In this blog, we dive into how the Open Cybersecurity Schema Framework (OCSF) improves the security 2024-2-28 23:8:14 Author: www.sentinelone.com(查看原文) 阅读量:21 收藏
In this blog, we dive into how the Open Cybersecurity Schema Framework (OCSF) improves the security analyst experience. By standardizing third party cybersecurity data through OCSF, SentinelOne enhances efficiency and effectiveness, enabling customers like Liberty Group to prioritize security operations over data acquisition challenges.
This exploration offers insights into the real-world benefits and potential of OCSF in elevating the cybersecurity landscape.

Understanding the OCSF Framework
The Open Cybersecurity Schema Framework (OCSF) is designed to standardize and streamline the way cybersecurity data is structured and shared across different security tools and platforms, enhancing interoperability and efficiency in threat detection, analysis, and response. It’s tackling a fundamental challenge in the security analytics space: the absence of a common, agreed-upon format and data model for logs and alerts across vendors. This lack of standard language in cybersecurity tooling and services creates a challenge for cybersecurity professionals and a lot of manual work.
The OCSF approach emphasizes both proactive defense and reactive response to cyber threats. With the goal of fostering adaptability and resilience in modern enterprises, OCSF works by integrating open systems for flexibility with closed systems for confidentiality and integrity. Combining these elements enables enterprises to be dynamic; adjusting quickly to evolving threats while balancing protection with the needs of the business.
Without the OCSF, security teams must compile data from multiple entities and standardize it to collect meaningful insights. This makes OCSF standardization crucial for the long-term health of defenders. It is a critical first step towards reducing the time and effort it takes to standardize security telemetry and log activity across tools and services, regardless of vendor.
We’re Committed to Making Things Easier with OCSF
SentinelOne’s goal is to improve efficiency and effectiveness of the analyst experience across the incident lifecycle. We recognize that the shift to adopting the OCSF makes the job of security analysts easier and simpler — ultimately supporting their ability to protect the organization from attacks. That’s why we’re committed to the OCSF and are leading the way by building this open standard into our Security AI platform from the ground up.
The Singularity Platform is a unified security AI platform, bringing a single agent, data lake, and console together for security operations. Singularity Data Lake powers this platform at every level. Using the Singularity Marketplace, customers can access a wide range of data connectors that transform third party data sources to OCSF standards, out-of-the-box, with no manual coding or extensive development required.
Singularity Data Lake is a cloud-native, high-performance, and scalable data lake that operates on a massively parallel query engine. It breaks down complex queries and runs computations simultaneously before returning answers to analysts with ~96% return rate on queries within a second. That’s up to 10x faster than legacy SIEM and XDR providers.
Adopting OCSF open standards allow for data portability, ensuring that organizations can future-proof their security tooling. You never know what’s needed next to secure the business, and building on a common data language gives businesses the confidence to add to Singularity Platform as the central hub for security operations. With OCSF, Singularity Data Lake provides the platform for future innovation.
A Real-World Scenario | Streamlining Data Sources in the Singularity Platform
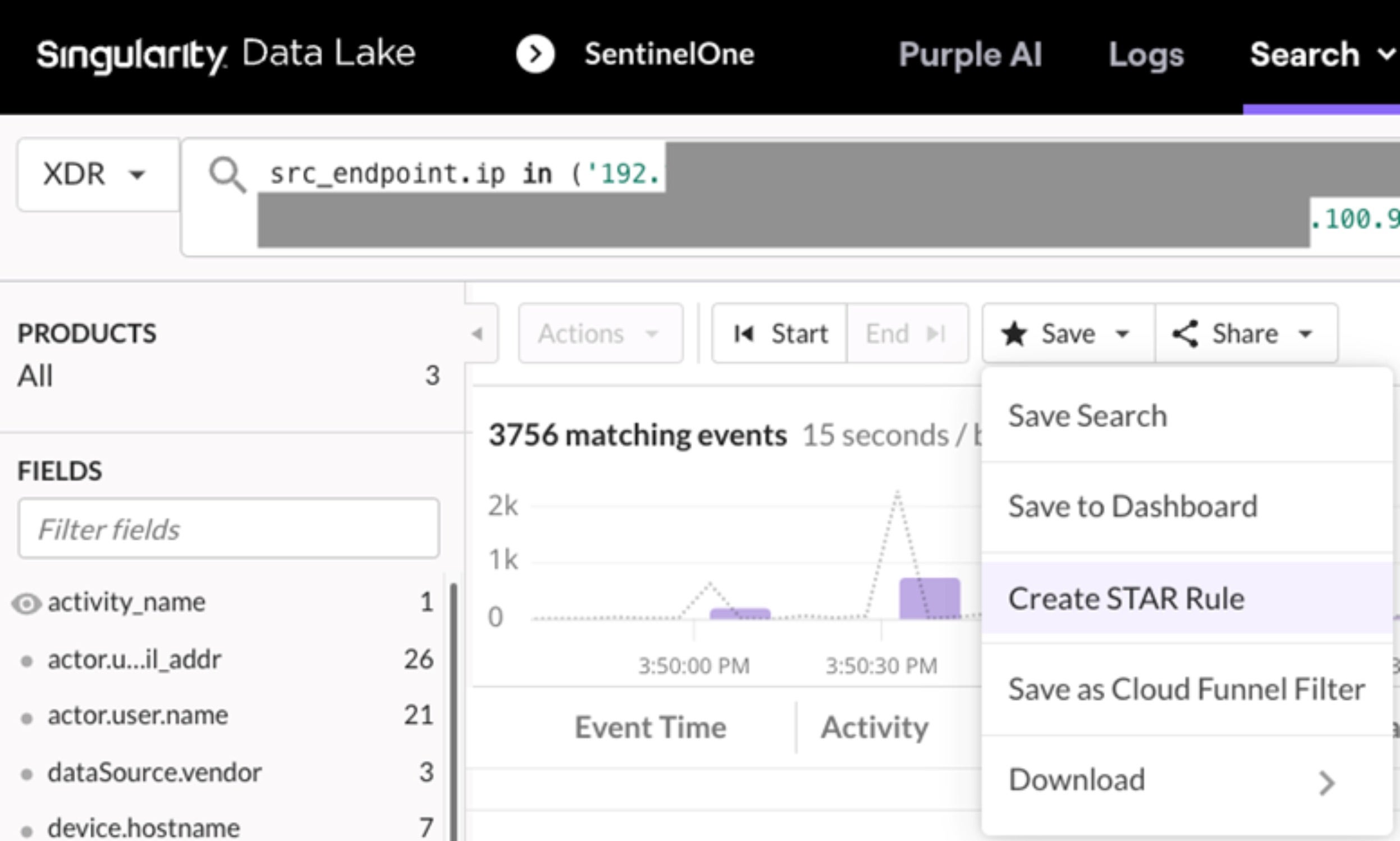
Data adhering to OCSF also streamlines the process of creating custom detections. In the Singularity Platform, custom detections are named STAR rules (Storyline Active Response) which empower security teams to create alerts by querying data they ingest into the Singularity Data Lake. Since our data conforms to OCSF, security teams can write one STAR rule that covers multiple data sources.
Let’s look at a simple STAR rule meant to track several source IP addresses across an environment that ingests logs from multiple vendor products into the Singularity Data Lake. From OCSF documentation, the standardized field name used for source IP address is src_endpoint.ip so, we’ll use that in our query. When we execute this query, notice that results from multiple vendor logs sources are automatically included (SentinelOne, Okta, and Fortinet).
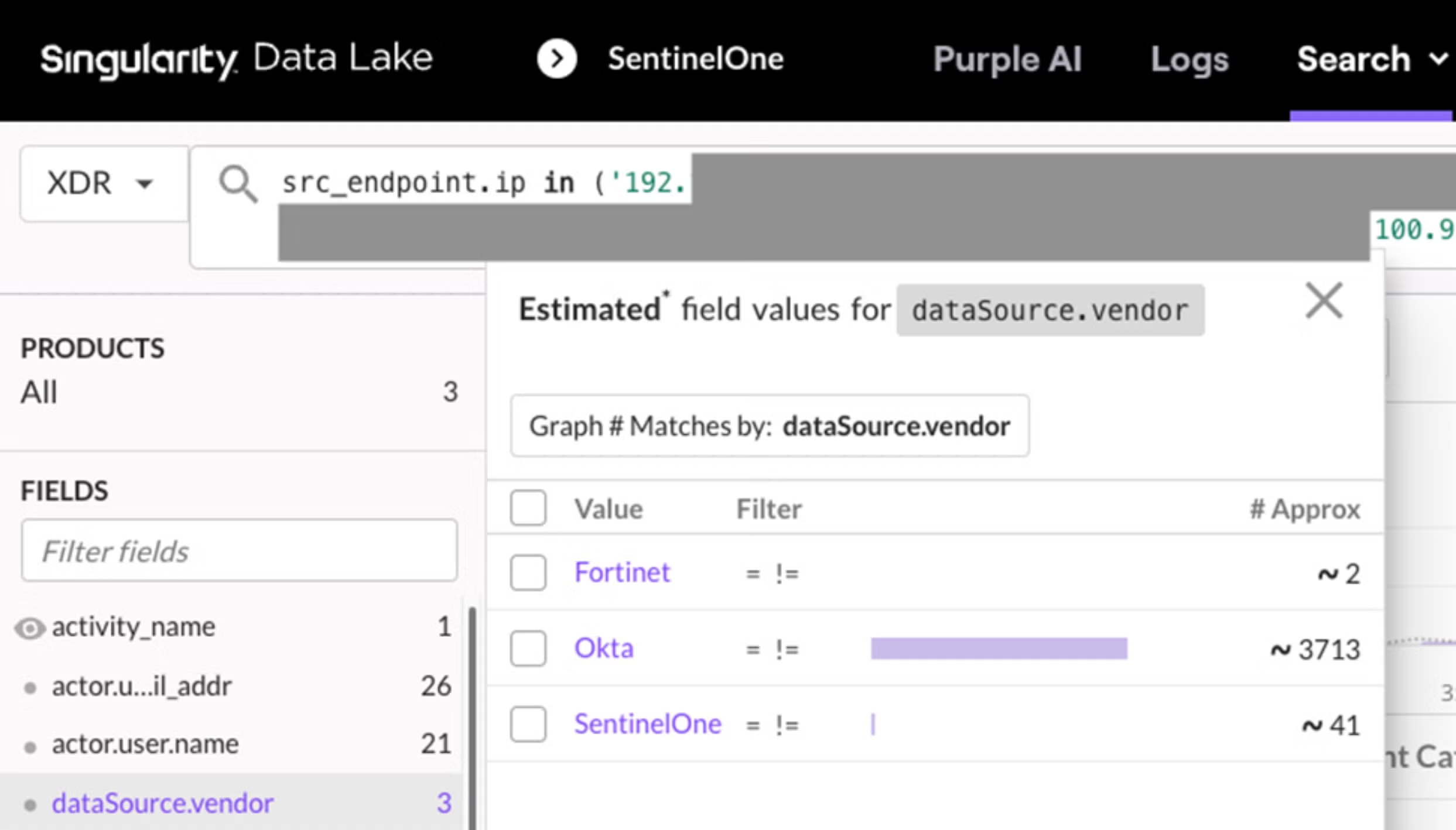
The query is tuned to minimize the result set. Then, we can create a STAR rule to generate alerts without the need to specify the log source. This essentially future-proofs the STAR rule so it is effective at finding this source IP address in additional log sources added to the data lake in the future.
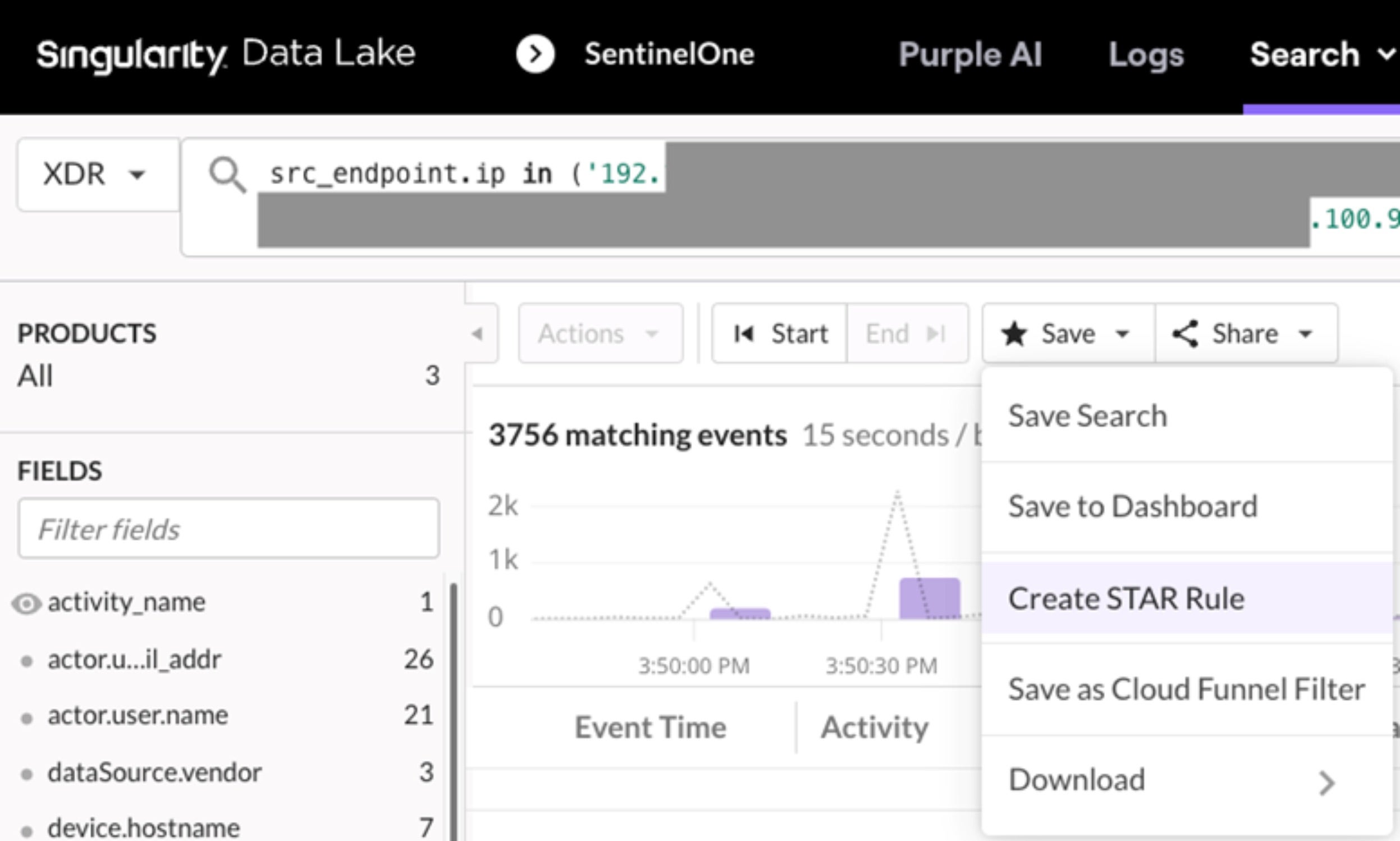
To ensure alerts generated by the STAR rule are acted upon immediately, we can leverage automatic response actions, such as network quarantine.
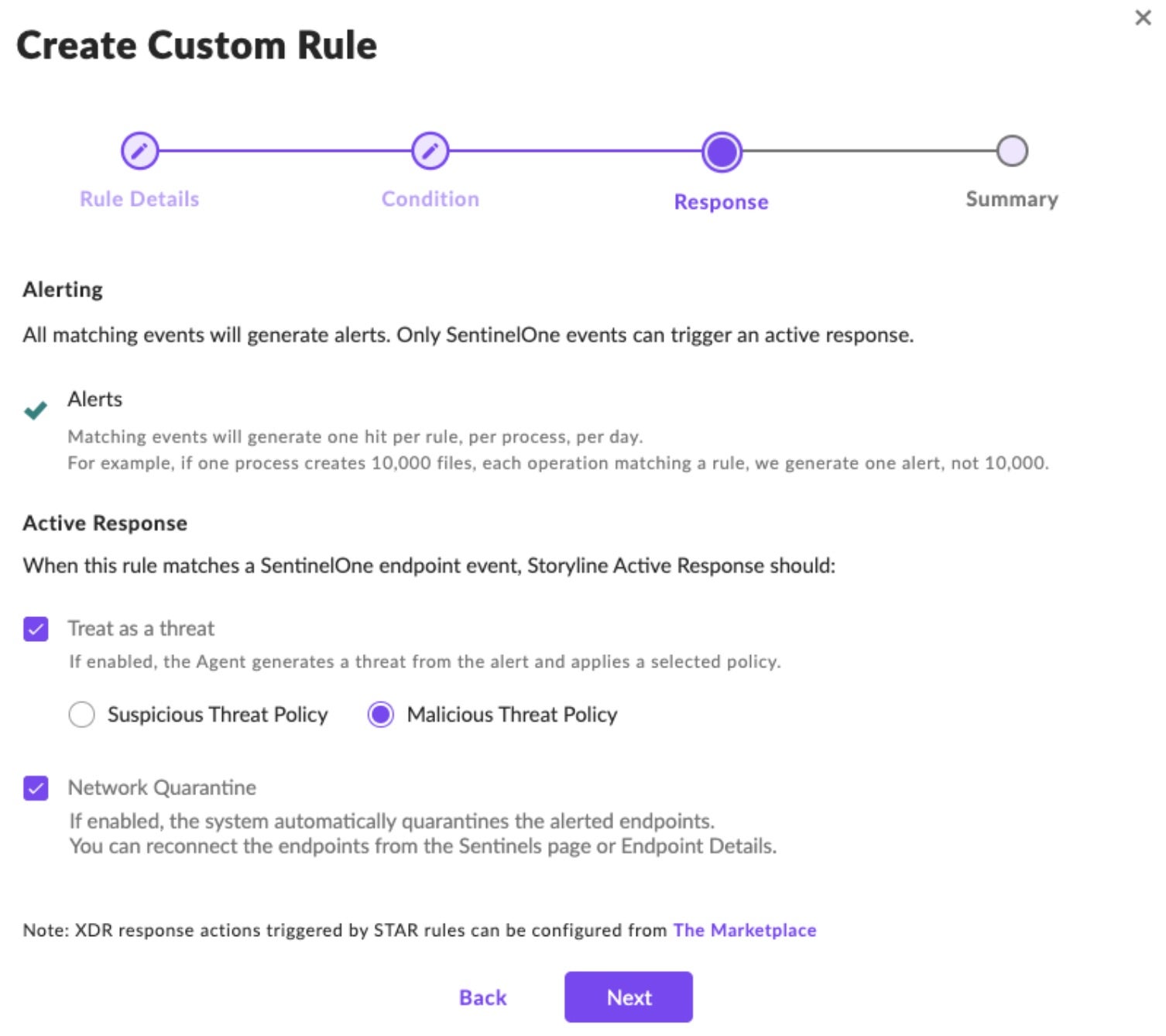
Now with OSCF, we can simplify the creation of custom rules across multiple data sources. Even when additional sources are added, this detection will persist across them all. Analysts can write rules once and apply them universally, regardless of the addition of new security data to the Singularity Data Lake.
What’s the Bottom Line?
Having a common schema for the cybersecurity industry is a significant step forward in our ability to respond to and hunt for threats. Adopting OCSF puts cyber defenders and enterprise leaders on the same page at the same time, so that ultimately they are equipped with the best tools for the job.
Leveraging OCSF, SentinelOne commits to:
- Greater efficiency – Our commitment to the OCSF drastically cuts data processing time. Now, data is normalized from the get-go, speeding up analysis and the ability to respond to threats.
- Comprehensive coverage – Without a common framework for cybersecurity data, there’s a risk that important information might be overlooked or misinterpreted. By adopting the OCSF, we help to ensure data is complete, so customers can accurately interpret insights, regardless of the tools they use.
- Scalability – As an organization grows, so does the complexity of its cybersecurity infrastructure. A standardized schema like the OCSF aims to provide a scalable approach to data management, so security systems can evolve without losing the ability to communicate effectively.
- Smarter team allocation – OCSF removes the need to hire or train people on vendor specific language normalization efforts, allowing people to get back to what they’re best at — protecting the enterprise.
Liberty Group | Our Customers Are Leading the Way
Our customers are ready for the opportunity OSCF provides; customers like Owen Connolly, CISO from Liberty Group.
Owen and his team manage a vast security infrastructure to protect its steel and mining business. The real challenge, however, lies in the incredible amounts of overhead time required to parse information between all their platforms before normalizing data across all ingested data.
In Owen’s words, “Before SentinelOne, much of our time was spent analyzing data across multiple systems due to the technical cost of getting an integrated view, rather than focusing on security operations.” He continues, “Having a platform that provides OCSF-ready data connectors is a game changer and allows my team to focus on detection, triage, investigation, and response rather than data architecture.”
Future-Proof Your Security Strategy
Here at SentinelOne, we want to do what’s right for the cybersecurity industry. When we improve the analyst experience, we empower them to focus on what matters most — defending the enterprise. Cyber defenders face an ever-changing landscape, working to stay steps ahead of malicious actors and the unknown nature of developing threats. By aligning our products to Open Source standards, we’re leveling the playing field. SentinelOne’s adoption of OCSF builds momentum towards a future where today’s leaders can plug in the tools they need without the burden of complexity to slow them down. We hope that more vendors will join us on this journey.
SentinelOne is trusted by global enterprises across a variety of industries and organizations with complex security requirements. Learn more about how Singularity Data Lake empowers businesses to centralize and transform data into actionable intelligence for cost-effective, high-performance security and log analytics here.
如有侵权请联系:admin#unsafe.sh