2024-2-29 03:43:38 Author: www.malwarebytes.com(查看原文) 阅读量:9 收藏
In late January 2024, the ThreatDown Managed Detection and Response (MDR) team found and stopped a three-month long malware campaign against a Managed Service Provider (MSP) based in Europe. In line with our observations of attackers increasingly relying on legitimate software in their attackers, the attacker employed various Living Off the Land (LOTL) techniques to avoid detection.
MSPs are a prime target of cyberattacks for two main reasons. One, they provide services to multiple clients, giving attackers access to a broader network of targets through a single breach. Two, MSPs often operate on tight security budgets, making them more vulnerable to attacks.
Almost immediately after onboarding the MSP in mid-January, the ThreatDown MDR team found extensive evidence of an ongoing malware campaign. The attackers, who targeted the MSP’s network from October 2023 to January 2024, silently monitored and manipulated the network for months, leveraging legitimate remote access tools like AnyDesk and TeamViewer and attempting to install malware like Remcos RAT and AsyncRAT.
Let’s dive into the details of this incident and how ThreatDown MDR neutralized the threat.
Initial discovery and evidence of compromise
In late October 2023, ThreatDown Endpoint Detection and Response (EDR) flagged multiple suspicious outbound connections on the MSP’s network. These were attempts to communicate with known malicious external sites and IPs, involving several endpoints within the network.
This activity was immediately blocked by ThreatDown, marking the first documented evidence of a security breach. The nature of these attempts—targeting sites associated with RDP-based attacks and other malicious activities—indicated a possible compromise.
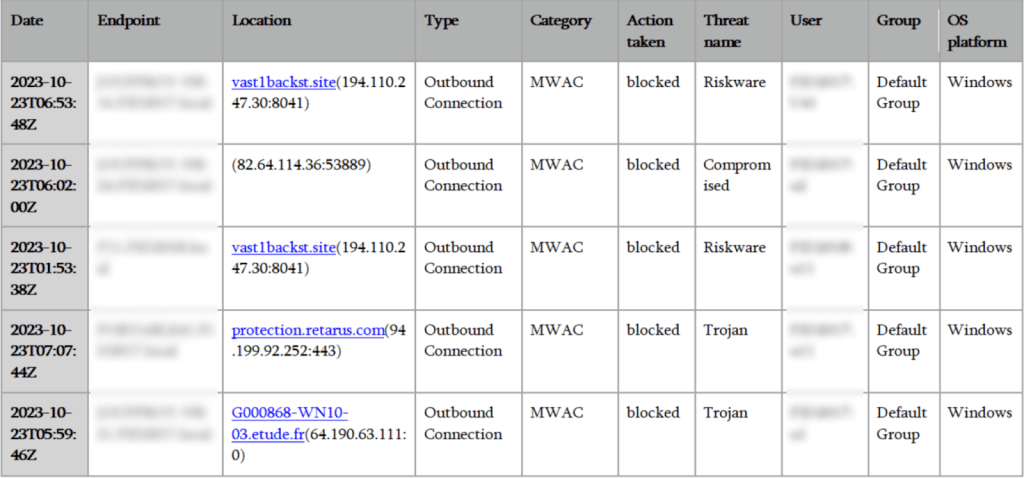
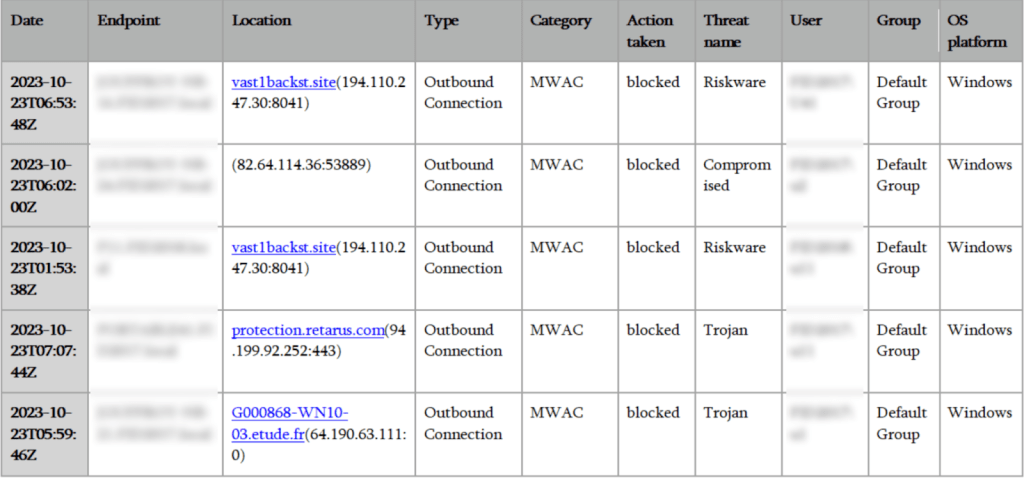
List of malicious sites automatically blocked by ThreatDown MDR.
Expanding presence and evasion
Following the initial detections in October, the attacker quietly expanded their presence within the network. On December 8th, network scanning activity was detected from an endpoint, indicative of the attacker’s efforts to map out the network for further exploitation. This activity went beyond mere exploration, suggesting a systematic approach to identify additional targets or vulnerabilities within the MSP’s digital environment.
Escalation and discovery of malware
The situation escalated in January 2024 with the discovery of malware on several endpoints, linked to unauthorized remote access tools like ScreenConnect and AnyDesk.
This pointed towards a more aggressive phase of the attack, with the attackers deploying malware to maintain and expand their access. An attempt to uninstall McAfee via PowerShell, observed on an endpoint, further underscored the attackers’ intentions to weaken the network’s defenses.

Detection of malware leveraging RMM tools.
Ongoing surveillance and response
The implementation of ThreatDown MDR services on January 18th, 2024, was a strategic move by the MSP to gain deeper insights into the attackers’ movements. By this time, the attackers had already established a significant presence within the network, as evidenced by the attempted communications with a known AsyncRAT botnet C2 server and the discovery of additional remote management and monitoring (RMM) tools on the network.
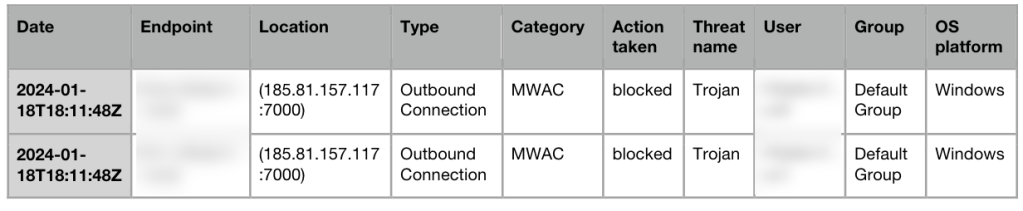
Connections to AsyncRAT were detected and automatically blocked by ThreatDown MDR
Fortunately, the ThreatDown MDR team caught the attack in action and made several immediate recommendations for the MSP, including:
- Isolating the compromised endpoints to halt the infection spread and re-imaging them for a clean slate.
- Changing all administrative and local passwords three times to fortify security.
- Restoring all infected endpoints from secure backups, eliminating the use of local administrator accounts, and implementing application and DNS filtering to control software usage and web access.
Threat hunting with ThreatDown MDR
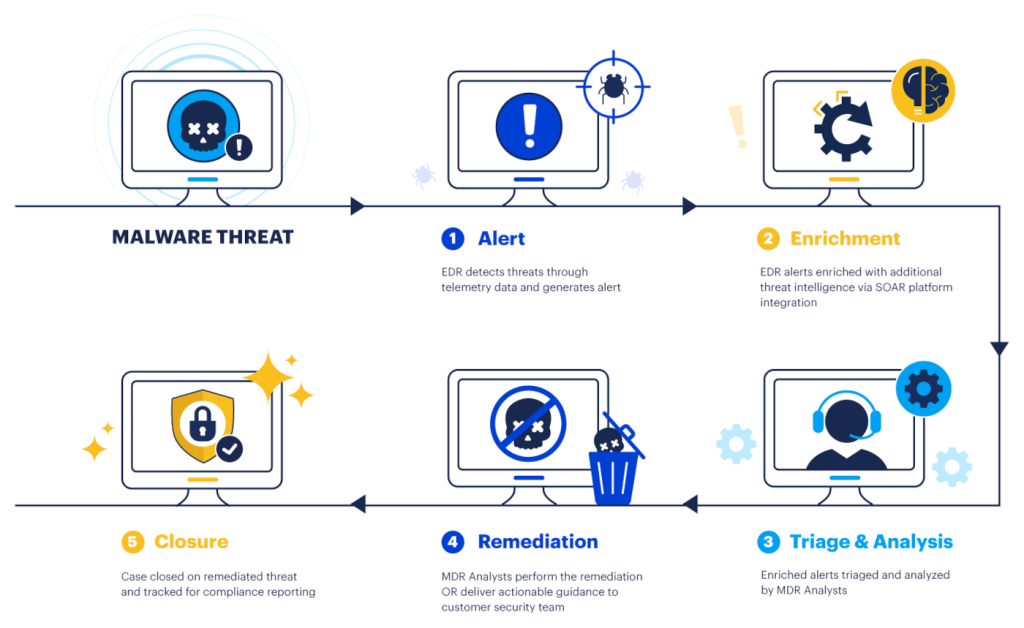
How ThreatDown MDR works
MSPs continue to be a prime target in cyber attacks—and as we’ve seen in this case study, attackers are in it for the long-haul, able to remain undetected for several months after compromising a network.
The attacker’s use of legitimate tools such as TeamViewer, ScreenConnect, and PowerShell, in their months-long attack on the MSP underscores a key theme we’ve been writing about on the blog recently: attackers are increasingly relying on LOTL techniques in their attacks to avoid detection.
In this example, if the attack had been allowed to continue, the MSP could have suffered a ransomware attack, data breach, or both. Fortunately, however, by hunting down LOTL techniques for the MSP based on suspicious activity and past indicators of compromise (IOCs), the ThreatDown MDR team successfully stopped the threat.
Protecting your MSP from stealthy LOTL threats takes an elite team of security professionals scouring your systems 24×7 for IOCs and suspicious activity observed on endpoints. Learn more about ThreatDown today.
如有侵权请联系:admin#unsafe.sh