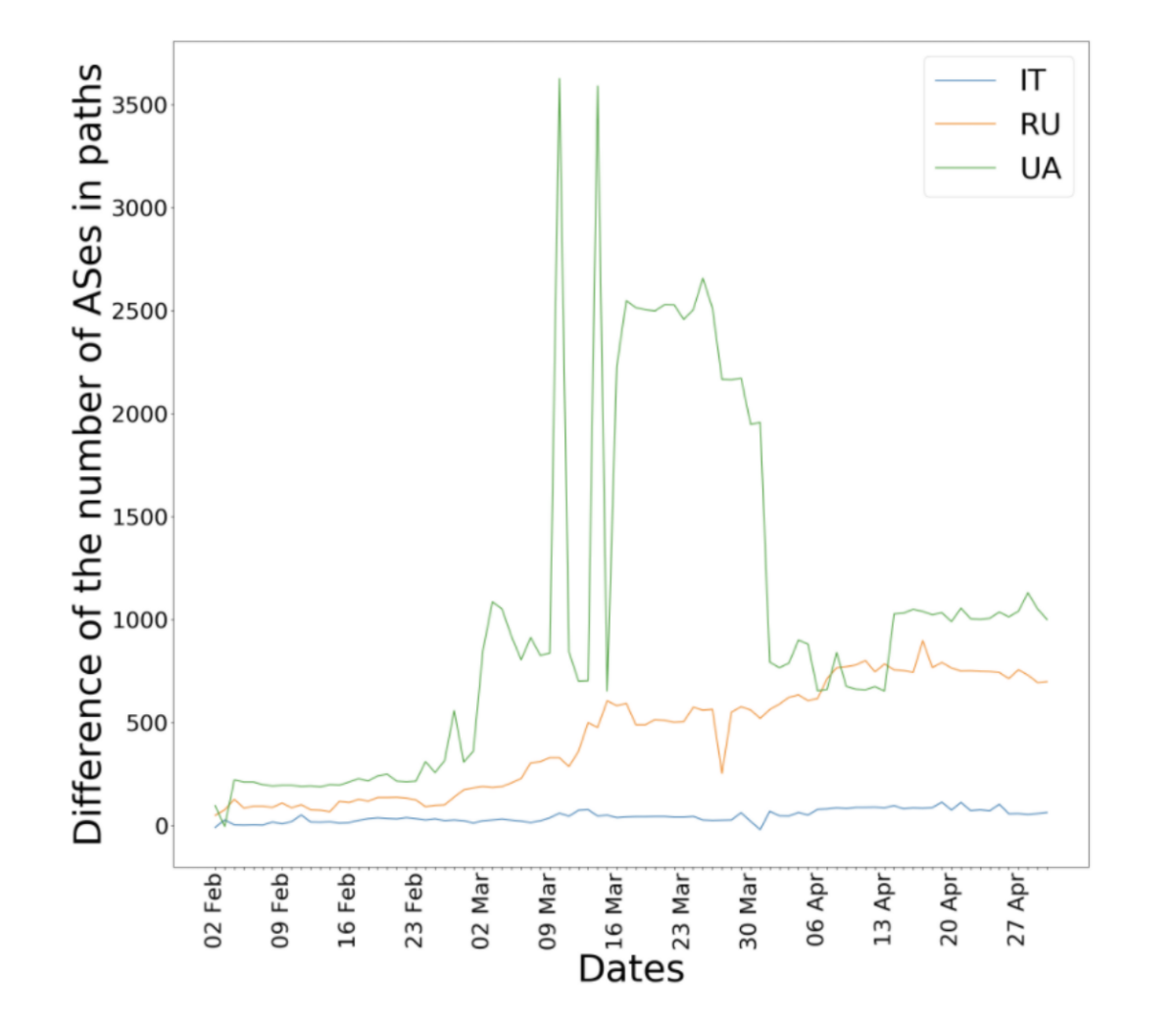
Related research by Valerio Luconi and Alessio Vecchio at the University of Pisa and Italy’s National Research Council found that this had lasting impacts on latency, or the delay for data from one network to reach another network.
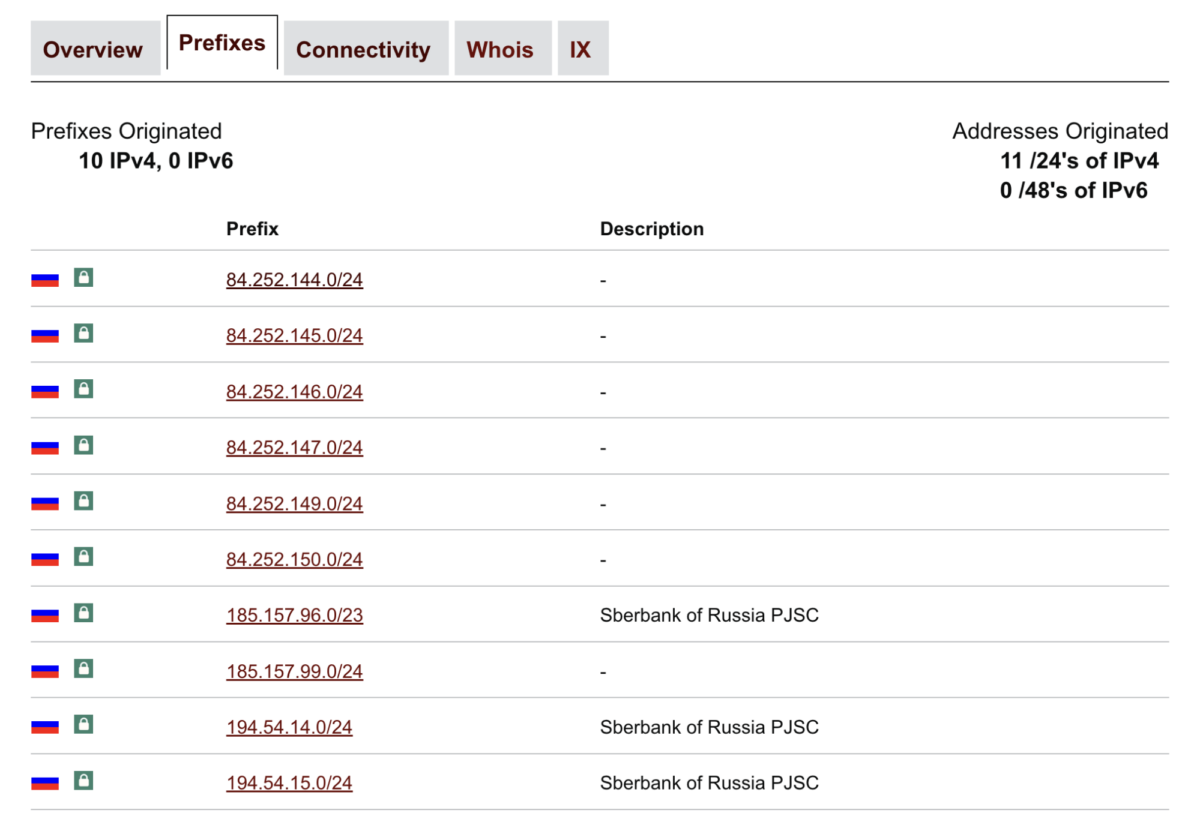
Additionally, BGP Tools can also be convenient for exploring the IP addresses associated with a network. We can examine these by looking at the “prefixes,” or blocks of IP addresses “originated” by an AS.
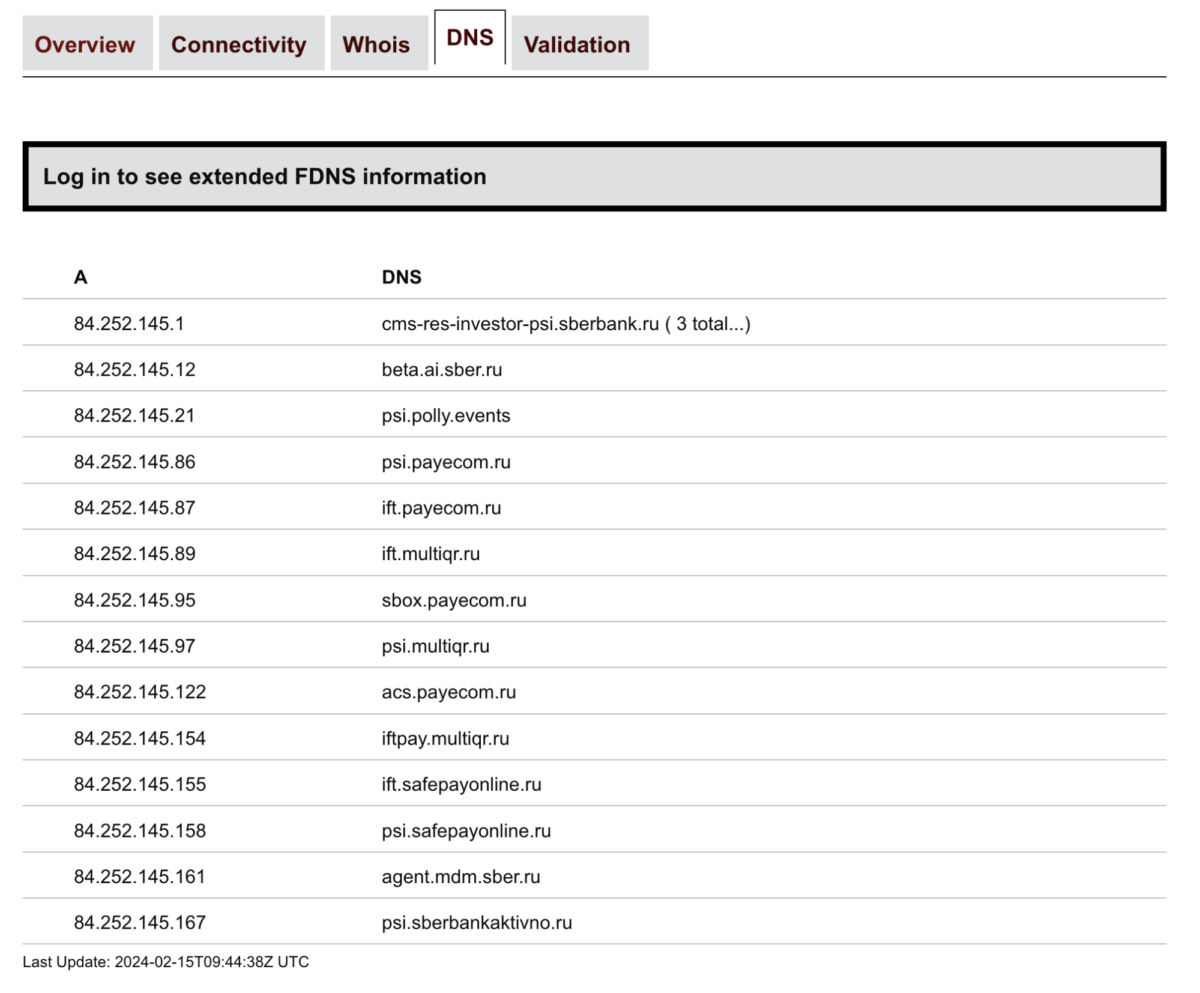
Clicking on the second link, 84.252.145.0/24, takes us to BGP Tools’ page for that prefix. We can see the websites that are served on these IP addresses from this autonomous system by clicking on the “DNS” tab. Here we can see that this block of IP addresses on Sberbank’s network appears to be used for payment processing infrastructure, as well as investor relations.
BGP Tools can be useful for looking at the websites hosted on an autonomous system and how it is connected to other ASes. But how does an AS come to be in the first place, and how does it get space allocated to it for computers and websites?
This happens at the level of Internet registries. There are five Regional Internet Registries, each covering a different part of the globe: AFRINIC (Africa), ARIN (North America except Mexico), APNIC (Oceania to East Asia), LACNIC (Caribbean and Latin America), and RIPE (Europe, including Russia, the Middle East and Central Asia.)
Internet registries allocate AS numbers for the creation of a network, and most importantly allocate IP addresses. IPv4 addresses, the “phone numbers” of the Internet, only number up to 4.3 billion, and are now a scarce resource. RIPE exhausted its supply in 2019, and they are now sold for $40-50 per IP address in the secondary market.
This means that regional Internet registries such as RIPE play a very important role in the Internet. While the connections between autonomous systems are decentralised, the registration of the systems themselves is centralised at the registry, as is the registration of the IP addresses. A server without an IP address cannot be reached and would effectively be disconnected from the Internet.
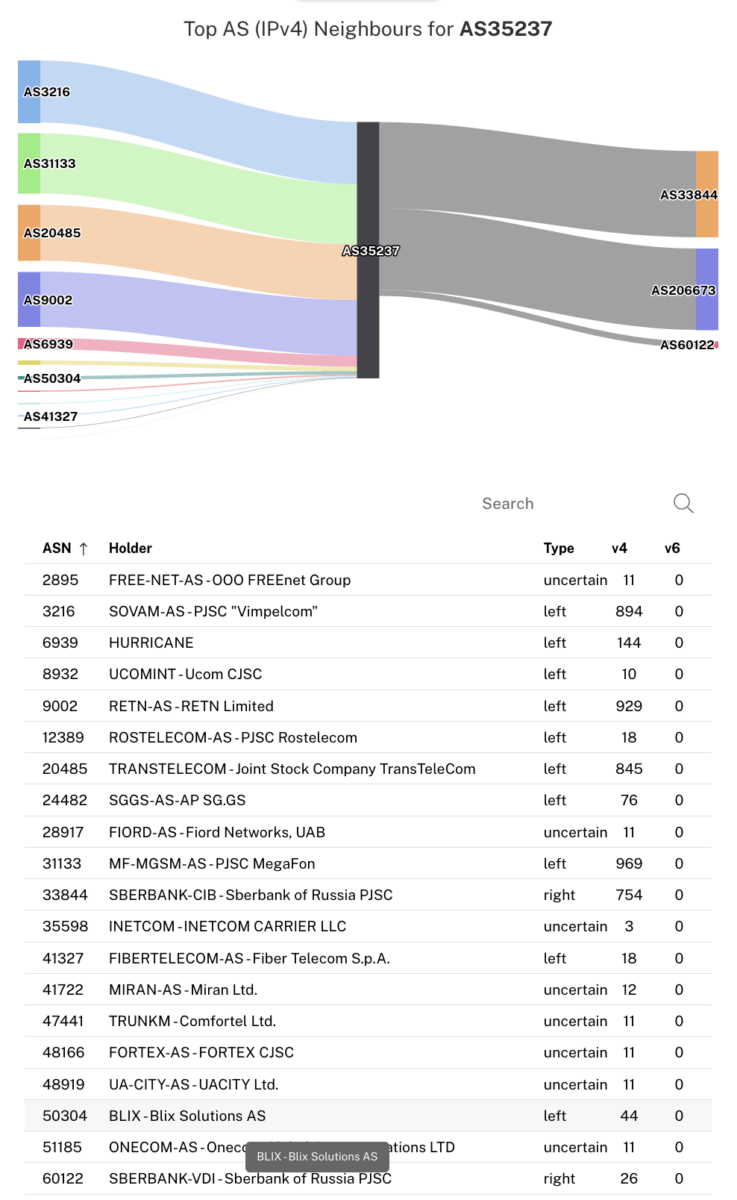
RIPE provides a toolbox called RIPEstat that can be used to dig into networks in more detail. Let’s take a look at AS35237, Sberbank, there. By default, RIPEstat shows the latest data it has for a single point in time.
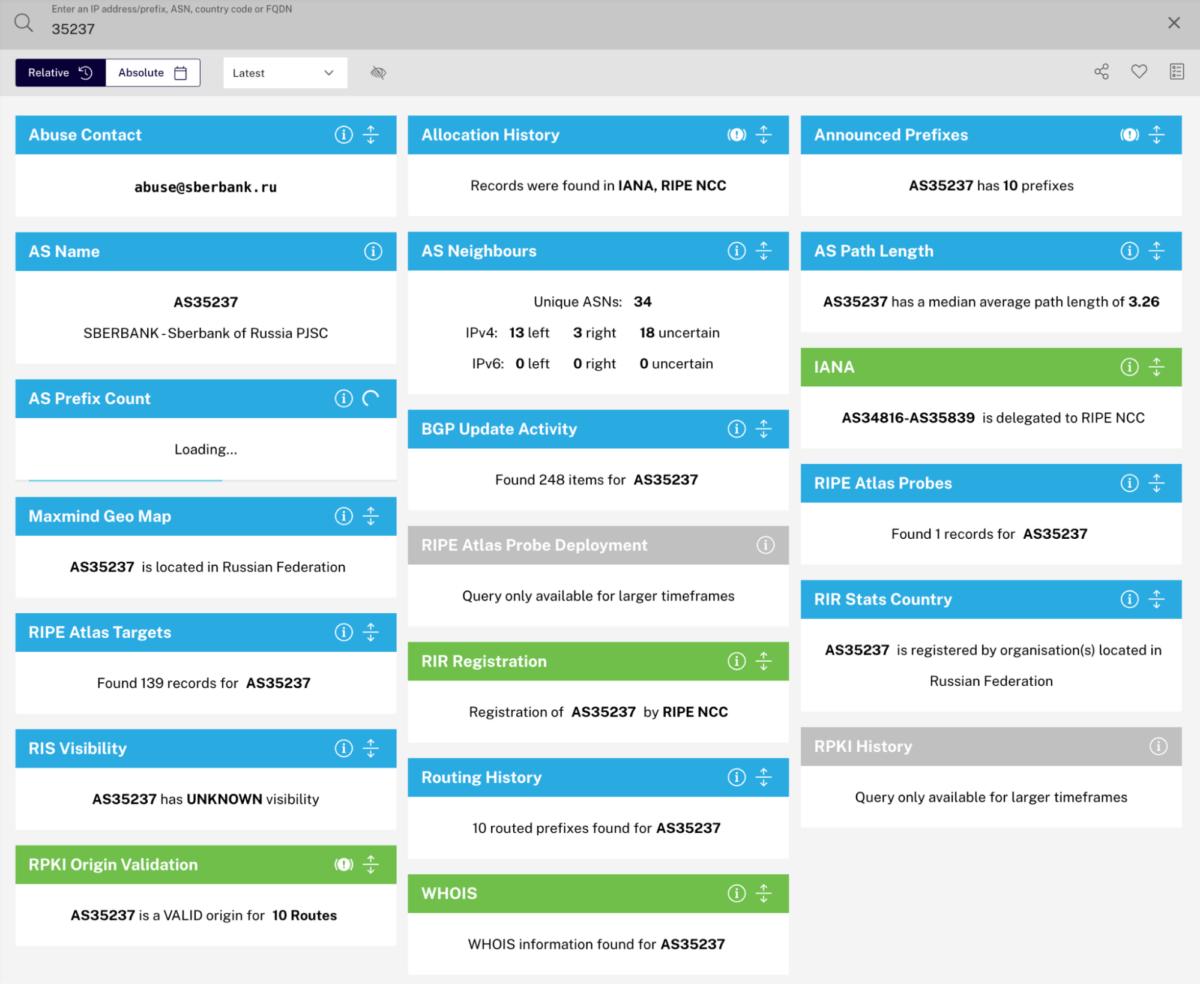
The RIPEstat interface organises pieces of information into panels. One important panel is “AS Neighbours”. Expanding AS Neighbours, we can see similar information to what is provided in BGP tools, but with a few important differences.
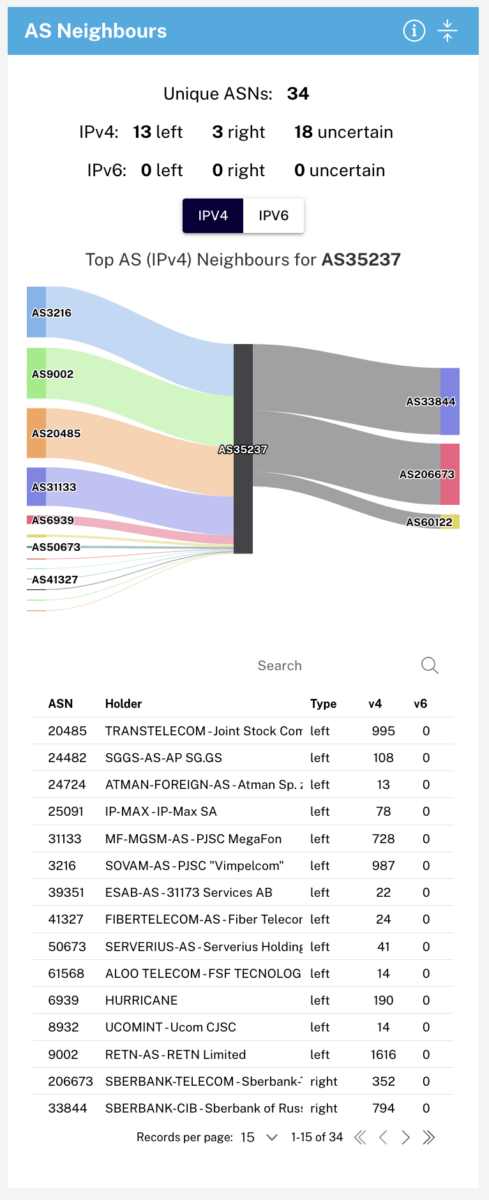
Other networks are classified into “left” or “right” neighbours. Right neighbours are essentially the same thing as what BGP Tools calls “downstreams.” However, left neighbours can refer to both peering and “upstream” connections. The graph also shows the approximate size/importance of the network connection by the total number of routes seen using each AS.
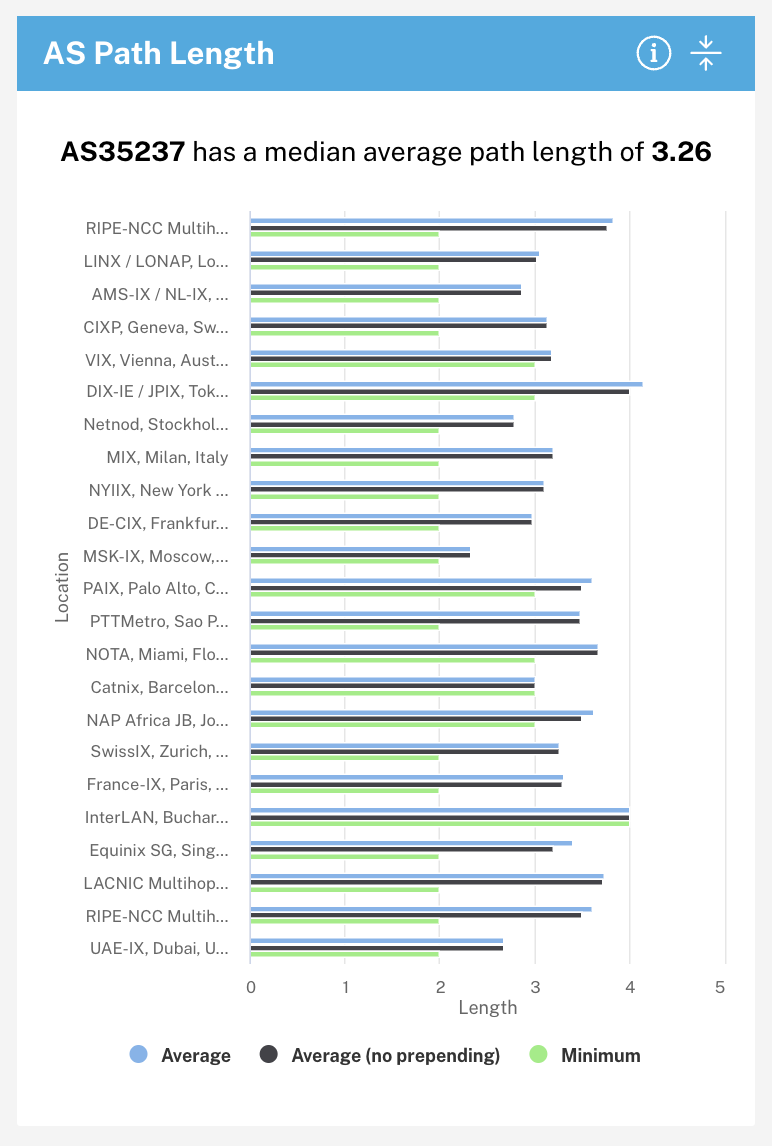
The AS Path Length shows the average number of different networks information must jump through to reach AS35237 from several internet exchange points around the world. In the case of Sberbank’s network, we can see that it is closest to the MSK-IX exchange in Moscow, and furthest from the DIX-IE exchange in Tokyo. As was seen in the case of Ukraine in 2022, disruptions or disconnections in internet infrastructure can cause this length to increase, with consequences for the speed, bandwidth, and reliability of the Internet.
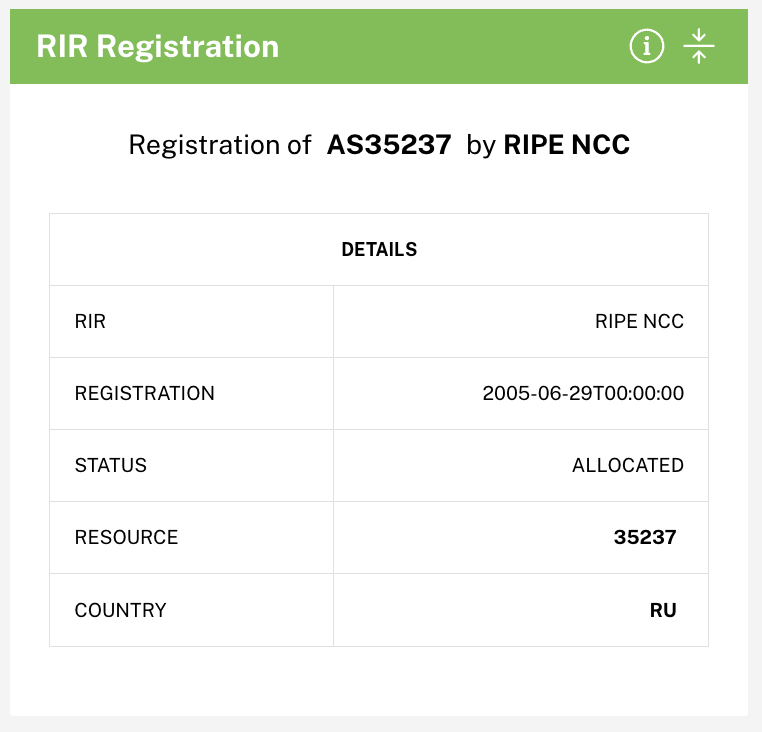
The RIR Registration panel provides basic information about how the network is registered in the RIR database (in this case, in RIPE itself), including the country.
Some panels make more sense to use with a date range, which can be entered below the search bar. Let’s search for the time range from January 1, 2022 until now.
The BGP Update Activity panel shows how many changes to the network’s routes were announced to other networks over time. This can show response to disruptive incidents, but the vast majority of BGP updates are routine. Note that there can be hundreds per hour.
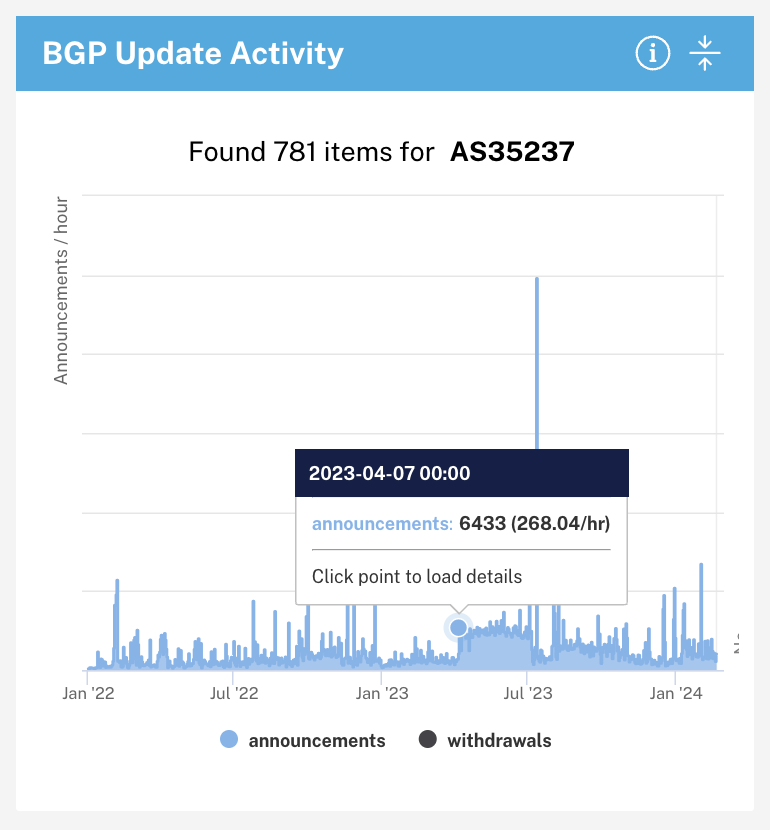
With a time range selected, the AS Neighbours panel shows a graph of the time spans that each AS was connected to Sberbank’s network. Again, notice that the neighbours can be relatively dynamic, and that there are many reasons, for example technical issues or changes in data centre location that might explain networks disconnecting or re-connecting.
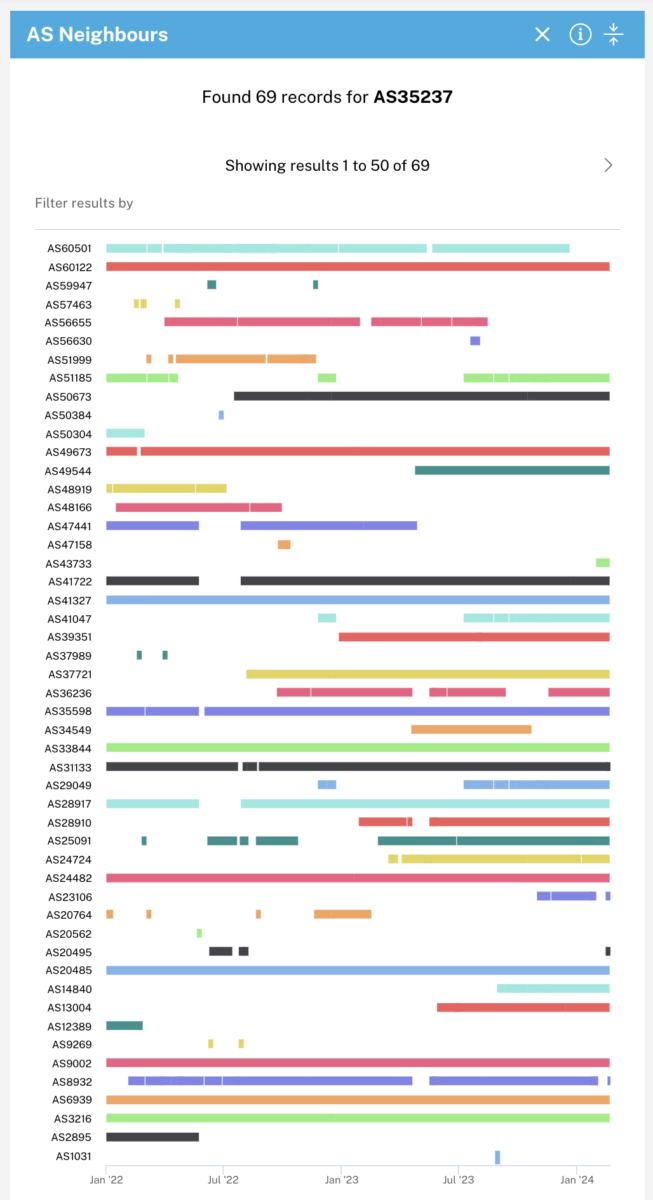
AS9002 (RETN), has remained consistently connected to AS35237 throughout the time period that we searched for. In contrast, AS5034, a Norwegian company that offers “infrastructure for cloud companies,” disconnected on March 2, 2022, the same day that the European Union removed Russian banks from the international SWIFT system. (Norway is not a member of the EU, and its own sanctions package followed on March 22, 2022.)
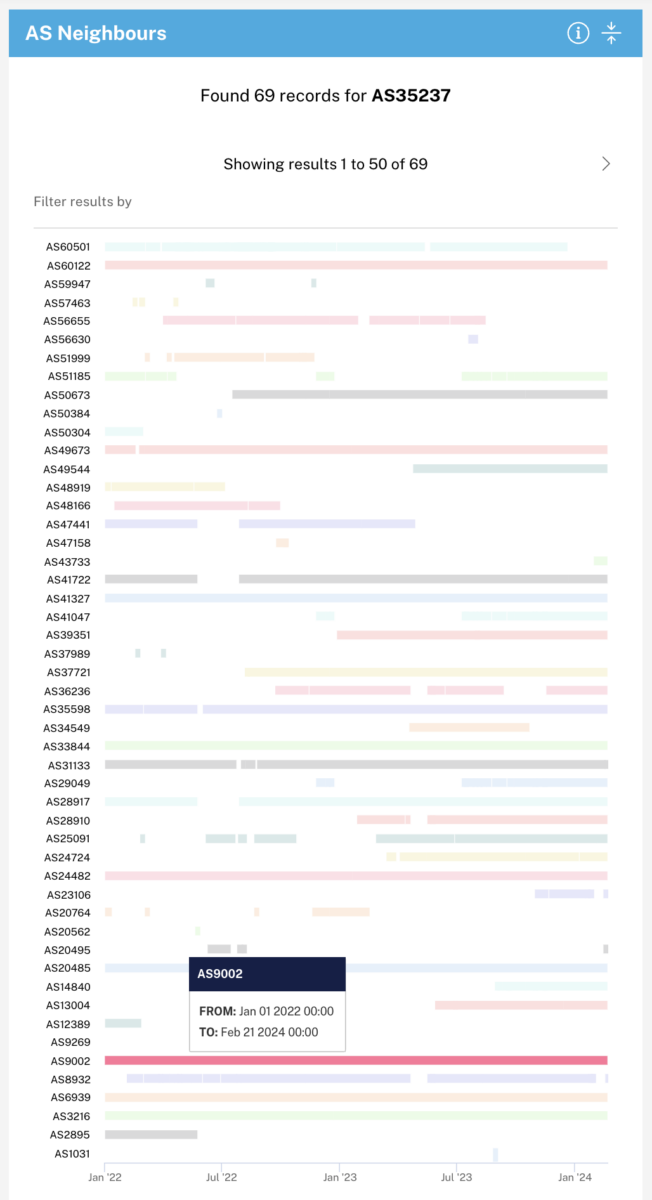

Switching the search time range to be a single day in the period of time when AS50304 was connected allows us to see if RIPEstat classified it as a left neighbour or a right neighbour.
Here it can be seen that AS50304 was a left neighbour, indicating an upstream or a peer.
This information can be used to probe how networks respond — or don’t — to disruptions including infrastructure damage, sanctions packages, wars, and even accidental configuration errors.
RIPEstate also has an API that can be used to download data programmatically. This makes it possible to look at large-scale trends and dependencies across the network.
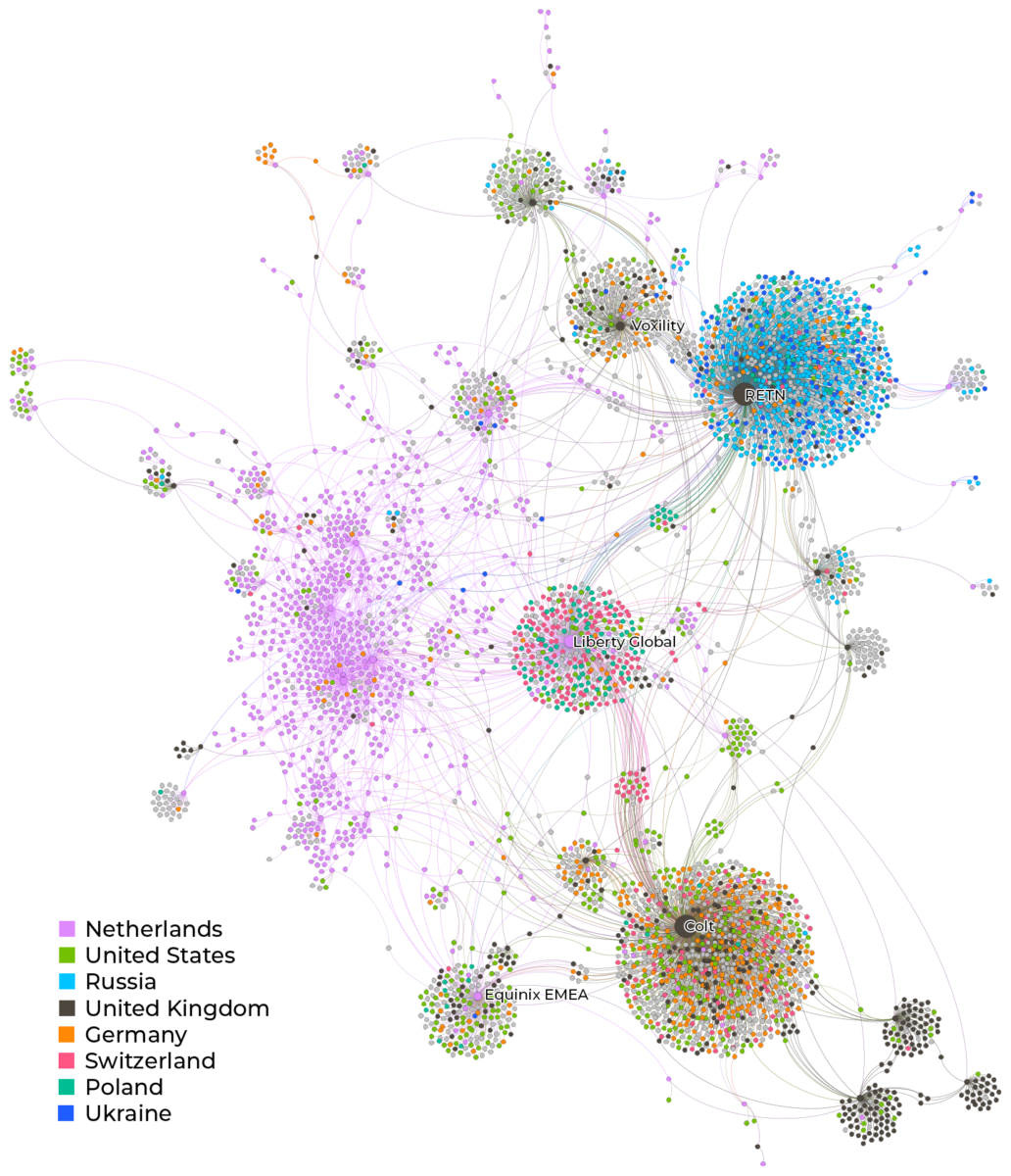
The network graph visualisation below shows the downstream connections from Dutch ASes to other networks, coloured by country. In this graph, purple are Dutch networks, light blue are Russian networks, and dark grey are British networks. The large node in the centre of the Russian cluster is RETN, showing its broad importance as an interconnect between Russia and the West.
A final tool that we will demonstrate is PeeringDB, which allows us to explore internet exchange points. These are specialised data centres where different networks can exchange data with each other. PeeringDB is slightly different from BGP Tools and RIPEstat because it relies on self-reported data. For this reason, it tends to carry little information about large commercial networks or surreptitious actors, but it can be useful nonetheless.
For example, we can look at AS50917, seen earlier as a peer of Sberbank.
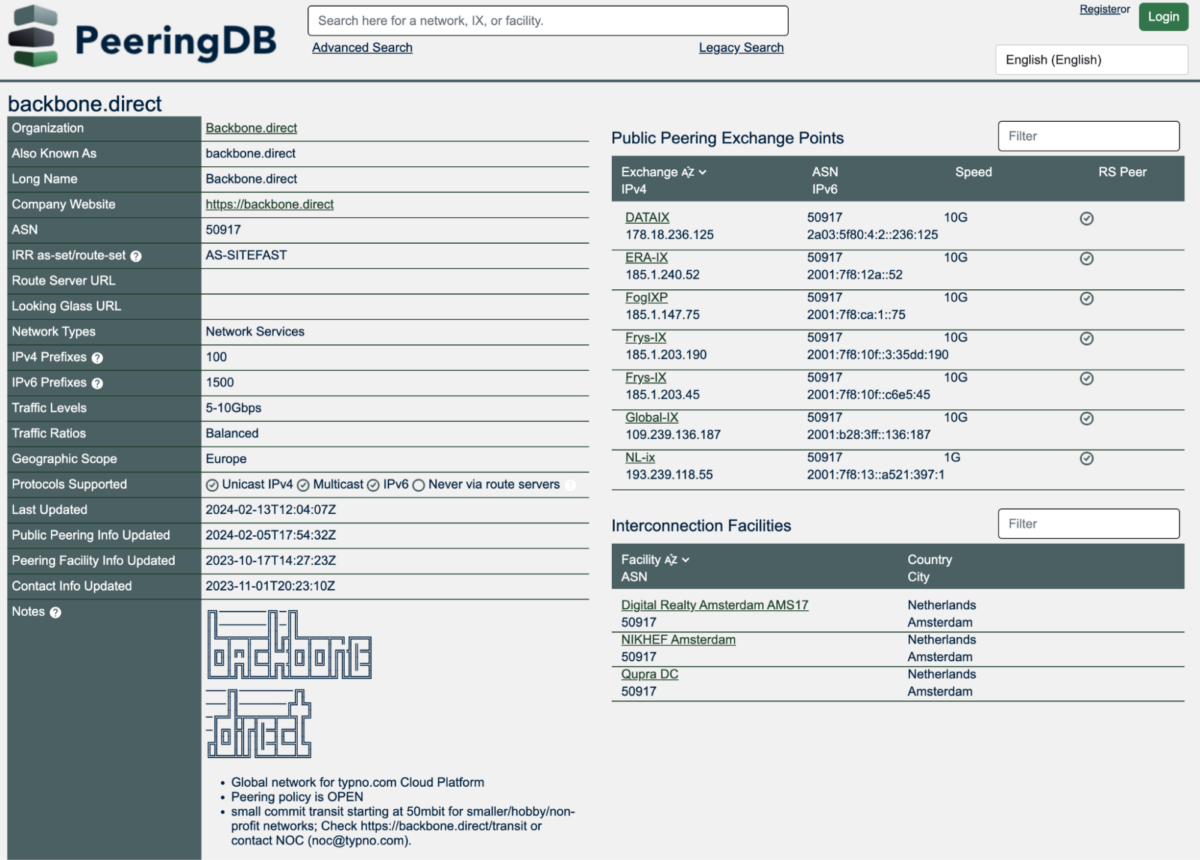
Here we can see some important statistics about their network, as well as self-reported notes. They indicate that they have an open peering policy, that is, they will peer with any network that wants to peer with them. However, they also sell transit bandwidth.
On the right, we can see internet exchange points listed in the panel titled “Public Peering Exchange Points.” Let’s examine the first one on the list, DATAIX. We can see contact information for the company that operates the exchange, technical details about the exchange, and networks that peer there.
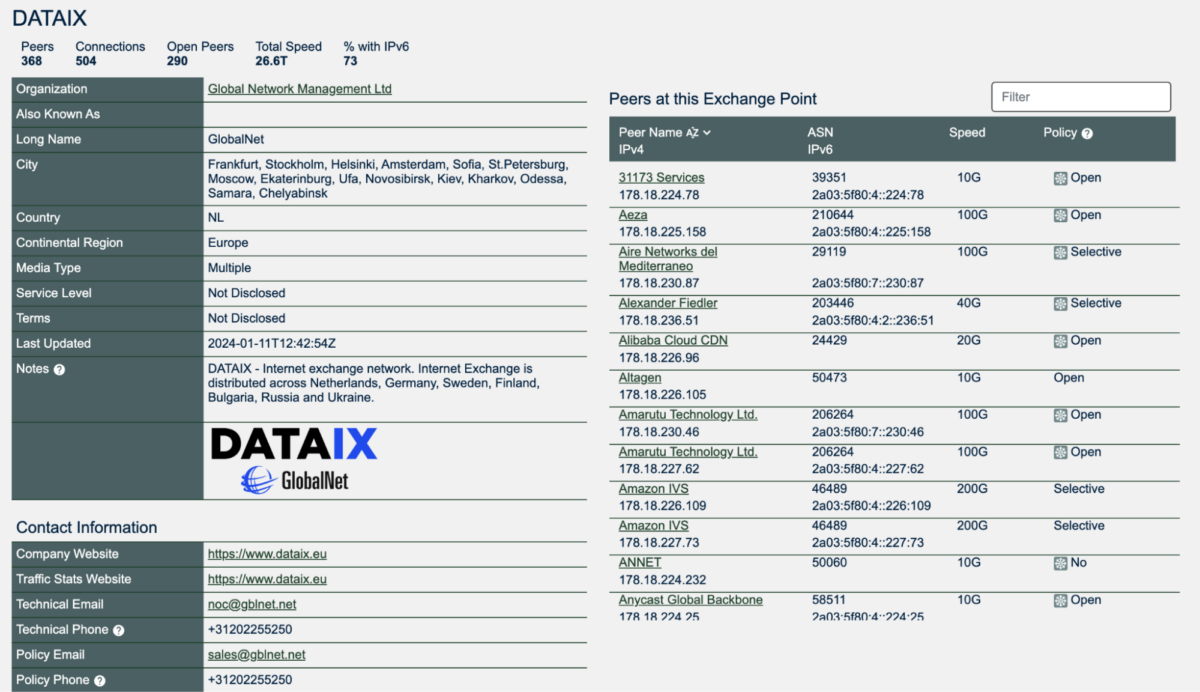
Scrolling down, it is also possible to see the list of local facilities that this exchange has — essentially, places where it is possible to plug in a server and connect your network.
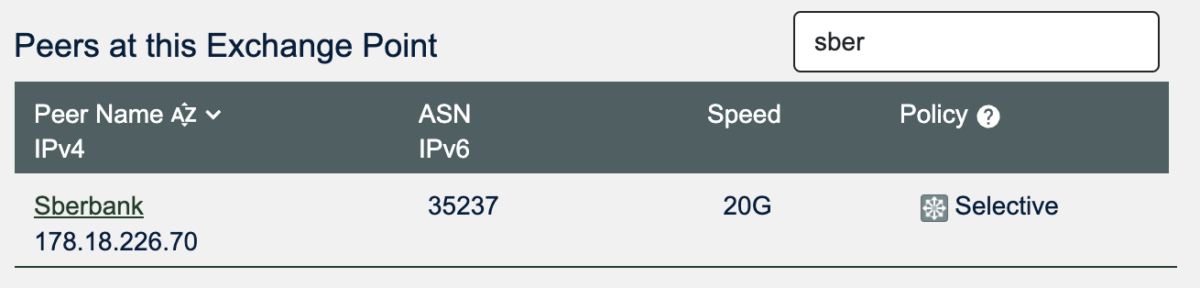
If we search for Sberbank in the list of Peers, we see that this is an exchange where the Sberbank AS peers, and that unlike Backbone.direct, they have a “selective” peering policy.
The Internet was built to robustly route traffic from one network to another network. Networks choose how they route traffic, and advertise the routes that they service. The Internet was not built to carry information about who is paying whom for data traffic, and it is not possible to directly observe this in any of the tools that we have looked at.
The Internet is both a vital worldwide communication network and an economic engine, and those two roles cannot be cleanly separated. Attempts to disable the Internet’s role in the economies of sanctioned countries could push those countries into their own independent “splinternets,” where access to information would be curtailed further and surveillance increased. But the status quo has led to inconsistent approaches and allows European companies to continue to profit from relationships with sanctioned entities and vice versa. There are no clear answers — from experts nor from policymakers.
With thanks to Alex Ștefănescu.
Bellingcat is a non-profit and the ability to carry out our work is dependent on the kind support of individual donors. If you would like to support our work, you can do so here. You can also subscribe to our Patreon channel here. Subscribe to our Newsletter and follow us on Instagram here, X here and Mastodon here.
如有侵权请联系:admin#unsafe.sh